Chapter 18: C-UAS and Large Scale Threats
Chapter 18 will introduce developing trends for countering illegal / rogue drone use within the United States using counter-UAS (C-UAS) technology and systems.
Student Learning Objectives. Upon completion of this chapter, students should be able to:
- Further understand what Counter-UAS (C-UAS) technology is
- What civil restrictions are currently in place and what agencies can use C-UAS
- How the government is attempting to ease restrictions for C-UAS use
- How Congress through HR302 plays a role in easing restrictions for C-UAS
- How and why government agencies use C-UAS
- What types of threats currently exist?
- The growing potential for countering large UAS
Countering Emerging Unmanned Air System Threats
The FAA has forecasted that the unmanned air systems market will see exponential growth over the next 20 years. Commercial ‘hobbyist’ drones are expected to double from 1.1 million to 2.4 million systems. The larger sized commercial UAS fleet will grow from 111,000 in 2017 to roughly 452,000 by 2022 with the number of registered pilots climbing from 74,000 to over 300,000 by 2022 (Miller, 2018). With this accelerated growth, (Figure 18-1) there have been -numerous incidents around the world involving safety and privacy issues. These incidents have ranged from intruding on personal property to the complete shutdown of major international airports. (Perez-Pena, 2018) These incidents stemmed from UAS being in either the wrong place at the wrong time or the systems were intentionally violating airspace for reasons unknown. The purpose of this study is to examine the current and future methods that are and will be used to safely identify, counter and intercept potentially hazardous drones and to review national policy regarding counter UAS (C-UAS) practices and procedures.
Figure 18-1: UAS Market Growth 2018 -2036
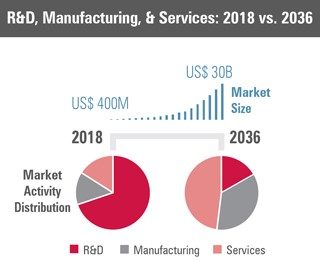
Source: (AIA & Avascent Report, 2018)
The demand for ever larger systems continues to push the UAS industry to meet this need. (see Figure 18-2) Increased payload capacity also increases the destructive potential for UAS systems when misused for malicious purposes. As these systems continue to grow in capability, so too will C-UAS to match.
Figure 18-2: UAS MTOW Market Analysis 2018 – 2036
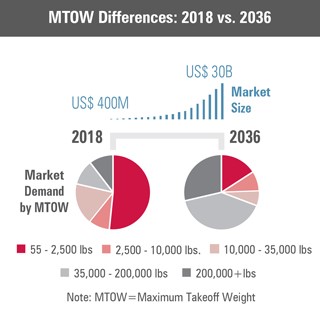
Source: (AIA & Avascent Report, 2018)
As of October 2018, the United States government implemented its first policy that directly affects drone usage. Known as the FAA Reauthorization act of 2018, HR 302 directs the FAA to begin drafting the way ahead for a UAS usage framework. Subtitle B – Unmanned Aircraft Systems, contains all directed actions the FAA will have to address to include C-UAS operations. (115th-congress, 2018) Most of the directed actions involve developing a practical way forward for C-UAS practices within the US and its territories. As of this moment, very few if any national policies are in place that regulate or even guide what can and cannot constitute C-UAS technology. Nor is there any governance on where and when C-UAS tech can be used outside of common laws that are already in use. It remains vague as to how a drone and its use is governed as personal property.
C-UAS is more than just using a system to knock a drone from the sky. The users must take into consideration the implications of what could happen if a UAS falls from the sky and damages property or injures people. If a drone is hovering over a large crowd for example, steps must be taken to allow the drone to be successfully removed without harming bystanders. This was the case recently when a drone was spotted dropping leaflets over a pro football game in Nov 2018. The operator was eventually identified and arrested but nothing could be done about the UAS while it was in flight. (Laris, 2018) This incident could have been far worse if the UAS operators’ intentions were more sinister in nature.
The US population has a vested interest in the future of UAS and C-UAS operations. Civil and -military agencies, academic researchers as well as the everyday citizen already have access to UAS technology. These systems are well on their way to becoming part of our daily lives and there is currently no limit to what they can achieve. Knowing when, where, and having the ability to stop UAS misuse will be paramount.
Introduction
Counter Unmanned Air Systems is an array of linked technology designed to detect, identify / analyze a threat and if necessary, intercept unmanned air systems / drones. Rogue and hostile drone use is becoming an exponentially increasing concern for the Department of Homeland Security (DHS) and the Department of Defense (DoD). Illicit drones have also stirred the general public into seeking technological means of preventing UAS from violating privacy or exploiting intellectual property. The recent passing of HR 302, the FAA Reauthorization Act of 2018, has directed the FAA to conduct multiple inter agency reviews in order to determine the current status of C-UAS affairs in the United States. It also directs the FAA to work with the DOD to glean current best practices and procedures for acquiring and operating C-UAS systems for future use with the US and its territories. The intent for this research is to illustrate the current lack of legislation and regulation regarding the use of C-UAS within the US as well as review current and future technology trends in use. This research also aims to review C-UAS technology under development with the Department of Homeland Security (DHS) and the Department of Defense (DOD).
Current Civil Restrictions / Policy, Directed Reviews from HR 302
“There are several legal impediments to utilizing counter-UAS technology. The Communications Act of 1934 prohibits the use of unlicensed radio equipment such as jammers or other devices that interfere with communication, such as the UAS command link.” (Embry Riddle Aeronautical University, 2018) “The general public is further prohibited to manufacture, import, market, sell or operate jamming equipment in the U.S. under 47 CFR 2.803.” (Embry Riddle Aeronautical University, 2018) “Finally, 18 USC section 32 imposes imprisonment or fines upon those that damage, disable, or destroy civil aircraft which can be interpreted to include drones.” (Embry Riddle Aeronautical University, 2018) “Operators may also be subject to liability associated with tort claims arising from the potential collateral damage, injury, or adverse effects of counter UAS activities.” (Embry Riddle Aeronautical University, 2018) Such liability issues may include interference caused by jamming equipment or damage / injury caused by the forced disabling of the offending unmanned aircraft. (Wallace, 2018)
Steps to Easing Restrictions
In 2016, Congress passed the National Defense Authorization Act of 2017. In Sec. 1697,
“Congress codified new authority for military leaders to mitigate UAS threats. The statute gave relatively broad powers for the armed forces to disrupt control, intercept, seize, disable, damage, and destroy offending aircraft.” (Embry Riddle Aeronautical University, 2018) The security risk posed by unmanned aircraft has not gone unnoticed by commercial entities either. Stadiums and other open-air public gatherings are recognizing the need for counter-UAS activities. On November 28, 2017, Tracy Mapes was arrested after flying a small UAS over NFL game at both the Levi Stadium and Oakland Coliseum two days earlier. (Gomez, 2017) The unmanned aircraft allegedly dropped leaflets over the stands at Levi Stadium. After reviewing surveillance footage of the initial incident, law enforcement personnel anticipated the alleged perpetrator would try the same activity at the nearby Oakland Coliseum. Santa Clara Police Lt. Dan Moreno highlighted the risk of UAS operations over the crowded areas stating, “A drone can lose control and injure someone in the crowd or drop material that may be harmful. We are evaluating our security practices with state and federal authorities to make sure this doesn’t happen again.” (Gomez, 2017) This and other incidents have led to the need for more robust yet public friendly C-UAS technology.
