Chapter 3: Understanding Hostile Use and Cyber-Vulnerabilities of UAS: Components, Autonomy v Automation, Sensors, SAA, SCADA and Cyber Attack Taxonomy
Student Learning Objectives
An introduction to the Problem of countering hostile use of UAS against U.S. national defense interests will be introduced. The student will be able to identify critical components of an Unmanned Aircraft System (UAS), identify potential cyber vulnerabilities and understand the taxonomy of UAS operations that may be compromised against USA interests. FAA rules and US laws lag the UAS technology growth. In this chapter, UAS critical components, sensors, and levels of self-reliance are identified. These components are viewed in terms of Sense and Avoid (SAA) and SCADA environments. These components are then incorporated -into the Cyber – Attack Taxonomy. (Nichols R.-0. , 2016)
What Is The Counter -UAS Problem?
The risk of successful terrorist attacks on USA Air Defense Systems (ADS) via UASs is greater because of improving commercial capabilities and accessibility. Advanced small drones, capable of carrying sophisticated imaging equipment and significant payloads, are readily available to the public. A range of terrorist, insurgent, criminal, corporate, and activist threat groups have demonstrated their ability to use civilian drones and gather intelligence. How does the country defend against a growing UAS threat? This is also known as the counter – UAS Problem. General James D Mattis, SECDEF summed up the Problem succinctly:
“Unmanned Aircraft are being developed with more technologically systems and capabilities. They can duplicate some of the capabilities of manned aircraft for both surveillance/ reconnaissance and attack missions. They can be small enough and / or slow enough to elude detection by standard early warning sensor systems and could pose a formidable threat to friendly forces.” (Chairman, 2012)
Operational Protection from Hostile UAS Attacks – A Helicopter View
“According to LCDR Boutros of the Navy War College, developing technologies do not paint a pleasant picture of counter – UAS problem (Boutros, Operational Protection 2015). UAS has seen a widespread proliferation among both state and non-state actors. This is a cause for concern to US Operational Commanders.” (Boutros, 2015) General James D Mattis, SECDEF concluded:
“The proliferation of low cost, tactical unmanned aerial systems demand we think about this potential threat now… we must understand the threat these systems present to our joint force and develop the tactics, techniques and procedures to counter the problem.” (Chairman, 2012) (Myer, 2013)
It can be argued from the quantity and diversity of production that China is the current leader in this technology. China is thoroughly exercising its UAS muscles in the Spratly Islands.
Over 90 countries and non-state actors have UAS technology. Many of these actors foster terrorism. “Most of the UAS systems, except for China, Russia, USA, Turkey, Saudi Arabia, and Iran inventories are low-technology, Intelligence, Surveillance, and Reconnaissance (ISR) platforms.” (Boutros, 2015) Experts believe that by 2025 China will produce over 50% of UAS systems. (Yan, 2017) China’s commercial drone market to top 9B USD by 2020. The market value would be tripled to 180 billion yuan by 2025, according to the guidelines made by the Ministry of Industry and Information Technology. The estimate was much higher than a forecast by an iResearch report last year, which said the overall market of UAVs, commonly known as drones, could reach 75 billion yuan by 2025 in China. (Yan, 2017)
Iran has supplied long range, low technology Ababil UAS weapons systems to Syria and Sudan, and to extremist groups like Hezbollah, Hamas, and ISIS. Hezbollah’s inventory is estimated at over 200 UAS, which concerns the Israeli military commanders. (Zwijnwenburg, 2014)
Joint Publication (JP) 3-01 identifies friendly assets that an adversary may attack during a campaign using UAS. A Theater Commander must plan for counter – UAS actions against air defense sites, logistics centers, and national critical infrastructure. (Boutros, 2015) “Due to their small size and unique flying signatures, many UAS are difficult to detect, identify, track, and engage with current joint air defense systems. The increasing proliferation of global UAS has exposed a critical vulnerability in the protection function of operational commanders, requiring joint efforts to include intelligence, Electronic Warfare (EW), cyber warfare, (CW) and FIRES.” (Boutros, 2015)
But UAS are not invincible. Neutralizing threats or mitigating risk includes active and passive defense methods with kinetic and non-kinetic FIRES.[1] (US DoD – JP 3-0, 2012)
Countering UAS Air Threats
Advanced UAS can carry large payloads great distances. US Predator and Global Hawk UAS, “Chinese Pterodactyl and Soring Dragon counterparts, and Iranian Ababil can carry at least 500 Kg payloads greater than 300 km.” (Boutros, 2015) “They can be armed or unarmed, with ISR payloads, communications relays, Over-The-Horizon (OTH) target acquisition, and precision strike capabilities.” (Boutros, 2015)
“Shorter range, tactical, small/micro UAS may not have the distance or payload capacity of more advanced systems, but they can impact a campaign (or US Homeland Defense) in equally serious ways. Because of their size, their heat signatures are almost nonexistent. They easily evade detection. They offer more freedom of action. They can be launched from within US air defense zones and fly to their targets in less time than it takes for a coordinated response.” (Boutros, 2015) [Nightmare alert: Imagine a swarm of UAS carrying small potent binary bomb payloads attacking a US Carrier at port less than one mile away from the UAS launch point.] The enemy can effectively balance space, time, and force (arguably frequency too). (Beaudoin, 2011) “Small UAS (sUAS) can perform short-range ISR, be outfitted with explosive charges or chemical and biological agents for aerial dispersion, or simply fly over troops or civilians to demoralize.” (Boutros, 2015) [Nightmare alert: Given the effectiveness of enemy use of IEDs in Iraq and Afghanistan, a mobile, airborne version would take the Problem to an entirely new level!] (Nichols R.-0. , 2016)
Vulnerabilities Perspective
“sUAS are vulnerable to kinetic and non-kinetic outside influence in four different areas; their link to a ground station, the ground station itself, the aircrafts various sensors, and cyber weapons.” The military recognizes the first three factors, the authors will concentrate on the fourth.
“In 2009 Iraqi insurgents successfully hacked into US Reaper drones, crashing them.” (Boutros, 2015) (Horowitz, 2014). “In September of 2011, ground control stations at Creech AFB were infected by a virus, temporarily grounding the entire UAS fleet.” (Boutros, 2015) (Hartman, 2013) UAS onboard sensors can be manipulated in many ways. “High intensity light directed at an optical sensor can blind it. GPS receivers can be cyber-spoofed, which consists of transmitting a stronger, but false, GPS signal to a receiver, resulting in inaccurate navigation. Influencing the local magnetic field can have adverse effects on both onboard hard drives and sensors that require magnetic orientation to operate correctly.” (Boutros, 2015) (Hartman, 2013) The object is to better understand UAS subsystems, to facilitate exploiting their weaknesses.
The author’s contention is that: The hostile technology of remote-controlled warfare is difficult to control or abort; the best defense (counter – UAS) is to address the root drivers of these threats. The threat- roots are SAA and SCADA. Chapter 3 UAS landscape includes automation, collaboration, conventional vulnerabilities and countermeasures, commercial UAS primer, SAA Attack / Defense (A/D) A/D Issues and SCADA vulnerabilities.
Conventional Vulnerabilities of Air Defense Systems (ADS), Attacks By sUAS and Countermeasures
A simplified, non-classified view of the US Air Defense System (ADS) against a hostile UAS attack occurs in two stages:
- Early Detection and Identification of “Danger Close” (Myer, 2013)[2]
- Applied appropriate countermeasures with secondary goal of restricted collateral damage.
The traditional ADS family of tools for Detection include:
- Active Radar Surveillance – generate waves, use rebound echoes on UAS to locate, estimate distance, approach speed, size, penetration vector and short-term trajectory, and
- Passive Monitoring – covers electromagnetic spectrum via visible, thermal infrared, radio waves on common communications channels.
When considering hostile UAS defense planners need to consider several issues. The US ADS is optimized for missiles and aircraft deployed at high altitude and speeds. ADS data fusion (detection, identification, weapon lock-on, execute countermeasures) works better with larger targets, not very small ones like UAS / sUAS. US ADS is effectively reactive for longer ranges. Close reactive engagements are sub-optimal. US ADS are not optimal for sUAS /UAS. (Nichols R.-0. , 2016)
There are clear vulnerabilities of the US ADS to UAS:
- “sUAS can be launched into action close to target(s), less than 1 mile.
- sUAS exhibit a small Radar signature. The detection phase is hindered.
- Reactive dictates quick response near target. This is not always possible.
- sUAS / UAS are designed for slow, low flight. Low flying sUAS avoids Radar identification.
- sUAS / UAS electric motors are both quiet and have limited thermal signature. This makes for difficult detection for noise.
- sUAS /UAS operate in urban areas. Urban sphere presents additional problems and potential collateral damage.” (Nichols R.-0. , 2016)
Conventional Countermeasures Against sUAS /UAS:
There are two families of conventional countermeasures used to disrupt /destroy hostile UAS/sUAS systems (Regulatory ~ locked in firmware GPS No-Fly Zones, Registration, FAA rules excluded).
Active Measures – Designed to incapacitate, destroy the sUAS/UAS threat in a direct way (Ground-to- Air Defense (GTA), missiles or, acoustical gun, or simple cyber rifle)
However, there are some defensive issues to be considered:
- GTA efficiency against sUAS, reactive targets is reduced, even less efficient in urban zones where public at risk.
- Simultaneous attacks on multiple fronts (See Team or Swarm formats, Tables 3-1 and 3-2) very difficult to apply and defense measures are mitigated.
UAS countermeasures research are improving. The goal is to increase ability of GTA to react and improve capabilities to a defined to a saturation limit. Team formation allows decoys and shields. Swarm formation is easier to detect. Arrival of a cloud of robot drones is hard to mask, but tough to neutralize. Commercial company Liteye has developed an Anti-UAV Defense System (AUDS) which are able to detect, track, and disrupt sUAS operation by pulsed, brief focused broadcast of direction frequency jamming. Liteye has also developed a mobile version call M-AUDS. (Liteye, 2018) China has developed a “5-sec” laser weapon to shoot down sUAS at low altitude (500 m) with a 10KW high energy laser beam. Its range is 1.2 mi and handles sUAS speeds up to 112 mph. (Nichols R.-0. , 2016)
Passive – Designed to protect indirectly; physical protections around target, decoys, shields, organized roadblocks, nets, jamming of sensors of the aggressor, GPS total or partial cyber-Spoof of signals. Passive countermeasures have some positive outcomes. Decoys can be effective if the ADS knows what the sensors employed for sUAS Kamikaze attack and how they are used in the SAA subsystem. Communication jamming is effective against level 1 & 2 drones (Table 3-1) which require pilot interaction. It can disrupt inter–drone communications required for either team or swarm formations. Sensor Jamming – especially GPS signals – giving false GPS information, camera/gimbal dislocation, and heading sensor demagnetization is effective regardless of automation.
The 2011 Iranian incident taught US ADS planner’s lessons about passive spoofing waypoints and Loss of Signal (LOS) via GPS. LOS is an emergency condition. sUAS/UAS have programmed responses. One of those responses may be,” return to waypoint”. Two types of spoofs were executed. A complete spoof uses the friendly SAA to estimate course, ground-speed, time to target to force a LOS and final waypoint change. A partial spoof reports false positions, during LOS and changes waypoints for perceived emergency conditions. Both spoofs are difficult to detect & effective (Editor, 2012)
Aggressor Counter-Countermeasures Specific to UAS Deployment – Swarm
The authors contend that a UAS swarm attack is practically unstoppable unless the defender (US ADS) exhibits strong collaboration and ability to match/identify the SWARM locations in a timely matter. This requires combined active & passive measures. This portends the ADS computer networks must process, detect, identify, and target information (and make critical decisions) significantly faster and more effectively than their enemies. Cost is an additional vulnerability factor. Swarms can be assembled, delivered, and targeted in a relatively inexpensive weapons package. A swarm can use local counter jamming on target nets. (Nichols R.-0. , 2016) The subjects of SWARM research, tactics and defenses, will be examined in later chapters.
Autonomy vs. Automation
Table 3-1 shows the normal five levels of automation that characterize UAS systems with examples of commercial vehicles. NASA presents a more detailed level of automation breakdown based on the OODA (Observe, Orient, Decide and Act) decision loops. (Barnhart, 2012) However, Table 3-1 should suffice to understand the cyber-purview. Level 1 lave and Level 2 Automated (minimal) are commonly found on UAS sold at Amazon, Walmart, and similar outlets. The pilot makes all the decisions and has complete control of flying orders. Level 3 steps up the navigation capabilities using an a priori mission plan.
Levels 4 and 5 add higher level decision making capabilities; collision avoidance without human intervention, complex mission planning in all weather conditions, expert systems intelligence without human intervention i.e. Artificial Intelligence (AI) and advanced Sense and Avoid systems (SAA). Level 5 is not commercially available; many designers are well on their way to a fully operational Level 5 UAS.