HR 302: FAA Reauthorization Act of 2018
For this theme the author spent a great deal of time reviewing two sections within HR 302
passed by congress in October of 2018:
- Section 364, U.S. C-UAS Review of Interagency Coordination Processes
- Section 365, Cooperation Related to Certain C-UAS Technology (115th-congress, 2018)
From these sections, the author was able to infer what the government was trying to accomplish. Congress directed the review of how the FAA and other agencies were using C-UAS within the United States and its territories. The reviews directed specific considerations to address, the most significant of these are listed below:
- Safety in the national airspace
- Protecting individuals and property on the ground
- Coordination procedures and protocols with the FAA during the operation of C-UAS systems
- Adequate training for personnel operating C-UAS systems
- Best practices for the consistent operation of C-UAS systems to the maximum extent practicable (115th-congress, 2018)
The last significant piece of information from HR 302 was that Congress directed the FAA to specifically conduct a review of any additional authorities needed by the FAA to effectively oversee the management of C-UAS systems within the US and its territories. (115th-congress, 2018)Section 365 deals directly with the deployment of C-UAS systems in the national airspace. Congress also directed the Secretary of Transportation to consult with the Secretary of Defense to streamline deployment of C-UAS systems by drawing upon the expertise and experience of the DOD in acquiring and operating C-UAS systems consistent with the safe and efficient operation of the national airspace system. (115th-congress, 2018) Once the directed reviews are complete and made public, C-UAS procedures will become standardized and regulated by the FAA. Industry will then be able to evolve, and narrow down existing trends moving forward and develop C-UAS technology that complies with these new standards. This moves industry one step closer to opening the door for broader general public use of C-UAS.
C-UAS and the Department of Homeland Security
To increase safety, lower costs and increase efficiency more and more private companies are looking to add drones to their workforce. These drones have the potential for use in dangerous aerial inspection jobs as well as local deliveries normally performed by humans. The largest hurdle for these companies is how to incorporate the large volume of drones necessary for these jobs safely into the national airspace without collisions or infringement on privacy. (Sullivan-Nightingale, 2015) This increased interest ultimately means more drones will soon be flying around localities and neighborhoods. This increase in drone activity will continue to pose a problem for privacy, security and general public safety. Presently, UAS and drones are an inexpensive way to gain real time situational awareness over any venue to include large gatherings and sporting events. Hovering drones pose a real danger to the crowd below should they malfunction or loose link with their pilot. (Warwick, 2016) Until recently, most C-UAS systems used kinetic means to physically remove a drone from the airspace. Researchers are now able to identify, track and if needed commandeer the drone and land it safely. Current technology can also be used to triangulate the offending pilot’s location to pass on if notifying the authorities is necessary. (Warwick, 2016) With the eventual increase in drone activity, local government authorities will need access to C-UAS in order to maintain the security and safety of its citizenry.
C-UAS and the Department of Defense
The militarization of drone use began during the opening years of the Global War on Terror (GWOT) in the early 2000’s. Before this time, the average citizen had no concept of what UAS capabilities were at the time. Large systems such as the MQ-1 Predator and RQ-9 Reaper have since become the face of GWOT. Their ability to conduct long endurance reconnaissance and precision strike operations vs large scale bombing campaigns has made drone proliferation a priority in most of the militaries of the world moving forward. China has declared that it will have produced over 20,000 drones by the year 2020 in order to protect its ever growing “One Road,” initiative as it seeks to expand is economic influence in the region. Other countries that would be considered potentially adversarial to the United States have also dramatically increased drone acquisitions within the past decade. Simplicity and low cost of UAS technologies make their proliferation difficult to control. (See Figure 18-3 and 18-4)
Figure 18-3: Unmanned Systems Funding by Service Source: (Krasnov, 2017)
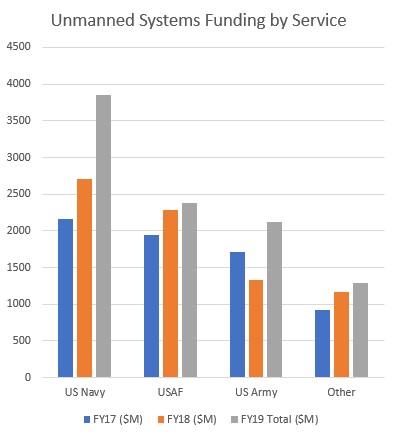
Figure 18-4: UAS Market Size by Destructive Mitigation Type
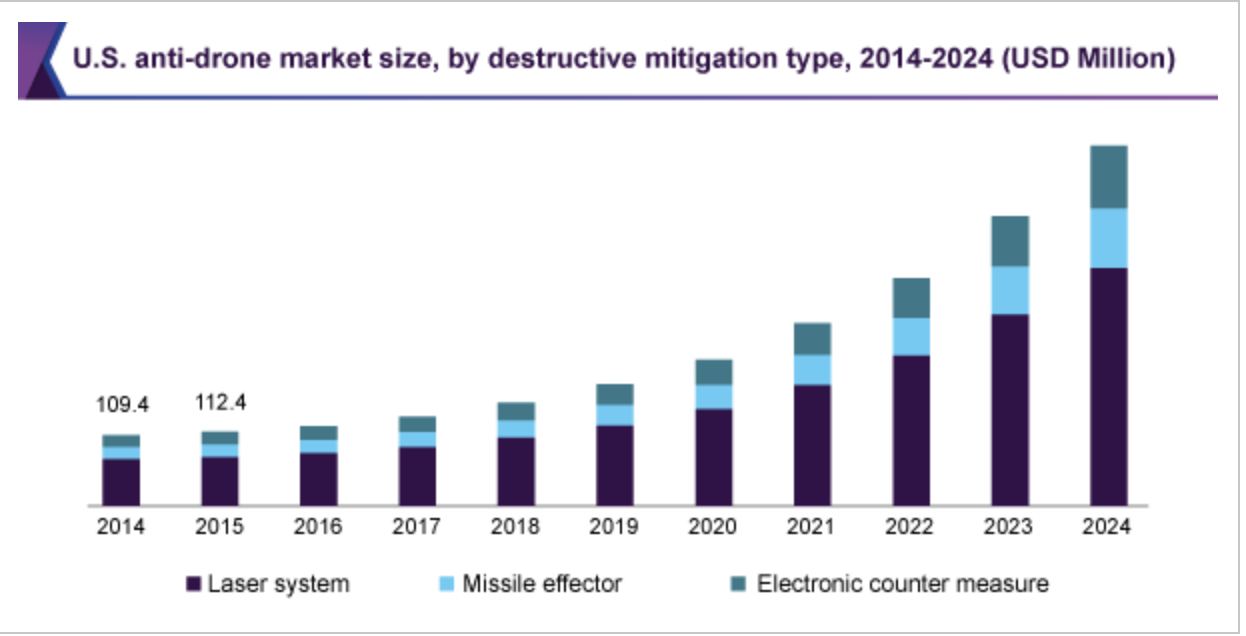
Source: (Grandview, 2018)
As more and more drones prepare to enter the future battlespace, the US Department of Defense (DoD) has begun to re-look its short- and long-range air defense capabilities. Vulnerabilities for each service have recently been identified based on the services given specific mission and current drone technology available to enemy combatant to observe and counter their operations. The DoD has specifically focused on brigade and below sized levels for the Army and Marines, individual vessels for the Navy and large airfield infrastructure for the Air Force. Each service has made C-UAS technology and system acquisitions a top priority in recent years and will remain a priority for the near future.
SWARMS
The threat(s) UAS pose continue to evolve with the most recent development of drone “SWARMS.” Drone swarm is used in two separate ways, cooperative and coordinated swarming. For a cooperative swarm, drones perform complex functions en masse such as land surveying, mapping, complex entertainment displays, manned / unmanned teaming, single attack performed by several drones against one target. Coordinated SWARMS, drones perform separate tasks aimed to achieve one goal. Examples include transmission line repair and complex attacks against multiple targets at the same time. Swarming has been carried out by low slow and small drones with varied success, the most notable was an attack against a Russian air base in Syria in January 2018, where several home-built drones carrying crude munitions penetrated Russian defenses and successfully damaged aircraft and equipment on the base. This attack proves drone SWARMS are difficult to track and engage effectively using current systems. The US DoD has taken great strides to create and expand C-UAS doctrine and update existing systems.
The most difficult challenge faced by the DoD is developing and implementing C-UAS across a Joint Force. Each service has its own methods, technologies and systems but the hard part is getting them all to talk and coordinate with each other. Some of these challenges include being able to identify current enemy UAS, integrating short range defense (SHORAD) and operating with the absence of robust joint doctrine that allows commanders to wield all forms of C-UAS within their respective battle space.
AI and Machine Learning
Advances in C-UAS tech has begun to see emerging technology, like artificial intelligence (AI), as a means of supporting non-lethal counter-UAS applications. Citadel Defense Company recently launched its newest counter-UAS specific system, Titan. The system is designed for anti-drone scenarios such as drug trafficking, espionage, cyber-attacks and attacks on airports. Titan provides the user real-time information, identifying and classifying a single approaching unmanned aerial vehicle or a larger swarm. The system selectively applies precise countermeasures to induce the UAV(s) to land or return to its home base. Citadel Defense uses machine learning, artificial intelligence and software defined hardware technology to rapidly address new threats and protect people and assets. (Rees, 2019)
C-UAS and the General Public
Reviewing currently available C-UAS technology yielded three major types that best suite usage by the general public in a civil domain. These systems have the lowest chances of posing any potential harm bystanders:
- Local radar systems
- Integrated microphone / RF signature detection systems
- Acoustical systems for passive detection / offensive destruction
Local Radars have seen success as recently as this year’s super bowl in Atlanta, GA. The FAA declared a restricted flying zone for one mile around Mercedes Benz Stadium. Local radar was used to track and if needed, direct integrated systems to remove the drone. The radars lead to the successful interception and safe landing of multiple drones without incident. (O’kane, 2019)A commonly occurring theme is that most vendors still do not know what they need as far as C-UAS systems and the demand for security experts with this knowledge continues to grow. (Warwick, 2016) The need for C-UAS systems extends to non-standard facilities such as correctional institutions. In recent years, prisons have seen an increase in illicit drone activity in the form of contraband drops to inmates. By integrating RF detection systems / jammers linked with passive microphones, correctional facilities have been able to identify when and where drones conduct these drops. (Dedrone, 2018)
The final emerging C-UAS tech trend is acoustical systems. Small teams in academia are currently working to see how ultra-high frequency noise that cannot be heard by the human ear, can be used to safely disrupt drones while in flight. There has been success in disrupting the microscopic gyroscopes (MEMS) within the drone motors causing the rotor heads to spin at differing speeds resulting in the drone becoming unstable and crashing. (Son, 2015) In its current form this technology is best used as an area denial system. Acoustical technology will most likely be used to defend an area from a multiple drone’s swarm and could possibly be coupled to part of an existing network of C-UAS systems to form a layered defense for a private facility.
Emerging Threat of Large Civil UAS
The next evolution for the UAS industry will to begin to dramatically increase payload capacities. This would enable more economical uses for delivery services to begin delivering large goods right to consumers or deliver goods across long distances reducing costs of aerial transport. As this trend seeks to take hold of the UAS market, C-UAS researchers will have to begin to visualize the threats scenarios these systems will pose and how they can be safely countered. (See Figures 18-5 to 18-7)
Figure 18-5: UAS Market Growth Predictions by Civil Sector
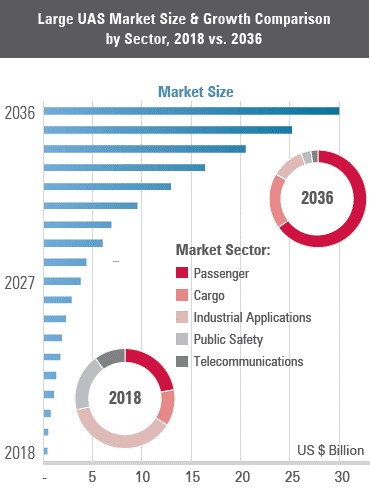
Source: (Unmanned Airspace.info, 2019)
Figure 18-6: Think Bigger: Large UAS and the Next Major Shift in Aviation

Source: (News, 2019)
Results
Current Restrictions / Policy, Directed Reviews from HR 302
Once the final reports from HR 302 are released, the FAA in coordination with the DOT and DoD will begin to standardize current best practices. This will establish rules and regulations that industry can then use to guide its research and development as it clamors to meet market need. Drone use will continue to grow exponentially as shown by market research as applications for UAS’ continues to be developed. It is the opinion of the researcher that once the FAA has established a firm precedent for civil C-UAS operations, the C-UAS industry will see very similar exponential growth to match the UAS industry.