Table 3-1:
UAS Automation Scale
Level 1: Slave – assisting piloting, reaction to disturbance
Level 2: Automated – maintains its flying orders and receives higher level orders
For Levels 1 and 2 are common, require pilot intervention and continuous communication link; reasonable prices < $1500 US, small, weight < 10lbs: Drone Parrot, Quad Flyer GAUI
Level 3: Automated Navigation (a priori mission plan)
For Level 3 micro-UAS premium (< $20,000 US): Dragonfly, Microdrone Gmbh, Fly-n-Sense, Mikrokopter
Level 4: Response from contextual data Collision Avoidance (CA) (w/o human intervention)
For Level 4 minimum knowledge of surrounding environment, reacts to events, perform CA, uses active SAA, requires mission plan
Level 5: Decision-Maker (expert system) from contextual data: navigation in unknown environment, complex missions, coordination and collaboration of signals
For Level 5 AI, decision making with heavy networked computer support, perceptive sensors for space and time, complex mission in unknown environments, capable of intelligent adjustments including mission rescheduling, key word- adaptive control
Levels 4 and 5 are confined to laboratories. (Nichols R.-0. , 2016)
Table 3-2 UAS Collaboration shows four types of possible UAS collaboration. At the lower end of a threat scale is the isolated UAS or a small group of UAS. The advantages lie in a specific mission, which may be piloted or autonomous. They carry light payloads and are affordable. They are easy to assemble in the field. An example is the Raven used by US Special Forces. The disadvantage (countermeasure applied) is to identify the pilot or leader vehicle and destroy/disable it. A UAS attack team is particularly effective against divided attack targets, Level 3 allows automatic navigation, synchronized actions, and limited updated mission information. With increased team members, synchronization is not guaranteed. Disabling part of the UAS Team does not guarantee that mission failure. The real vulnerability of the UAS team is the Chief. All synchronization and updates go through the Chief. Disable/destroy the Chief and the Team is rendered useless. Determining who the Chief is critical.
Far more dangerous is the Swarm configuration especially in the higher levels of autonomous engagement. Swarms have several advantages. They are efficient based on numbers, they demonstrate emergent large group behaviors and reactions. Even not controllable or automated, they show a decentralized intelligence – think shoal of fish with evolving local rules. UAS Swarms are a highly resistant form, not changing based on survivability of members. There is no hierarchy like a team. Destroy part of the swarm and the rest will continue their mission without abatement.
The two known countermeasures are: 1) Disrupt / Change the Strategic Global View of Swarm (its only real vulnerability) and 2) force defender collaboration. (Nichols R.-0. , 2016)
China appears to be the leader in innovative UAS swarm intelligence, through the efforts of the Chinese Electronics Technology Group Corporation (CETC). (Kania, 2017)
Table 3-2 UAS Collaboration
Type 1: Isolated Individual UAS
Advantages: piloted or autonomous w/ specific mission to perform. Small, easy to assemble, affordable, light payloads.
Countermeasures: Stop, Disable or Destroy Pilot, Threat removed.
Type 2: Group of Individual UASs (Isolated with own mission but not coordinated)
Advantages: sphere of action may be different for each mission, increased numbers, and increases success of attacks by defenses saturation
Countermeasures: Stop, Disable, Discover and Deter or Destroy Pilot(s), Threat(s) may be removed.
Type 3: Team of UASs (All members assigned specialized tasks and coordinated by Chief)
Advantages: Particularly effective against divided attack targets, Level 3 allows automatic navigation, synchronized actions, but no update to mission plans based on field activities.
Disadvantages: Level 4 (w/o humans) yields surrounding reactions but may lose synchronization between team members. Level 5 permits continuous updates, communications, commando style.
Countermeasures: Stop, Disable or Destroy Team members. Determine behavior logic and intervene. Survival of team members is critical to defense actions. Threat mitigated.
Type 4: UAS Swarm (Uniform mass of undifferentiated individual’s w/o Chief at level 4 or 5)
Advantages: Efficient based on numbers, emergent large group behaviors and reactions, not controllable or automated, decentralized intelligence – think shoal of fish w/ evolving local rules; highly resistant form, not changing based on survivability of members, no hierarchy
Countermeasures: Disrupt / Change the Strategic Global View of Swarm (its only real vulnerability). Defender collaboration. (Kania, 2017)
Figure 3-1 Drone Crash into 737-700 passenger jet while landing at Mozambique

Source: Cuskelly, C. (January 6, 2017), UK Express. http://www.express.co.uk/travel/articles/751165/drone-boeing-737-planecrash-Mozambique. Also See: https://youtu.be/2jzx8BpDuHE
Commercial Small Unmanned Aircraft Systems (sUAS) Overview
There is a natural tendency to think that small unmanned aircraft systems present no threat, especially to US defenses. They are simply recreational or commercial toys. But they present a threat to National Airspace (NAS) – especially near airports. Figure 3-1 shows the results of a sUAS crashing into a jetliner in 2016.
USA FAA Part 107 special rule forbids use of sUAS within a five-mile radius of an airport. (FAA, 2018)
Table 3-3 shows some of the available options and each year more capabilities are being added. Imaging, camera capabilities, weather-proofing, and payloads all can be used to gather intelligence, provide reconnaissance or deliver a lethal payload. They are radar resistant and deploy with a very small heat signature, so they can be in close target quickly, before defenders can activate countermeasures.
Table 3-3 Commercial sUAS Parameters
- “Flying Characteristics Available as RTF (off-the-shelf Ready to Fly); BNF (Bind and Fly –with custom transmitter); PNF (Plug and Fly with custom transmitter, receiver, battery, and charger). RTF and BNF – no prior flight experience required.
- Models most rotary multicopter – quad (4), hexa (6) octo (8) variants. Fixed wing used for deployments in agriculture, public safety, emergency response and ISR (Intelligence, Surveillance, and Reconnaissance) many fully customizable to achieve specific capabilities, flight time, payload capacity, programmable flight, maximum speed and weather hardening.
- Average SUAS flight time 18 minutes, average range approximately one mile, cost $600 US, dry conditions” (Angelov, 2012)
“Specifications affecting hostile UAS operations
- Payload capacity function (weight and size more than gimbal, camera, battery) LIDAR or infrared or experimental sensors require larger capacity and subject to easier detection.
- Range function (signal transmission, LOS, image relay distance, battery and power constraints).
- Weather Proofing function (limited operating conditions, mostly dry. Upgradable to near military grade to operate in extreme conditions) Retrofit to harden for weather is a trade-off for weight, cost, flight time and payload capacity unless no of rotors increases.
- Imaging function (available medium –high resolution cameras of > 12 megapixels, with still and video) Infrared and LIDAR installable.
- Automated and Programmable Pilot / Follow Me settings function (predetermined flight mission path based on GPS coordinates (Fly-by-wire). Some with Follow Me autopilot settings enable the SUAS to automatically follow the operator.” (Angelov, 2012)
Airborne Sensing Systems
There are two technologies available for airborne sensing of other aircraft; cooperative and non-cooperative. Cooperative technologies receive radio signals from other aircraft’s onboard equipment. Two requirements for cooperative behavior. First ATC Transponder, which responds to ground-based secondary radar interrogations for air traffic control (ATC) usage. Traffic Alert Collision Avoidance System (TCAS) uses the same technology in FAA classes of airspace. Second is the Automatic Dependent Surveillance – Broadcast systems (ADS-B). ADS-B technology uses the Global Positioning System (GPS) or alternative navigational source to make broadcasts of its own aircraft position, velocity, and data required to avoid collisions. (Angelov, 2012) Table 3-4 shows typical sensor coordinate systems. The first three cooperate with each other, the latter five are non-cooperative technologies. (Angelov, 2012)
Table 3-4 Typical Sensor Coordinate Systems
| Sensor Technology | Coordinate System |
| Active interrogation of Mode A/C transponder | Relative range, altitude |
| TCAS | Relative range, altitude |
| ADS-B | Latitude, longitude, altitude, velocity |
| Electro-Optical | Bearing (azimuth and elevation) |
| Laser /LIDAR | Relative range |
| Onboard radar | Relative range, Bearing (azimuth & and elevation) |
| Ground-based radar | Range and bearing from ground-reference |
| Acoustic | Bearing |
Sensor Parameters
Sensor technologies use standard parameters to provide a basis for comparison and ISR performance. Table 3-5 Standard Sensor Parameters shows the base set:
| Table 3-5 Standard Sensor Parameters |
|
| Sensor |
Function |
| “Field of View | Describes angular sector within sensor making measurements. Outside this field of view, sensor is blind. |
| Range | Distance measured by sensor, within which some good probability of detection of targets |
| Update Rate | Interval at which sensor provides measurements |
| Accuracy | Uncertainty of position measurement – usually single dimension |
| Integrity | probability that measurement falls beyond some normal operation limit |
| Data Elements | Cooperative sensors – specific data to enhance ISR platform, ex: trajectory, identity, intent” (Angelov, 2012) |
SAA Critical Control Systems include circuitry to affect UAS movement, landing, control of direction, detection, and correction of the aircraft. Many of these functions are incorporated into a UAS Autopilot, if capable.
Autopilot
Table 3-6 shows the common components found in UAS autopilots. These provide the means for UAS to affect movement, control, communications, detection, emergency operations, battery, waypoint delivery, and payloads.
Table 3-6 Common components found in UAS autopilots
-
-
- “Main Program/Processor: processing sensor data & implementation of control of UAV
- Magnetometer: measuring direction
- GPS: determine global position
- Airspeed/Altimeter: measure air speed & altitude
- UAV Wireless Communication: communicating with ground station
- Power System: provides power to UAV
- Inertial Measurement Unit: measures movement of UAV
- Boot Loader Reset Switch: loads programs into main program board
- Actuators: receives commands from main processing board & moves control surfaces
- Manual Flight Control: overrides autopilot & gives control of UAV control surfaces to ground station” (Clothier R. R., 2011) (Boutros, 2015)
-
(Clothier R. F., 2010) describes an ambitious SAA scientific research project involving multiple vendors, research teams, multiple aircraft, control stations, global communications and payloads known as the Smart Skies project. (Clothier R. F., 2010) Table 3-7 shows just a few of the SAA technologies that Smart Skies employed.
Table 3-7 SAA systems include (Smart Skies Project)
-
-
- “Low Cost Scout UAV Acoustic System (LOSAS)
- Passive Acoustic Non-Cooperative Collision-Alert System (PANCAS)
- Beyond Line of Sight Combat Identification (BLOS)
- Optical Collision Avoidance
- Common Control System
- Conventional Surveillance: Radar & Beacon Transmitters
- Acoustic Sensing
- Radio Emission Sensing
- Electro-Optical Sensing (EO)
-
(Clothier R. F., 2010)
SAA Subsystems
The purpose of a Sense and Avoid systems (SAA) function is replace a human pilot, to detect and resolve certain hazards of flight. “These hazards consist traffic or objects presenting a risk of collision. Air traffic includes anything that flies. Other hazards include terrain and obstacles (buildings, towers, power lines.) Aircraft preservation is not the primary reason for SAA. SAA must operate in emergency and diversionary events as well as throughout normal operations.” (Angelov, 2012)
The main components of SAA configurations are the aircraft and systems onboard, the off-board control station, and the communication link(s) between these. The key distinctions are:
- “Whether the SAA surveillance system consists of sensors located onboard the aircraft, off-board, or both, and
- Whether the SAA decisions are made at the off-board control station or onboard the aircraft by its automation.”
In both cases, there is volume of air above the ground stations in which the UAS flies. (See Figure 3-2) “In one configuration, all decisions are made on the ground. In another configuration, sensors and decisions are located aboard the aircraft, the ground station is monitor, and depending on the level of autonomy” (Table 3-1 above) the UAS detects targets, declares threats and selects maneuvers. In yet another configuration example, “sensors are located onboard or ground, but threat and maneuver decisions (human) are made via the ground station and communicated via communication links to the UAS.” (Angelov, 2012)
SAA Services and Sub-Functions
The SAA function supplies two services. These are:
- A Self-separation service to act BEFORE a collisions avoidance maneuver is needed, and could support earlier, gentler maneuvers, and
- “The collision avoidance service that attempts to protect a small collision zone and usually is achieved by means of a late, aggressive maneuver” (Angelov, 2012)(see Figure 3-2 Self -Separation and Collision Volume). (Angelov, 2012)
To achieve these services, the following list of SAA design sub-functions is required:
- “Detect – various hazards and objects such as other aircraft, weather, terrain
- Track – detected motion of object, determination of position and trajectory
- Evaluate – tracked objects, against criteria that would need a SAA maneuver
- Prioritize – tracked objects based on evaluation and tests performed
- Declare – that paths of object and own aircraft reach a point of decision for movement
- Determine – specific maneuver based on geometry of encounter
- Command – own aircraft to perform maneuver
- Execute – commanded maneuver” (Angelov, 2012)
Figure 3-2 Self -Separation and Collision Volume
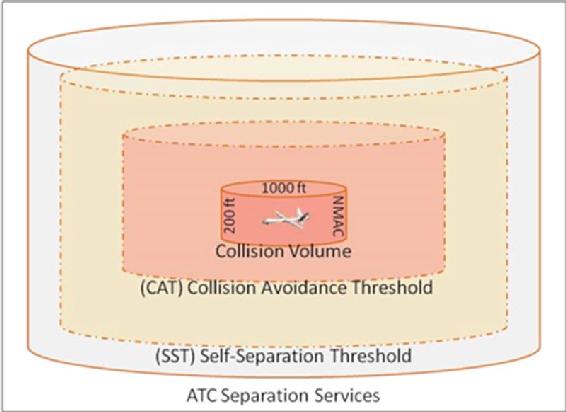
Source: Angelov, P. (2012). Sense and avoid in UAS research and applications. Hoboken: NJ.