Figure 18-7: Defining Large UAS

Source: (AIA & Avascent Report, 2018)
C-UAS and the Department of Homeland Security
Civil authorities will soon have no choice and will have to address / budget for local government use of C-UAS in order to protect local infrastructure and public gatherings. The threat(s) posed to open space venues and facilities will require affordable and adaptable systems that can be used to protect the public at large. Fortunately, private industry has already been developing integrated systems that are designed for this purpose(s). As drones become increasingly sophisticated, potential adversaries and drug cartels can also potentially use these systems to conduct cross border incursions.
C-UAS and the Department of Defense
Addressing current gaps for the DoD and finding ways forward for joint doctrine integration will be crucial for the Defense Department to stay ahead of growing threats posed by peer / near peer state actors and rogue organizations / individuals. The DoD was the first organization to see and begin to adapt to the growing threat of drone use. There guidance and expertise will be invaluable for the FAA and DHS to expand C-UAS from. With the largest budget for C-UAS technology development, the DoD will maintain its current position as the industry leader for C-UAS in the US.
C-UAS and the General Public
As the commercial and private use of drones and other UAS systems continues to grow, systems to limit their use will inevitably see use to limit the areas in which they can fly. With several forms of non-kinetic C-UAS technology emerging, the author predicts that the general public will soon be able to own and operate these systems once Congress has formalized further authorizations allowing the FAA to regulate C-UAS use. General safety for the public is paramount when considering using C-UAS technology in the public domain. The three emerging technologies discussed, I feel, have the greatest potential to serve the public safely and effectively. Large open-air vendors and correctional institutions are two of the many organizations along with private citizens who could use these types of C-UAS systems. They will be able to maintain their privacy and security while not inadvertently harming bystanders or creating collateral damage in the general area around them.
Conclusion(s)
The literature collected shows the growing need for C-UAS for national defense, civil defense and private property protection market(s). The only limiting factors appear to be the lack of government regulation. Once the FAA has identified and recommended to Congress C-UAS standard operating procedures and best practices, stemming from HR 302, Congress will then create legislation that will help guide the C-UAS industry in developing new and better technology for civil use. Outside of the DOD, private industry has recognized the growing need for C-UAS and has already developed technologies that allow for the safe removal of drones from private airspace. Once the regulations are in place, the C-UAS industry is ready to grow exponentially.
The rapid pace of UAS development will soon introduce larger UAS to the public airspace. This will further drive the need to develop systems that can counter / deter there use for nefarious reasons. Large UAS will be able to inflict more severe damage to varying degrees of structures and venues if they are repurposed or digitally hi-jacked. Currently the only way to combat large UAS is using kinetic means which is only operated by the DoD and is in very sparse location across the country. As this sector grows, so too will the need for larger and more integrated systems across the US.
Counter-UAS will continue to grow exponentially to match the capabilities of the UAS industry. This growth will be bolstered once Congress and the FAA formalize procedures and operating parameters for these systems.
Bibliography
115th-congress. (2018). 115th Congress. (2018). HR 302 FAA Reauthorization Act. Sec 364 and 365. Retrieved from www.congress.gov/bill/115th-congress/house-bill/302/text : https://www.congress.gov/bill/115th-congress/house-bill/302/text
49 U.S. Code § 40103, 49 U.S. Code § 40103 Sovereignty and use of airspace (U.S. Code July 5, 1994).
Abramson, E. (2016). Ethical Dilemmas in the Age of AI. Retrieved from Abramson, E. – knowmail.me/blog: https://www.knowmail.me/blog/ethical-dilemmas-age-ai/
Adamy, D. -0. (2015). EW 104 EW against a New Generation of Threats. Boston: Artech House.
Adamy, D. (2001). EW 101 A First Course in Electronic Warfare. Boston, MA: Artech House.
Adamy, D. (2001). EW 101 A First Course in Electronic Warfare. Boston: Artech House.
Adamy, D. (2004). EW 102 A Second Course in Electronic Warfare. Boston: Artech House.
Adamy, D. (2009). EW 103 Tactical Battlefield Communications Electronic Warfare. Boston: Artech House.
Adamy, D.-9. (1998, Jan). Lesson 4: the basic link for all EW functions. (electronic warfare)(EW Reference & Source Guide). Journal of Electronic Defense, Jan 1998 Issue.
Administrator. (2015, June 15). Standing Wave and Fundamental Frequency. Retrieved from Electronics Hub: https://www.electronicshub.org/?s=fundamental+frequency
Administrator. (2019, May 17). Harmonic Frequencies. Retrieved from electronicshub.org: https://www.electronicshub.org/harmonic-frequencies/
AIA & Avascent Report. (2018, April 23). Think Bigger: Large Unmanned Systems and the Next Major Shift in Aviation. Retrieved from www.avascent.com: https://www.avascent.com/2018/02/think-bigger-large-unmanned-systems-and-the-next-major-shift-in-aviation/
Alejandro Aragon-Zavala, J. L.-R.-P. (2008). High-Altitude Platforms for Wireless Communications. Chichester, West Sussex, UK: John Wiley & Sons.
Alford, L. (2000). Cyber Warfare: Protecting Military Systems. Acquisition Review Quarterly.
Anon. (2019). Saudi Arabia grants citizenship to robot Sophia. Retrieved from dw: Saudi Arabia grants cihttps://www.dw.com/en/saudi-arabia-grants-citizenship-to-robot-sophia/a-41150856
Asimov, I. (1950). “Runaround”. I, Robot (The Isaac Asimov Collection ed.). New York City: Doubleday.
Atherton, K. D. (2019). Can the Pentagon sell Silicon Valley on AI as ethical war? . C4ISRNET.
Austin, R. (2010). “Design for Stealth”, Unmanned Aircraft Systems UAVS Design Development and Deployment. New York: John Wiley and Sons.
Brown, E. F. (Dec 2008). Airborne Communication Networks for Small Unmanned Aircraft Systems. Proc. IEEE, vol 96, no 12, pp. 2008-17.
Burch, D. (2015). RADAR for Mariners. New York: McGraw-Hill.
Cameron, J. &. (Director). (1991). Terminator 2: Judgement Day [Motion Picture].
Chapman, A. (2019, May 31). GPS Spoofing. Retrieved from Tufts University – Tech Notes 2017: https://sites.tufts.edu/eeseniordesignhandbook/files/2017/05/Red_Chapman.pdf
Cornell University Legal Information Institute. (2019, June 5). But-for test. Retrieved from law.cornell.edu: https://www.law.cornell.edu/wex/but-for_test
Cornell University Legal Information Institute. (2019, June 5). Intervening Cause. Retrieved from law.cornell.edu: https://www.law.cornell.edu/wex/intervening_cause
Cornell University Legal Information Institute. (2019, June 5). Personal Jurisdiction. Retrieved from law.cornell.edu: https://www.law.cornell.edu/wex/personal_jurisdiction
D, G. a. (2010). Broadband Communications via High Altitude Platforms. New York City, NY: John Wiley & Sons.
Daniel-Cornel TĂNĂ, S. (2018). The Impact of the Development of Maritime Autonomous Systems on the Ethics of Naval Conflicts. Annals: Series on Military Sciences(2), 118-130.
Dedrone. (2018). Correctional Facilities. Retrieved from www.dedrone.com/solutions: https://www.dedrone.com/solutions/correctional-facilities
Deloitte Center for Government Insights analysis. (2018, June 18). The future of regulation. Principles for regulating emerging technologies. Retrieved from Deloitte Insights: https://www2.deloitte.com/insights/us/en/industry/public-sector/future-of-regulation/regulating-emerging-technology.html
Dewey, D. (2017, July 14). Drone crashes into LDS temple in Utah; raises questions of airspace rules. Retrieved from eastidahonews.com: https://www.eastidahonews.com/2017/07/drone-crashes-lds-temple-utah-raises-questions-airspace-rules/
Diversity of citizenship; amount in controversy; costs, 28 U.S. Code § 1332 (United States Congress June 25, 1948).
DJI. (2019, June 5). DJI Enterprise. Retrieved from Enterprise DJI.com: https://enterprise.dji.com/civil-protection
DLSR Pros. (2019, June 3). Best Drones (UAVs) for Firefighting in 2019. Retrieved from dlsrpros.com: https://www.dslrpros.com/dslrpros-blog/best-drones-firefighting-2019/
DoD. (2018). Dictionary of Military Terms. Retrieved from JCS.Mil: http://www.jcs.mil/doctrine/dod_dictionary/
DoD. (2018). Joint Publication (JP) 3-01 Countering Air and Missile Threats. Washington, DC: DoD.
DoD-02. (2018). Information Operations (IO) in the United States. Retrieved from JP 3-13 : http://www.dtic.mil/doctrine/new_pubs/jp3_13.pdf
DoD-03. (2015). Unmanned Systems Roadmap 2013 to 2038. Retrieved from DTIC: http://www.dtic.mil/dtic/tr/fulltext/u2/a592015.pdf
Drones, Q. S. (2017, July 11). quadcopters-have-hit-the-sound-barrier/. Retrieved from quadstardrones.com: https://quadstardrones.com/2017/07/11/quadcopters-have-hit-the-sound-barrier/
EARSC. (2015). A Taxonomy for the EO Services Market: enhancing perception and performance of the EO service industry. EARSC Issue 2.
Embry Riddle Aeronautical University. (2018, June 16). ERAU Common Documents. Retrieved from ERAU: www.commons.erau.edu
Entokey, a. G. (2019, May 16). entokey.com/acoustics-and-sound-measurement/. Retrieved from entokey.com/acoustics-and-sound-measurement/: https://entokey.com/acoustics-and-sound-measurement/
ESA-ESTEC Contract 162372/02/NL/US. (September 2005). STRATOS: Stratospheric Platforms a definition study for ESA Platform, Final Report, 1-34. ESA-ESTEC .
European Union. (2019, May 2019). About the regulation and data protection. Retrieved from ec.europa.eu: https://ec.europa.eu/commission/priorities/justice-and-fundamental-rights/data-protection/2018-reform-eu-data-protection-rules_en
Federal Question, 28 U.S. Code § 1331 (United States Congress June 25, 1948).
FEMA. (2013). Lessons Learned from the Boston Marathon Bombings: Preparing for and Responding to the Attack. Retrieved from www.fema.gov: http://www.fema.gov/media-library-data/20130726-1923-25045-1176/lessons_learned_from_t
Filippo Santoni de, S. &. (2018). Meaningful Human Control over Autonomous Systems: A Philosophical Account. Frontiers in Robotics and AI. doi:10.3389/frobt.2018.00015
Fleetwood, J. (2017). Public Health, Ethics, and Autonomous Vehicles. American Journal of Public Health, 107(4), 632-537.
Fortuna, C. (2017, 12 02). Autonomous Driving Levels 0–5 + Implications. Retrieved from cleantechnica.com: https://cleantechnica.com/2017/12/02/autonomous-driving-levels-0-5-implications/
Gelfand. (2004). “Physical Concepts”, Hearing an Introduction to Psychological and Physiological Acoustics, 4th ed. New York City.
Gelfand, S. A. (2009). Essentials of Audiology, 3rd Edition. Stuttgart, DE: Thieme.
Giordano, N. (2009). College Physics: Reasoning and Relationships. New York City, NY: Cengage Learning. pp. 421–424.
Gomez, M. &. (2017). Man suspected of flying drone over 49ers, Raiders games arrested. Retrieved from securityinfowatch.com/news/12383982: www.securityinfowatch.com/news/12383982/man-suspected-of-flying-drone-over-49ers-raiders-games-arrested
Grandview. (2018). US Anti-Drone Market Size, by destructive Mitigation Size. Retrieved from Grandviewresearch.com: www.Grandviewresearch.com
Guardbaum, S. (1994). The Nature of Preemption. Cornell Law Review, 767, 771.
Harris Aerial. (2019, June 5). Carrier HX8 Sprayer Drone. Retrieved from harrisaerial.com: https://www.harrisaerial.com/carrier-hx8-sprayer/
Heinman, C. (2019). Hearing Loss Tests Patrient D v-105. Carlisle, PA: Brown Optical Hearing Aid Service.
Henderson, T. (2017). The Doppler Effect – Lesson 3, Waves. Physics tutorial. The Physics Classroom. Retrieved from Henderson, Tom (2017). “The Doppler Effect – Lesson 3, Waves”. Physics tutorial. The Physics Classroom. Retrieved September 4, 2017.: Henderson, Tom (2017). “The Doppler Effect – Lesson 3, Waves”. Physics tutorial. The Physics Classroom. Retrieved September 4, 2017.
Hern, A. (2017, 1 12). Give robots ‘personhood’ status, EU committee argues. Retrieved from The Guardian: www.theguardian.com/technology/2017/jan/12/give-robots-personhood-status-eu-committee-argues
Hubbard, R. K. (1998). Boater’s Bowditch. Camden, MA: International Marine.
Ibrahim, A. (2019). Optimization Methods for User Admissions and Radio Resource Allocation for Multicasting over High Altitude Platforms . Memorial University of Newfoundland , Canada: River Publications.
IEEE . (2017). The IEEE Global Initiative on Ethics of Autonomous and Intelligent Systems Announces New Standards Projects. Telecom Standards, 27(11), pp. 4-5. .
Jesus Gonzalo, D. L. (2018, March 15). On the Capabilities and Limitations of High Altitude Pseudo-Satellities. Progress In Aerospace Sciences, 37-56. doi:https://doi.org/10.1016/j.paerosci.2018.03.006
Johnson, O. &. (2012). Ethics: Selections from Classic and Contemporary Writers. Boston, MA: Cengage Learning.
Jones, T. (2017). International Commercial Drone Regulation and Drone Delivery Services. Santa Monica: The Rand Corporation.