Figure 3-3 shows the process of decisions required when two or more aircraft or UAS are on collision courses. (Yu, 2015)
Figure 3-3 Decision Process to Avoid Collision of Two Aircraft
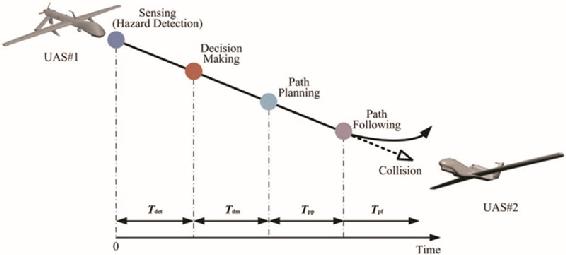
Source: Yu, X. (2015). Sense and avoid technologies with applications to unmanned aircraft systems: Review and prospects. Progress in Aerospace Sciences, 74, 152-166.
Low Hanging Fruit
Many textbooks detail UAS SAA systems ad nauseum. Angelov’s Sense and Avoid in UAS is by far the best. The reader is directed to it as the aviation source. (Angelov, 2012) What makes the present book unique is its concentration on hostile UAS activities and speculative cyber -vulnerabilities and attacks on the US ADS. The security fault “low hanging fruit” in UAS systems is SCADA.
SCADA
There are hundreds of millions of SCADA systems. They are used to control every practical machine you can imagine. SCADA stands for Supervisory Control and Data Acquisition. SCADA started in the 1940’s to control manufacturing processes such as flow rates, temperatures, valves, pressure, density, chemical, mechanical processes of all kinds. See Figure 3-4 for Legacy SCADA system for Chemical Plant. (Nichols R., Nov 28-30, 2006)
SCADA systems have improved significantly over the decades in all areas except one – SECURITY. SCADA systems are a security sieve. Figures 3-4 and 3-5 show examples of SCADA Architectures. (Nichols R., Nov 28-30, 2006) An interesting example are the automated/computerized systems in modern cars.
Figure 3-4 for Legacy SCADA system for Chemical Plant.
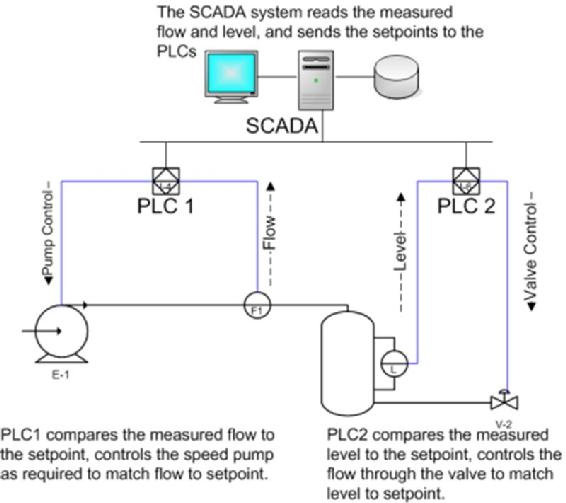
Source: Nichols, R.-0. (2016, March 29). NCIE UAS SAA Final Rev 4. 2016 INFOWARCON conference presentation April 4-7, Nichols, R.K. et. al. (3-29-2016) Presentation to INFOWARCON April 4-7 on NCIE UAS SAA Final Rev 4, presented to 2016 INFOWARCON conference, Memphis TN. Available as PPTx presentation download from author or in CANVAS. Memphis, TN, USA: INFOWARCON16
Everything is controlled by SCADA; tires, engine, seat belts, safety bags, oil pressure, even door locks. However, cyber hackers can exploit SCADA to disable a car remotely, with the driver still in it! Greenburg, Wired (2015). Hackers Remotely Kill a Jeep on the Highway—With Me in It. (Greenburg, 2015)
“UAS ARE JUST FLYING SCADA MACHINES!” (Nichols R.-0. , 2016) Table 3-8 SCADA shows the principle functions that apply to all SCADA systems, especially UAS.
Table 3-8 SCADA
-
-
- Supervisory Control and Data Acquisition (SCADA) systems facilitate management with remote access to real-time data
- Channel to issue automated or operator-driven supervisory commands to remote station control devices
- A human–machine interface (HMI) is responsible for data presentation to human operator
- Composed by a console that makes it possible to monitor & control process
- Remote terminal units (RTUs) are microprocessor-controlled electronic devices that interface sensors to SCADA by transmitting telemetry data
- Is a process control system for computerized real-time monitoring and control?
- Typically consists of:
- Master Control Unit (MCU)
- Remote Terminal Unit (s) (RTU)
- Communication Links
- Supervisory system is responsible for:
- Data acquisition
- Control activities on process
- Programmable logic controllers (PLCs) are final actuators used as field devices
- Communication infrastructure connecting supervisory system to RTUs
- Various process & analytical instrumentation
- RTU’s Alarm Systems
- Doors
- Battery Backup
- Low Power/Loss of Power Alarm
- Power Protection
- Passwords for Keypads, PC ports
- Log Alarm (or Event) When Local User Plugs PC in or Signs On
- Log Event when Local User Changes Values
- Supervisory Control and Data Acquisition (SCADA) systems facilitate management with remote access to real-time data
-
Figure 3-5 for Corporate SCADA system
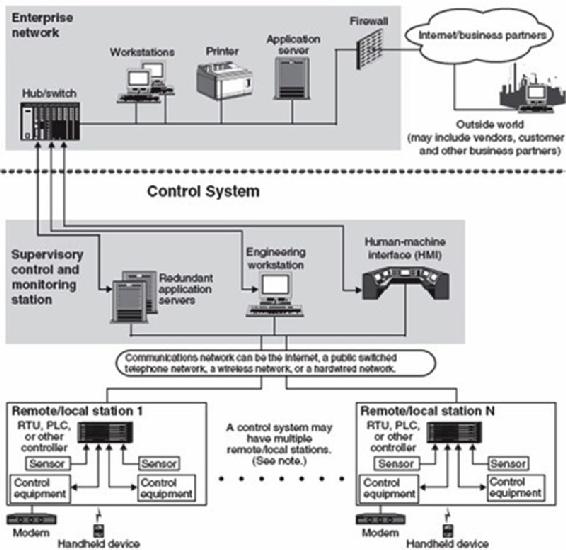
Source: Nichols, R.-0. (2016, March 29). NCIE UAS SAA Final Rev 4. 2016 INFOWARCON conference presentation April 4-7, Nichols, R.K. et. al. (3-29-2016) Presentation to INFOWARCON April 4-7 on NCIE UAS SAA Final Rev 4, presented to 2016 INFOWARCON conference, Memphis TN. Available as PPTx presentation download from author or in CANVAS. Memphis, TN, USA: INFOWARCON16
Figure 3-6 UAS SCADA System Internals
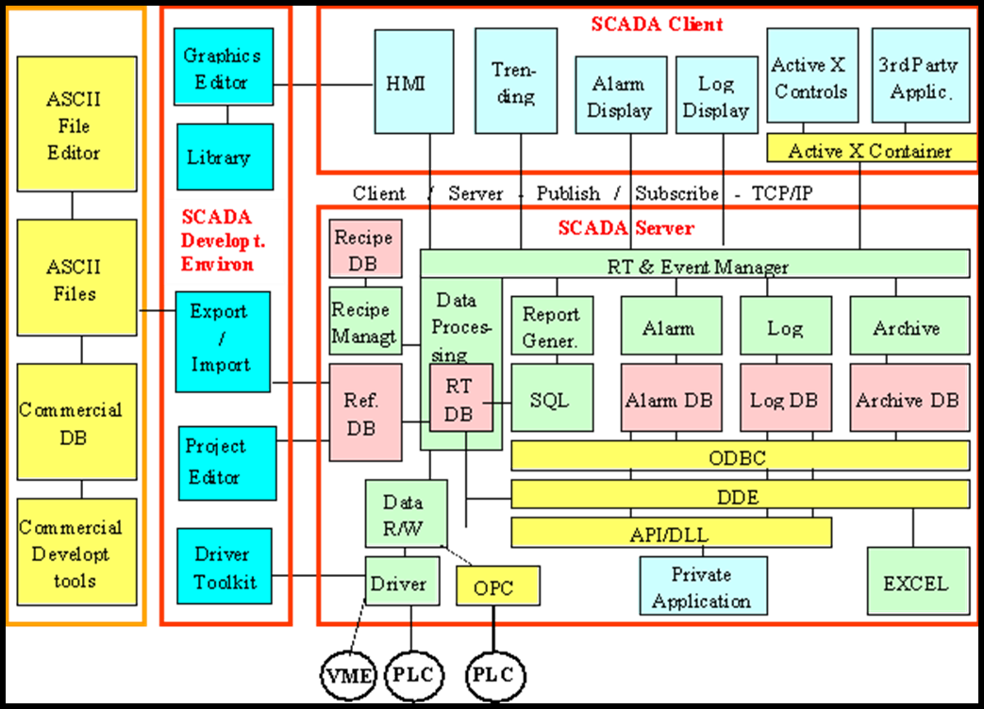
Source: Nichols, R.-0. (2016, March 29). NCIE UAS SAA Final Rev 4. 2016 INFOWARCON conference presentation April 4-7, Nichols, R.K. et. al. (3-29-2016) Presentation to INFOWARCON April 4-7 on NCIE UAS SAA Final Rev 4, presented to 2016 INFOWARCON conference, Memphis TN. Available as PPTx presentation download from author or in CANVAS. Memphis, TN, USA: INFOWARCON16.
Table 3-9 SCADA shows the principle functions that apply to all SCADA systems, especially UAS.
Table 3-9 SCADA Functions
-
-
- Supervisory Control and Data Acquisition (SCADA) systems facilitate management with remote access to real-time data
-
- Channel to issue automated or operator-driven supervisory commands to remote station control devices
-
- A human–machine interface (HMI) is responsible for data presentation to human operator
- Composed by a console that makes it possible to monitor & control process
- Remote terminal units (RTUs) are microprocessor-controlled electronic devices that interface sensors to SCADA by transmitting telemetry data
-
- Is a process control system for computerized real-time monitoring and control
- Typically consists of:
- Master Control Unit (MCU)
- Remote Terminal Unit (s) (RTU)
- Communication Links
- Supervisory system is responsible for:
- Data acquisition
- Control activities on process
- Programmable logic controllers (PLCs) are final actuators used as field devices
- Communication infrastructure connecting supervisory system to RTUs
- Various process & analytical instrumentation
- RTU’s Alarm Systems
- Doors
- Battery Backup
- Low Power/Loss of Power Alarm
- Power Protection
- Passwords for Keypads, PC ports
- Log Alarm (or Event) When Local User Plugs PC in or Signs On
- Log Event when Local User Changes Values
- Supervisory Control and Data Acquisition (SCADA) systems facilitate management with remote access to real-time data
-
SCADA systems have plenty of cyber related vulnerabilities. Most are connected to computers. Those vulnerabilities multiply when connected to the Internet. SCADA systems differ from the IT structures. See Figure 3-7. (Shapiro, 2006) Table 3-10 Sample SCADA Design Vulnerabilities apply to all systems including UAS. (Nichols R. , Nov 28-30, 2006)There are so many design flaws and vulnerabilities in SCADA systems that the US government has a special SCADA testing lab in Utah and has published copious recommendations to improve security. (NTSB, 2009)
Figure 3-7 IT Systems Vs Control Systems (Kilman, 2003)

Source: Kilman, D. & Stamp, J. (2003), CT: Framework for SCADA Security Policy. Albuquerque, NM: Sandia National Laboratories. Retrieved from Energy.gov: https://www.energy.gov/sites/prod/files/Framework for SCADA Security Policy.pdf
Table 3-10 Examples of SCADA Design Vulnerabilities
-
-
- “Ease of operation outweighs security
- Commonly set up on operating systems with known vulnerabilities
- Poor authentication systems in place
- Remote access allowed for maintenance &/or IT support
- Interconnectivity to vulnerable corporate networks
- Weak access control lists on firewalls
- Proper Network Access Control (NAC) is most crucial to prevent unauthorized connection within network
- First target of compromise for an attacker
- No use of standard IT defense software
- Wireless technology common
- System connect to unsecured remote processors
- SCADA software not designed with robust security features
- Public information often available on specific systems
- Poor physical security on remote access points
- No use of standard IT defense software
- Wireless technology common
- System connect to unsecured remote processors
- SCADA software not designed with robust security features
- Public information often available on specific systems
- Poor physical security on remote access points” (Kilman, 2003)
-
Attack Vectors
A brief overview of UAS Attack Vectors (by no means the exhaustive list) is demonstrated in Table 3-11. (Nichols R.-0. , 2016)
Table 3-11 Common Attack Vectors
“Common Vectors
-
-
- Backdoors & holes in network perimeter
- Protocol vulnerabilities
- Attacks on field devices through cyber means
- Database attacks
- Communications hijacking & Man-in-the-middle attacks
- Cinderella attack on time provision & synchronization
- Bogus input data to controller introduced by compromised sensors &/or exploited network link between controller & sensors
- Manipulated & misleading output data to actuators/reactors from controller due to tempered actors/reactors or compromised network link between controller & actuators
- Controller historian changes – feed forward control
- Distributed Denial of Service – missing deadlines of needed task actions
- Backdoors and holes in network perimeter
- Vulnerabilities in common protocols
- Attacks on field devices through cyber means
- Database attacks
- Communications hijacking and Man-in-the-middle attacks
- Cinderella attack on time provision and synchronization
- To a control engineer, possible attacks can be grouped into following categories:
- Bogus input data to controller introduced by compromised sensors and/or exploited network link between controller and sensors
- Manipulated and misleading output data to actuators/reactors from controller due to tempered actors/reactors or compromised network link between controller and actuators
- Controller historian
- Denial of Service – missing deadlines of needed task actions
-
Attacks on Software:
-
-
- No Privilege Separation in Embedded Operating System
- Buffer Overflow
- Structured Query Language Injection
-
Possible UAS Attack Hardware / Software
Attacks on Communication Stack
-
-
- Network Layer
- Transport Layer
- Application Layer
-
Auxiliary tools:
-
-
- Password Theft
- Wireshark
- Man-In-the-Middle Attacks
- Trojan Horse Virus
- Distributed Denial of Service Attacks” (Nichols R.-0. , 2016)
-
Cyber – Attack Taxonomy
UAS SCADA systems susceptible to a broad range of cyber and network specific attacks on the SAA modules in the aircraft and communication structures from the ground or satellite links. These represent system threats and vulnerabilities of the UAS structure, increasing the risk of hostile use or takeover. (Nichols R. , Nov 28-30, 2006)A UAS Cyber Attack Taxonomy is an organized view of potential cyber threats to UAS assets. The Taxonomy is a list of agents that increase risk of a successful attack on US UAS ADS assets. Remember the authors’ contention, the risk of success of terrorist attacks on USA Air Defense Systems (ADS) via UASs is higher because of improving commercial capabilities and accessibility.