Kanowitz, S. (2019, 05 15). Toward the deployment of ethical AI. Retrieved from Government Computer News. : Kanowitz, S. (2019). Toward the dephttps://gcn.com/articles/2019/05/15/ethical-ai-idc.aspx?s=gcntech_200519
Kirk, J. (2015, August 5). sounds-can-knock-drones-sky. Retrieved from www.computerworld.com.au/article/581231: https://www.computerworld.com.au/article/581231/sounds-can-knock-drones-sky/
Knight, W. (2018). Nine charts that really bring home just how fast AI is growing. MIT Technology Review .
Krasnov, V. (2017, November 08). Arm-takes wing. Retrieved from https://blog.cloudflare.com/: https://blog.cloudflare.com/
Laris, M. (2018, May 10). Stadium and Team Owners See Drones as Major Threat. Retrieved from washingtonpost.com/local/trafficandcommuting;nationalinclude: https://www.washingtonpost.com/local/trafficandcommuting;nationalinclude;/stadium-and-team-owners-see-drones-as-major-league-threat/2018/05/10/83e0b954-50ad-11e8-84a0-458a1aa9ac0a_story.html?noredirect=on&utm_term=.e6aebf20ac9a
Legal Information Institute – Cornell University. (2019, May 31). Strict Liability . Retrieved from Legal Information Institute: https://www.law.cornell.edu/wex/strict_liability
LRAD. (2019, May 189). LRAD 450XL Datasheet. Retrieved from LRADX: http://www.lradx.com/wp-context/uploads/2015/05/LRAD_datasheet_450XL.pdf
MacGregor, D. S. (2018). Colorado Causes of Action: Elements, Defenses, Remedies, and Forms. Denver: Bradford Publishing Co. .
Macnamara, T. M. (2010). Introduction to Antenna Placement & Installation. New York City, NY : John Wiley & Sons.
Mahon, J. (2012). Classical Natural Law Theory St. Thomas Aquinas (1227-1274) — the “Angelic Doctor” Lecture. Retrieved from Mahon, J. (2012). Classical Natural Law Theory St. Thomas Aquinas (1227-1274) — the Philosophy of Law. : Mahon, J. (2012). Classical Natural Law Theory St. Thomas Aquinas (1227-http://home.wlu.edu/~mahonj/PhilLawLecture1NatLaw.htm
Marbury v. Madison, 5 U.S. 137 (United States Supreme Court February 23, 1803).
Matolak, R. S. (April 2015). Initial Results for Airframe Shadowing in L-band and C-band Air -Ground Channels. Proc. Integrated Commun,, Navigation, and Surveillance Conf, (pp. pp. 1-8).
McCullogh v. Maryland, 17 U.S. 316 (United States Supreme Court March 6, 1819).
Merriam-Webster. (2019, May 17). Merriam-Webster Online Dictionary.
Merriam-Webster, Inc. (2019). Definition of Ethics. online: Merriam-Webster, Inc. Retrieved from Definition of Ethics. (2019a). Online: Merriam-Webster, Incorporated.: Definition of Ethics. (2019a). Online: Merriam-Webster, Incorporated.
Middleton, C. (2018). SAP launches ethical A.I. guidelines, expert advisory panel. Retrieved from internetofbusiness.com: Middleton, C. (2018). SAP launches ethical A.I. guidelines, expert advisory panel. Retrieved from https://internetofbusiness.com/sap-publishes-ethical-guidelines-for-a-i-forms-expert-advisory-panel/
Miller, P. C. (2018, March 27). FAA Forecasts Phenomenal Growth for UAS. Retrieved from www.uasmagazine.com/articles/1833/: http://www.uasmagazine.com/articles/1833/faa-forecasts-phenomenal-growth-for-uas-industry
Misselhorn, C. (2018). Artificial Morality. Concepts, Issues and Challenges. Society, 55(2), 161-169.
Mohorcic, D. G. (2010). Broadband Communications via High Altitude Platforms. New York City, NY: John Wiley & Sons.
Monahan, K. (2004). The Radar Book: Effective Navigation and Collision Avoidance. Anacortes, WA: Fineedge Publications.
Muspratt, A. (2018, November 22). New global drone standards proposed. Retrieved from Defence iQ: https://www.defenceiq.com/defence-technology/news/new-global-drone-standards-proposed
Goddemeir, K. D. (June 2015). Role-based Connectivity Management with Realist Air to Ground Channels for Future Applications. IEEE Vehic. Tech. Mag. Vol 10, no 2, pp. 79-85.
National Conference of State Legislatures. (2018, September 10). Current Unmanned Aircraft State Law Landscape. Retrieved from NCSL.org: http://www.ncsl.org/research/transportation/current-unmanned-aircraft-state-law-landscape.aspx
NBC Today Show. (2018, May 9). How peeping drones could be spying on you without you knowing it. Retrieved from Today.com: https://www.today.com/video/how-peeping-drones-could-be-spying-on-you-without-you-knowing-it-1229001795967
Newman, L. H. (2017, August 7). THE ARMY GROUNDS ITS DJI DRONES OVER SECURITY CONCERNS. Retrieved from WIRED: https://www.wired.com/story/army-dji-drone-ban/
News, U. T. (2019, April 21). Explosive Growth in Large UAS Operations, Predicts New Report If Regulators Think Big. Retrieved from Unmannedairspace.info: https://www.unmannedairspace.info/uncategorized/explosive-growth-large-uas-operations-predicts-new-repo
Nichols, R. K. (1996). Classical Cryptography Course Volume I / II. Laguna Hills, CA: Aegean Park Press.
Nichols, R. K. (1996). Classical Cryptography Course, Volume I. Laguna Hills, CA: Aegean Park Press.
Nichols, R. K. (2018). Unmanned Aircraft Systems (UAS) In the Cyber Domain: Protecting USA’s Advanced Air Assets. 1st Ed. Manhattan, KS: New Prairie Press.
Nichols, R. K. (2019, March 14). Hardening US Unmanned Systems Against Enemy Counter Measures. 7th Annual Unmanned Systems Summit. Alexandria, VA, USA: PPTX presentation , self.
Nichols, R. K., Mumm, H. C., Lonstein, W. D., Ryan, J. J., & and Carter, C. (2018). Unmanned Aircraft Systems (UAS) in the Cyber Domain: Protecting USA’s Advanced Air Assets. Manhattan, KS: New Prairie Press (NPP) eBooks. 21.
NIST. (September 2012). Guide for Conducting. Washington, DC: GPO.
North Carolina Department of Transportation. (2019, May 30). Law & Regulations. Retrieved from NCDOT.GOV: https://www.ncdot.gov/divisions/aviation/uas/Pages/laws-regulations.aspx
O’kane, S. (2019, March 18). Drones are Already Being Confiscated Near the Super bowl. Retrieved from The Verge.
Osseiran, A. (Dec 2014). Scenarios for 5G Mobile and Wireless communications: the vision of the METIS Project. IEEE Communications Magazine, Vol 52, no 5, pp. 26-35.
O’Sullivan, J. L. (1845). The Great Nation of Futurity. United States Magazine and Democratic Review Vol 6 Issue 23, pp. 426-430.
Perez-Pena, R. (2018, December 27). Gatwick Airport Drone: Lots of Guessing, but Not Many Answers. Retrieved from NY Times: https://www.nytimes.com/2018/12/27/world/europe/gatwick-airport-drone.html
Pierson. (2019, May 16). tuning-fork-waves-sound. Retrieved from airfreshener.club – Pierson Education: https://airfreshener.club/quotes/tuning-fork-waves-sound.html
Porter, J. D. (2019, June 8). jdporterlaw.com/intellectual-property-law/. Retrieved from jdporterlaw.com: http://www.jdporterlaw.com/intellectual-property-law/
Possel, M. (2017). Waves, motion and frequency: the Doppler effect. Einstein Online, Vol. 5. Max Planck Institute for Gravitational Physics, Potsdam, Germany.
Pricewaterhousecoopers, LLP. (2018). Skies without limits – Drones- taking the UK’s economy to new heights. London: Pricewaterhousecoopers, LLP.
PROTECTION OF CERTAIN FACILITIES AND ASSETS FROM UNMANNED AIRCRAFT, H. R. 302 (United States Congress January 3, 2018).
Proyas, A. (Director). (2004). I, Robot. In. Hollywood, CA. [Motion Picture].
Ramzy, A. &. (2008). Tainted-Baby-Milk Scandal in China. Retrieved from content.time.com/time/world/article/: http://content.time.com/time/world/article/0,8599,1841535,00.html
Randall K. Nichols and Lekkas, P. C. (2002). Wireless Security: Threats, Models, Solutions. New York City, NY: McGraw Hill.
Randall K. Nichols, D. (2018). Chapter 20 Acoustic CM & IFF Libraries V SWARMS Rev 1 05142019. In R. K. Nichols, H. C. Mumm, W. D. Lonstein, & J. S. Hood, Unmanned Aircraft Systems (UAS) in the Cyber Domain: Protecting USA’s Advanced Air Assets, 2nd ed. Manhattan, KS: NPP Press.
Randall K. Nichols, D. (2019 for publication). Unmanned Aircraft Systems in the Cyber Domain: Protecting USA’s Advanced Air Assets, 2nd ed. In H. M. Randall K. Nichols, Chapter 18 Audiology, Acoustic Countermeasures against Swarms and Building IFF Libraries (p. 2nd ed.). Manhattan, KS: For Publication, NPP.
Randall K. Nichols, J. J. (2018). Unmanned Aircraft Systems (UAS) in the Cyber Domain: Protecting USA’s Advanced Air Assets. Manhattan, KS: New Prairie Press.
Rappaport, T. (2014). Millimeter Wave Wireless Communications. New York City, NY: Prentice Hall.
Rees, M. (2019, April 9). New Counter-UAS System Utilizes AI and Machine Learning. Retrieved from Unmanned Systems News.
Ricker, D. (2017, July 1). Navigating drone laws has become a growing and lucrative legal niche. Retrieved from ABA Journal: http://www.abajournal.com/magazine/article/drone_law_attorneys
Rupprecht, J. (2017). 7 big problems with counter-drone technology (drone jammers, anti-drone guns, . Retrieved from jrupprechtlaw.com: https://jrupprechtlaw.com/drone-jammer-gun-defender-legal-problems
Said Emre Alper, Y. T. (December 2008). Compact Angular Rate Sensor System Using a Fully Decoupled Silicon-on-Glass MEMS Gyroscope. JOURNAL OF MICROELECTROMECHANICAL SYSTEMS, VOL. 17, NO. 6.
Sanchez, M. (2019, June 4). No Drones. Retrieved from Unspalsh.com: https://unsplash.com/photos/oMqswmrie4Y
Schroeder, A. (2018, February 1). Localizing Humanitarian Drones: Robotics & Disaster Response from the Maldives to Malawi. Retrieved from medium.com: https://medium.com/radiant-earth-insights/localizing-humanitarian-drones-robotics-disaster-response-from-the-maldives-to-malawi-a1f362432cb1
Signia. (2019, May 16). Signia Hearing Aids. Retrieved from Signia Hearing Aids – Hear across America: www.signiausa.com
Singer v. City of Newton, 284 F. Supp. 3d 125 (U.S. District Court Massachusetts September 21, 2017).
Son. (2015). Rocking Drones with Intentional Sound Noise. Retrieved from USINEX Symposium. 24, 881.: https://www.usenix.org/systems/files/confrence/usenixsecurity15/
Sood A.K. & Enbody, R. (2014, December 19). https://www.georgetownjournalofinternau-s-military-defense-systems-the-anatomy-of-cyber-espionage-by-chinese-hackers. Retrieved from georgetownjournalofinternationalaffairs.org/online-edition: https://www.georgetownjournalofinternationalaffairs.org/online-edition/u-s-military-defense-systems-the-anatomy-of-cyber-espionage-by-chinese-hackers
Sovereignty and use of airspace, 49 U.S. Code § 40103 (United States Congress July 5, 1994).
Staff. (2008). FINAL ACTS WRC-07. World Radiocommunication Conference. Geneva: ITU.
Staff. (2012). FINAL ACTS WRC-12. World Radiocommunication Conference. Geneva: ITU.
Staff. (2016, April 17). Equal Loudness Contours. Retrieved from Gutenberg Organization: http://central.gutenberg.org/article/WHEBN0001046687/Equal-loudness%20contour
Staff. (2019). FINAL ACTS WRC-15. World Radiocommunication Conference. Geneva.
Stone, Z. (2007, 11 7). Stone, Z. (2017). Everything You Need To Know About Sophia, The World’s First Robot Citizen. Retrieved from https://www.forbes.everything-you-need-to-know-about-sophia-the-worlds-first-robot-citizen. Retrieved from Forbes: https://www.forbes.com/sites/zarastone/2017/11/07/everything-you-need-to-know-about-sophia-the-worlds-first-robot-citizen/#1667784246fa
Studios, D. D. (2017). Boaters Ref. USA.
sUAS News. (2018, March 2). RAS Consulting & Investigations hire Jeff Parisse to offer sophisticated UAS security and surveillance services. Retrieved from suasnews.com: https://www.suasnews.com/2018/03/ras-consulting-investigations-hire-jeff-parisse-offer-sophisticated-uas-security-surveillance-services/
Sullivan-Nightingale, D. (2015). Unmanned Aerial Systems: Risks & Opportunities in the Workplace. Professional Safety, 6(3), 34-42.
Sun, W. M. (June 2015). Unmanned Aircraft Systems:Air-Ground Channel Characterization for future applications. IEEE Vehic. Tech Mag. Vol 10, No 2 , pp. 79-85.