A qualitative view of information risk (also a measure of cyber-attack lethality) in a system such as SAA or computer network is expressed as:
Risk = (Threats x Vulnerabilities x Impact / Countermeasures) Eq. 3-1
And at time state 0, this equation can be reduced to
Risk = function (Threats / Countermeasures) Eq. 3-2
(Nichols R.-0. , 2016)
At time state =0, where Vulnerabilities & Impact are constants and drop out of the equation.
Threats are real, and if applied in the absence of appropriate countermeasures, will increase the likelihood of a successful cyber-attack. Vulnerabilities are weaknesses in the system that a threat may or may not exploit. Vulnerabilities essentially in the system, ab initio. Threats can be mitigated or improved based on the attack circumstances. Impact is an after-the-fact accounting of the cyber-attack. No matter what the magnitude, it is a constant. Countermeasures are a host of technologies that can be applied to mitigate threats and reduce Risk. Increased Threats means increased Risk. Increased Countermeasures means decreased Risk. In practice, these equations require a qualitative legend to make comparable cases. Conversely, decreased threats means decreased Risk and decreased countermeasures means increased Risk. (Nichols R.-0. , 2016)Some authors use Vulnerabilities to assess Risk. (Garcia, 2006) Therefor our cyber-attack taxonomy must work for either Risk approach. There are many approaches to evaluating Risk. The authors choose the simplest approach to understand the attack vectors.
Espionage
Let us define some of its elements. First, we have espionage by foreign hackers. One of the main culprits are the Chinese who both encourage stealing state secrets have been quite successful. (Brenner, 2011) Hackers have successfully attacked U.S. Transportation Command (TRANSCOM) networks, “Stole designs for advanced U.S. weapons systems, including:
- F-35 Joint Strike Fighter,
- F/A-18 Fighter Jet,
- Patriot Missile System,
- RQ-4 Global Hawk Drones,
- P-8 Poseidon Reconnaissance Aircraft,
- UH-60 Black Hawk Helicopter,
- Littoral Combat Ship,
- Army’s Terminal High Altitude Area Defense Missile Defense System
- Navy’s Aegis Ballistic Missile Defense Program,
- compromised White House computer systems for espionage against military offices, targeting: Interoffice communication;
- Nuclear codes,
- took temporary control of National Oceanic and Atmospheric Administration’s (NOAA) weather satellites, and
- Civil Reserve Air Fleet systems by compromising computers defense contractors.” (Sood A.K. & Enbody, 2014)
Adding to our taxonomy, there are three Vulnerability classes exploited in UAS cyber-attacks: “Software-based, Insider Threats, and Hardware-based. Software and hardware vulnerabilities are result of poor coding practices and dearth of security understanding in developers. Hardcoded passwords exist because programmers prefer an effortless way for recovery purposes such as debugging. Vulnerabilities have drastic impact on security of software.” (Sood A.K. & Enbody, 2014) “Developers or programmers with malicious intent may implant computer hardware with code as part of a targeted attack. Insider threat vulnerabilities are difficult to assess due to human element involved. Multi-layer defenses are required to combat vulnerabilities in software/hardware world.” (Sood A.K. & Enbody, 2014)
Software – Based Vulnerabilities
“Military UAS defense systems deploy widely used software in their network devices: Operating systems, open source software, routers, radio frequency devices, Internet Connection Sharing (ICS) and SAA SCADA.” (Sood A.K. & Enbody, 2014) UAS ground system network software may have the standard vulnerabilities; “hardcoded passwords, backdoors in firmware, insecure protocols, Remote Command Execution (RCE), default passwords for Human-Machine Interfaces (HMIs), Insecure authentication and authorization, malicious hardware, critical infrastructure systems have hardcoded passwords embedded in firmware which may allow attackers to gain complete access to system.” (Sood A.K. & Enbody, 2014) It doesn’t end there. Other software-based vulnerabilities: “Backdoors exist for support or remote access purposes, Hardcoded passwords easily obtained by: Reverse engineering firmware, analyzing functional components,” (Sood A.K. & Enbody, 2014) Remote Code Execution (RCE) which is an attacker’s ability to execute attacker’s commands on target machine or target process remotely. Another RCE vulnerability is a software bug that gives attacker way to execute arbitrary code or ability to trigger arbitrary code execution from one machine on another. (Nichols R.-0. , 2016)
Unfortunately,” Remote Code Execution (RCE) can be triggered by exploiting security flaws in:
Operating system components, browsers,” ICS, SCADA, routers, Microsoft Office, Adobe Reader, and Java. Remote Code Execution (RCE) is a powerful threat to UAS and supporting computer systems. “Attackers exploit security issues; buffer overflows (stack, heap, integer), use-after free errors, race conditions, memory corruption, privilege escalations and dangling pointers.”
Remote Code Execution (RCE) vulnerabilities keeps growing and RCE vulnerabilities allow “attackers to execute arbitrary code on compromised systems, drive-by downloads, spear phishing attacks.” (Sood A.K. & Enbody, 2014)
ICS/SCADA is particularly vulnerable to remote code execution vulnerabilities. Another form is SQL injections, “which exploits weaknesses in web applications to allow attackers’ queries to be executed directly in backend database” and allow attackers to extract sensitive information such as credentials, emails, critical documents, intelligence. “Data stolen using SQL injection can provide critical information for advanced UAS targeted attacks.” (Sood A.K. & Enbody, 2014)
The final group in the software- based vulnerabilities set is “insecure authentication and file uploading flaws. These allow remote attackers to access critical systems by exploiting weak authentication design and uploading malicious code or firmware. This security issue persists due to inability of systems to implement granular control through proper authentication and authorization checks. File uploading attacks exploit a system’s inability to determine type of files being uploaded on server.” (Sood A.K. & Enbody, 2014)
Insider Threat Vulnerabilities
“Insider threats involve a malicious employee or contractor that steals sensitive organizational assets or otherwise diminishes integrity of organization.” (Sood A.K. & Enbody, 2014) Insider threats may be intentional or unintentional. The outcome is the same, increased risk.
Intentional Insider Threats (IIT): is “when contractors or employees turn malicious,” their motives: revenge, personal grudge, and /or greed. Regarding Unintentional Insider Threats (UIT), “the US military defense outsources jobs to contractors, which presents a softer target than military facilities. The result is compromised contractors’ assets allows attackers to steal intelligence from military defense networks. The contractor acts as a proxy to provide entry for attacker, even though contractor has no intention to conduct spying / stealing assets.” (Sood A.K. & Enbody, 2014)
“Edward Snowden worked as a contractor for Central Intelligence Agency and NSA. Snowden leaked copious amounts of information, including information of Government Communications Headquarters (GCHQ) and National Security Agency (NSA) project, ‘Anarchist; Hacking of Israeli drone feeds; ‘The Drone Papers’ – The Intercept and Leaks regarding drone usage in Afghanistan, Yemen, and Somalia.” (Sood A.K. & Enbody, 2014)
Hardware-based Vulnerabilities
The US sometimes picks the wrong vendors to supply its UAS critical hardware. Hardware imported from China includes backdoor access to hardware after deployment. “Exported Chinese manufacturing units compromised military-grade FPGA computer chips, circuits, and counterfeit devices, such as scanners.” “Zombie Zero malware has been implanted in software of scanner hardware manufactured in China as part of attack targeting shipping and logistics industries, especially printers. When scanners are connected to networks they provide platforms for compromising networks. Counterfeit devices and circuits developed in China for U.S. military and defense contractors to be used in warships, missiles, airplanes and
UAS.” (Sood A.K. & Enbody, 2014) (Threat to all nations that receive hardware preinstalled with malware.) (Nichols R.-0. , 2016)
“Hardware based vulnerabilities observed in actual attacks on military defense systems (Army) and applications include the following; backdoors and hardcoded passwords, compromised
GPS Satellite Communication (SATCOM) systems,” SCADA systems vulnerable to buffer overflows, and compromised GPS SATCOM systems. The Navy had its share of hardware-based threats; Remote Code Execution – “XMLDOM Zero-day vulnerability was exploited to attack U.S. Veterans of Foreign Wars’ website, SQL injections, Royal Navy website hacked, U.S. Army website hacked, insecure protocols, spoofing and hijacking and attacks to spoof GPS communication to control U.S. drones.” (Sood A.K. & Enbody, 2014)
Wireless attacks are the most generic form of hacking. “Strategies to compromise a system’s ability to be controlled by rightful owner include:
- Password Theft
- Wireshark
- Man-In-the-Middle Attacks
- Trojan Horse Virus
- Gain Scheduling
- Fuzzing
- Digital Update Rate,
- Distributed Denial of Service,
- Buffer Overflow.” (Rani, 2015)
Password cracking/theft. “Even complex passwords can be cracked using software tools such as dictionary attacks and brute force attacks”. Cracking programs are easy to obtain. “Statistical methods such as Aircrack-ng” which is a “Wired Equivalent Privacy and Wi-Fi Protected Access Pre-Shared Key cracking program is freeware.” (Rani, 2015)
Wireshark. A robust tool to analyze and capture packets for wireless networks. It provides valuable and sensitive information of transmitted packets. Wireshark allows effortless access to “client system and gain control over it.” It displays a list of available interfaces. A victim’s username and password can be obtained on a Graphical User Interface (GUI).
Another cyber-goodie is the Man-in-the-Middle (MIM) attack: “Attacker gains control of sensitive data by furtively modifying communication link between two parties. End users are usually unaware of manipulation performed by attacker.” (Rani, 2015) “Attacker forms fake connections between server and client. “Forms of MIM attacks are:
- URL manipulation
- Rogue Domain Name Server
- Address Resolution Protocol poisoning
- Duplication of Media Access Control
- False Emails” (Rani, 2015)
Trojan Horse Virus. It is malicious program or software that causes detrimental effects. It can monitor traffic over a network, damage hard drives, leverage of a security glitch, multiply/replicate like rabbits, give attacker an access to system remotely, “Trojan can continuously delete files and ultimately demolish Operating System and cannot be easily identified by anti-virus programs.” (Rani, 2015)
Gain Scheduling. A special form of cyber- attack. There are four classes: fuzzing, digital update rate, Distributed Denial of Service (DDoS), buffer overflow. “Gain scheduling is used to control non-linear UAS systems and hybrid UAS systems.” (Rani, 2015) “UAS will need different gains for control depending on states of UAS: Mass, Altitude, Speed, Flaps down.” “In a hybrid system, a system is assumed to have multiple modes of operation corresponding to take off, landing, and cruising.” “UAS will have different gains for controlling the vehicle. Control gains are often pre-computed and trusted. Gain parameters are coded into on-board autopilots. Without strict monitoring of software, an override of gains goes undetected. Changes to gains or gain scheduling logic can cause decreased performance in autopilot or instability in UAS.” (Rani, 2015) Attacker can manually override safety systems for an hour, shut down system, and take control. Not much is required; IP address of SCADA Server, path to server and then a Trojan or back door can be installed. (Nichols R.-0. , 2016)
Gain Scheduling attack methods vary depending on UAS SAA systems. “There are generally five methods of attacks:
- Sensor spoofing to cause mode confusion,
- Overriding gains through hacking,
- Infinite switching between gains, will cause loss of control,
- Causing Denial of Service (DOS) between controller gain block, and
- UAS controller block by overloading the on-board processor.” (Kim, 2012)
Fuzzing. “In UAS autopilot system, random inputs with expected distributions are not uncommon, and Gaussian noise inputs are routinely accounted for however, unexpected, invalid, or completely random inputs can cause unknown behaviors. Attacker can access any data flow between components and corrupt them with bogus values.” “Attackers use malicious fuzzing to discover SAA vulnerabilities.” Intentional white-box and black-box fuzzing tests can determine system robustness of Guidance, Navigation and Control (GNC) algorithms. Avionic and UAS programmers develop GNC for unmanned rotatory and fixed-wing aircraft. GNC algorithms are key to counter-terrorist activities and targeting High Value targets (HVT). “Consequences for a fuzzing attack: Aircraft instability, Process lock-up and/or invalid outputs to next SAA/GNC process. Common fuzzing attack methods include buffer overflow attacks, sending malicious packets with invalid payload data to UAS, and adding malicious hardware between components.” (Kim, 2012)
Digital Update Rate. UAS autopilots are digital computers. Inputs/outputs to/from the autopilot are discretized. (Zaharia, 2012) “Any continuous inputs to autopilots are converted to digital inputs through discrete sampling. If the autopilot was designed with a continuous controller, it is also converted to a discretized form. For a discretized system, as sample time increases system becomes unstable/uncontrollable. For data collection, longer sampling periods will increase probability of data aliasing.” (Kim, 2012) Hackers, knowing the above, have created a few methods cyber-attacks; “changing sampling time of analog-to-digital converters through buffer overflow, hardware manipulation and Denial of Service (DOS) or Distributed [networked] Denial of Service (DDOS) attacks that prevent processor from running controller or navigator at desired update rate.” (Kim, 2012)
Distributed Denial of Service (DDoS). “A large-scale intrusion method performed by a host source which causes detrimental effects to legitimate users by withholding services. This either causes system to shut down completely or rapidly drain system resources such as computing power and bandwidth.” (Rani, 2015) “Once attacker gains access new tools can be installed to enable control of host. Infected systems continue to look for other vulnerable systems and attack them too. Distributed Denial of Service (DDoS) attacks results in a master-slave process where affected victim is controlled by the attacker.” The attacker comes into possession of controls of many systems. “Resources of system are exhausted rapidly, and flooding of packets occurs on victim end. Attacker then removes all traces that could lead to locating the source of attack by using spoofed Internet Protocol address preventing victim to permeate illegal traffic targeted towards them.” (Rani, 2015)
The question is how is a DDoS attack initiated and how related to UAS? Think team or swarm configuration controlled at a ground-station network.
“Steps in initiating a complex DDoS attack:
Compilation of vulnerable agents
- Network first scanned for vulnerable agents for attacker to compile list of agents to attack
- Possible to attack systems by setting up automated software to scan network and take over vulnerable agents
Defuse
- Flaws in security and agent vulnerability are misused by attacker
- Software codes used to automatically attack and disband owner from controlling system
- Actions are taken by attacker to safeguard code planted from being Distributed Denial of Service (DDoS)
Connection
- Protocols such as TCP or UDP used to connect with numerous agents and plan attacks accordingly via scheduling
- Attacks can be performed on either single or multiple agents
Intrusion
- Features of victim such as port numbers are conformed
- Attacker launches attack and alters properties
- In favor of attacker since alteration of packets would lead to complications in identification of source of attack” (Rani, 2015)
“Distributed Denial of Service (DDoS) Scanning attack techniques:
- Random
- Local subnet
- Hit-list
- Permutation
- Topological
Distributed Denial of Service (DDoS) System Shutdown for at least five minutes:
-
- UAS Operations can no longer monitor or control process conditions
- SCADA locks up, must be rebooted
- When comes back on-line, locks up again
- Items Needed for DDoS:
- Ability to flood server with TCP/IP calls
- IP Address of SCADA Server
- Path to server” (Rani, 2015)
Buffer Overflow SCADA Attack. Exploiting a buffer overflow vulnerability is to overwrite some control information to modify flow of control in a program, exploiting and compromising control information to give control to the attacker’s code. It involves overwriting return address stored on stack to transfer control to code placed in buffer or past end of buffer. On hardware implementations, stack grows downwards towards lower memory addresses.
When a function is called, the address of instruction following function call is pushed onto stack, so that the function knows where to return control when it is finished. While the called function is being executed, it allocates local variables on stack, variables and buffers, allocated at lower memory addresses than return address. The process permits writes to base address of buffer plus offset to return address, overwrites value of return address.
In a buffer overflow SCADA attack, if the return address is overwritten with some arbitrary value, control will be transferred either to invalid location in memory or location that does not contain valid executable code. This results in segmentation fault. If the overflow SCADA attack
return address is overwritten in a clever manner, it can transfer control to code inserted by the attacker in a buffer overflow. Attacker can place executable code into the buffer, then overwrite return address with the address of buffer. Control will then be transferred to executable attack code contained in buffer. (Nichols R.-0. , 2016)
Control Acquisition Attack (CAA). The objective of attacker in a CAA is to assume direct control of unmanned vehicle. A proven example is to use GPS spoofing to shift flight path of UAS to suit purposes of attacker with limited control. If the attacker can gain complete control of unmanned vehicle, the possibility of a man-in-the-middle attack is promulgated. The attacker could send falsified data to original controller to make it appear that vehicle is behaving normally, when it is being controlled by attacker. CAA is undetectable attack that is especially dangerous. (Nichols R.-0. , 2016)
General Attack Possibilities
Autopilot Hardware Attack. The attacker can link directly to UAS autopilot to give control over UAS and/or tactical data. “They can corrupt data stored on-board autopilot or install extra components that corrupt data flow. Hardware attacks affect UAS survivability, control and allow tactical data to be collected. Hardware attacks can be carried out during maintenance, storage, manufacturing, and delivery phases.” (Kim, 2012)
Wireless Attack. “Attacks are carried out through wireless communication channels. They can occur if an attacker uses wireless communication channels to alter data on-board UAS autopilot. Worst case scenario is if an attacker can break encryption of communication channel. Attacker can gain full control of UAS if communication protocol is known and then can use a buffer overflow or like corrupt data onboard or initiate some event.” (Kim, 2012) Another type of attack is sensor spoofing. The attacker send false data through on-board sensors of UAS autopilot. The danger of wireless attacks they can be carried out from afar while UAS is being operated. (Nichols R.-0., 2016)
Control System Security. “Attacks that prevent hardware/CPU from normally
Include buffer overflow exploits through some input device, forced system resets to load malicious code, and hardware changes or additions to system.” (Kim, 2012)
Application Logic Security. These attacks use malicious manipulation of sensors or environment, providing false data to control system. The control system behaves as programmed without fault, but some or all inputs to system are corrupted. Attacks include sensory data manipulation
Vehicle/system component state data manipulation, navigational data manipulation, command and control data manipulation, to gain complete control over connected drone and gained access to corrupt pre-programmed flight path. Since the communication channel between ground station and flight controller of drone is based on an unsecured protocol, a hacker can easily attack and gain real-time access to drone. (Nichols R.-0. , 2016)
Conclusions
Unmanned Aircraft Systems represent some of US most advanced air assets. They are critical to the US ADS. Because they were designed on top of open communications, SCADA controlled, and interact with the Internet for ground, air, sea, and satellite support, plus use COT software/hardware, they are vulnerable to a host of cyber-attacks to control their destiny. Based on the sheer diversity and number of potential cyber weapons that can be used at every stage of the UAS mission, and the significant growth of UAS for defense purposes, the risk of hostile use against US ADS is steadily increasing. Couple this with a huge growth and sophistication in the UAS commercial technologies supporting and global sectors requiring UAS, the threat of hostile use cannot be minimized.
Discussion Topics
1) You are a terrorist. Contemplate the Risk and Success of a hostile take-over or destruction of a friendly UAS by the following four methods:
1A – Spoofing GPS satellite communication
1B – Corrupting authentication of ground station communication signals
1C – Hijacking a UAS by hacking internal ASIC chip communication
1D – ADS-B Spoofing / Jamming
What cyber tools from the Chapter 3 Cyber- Attack Taxonomy would you use to accomplish the 1A- 1D goals?
2) Discuss the cyber counter measures that could be used to terminate/disrupt/destroy a SWARM attack of fifty or more UAS on an ADS facility.
3) U.S Navy Vessel Collisions in the Pacific:
Facts:
In 2017, there were chain of incidents/collisions involving four U.S. Warships and one U.S Submarine. On 20 August, the guided-missile destroyer USS John S McCain collided with the 600-foot oil and chemical tanker Alnic MC at 0624 JST. Ten sailors died. On 17 June, the destroyer USS Fitzgerald collided with the ACX 30,000-ton container ship at 1330 JST, leaving seven dead. Records show that the ACX turned sharply right at the time of collision. The route of the destroyer is not shown on maps because commercial tracking data does not include military ships. Damage to the starboard side of the USS Fitzgerald indicates it would have been on a bearing of approximately 180 deg. (South). The captain of the Philippine-flagged container ship accused the Navy destroyer of failing to heed warning signs before the crash. On 9 May, the guided-missile cruiser USS Lake Champlain collided with a South Korean fishing boat off the Korean Peninsula. There were no injuries. On 31 January, the guided-missile cruiser USS Antietam ran aground dumping more than 1000 gallons of oil into Tokyo Bay. On 18 August, the ballistic- missile submarine, USS Louisiana collided with the Navy Offshore Support Vessel in the Strait of Juan de Fuca. No injuries.
US Navy Response
In all five incidents, the US Navy blamed their field leadership for not responding in an appropriate manner. Court marshals and relief from duty are the punishments of the day. The Navy blames funding, lack of readiness, and lack of training. Investigations and maintenance “holds” have been initiated. Reading between the lines, this response would imply that the Skipper/XO/COB and at least five watch sailors on each Naval vessel (roughly –forty to fifty personnel including bridge staff) were judged incompetent. Many US Navy careers were finished. Further, this would also imply that all five vessels radar, emergency positioning alert systems, AIS, sonar, and long-range collision avoidance equipment must have been functioning perfectly, without a catastrophic failure or interference of any kind.
OR…
The Case for a Cyber Weapon
To this researcher, there appears to be valid evidence to support the theory that at least two of the US Navy Warships above AND the commercial vessels they struck were the on the wrong end of a cyber-weapon. They were receiving wrong GPS generated positional information. The Cyber Weapon may have been deployed by UAS off a small, nearby vessel by an adversary. The author believes, that the subject cyber weapon is an advanced modular entity that can spoof the GPS signals received by all vessels in its range. Vessels given misleading data will make incorrect decisions in terms of navigation and emergency responses – potential leading to collisions and deaths.
Contemplate and comment on the viability of the researcher’s cyber-weapon theory.
Bibliography
Adamy, D. -0. (2015). EW 104 EW against a New Generation of Threats. Boston: Artech House.
Adamy, D. (2001). EW 101 A First Course in Electronic Warfare. Boston, MA: Artech House.
Adamy, D. (2009). EW 103 Tactical Battlefield Communications Electronic Warfare. Boston, MA: Artech House.
Adamy, D. L. (2004). EW 102 A Second Course in Electronic Warfare. Boston: Artech House.
Adamy, D.-9. (1998, Jan). Lesson 4: the basic link for all EW functions. (electronic warfare)(EW Reference & Source Guide). Journal of Electronic Defense, Jan 1998 Issue.
Alford, L. (2000). Cyber Warfare: Protecting Military Systems. Acquisition Review Quarterly.
Angelov, P. (2012). Sense and avoid in UAS research and applications. Hoboken: NJ.
Army, U. (1992, November 23). US Army Field Manual FM 34-40-7. Communications Jamming Handbook.
Austin, R. (2010). “Design for Stealth”, Unmanned Aircraft Systems UAVS Design Development and Deployment. New York: John Wiley and Sons.
Barker, W. (2003, August). SP 800-59 Guidelines for Identifying an Information System as a National Security System. Retrieved from NIST: https://csrc.nist.gov/publications/detail/sp/800-59/final
Barnhart, R. K. (2012). Introduction to Unmanned Aircraft Systems. New York: CRC Press.
Beaudoin, L. e. (2011). Potential Threats of UAS Swarms and the Countermeasures Need. ECIW.
Boutros, D. (2015, May 15). US Navy War College. Retrieved from Operational Protection from Unmanned Aerial Systems: http://www.dtic.mil/dtic/tr/fulltext/u2/a621067.pdf
Brenner, J. (2011). America the Vulnerable: Inside the New Threat Matrix of Digital Espionage, Crime, and Warfare. New York: Pilgrim Press.
Burch, D. (2015). RADAR for Mariners. New York: McGraw-Hill.
C4ISystems. (2013). basics-of-information-operations. Retrieved from Blogspot: http://c4isys.blogspot.com/2013/11/basics-of-information-operations-24.html
Chairman, U. (2012, March 23). Countering Air and Missile Threats, final coordination, JP 3-01. CJCS.
Clothier, R. (2017, April 02). The Smart Skies Project: Enabling Technologies for UAS Operations in Non-segregated Airspace. Retrieved from QUT ePrints: http://eprints.qut.edu.au/40465/3/40465.pdf
Clothier, R. F. (2010). The Smart Skies Project: Enabling technologies for future airspace. . Clothier, R.A., Frousheger, D., Wilson, M., (2010). The Smart Skies Project: Enabling technologies for future airspace. Australian Research Center for Aerospace Automation, Commonwealth Scientific and Industrial Research Organization, Boeing Research an. Australian Research Center for Aerospace Automation, Commonwealth Scientific and Industrial Research Organization.
Clothier, R. R. (2011). The Smart Skies project. IEEE Aerospace and Electronic Systems Magazine.