T.C. Dozer, D. A. (2008). High Altitude Platforms for VHDR in-theater communications. IET Seminar on Military Satellite Communications Systems.
The Shepard News Team. (2018, September 12). Liteye Receives Follow-on Contract for C-AUDS – DB – Digital Battlespace. Retrieved from Aerospace, Defense and Security News and Analysis – Shephard Media, The Shepard Press, Ltd: www.shephardmedia.com/news/digidigital-battlespace/liteye-receives-follow-contract-c-auds
Toomay, J. (1982). RADAR for the Non – Specialist. London; Lifetime Learning Publications. London: Lifetime Learning Publications.
TRS, S. (2018, July 10). Tontechnik-Rechner-Sengpielaudio. Retrieved from Tontechnik-Rechner-Sengpielaudio Calculator: www.sengspielaudio.com/calculator-wavelength.htm
UAV Coach. (2019, May 30). Drone Laws in South Carolina (2019). Retrieved from UAVcoach.com: https://uavcoach.com/drone-laws-south-carolina/
United States Constitution Article VI, Sec.2 (United States of America September 17, 1787).
Uni-wuppertal. (2019, May 15). Inverse Square Law, General. Retrieved from hydrogen.physik.uni-wuppertal.de/hyperphysics/: http://hydrogen.physik.uni-wuppertal.de/hyperphysics/hyperphysics/hbase/forces/isq.html
Unmanned Airspace.info. (2019, June 17). US Market Growth Predictions for Civil Sector. Retrieved from UnmannedAirspace.info: https://www.unmannedairspace.info/counter-uas-industry-directory/
Urban, T. (2018). Teach Your Robots Well: Will Self-Taught Robots Be the End of Us? Retrieved from www.worldsciencefestival.com: Urban, T. (2018). Teach Your Robots Well: Will Self-Taught Robots Be the End of Us? Retrieved from https://www.worldsciencefestival.com/programs/teach-robots-well-will-self-taught-robots-end-us/
Usenix.org. (2019, 6 9). MEMS, Drones, & Sound Sourcing. Retrieved from Usenix.org: www.usenix.org
Wallace, R. e. (2018, April 9). Exploring Counter-UAS Operations. A Case Study of the 2017 Dominican Republic Festival Presidente. Retrieved from researchgate.net/publication/325209812: https://www.researchgate.net/publication/325209812_Exploring_Commercial_CounterUAS_Operations_A_Case_Study_of_the_2017_Dominican_Republic_Festival_Presidente
Warwick, G. (2016). Rapid Defense. Aviation Week & Space Technology, 178(9), 31.
WebFinance, Inc. (2019). Definition of Ethics. (2019b). online: Online: WebFinance, Inc.
Weise, E. (2017, August 23). could-hackers-behind-u-s-navy-collisions. Retrieved from USATODAY: https://www.ruidosonews.com/story/tech/news/2017/08/23/could-hackers-behind-u-s-navy-collisions/594107001/
Wong, C. (2017). Top Canadian researcher says AI robots deserve human rights. Retrieved from Wong, C. (2017). Top Canadian researcher says AI robots deserve human rights. Retrieveitbusiness.ca: Wong, C. (2017). Top Canadian researcher says AI robots deserve human rhttps://www.itbusiness.ca/news/top-canadian-researcher-says-ai-robots-deserve-human-rights/95730
Wordpress. (2012, 08 29). The True Sign of Intelligence. Retrieved from deepthinkings.wordpress.com: http://deepthinkings.wordpress.com/2012/08/29/the-true-sign-of-intelligence/
Wright, T. (2017, August 11). You’ve Been Warned: Keep Your Drones Away From Military Bases. Retrieved from Air & Space, Smithsonian: https://www.airspacemag.com/daily-planet/keep-your-drones-away-military-base-180964451/
Wyvern, T. (2018). National Critical Intelligence Estimate: Counter Unmanned Aircraft Systems (C-UAS) in the US. Salina, KS: KSUP.
Xiaoyang Liu, C. L. (2016). High Altitude Platform Station Network and Channel Modeling Performance Analysis. Mathematics and Computer Science. Vol. 1, No 1, pp. 10-16. doi:Xiaoyang Liu, Chao Liu, Wanping Liu, Xiaoping Zeng. High Altitude Platform Station Network and Channel Modeling Performance Analys10.11648/j.mcs.20160101.13
Zeng, R. Z. (May 2016.). Wireless communications with unmanned aerial vehicles: opportunities and challenges. IEEE Communications Magazine.vol. 54, no.5, pp. 36-42.
Yong Zeng, R. Z. (2016). Wireless Communications with Unmanned Aerial Vehicles: Opportunities and Challenges. IEEE Communications Magazine, 36-42.
Yunmonk Son, H. S. (2015, August 12-14). Rocking Drones with Intentional Sound Noise on Gyroscopic Sensors. Proc. 24th Usenix Security Symposium. Washington, DC: USENIX. Retrieved from https://www.usenix.org/conference/usenixsecurity15/technical-sessions/presentation/son
Zetter, K. (2015). So, The NSA Has An Actual SKYNET Program . WIRED Magazine(Online). . Retrieved from Zetter, K. (2015). So, The NSA Has An Actual SKYNET Program WIRED Magazine(Online).
Further Readings
Knowles, J. (2017). Technology Survey: A Sampling of Counter-UAS Systems. Journal of Electronic Defense, 40(9), 37.
Lee, C. (2018). Pentagon Exploring Counter-UAS Software. National Defense Journal, 102(775), 11.
Mason, et al. (2009). Assimilating Unmanned Aircraft Systems. Air and Space Power Journal, 23(2), 5-10, 126-127.
Nichols, Randall et. Al. (2018) Unmanned Aircraft Systems (UAS) in the Cyber Domain: Protecting USA’s Advanced Air Assets. Kansas State Polytechnic Universities Libraries.
Palmer, T. S.; Geis, J. P. (2017). Defeating Small Civilian Unmanned Aerial Systems to Maintain Air Superiority. Air & Space Power Journal, 31 (2).
Park, et al. (2018). Aerial Release of Rhinoncomimus Latipes (Coleoptera: Curculionidae) to Control Persicaria Perfoliata (Polygonaceae) Using an Unmanned Aerial System. Pest Management Science, 74 (1), 141-148.
Patterson, D. R. (2017). Defeating the Threat of Small Unmanned Aerial Systems. Air and Space Power Journal, 31(1), 15-25.
Urban, J. (2018). What is the Eye in the Sky Actually Looking at and Who is Controlling It? An International Comparative Analysis on How to Fill Cybersecurity and Privacy Gaps to Strengthen Existing U.S. Drone Laws. Federal Communications Law Journal, 70(1), 0-6.
Warwick, G. (2016). Measured Response. Aviation Week & Space Technology, 178(5), 19.