DoD. (2018). Dictionary of Military Terms. Retrieved from JCS.Mil: http://www.jcs.mil/doctrine/dod_dictionary/
DoD-01. (2018). JP 1-02. Retrieved from Department of Defense Dictionary of Military and Associated Terms: www.dtic.mil/doctrine/new_pubs/jp1_02.pdf
DoD-02. (2018). Information Operations (IO) in the United States. Retrieved from JP 3-13 : http://www.dtic.mil/doctrine/new_pubs/jp3_13.pdf
DoD-03. (2015). Unmanned Systems Roadmap 2013 to 2038. Retrieved from DTIC: http://www.dtic.mil/dtic/tr/fulltext/u2/a592015.pdf
Editor. (2012, April 22). RT Question More. Retrieved from Iran starts cloning of American spy drone: https://www.rt.com/news/iran-spy-drone-copy-667/
FAA. (2018, February 1). Part 107 Rule for sUAS. Retrieved from Fly under the Special Rule for Model Aircraft: https://www.faa.gov/uas/getting_started/model_aircraft/
Filbert, F. &. (2014, (July – August). Joint Counter Low, Slow, Small Unmanned Aircraft Systems Test. Fires PB644-14, no 4. Washington: DoD.
Fitts, R. (1980). The Strategy of Electromagnetic Conflict. Los Altos, CA: Peninsula Publishing.
Garcia, M. (2006). Vulnerability Assessment of Physical Protection Systems. Albuquerque: Sandia National Laboratories,BH.
Greenburg, H. (2015). Hackers Remotely Kill a Jeep on the Highway—With Me in It. Retrieved from Wired : https://www.wired.com/2015/07/hackers-remotely-kill-jeep-highway/
Hartman, K. a. (2013). The Vulnerability of UAVs to Cyber Attacks – An Approach to the Risk Assessment. 2013 5th International Conference on Cyber Conflict . Tallin: NATO CCD COE Publications.
Horowitz, M. C. (2014). Droning On: Explaining the Proliferation of Unmanned Aerial Vehicles. University of Pennsylvania and Texas A&M Universities. University of Pennsylvania and Texas A&M Universities.
Hubbard, R. K. (1998). Boater’s Bowditch. Camden, MA: International Marine.
Kania, E. (2017, July 6). Swarms at War: Chinese Advances in Swarm Intelligence. China Brief Volume: 17 Issue 9. China Brief Volume: 17 Issue 9.
Kilman, D. &. (2003). Framework for SCADA Security Policy. Albuquerque, NM: Sandia National Laboratories. Retrieved from Energy.gov: https://www.energy.gov/sites/prod/files/Framework%20for%20SCADA%20Security%20Policy.pdf
Kim, A. G. (2012, June). Cyber Attack Vulnerabilities Analysis for Unmanned Aerial Vehicles. Retrieved from Infotech@Aerospace.com: https://www.researchgate.net/publication/268571174_Cyber_Attack_Vulnerabilities_Analysis_for_Unmanned_Aerial_Vehicles
Liteye. (2018, August 25). AUDS. Retrieved from Liteye Corporation: http://liteye.com/products/counter-uas/auds/
Marshall, D. M. (2016). Introduction to Unmanned Aircraft Systems, 2nd Edition. New York: CRC Press.
Merrick, K. (2016). Future Internet. 10.3390/fi8030034 Review, 8(3), p. 34.
Moir, I. a. (2006). Military Avionics Systems. New York: Wiley Aerospace Series.
Monahan, K. (2004). The Radar Book: Effective Navigation and Collision Avoidance. Anacortes, WA: Fineedge Publications.
MORS. (2018). Military Operations Research Society . Retrieved from http://www.mors.org/meetings/oa_definition.htm
Myer, G. (2013, May-June). Danger Close Definition. Retrieved from US Army Magazine: www.benning.army.mil/infantry/magazine/issues/2013/May-June/Myer.html
NASA. (2018). Unmanned Aircraft Systems (UAS) Integration in the National Airspace System (NAS) Project. Retrieved from NASA: https://www.nasa.gov/feature/autonomous-systems
Nichols, R. K. (2008, September 05). Counterintelligence & Sensitive Compartmented Information Facility . (SCIF) Needs – Talking Points.
Nichols, R. (Nov 28-30, 2006). Cyber Terrorism, Critical Infrastructure, & SCADA Presentation. In R. Nichols (Ed.), Defense Threat Reduction Agency Conference. Shirlington VA: Utica College, Utica NY.
Nichols, R.-0. (2016, March 29). NCIE UAS SAA Final Rev 4. 2016 INFOWARCON conference presentation April 4-7, Nichols, R.K. et. al. (3-29-2016) Presentation to INFOWARCON April 4-7 on NCIE UAS SAA Final Rev 4, presented to 2016 INFOWARCON conference, Memphis TN. Available as PPTx presentation download from author or in CANVAS. Memphis, TN, USA: INFOWARCON16.
NTSB. (2009, September 16). National SCADA testbed Documents and Media. Retrieved from National SCADA Testbed Fact Sheet: https://www.energy.gov/sites/prod/files/oeprod/DocumentsandMedia/NSTB_Fact_Sheet_FINAL_09-16-09.pdf
Pettit, R. (1982). ECM and ECCM Techniques for Digital Communication Systems. Belmont, CA: Lifetime Learning Publications .
Rani, C. M. (2015). Security of unmanned aerial vehicle systems against cyber-physical attacks. The Journal of Defense Modeling and Simulation: Applications, Methodology, Technology.
Shapiro, J. (2006, February 14). Slideplayer.com. Retrieved from Cybersecurity: http://slideplayer.com/slide/4545982/
Singer, P. W. (2010, February 25). Will Foreign Drones One Day attack the US? . Newsweek.
Sood A.K. & Enbody, R. (2014, December 19). https://www.georgetownjournalofinternau-s-military-defense-systems-the-anatomy-of-cyber-espionage-by-chinese-hackers. Retrieved from georgetownjournalofinternationalaffairs.org/online-edition: https://www.georgetownjournalofinternationalaffairs.org/online-edition/u-s-military-defense-systems-the-anatomy-of-cyber-espionage-by-chinese-hackers
Toomay, J. (1982). RADAR for the Non – Specialist. London; Lifetime Learning Publications. London: Lifetime Learning Publications.
TRS, S. (2018, July 10). Tontechnic-Rechner-Sengpielaudio. Retrieved from Tontechnic-Rechner-Sengpielaudio Calculator: www.sengspielaudio.com/calculator-wavelength.htm
Wiley, R. G. (1993). Electronic Intelligence: The Analysis of Radar Signals, 2nd ed. Norwood, MA: Artech House.
Wilson, M. (2012). The Use of Low-Cost Mobile Radar Systems for Small UAS Sense and Avoid. Sense and Avoid in UAS Research and Applications.
Yan. (2017, December 23). China’s commercial drone market to top 9 bln USD by 2020. Retrieved from Xinhuanet: http://www.xinhuanet.com/english/2017-12/23/c_136847826.htm
Yu, X. &. (2015). Sense and avoid technologies with applications to unmanned aircraft systems: Review and prospects. Progress in Aerospace Sciences, 74, 152-166.
Zaharia, M. D. (2012). Discretized Streams: An Efficient and Fault-Tolerant Model for. Retrieved from UNIX Org: https://www.usenix.org/system/files/conference/hotcloud12/hotcloud12-final28.pdf
Zwijnwenburg, W. (2014, October 8). ZwijnwenbDrone-tocracy? Mapping the Proliferation of Unmanned Systems. Retrieved from Sustainable Security.org.
Readings
Abbot, C, Clarke, M, Hathorn, S, Hickie, S. (2016) Hostile Drones: The Hostile -Use of Drones by Non-State Actors against British Targets.
Aeronautical Decision Making (2015) (PDF) Professor Handout.
Ang, C. and Costello, M. (n.d.). When Firmware Modifications Attack: A Case Study of Embedded Exploitation. Columbia University, NY
Anonymous (n.d.). 21 Steps to Improve Cyber Security of SCADA Networks, Department of Energy.
Anonymous. (2012). Advanced Threats in the Enterprise: Finding an Evil in the Haystack with RSA ECAT (Rep.). RSA.
Anonymous, (2011). Keeping Track of Unmanned Aircraft by Overcoming “Lost Links”, MITRE.
Anonymous (2004). National Communications System Technical Information Bulletin 04-1. Supervisory Control and Data Acquisition (SCADA) Systems. Virginia, Chantilly.
Anonymous (n.d.). Unmanned Aircraft Systems: Perceptions and Potential, Arlington, VA, Aerospace Industries Association.
Anonymous, (2009). Unmanned Air Systems: The Future is Now, New York, Access Intelligence LLC.
Barnhart, R.K., Hottman, S.B, Marshall D.M., and Shappee, E. (2012) Introduction to Unmanned Aircraft Systems. New York: CRC Press.
Bartelds, T., Capra, A., Hamaza, S., Stramigioli, S., Fumagalli, M., (2015). Compliant Aerial Manipulators: Towards a New Generation of Aerial Robotic Workers, IEEE.
Beaudoin, L. et.al (2011) Potential Threats of UAS Swarms and the Countermeasures Need. European Conference on Information Warfare and Security (ECIW), Tallin, Estonia.
Birnbaum, Zackary (2012). Behavior based analytics for securing cyber-physical systems. Binghampton University.
Brenner, J. (2011) America the Vulnerable: Inside the New Threat Matrix of Digital Espionage, Crime, and Warfare. NY: Pilgrim Press.
Bristeau, P., Callou, F., Vissiere, D., and Petit, N. (2011). The Navigation and Control Technology inside the AR. Drone Micro UAV. Proceedings of the 18th IFAC World Congress, 1477-1484. Retrieved February 11, 2016.
Boutros, D.A, LCDR. (2015) Operational Protection from Unmanned Aerial Systems: Drones, UAS Proliferation, ISR Platforms, UAS Capabilities and Vulnerabilities, Current Protective Measures, Protection Shortfalls. UAS Navy War College, Newport, RI: Progressive Management Publications.
Brodsky, D. W. (2012). An Analysis of the Vulnerabilities of Unmanned Aircraft Systems to Cyber Attack. Retrieved February 13, 2016.
Bunker, R. J. (2015). Progressive Management Publications (United States, Department of Defense, U.S. Army).
Christensen, R. (1997). Effect of technology integration education on the attitudes of teachers and their students. Doctoral dissertation, Univ. of North Texas. Based on Russell, A. L. (1995) Stages in learning modern technology. Computers in Education, 25(4), 173-178.
Class Lecture [Personal interview]. Randall Nichols (2016, February 23).
Class Lecture [Personal interview]. Randall Mai (2016, February 23).
Claveau, D., (2015). Autonomous UAS Controlled by Onboard Smartphone, International Conference on Unmanned Aircraft Systems.
Compton, M.D., (2009). Improving the Quality of Service and Security of Military Networks with a Network Tasking Order Process, Wright-Patterson Air Force Base, OH, Air Force Institute of Technology.
Delves, P. and Angelov, P. (2012). Sense and Avoid in UAS: Research and Applications (2nd Edition), John Wiley and Sons.
Dekker, M. (2013). Transforming Information Security: Future-Proofing Processes (pp. 1-13, Rep.). RSA.
Derynck, R. (2004). SCADA system security threats, vulnerabilities and solutions. IEE Seminar on Developments in Control in the Water Industry.
Elkaim, G. H., Pradipta Lie, F. A., and Gebre-Egziabher, D. (2012). Principles of Guidance, Navigation and Control of UAVs [Scholarly project]. Retrieved March 11, 2016, from https://users.soe.ucsc.edu/~elkaim/Documents/UAV_GNC_chapter.pdf
Federal Aviation Administration, (2011). Unmanned Aircraft Operations in the National Airspace System, U.S. Department of Transportation, Unmanned Aircraft Systems Group.
Finke, C., Butts, J., Mills, R., and Grimalia, M. (2013). Evaluation of a Cryptographic Security Scheme for Air Traffic Control’s Next Generation Upgrade. Retrieved March 9, 2016.
Firmware [Personal interview]. Danny Mersch (2016, January 26).
Fonash, P., Schneck, P., (n.d.). Cybersecurity: From Months to Milliseconds, US Department of Homeland Security, Outlook.
Garcia, M.L. (2006) Vulnerability Assessment of Physical Protection Systems. Sandia National Laboratories. Albuquerque, NM: BH.
Gardinier, M. (2013). The Critical Incident Response Maturity Journey (Rep.). RSA.
Giancarmine, F. and Domenico, A. (2015) Radar Electo-Optical Data Fusion for non-cooperative UAS Sense and Avoid Retrieved February 6, 2016
Gowda, C. R. (2015). System Security, Threat Detection and Prevention Measures of Autonomous Systems. Retrieved February 19, 2016.
Hartman, K. and Steup, C (2013). The Vulnerability of UAVs to Cyber Attacks – An Approach to the Risk Assessment. 2013 5th International Conference on Cyber Conflict NATO CCD COE Publications, Tallinn. Retrieved February 5, 2016.
Heitner, K. (2014). Cyber Threats within Civil Aviation, Utica College. Retrieved February 17, 2016
House, Commonwealth of Virginia, (2013). Unmanned Aircraft Systems Protocols for use by Law Enforcement Agencies, Virginia Department of Criminal Justice Services.
Idaho National Laboratory, (2006). Control Systems Cyber Security: Defense in Depth Strategies, Department of Homeland Security.
Horowitz, M.C. & Fuhrmann, M. (2014) Droning On: Explaining the Proliferation of Unmanned Aerial Vehicles. University of Pennsylvania and Texas A&M Universities.
IKANOW. (2015). Managed Service Providers: The Talent and Tech to Beat Back Cyber Attacks (Rep.).
IKANOW. (2015). Threat Intelligence Ranking (Rep.).
Incze, M.L., Sideleau, S.R., Gagner, C., Pippin, C.A., (n.d.). Communication and Collaboration Among Heterogeneous Unmanned Systems Using SAE JAUS Standard Formats and Protocols, Newport, RI, Naval Undersea Warfare Center Division.
Jackson, A., (n.d.). Operational Reconnaissance and Intelligence Gathering is Critical to Battle Success, Audio Visual Innovations.
Jackson, B. A., Lostumbo, M. J., Frelingeer, D. R., and Button, R. W. (2008). Evaluating novel threats to the homeland: Unmanned aerial vehicles and cruise missiles. Santa Monica, CA: RAND National Defense Research Institute.
Jacobs, T., Coffey, J., (2015). Arctic Shield 2015 Unmanned Aircraft Systems Test Plan and Operational Assessment, NOAA UAS Program Office.
Kania, E. (6 July 2017) Swarms at War: Chinese Advances in Swarm Intelligence. China Brief Volume: 17 Issue 9. The Jamestown Foundation.
Kaspersky Lab (2015). Equation group: Questions and Answers. Retrieved February 24, 2016
Kim, A., Wampler, B., Goppert, J., Hwang, I., and Aldridge, H. (2012). Cyber Attack Vulnerabilities Analysis for Unmanned Aerial Vehicles. Infotech@Aerospace 2012. Retrieved February 13, 2016.
Kilman, D. & Stamp, J. (2003) Framework for SCADA Security Policy. Albuquerque, NM: Sandia National Laboratories. https://www.energy.gov/sites/prod/files/Framework for SCADA Security Policy.pdf
Kindervater, K.H., (2015). Lethal Surveillance: Drones and the Geo-History of Modern War, University of Minnesota.
Knapp, E. D., and Langill, J. T. (2015). About Industrial Networks. Industrial Network Security, 9-40.
Lacher, A., Zeitlin, A., Maroney, D., Markin, K., Ludwig, D., Boyd, J., (2010). Airspace Integration Alternatives for Unmanned Aircraft, the MITRE Corporation.
Ledbetter III, T., Munoz, C., (2010). Outgoing USAF Intel Chief Sees Need for More Autonomy in UAS Platforms, Arlington, Inside Washington Publishers.
Lemay, A., (2013). Defending the SCADA Network Controlling the Electrical Grid from Advanced Persistent Threats, University of Montreal.
Li, L., Heymsfield, G., Schaubert, D.H., McLinden, M.L., Creticos, J., Perrine, M., Coon, M., Cervantes, J.I., Vega, M., Guimond, S., Tian, L., Emory, A., (2016). The NASA High-Altitude Imaging Wind and Rain Airborne Profiler, IEEE.
Loukas, G., Gan, D., Vuong, T., (2013). A Review of Cyber Threats and Defense Approaches in Emergency Management, London, UK, University of Greenwich.
Loukas, G. (2015). Cyber-physical attacks: A growing invisible threat (First Ed.). Waltham, MA: Butterworth-Heinemann.
Lugabihl, J., Owen, D., Rand, T. A., and Tran, P. M. (2013). Taking Charge of Security in a Hyper-connected World (Rep.). RSA.
Lyu, Y., Pan, Q., Zhao, C., Zhu, H., Tang, T., Zhang, Y., (2015). A Vision Based Sense and Avoid System for Small Unmanned Helicopter, Key Laboratory of Information Fusion Technology, Ministry of Education, Northwestern Polytechnical University.
Mackie, J., Spencer, J., and Warnick, K. F. (2014). Compact FMCW radar for a UAS Sense and Avoid system. 2014 IEEE Antennas and Propagation Society International Symposium (APSURSI).
Maddox, S., Stuckenberg, D., (2015). Drones in the U.S. National Airspace System: A Safety and Security Assessment, Harvard Law School.
Matolak, D.W., Sun, R., (2015). Air-Ground Channel Characterization for Unmanned Aircraft Systems: The Near-Urban Environment, IEEE.
McCallie, Donald. (2011) Exploring Potential ADS-B Vulnerabilities in the FAA’s Nextgen Air Transportation System. Air Force Institute of Technology. http://www.hsdl.org/?abstractanddid=697737
McCallie, D., Butts, J., and Mills, R. (2011). Security analysis of the ADS-B implementation in the next generation air transportation system [Scholarly project]. Retrieved March 9, 2016.
Meixall, B., Forner, B., (2013). Out of Control: Demonstrating SCADA Exploitation, Cimation.
Mukherjee, A., (2015). First Ever Anti-Drone Weapon that Shoots Down UAVs with Radio Waves, Death Ray.
Mumm, H. (2015). Applying Complexity Leadership Theory to Drone Airspace Integration. Melbourne, Florida: Motivational Press
Mumm, H. (2015, December 4). Managing the Integration and Harmonization of the National Airspace for Unmanned and Manned Systems. Lecture presented at DuPont Summit in the Historic Whittemore House, Washington D.C.
Nestler, V. (2015, October 15). The Age of Drones and Cybersecurity. Lecture presented at Centers of Academic Excellence TECH TALK in Capitol Technology University, San Bernardino, CA.
Nichols, R.K, and (Nov 28-30, 2006) Cyber Terrorism, Critical Infrastructure, and SCADA Presentation: Utica College, Utica NY. Defense Threat Reduction Agency Conference, Shirlington VA
Nichols, R.K. (2004, January 1). “Trust Me, Its Encrypted”. Lecture presented at Rutgers University, New Brunswick, NJ.
Nichols, R.K., and Lekkas, P.C., (2002) Wireless Security: Models, Threats and Solutions, New York: McGraw Hill.
Nichols, R.K., Ryan, D.J., and Ryan, J.C.H., (2001) Defending Your Digital Assets against Hackers, Crackers, Spies and Thieves, McGraw-Hill.
Nichols, R.K. (2009, April 16). Terrorism – The Mutating Threat CYBERSECURITY – A Future in Crisis? Lecture presented at NYSETA Plenary in SUNYIT, Utica, NY.
Norris, A. (2013). Legal Issues Relating to Unmanned Maritime Systems, Monograph. Retrieved November 23, 2015.
O’Connor, T. (2011). Military Intelligence, Mega Links in Criminal Justice.
Oded, G. (2014). Understanding the threat to SCADA networks.
Oltsik, J. (2013). The Big Data Security Analytics Era is Here (Rep.). RSA.
Oltsik, J., McKnight, J., Gahm, J. (2010). Enterprise Strategy Group, “Assessing Cyber Supply Chain Security Vulnerabilities within the U.S. Critical Infrastructure.”
Ott, J.T., (2014). Well Clear: General Aviation and Commercial Pilots’ Perception of Unmanned Aerial Vehicles in the National Airspace System, San Jose State University.
Owen, M. and Duffy, S. (2014). Unmanned Aircraft Sense and Avoid Radar: Surrogate Flight Testing Performance Evaluation.
Paganini, P., (2013). Hacking Drones – Overview of the Main Threats, Infosec Institute.
Paganini, P. (2015). SCADA and Security of Critical Infrastructures. In InfoSec Institute. Retrieved February 11, 2016, from http://resources.infosecinstitute.com/scada-security-of-critical-infrastructures/
Pauner, C., Kamara, I., Viguri, J., (2015). Drones. Current Challenges and Standardization Solutions in the Field of Privacy and Data Protection, University Jaume I, Spain, Vrije Universiteit Brussel, Belgium.
Parker, D.B, (1991) Proceedings of the 14th National Computer Security Conference.
Petersen, J. (2001). Understanding surveillance technologies: Spy devices, their origins and applications. Boca Raton, FL: CRC Press.
Pitchford, M., (2013). What’s needed to ensure safety and security in UAV software, Military Embedded Systems?
Radmanesh, M., and Kumar, M. (2016). Flight formation of UAVs in presence of moving obstacles using fast-dynamic mixed integer linear programming. Aerospace Science and Technology, 50, 149-160. Retrieved February 11, 2016.
Raffetto, M., (2004). Unmanned Aerial Vehicle Contributions to Intelligence, Surveillance, and Reconnaissance Missions for Expeditionary Operations, Monterey, CA, Naval Postgraduate School.
Ramasamy, S., Sabatini, R., Gardi, A., (2014). Avionics Sensor Fusion for Small Size Unmanned Aircraft Sense-and-Avoid, Melbourne, Australia, RMIT University – SAMME.
R.G., D.M., (n.d.). SCADA Security and Terrorism: We’re not crying wolf, Internet Security Systems.
Sabatini, R. (2015). Airborne Lasers and Integrated Weapon Systems: Design, Development, Test and Evaluation, RMIT University.
Sabatini, R., Gardi, A., Richardson, M., (2014). A Laser Obstacle Warning and Avoidance System for Manned and Unmanned Aircraft, Melbourne, Australia, RMIT University – SAMME, Shrivenham, Swindon, UK, Cranfield University – DAUK.
Shaneck, M. (2003). An Overview of Buffer Overflow Vulnerabilities and Internet Worms [Scholarly project]. In University of Minnesota. Retrieved February 20, 2016, from http://www-users.cs.umn.edu/~shaneck/MarkShaneck_BufferOverflows.pdf
Shull, A.M., (2013). Analysis of Cyberattacks on Unmanned Aerial Systems, West Lafayette, IN, Purdue University.
Stockwell, T. M. (2012). Defending Against Data Breach: Developing the Right Encryption Strategy (Rep.). Linoma Software.
The National Intelligence Strategy, (2009).
Thiobane, F. (2015). Cyber Security and Drones, Utica College.
Tsang, R. (n.d.). Cyberthreats, Vulnerabilities and Attacks on SCADA Networks [Scholarly project]. Retrieved February 19, 2016.
Wapner, J., (2016). Medical Transport Drones Could Transform Health Care in Overcrowded Cities, India, Newsweek, Global Ed.
Wilhoit, K., (2013). The SCADA that Didn’t Cry Wolf, Trend Micro.
Yagdereli, E., Gemci, C., and Aktas, A. Z. (2015). A study on cyber-security of autonomous and unmanned vehicles. The Journal of Defense Modeling and Simulation: Applications, Methodology, Technology, 12(4), 369-381
Yu, X., and Zhang, Y. (2015). Sense and avoid technologies with applications to unmanned aircraft systems: Review and prospects. Progress in Aerospace Sciences, 74, 152-166. Retrieved February 13, 2016.
Zeitlin, A., Lacher, A., Kuchar, J., and Drumm, A. (2006). Collision Avoidance for Unmanned Aircraft: Proving the Safety Case [Scholarly project]. Retrieved February 11, 2016.
Zhu, B. and Anthony, Joseph. (n.d.). A Taxonomy of Cyber Attacks on SCADA System. University of California, Berkley.
Secondary References
45 years ago: First message sent over the Internet. (2014, October 29). Retrieved December 3, 2015, from http://www.cbsnews.com/news/first-message-sent-over-the-internet-45-years-ago/
1950s and 1960s. (n.d.). Retrieved December 5, 2015, from https://sites.google.com/site/uavuni/1950s-1960s
Accenture Technology. (2015). Security for the Internet of Things: A Call to Action. Retrieved February 14, 2016, from http://www.slideshare.net/AccentureTechnology/security-for-the-internet-of-things-a-call-to-action
Acoustic Sensors for Unmanned Air Vehicles. (2016). Retrieved February 11, 2016, from http://www.sara.com/ISR/acoustic_sensing/LOSAS.html
ACPI, firmware and your security. (2014) Retrieved January 31, 2016, from http://www.markshuttleworth.com/archives/1332
Adamcaudill/Psychson. (n.d.). Retrieved January 31, 2016, from https://github.com/adamcaudill/Psychson
ADS, Inc. (2013). Tactical Communications: C4ISR Expanding the Grid. Retrieved from https://adsinc.com/c4isr-expanding-the-grid/
Advanced Drone Detection Technology. (2015). Retrieved December 3, 2015, from http://www.dronedetector.com/
Aerialtronics. (2016). Drones for a world of applications – Unmanned Aircraft Systems – Aerialtronics. Retrieved March 12, 2016, from http://www.aerialtronics.com/
Aircrack-ng. (2016). Documentation. Retrieved March 12, 2016, from http://www.aircrack-ng.org/
Aircraft Hull Insurance. (2012). Retrieved November 29, 2015, from http://financial-dictionary.thefreedictionary.com/
Air Informatics® LLC. (2015). Retrieved October 25, 2015 from http://www.airinformatics.com/e-Enabled_Definition.html/
Amazon’s Drone Highway Concept. (2015, September 23). Retrieved December 3, 2015, from https://www.workinghomeguide.com/23979/amazons-drone-highway-concept
Anderson, C. (2016). DIY Drones. Retrieved March 12, 2016, from http://diydrones.com/
Anonymous. (n.d.). BlueScan – Scanner de dispositions Bluetooth. Retrieved March 12, 2016, from http://bluescanner.sourceforge.net/
Anonymous. (2012). Global Hawk Aircraft. Retrieved March 11, 2016, from http://www.nasa.gov/multimedia/imagegallery/image_feature_2362.html
Anonymous. (2015). IAI Unveils the Drone Guard: Drone Detection, Identification and Disruption Systems. Retrieved March 11, 2016, from http://www.israeldefense.co.il/en/content/iai-unveils-drone-guard-drone-detection-identification-and-disruption-systems
Anonymous. (2011). Keeping Track of Unmanned Aircraft by Overcoming “Lost Links” Retrieved March 11, 2016, from http://www.mitre.org/publications/project-stories/keeping-track-of-unmanned-aircraft-by-overcoming-lost-links
Anonymous. (2015). Sky for All: Air Mobility for 2035 and Beyond. Retrieved March 11, 2016, from https://herox.com/SkyForAll
Anonymous. (2015). SQL Injection Tutorial – w3resource. Retrieved March 11, 2016, from http://www.w3resource.com/sql/sql-injection/sql-injection.php
Arthur, C. (Ed.). (2009, December 17). SkyGrabber: The $26 software used by insurgents to hack into US drones. Retrieved December 5, 2015, from http://www.theguardian.com/technology/2009/dec/17/skygrabber-software-drones-hacked
B, W. (2009, June 8). Air Traffic Control System Vulnerable to Cyber Terrorism. Retrieved December 2, 2015, from https://www.globaldatavault.com/blog/air-traffic-control-system-vulnerable-to-cyber-terrorism/
Baugh, C. (2011). GPS Hacking Guide: Learn How to Hack Your GPS Device. Retrieved March 12, 2016, from http://www.brighthub.com/electronics/gps/articles/125230.aspx#imgn_0
BCN Drone Center. (2016). BCN Drone Center | UAV Test Site – UAV Remote Sensing Applications 6. Retrieved March 12, 2016, from http://www.barcelonadronecenter.com/index.php/uav-remote-sensing-applications-6
Beaudoin, L, Gademer, A, Avanthey, L, Vittori, V, Germain, V. (January 2011) Potential Threats of UAS Swarms and the Countermeasure’s Need. Conference Paper retrieved 21 March 2016. https://www.researchgate.net/publication/261633504
Beaufort scale. (2011). Science/SOSE. Retrieved March 09, 2016, from http://cpsroom10.edublogs.org/2011/03/03/sun/#more-73
Bonggay, C. (2015, March 4). Commercial Drone Rules Around the World PrecisionHawk. Retrieved November 17, 2015, from http://media.precisionhawk.com/topic/commercial-drones-faa/
Breakthrough Technologies for National Security. (March 2015) Retrieved January 30, 2016, from http://www.darpa.mil/attachments/DARPA2015.pdf
C4ISR Definition. (n.d.). Retrieved March 09, 2016, from http://www.acronymfinder.com/
Calvo, K. (2015, October 29). So, You Want to Keep Track of All Your Drone Flights? Retrieved November 3, 2015, from http://voices.nationalgeographic.com/2015/10/29/so-you-want-to-keep-track-of-all-your-drone-flights/
Carpenter, R., and Anderson, A. (2006). The death of Schrödinger’s cat and of consciousness-based quantum wave-function collapse. Annales De La Fondation Louis De Brogli, 31(1), 45-52. Retrieved December 2, 2015, from http://web.archive.org/web/20061130173850/http:/www.ensmp.fr/aflb/AFLB-311/aflb311m387.pdf
CARAC Activity Details. (2015). Retrieved November 9, 2015, from http://wwwapps.tc.gc.ca/Saf-Sec-Sur/2/NPA-APM/actr.aspx?id=17andaType=1andlang=eng
Castillo, A. (2015, November 10). A DMV for Drones? Inside the FAA’s Clumsy Push to Regulate Flying Computers. Retrieved November 22, 2015, from https://reason.com/archives/2015/11/10/faa-versus-drones
Chesson, J. (n.d.). Cyber Crime. Retrieved December 3, 2015, from http://www.powershow.com/view/20b54-OGU4Z/Cyber_Crime_powerpoint_ppt_presentation
Chicago Protects Critical Infrastructure and Services with Security Connected. (2014). Retrieved December 2, 2015, from http://www.mcafee.com/us/case-studies/cs-city-of-chicago.aspx
Chinese drone manufacturer DJI building outpost and hiring in Palo Alto – Silicon Valley Business Journal. (2015, October 30). Retrieved October 31, 2015, from http://www.bizjournals.com/sanjose/blog/techflash/2015/10/chinese-drone-manufacturer-dji-is-building-a.html
Cole, C. (2012). Mapping drone proliferation: Big business vs. the MTCR. Retrieved March 11, 2016, from http://dronewars.net/2012/09/18/mapping-drone-proliferation-big-business-vs-the-mtcr/
COTS Journal. (2016). Retrieved March 11, 2016, from http://www.cotsjournalonline.com/
Coventor. (2016). MEMS Accelerometer Design and Simulation. Retrieved March 12, 2016, from http://www.coventor.com/mems-solutions/accelerometers/
Cravey, P. A. (2016). TRADOC Capability Manager for Unmanned Aircraft Systems. Retrieved March 12, 2016, from http://www.rucker.army.mil/usaace/uas/
Crowe, S. (2015). Boeing’s Mid-Air Charging Lets Drones Fly Forever – Robotics Trends. Retrieved March 12, 2016, from http://www.roboticstrends.com/article/boeings_mid_air_charging_lets_drones_fly_forever/
Cyber Threats. (2015). Retrieved December 2, 2015, from http://thefc2.org/news/cyberthreatvectors.aspx
DARPA uses open systems to boost airpower. (2015). Retrieved January 30, 2016, from http://www.af.mil/News/ArticleDisplay/tabid/223/Article/582052/darpa-uses-open-systems-to-boost-airpower.aspx
Definition of Black Swan Theory. (2015). Retrieved December 2, 2015, from http://www.davemanuel.com/investor-dictionary/black-swan-theory/
DJI: The World Leader in Camera Drones/Quadcopters for Aerial Photography. (2015). Retrieved December 1, 2015, from http://www.dji.com/
Drones: Detect, identify, intercept and hijack. (n.d.) Retrieved January 31, 2016, from https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2015/december/drones-detect-identify-intercept-and-hijack/
Drones vs. Radio-Controlled Aircraft: A Look at the Differences between the Two. (2015). Retrieved November 3, 2015, from https://rcflightline.com/drones-vs-radio-controlled-aircraft-a-look-at-the-differences-between-the-two/
DuPaul, N. (2014). Wireless Sniffer: Tools, Software to Detect Packet or Network Sniffers. Retrieved March 09, 2016, from http://www.veracode.com/security/wireless-sniffer
Dussalult, J. (2014, March 14). 7 commercial uses for drones. Retrieved December 1, 2015, from http://www.boston.com/business/2014/03/14/commercial-uses-for-drones/dscS47PsQdPneIB2UQeY0M/singlepage.html
EBumper4. (2016). Retrieved February 11, 2016, from http://www.panoptesuav.com/ebumper
Edwards, D. (2015). Flying-Swimmer (Flimmer) UAV/UUV. Retrieved December 1, 2015, from http://www.nrl.navy.mil/lasr/content/flying-swimmer-flimmer-uavuuv
Electro-Optical sensor payloads for small UAV’s (2013) Retrieved February 3, 2016, from C:\Users\Carrie\Desktop\Payload research items\Electro-optical sensor payloads for small UAVs – Military and Aerospace Electronics.htm
EPSON. (2016). Measurement instrument | Application | Epson device. Retrieved March 12, 2016, from http://www5.epsondevice.com/en/applications/measurement_instruments/
Equation Group: The Crown Creator of Cyber-Espionage. (2015) Retrieved January 31, 2016, from http://www.kaspersky.com/about/news/virus/2015/Equation-Group-The-Crown-Creator-of-Cyber-Espionage
Essential Equipment: Reach of FLIR Surges Forward. (2014) Retrieved January 31, 2016, from http://www.aviationtoday.com/rw/public-service/police/Essential-Equipment-Reach-of-FLIR-Surges-Forward_82549.html#.VsNI5PkrLIU
FAA Part 107 Rule for sUAS: https://www.faa.gov/uas/getting_started/model_aircraft/
FLIR. (2016). Thermal Imaging Cameras for sUAS. Retrieved March 12, 2016, from http://www.flir.com/suas/content/?id=70733
Federal Aviation Administration. (2015, November 1). Retrieved November 30, 2015, from https://www.faa.gov/
Facts. (2015). Retrieved November 1, 2015, from http://knowbeforeyoufly.org/ – Facts/
Federal Register. (2015, February 3). Retrieved October 25, 2015 from http://www.gpo.gov/fdsys/pkg/FR-2015-02-03/html/2015-01918.html
Ferranti, M. (2015, October 19). US to require registration process for drones. Retrieved October 31, 2015, from http://www.cio.com/article/2994818/us-to-require-registration-process-for-drones.html
Foxx, A. (2015, October 19). Clarification of the Applicability of Aircraft Registration Requirements for Unmanned Aircraft Systems (UAS) and Request for Information Regarding Electronic Registration for UAS. Retrieved October 31, 2015, from https://www.federalregister.gov/articles/2015/10/22/2015-26874/clarification-of-the-applicability-of-aircraft-registration-requirements-for-unmanned-aircraft
Gabbert, B. (2015). Fire drones. Retrieved March 11, 2016, from http://fireaviation.com/tag/uav/
GAO Report: Unmanned Aircraft Systems. (2012). Retrieved March 09, 2016, from http://radionavlab.ae.utexas.edu/spotlight/279-gao-report-unmanned-aircraft-systems-september-2012
Geofencing: What is it and how does it Work? (2014). Retrieved December 3, 2015, from http://socialbrothers.net/2014/03/18/geofencing-what-is-it-and-how-does-it-work/
Gettinger, D. (2015). Domestic Drone Threats. Retrieved March 11, 2016, from http://dronecenter.bard.edu/what-you-need-to-know-about-domestic-drone-threats/
Glas, J. (2010). Frequency Hopping. Retrieved March 12, 2016, from http://www.wirelesscommunication.nl/reference/chaptr05/spreadsp/fh.htm
Glenn. (2012). SensePost | Snoopy: A distributed tracking and profiling framework. Retrieved March 11, 2016, from https://www.sensepost.com/blog/2012/snoopy-a-distributed-tracking-and-profiling-framework/
Goodrich, R. (2013). Accelerometer vs. Gyroscope: What’s the Difference? Retrieved March 12, 2016, from http://www.livescience.com/40103-accelerometer-vs-gyroscope.html
Gorman, S., Dreazen, Y., and Cole, A. (2009, December 17). Insurgents Hack U.S. Drones. Retrieved December 2, 2015, from http://www.wsj.com/articles/SB126102247889095011
GPS Spoofing: Hijacking in the Digital Age. (2013) Retrieved January 30, 2016, from http://www.nolanwpeterson.com/gps-spoofing-hijacking-in-the-digital-age/\
Greenburg, A, Wired (2015). Hackers Remotely Kill a Jeep on the Highway—With Me in It. https://www.wired.com/2015/07/hackers-remotely-kill-jeep-highway/
Greenwood, J. (2015). The Phantom Menace – Weaponizing a consumer drone. Retrieved February 14, 2016, from https://www.4armed.com/blog/phantom-menace-weaponising-drones/
Guo, E. (2011). VT-SHA3 A. Retrieved March 09, 2016, from http://rijndael.ece.vt.edu/sha3
Hackers. (2015, March 10). Retrieved December 3, 2015,
from http://csrc.nist.gov/publications/nistir/threats/subsection3_4_2.html
Haines, B., (n.d.). Hackers and Airplanes, No Good Can Come from This. http://korben.info/wp-content/uploads/defcon/SpeakerPresentations/Renderman/DEFCON-20-RenderMan-Hackers-plus-Airplanes.pdf
Hard disk hacking -Parts on the PCB. (n.d.) Retrieved January 30, 2016, from https://spritesmods.com/?art=hddhackandpage=2
Help Net Security. (2016). Deep and Dark Web: Complexity and escalating cybercriminal activity – Help Net Security. Retrieved March 12, 2016, from https://www.helpnetsecurity.com/2016/02/22/deep-and-dark-web-complexity-and-escalating-cybercriminal-activity/
Hernandez, A. (2015, October 2). UAV. Retrieved November 17, 2015, from http://www.slideshare.net/AnthonyHernandezMPAB/uav-53447022
Holmlund, K. (2010). When the Eyjafjallajökull volcano in Iceland erupted in 2010, satellite imagery proved to be instrumental in helping track the movement of the large ash plume. Retrieved March 09, 2016, from http://www.eumetsat.int/website/home/Images/ImageLibrary/DAT_2187509.html
Howard, C. (2015). Team of military pilots enter consumer drone market, launch UAV control software. Retrieved November 16, 2015, from http://www.intelligent-aerospace.com/articles/2015/05/team-of-military-pilots-enter-consumer-drone-market-launch-uav-control-software.html
Howard, C. (2013). UAV Command, Control and Communications. Retrieved March 09, 2016, from http://www.militaryaerospace.com/articles/print/volume-24/issue-7/special-report/uav-command-control-communications.html
Huerta, M. (2013). Integration of Civil Unmanned Aircraft Systems (UAS) in the National Airspace System (NAS) Roadmap. Retrieved November 17, 2015, from http://www.faa.gov/uas/legislative_programs/uas_roadmap/media/UAS_Roadmap_2013.pdf
IEEE. (n.d.) Airborne Communication Networks for Small Unmanned Aircraft Systems. (n.d.). Retrieved March 09, 2016, from http://ieeexplore.ieee.org/ieee_pilot/articles/96jproc12/jproc-EFrew-2006127/article.html
I-HLS. (2015). Nanoradar system for UAVs collision avoidance set for 2016 – i-HLS Israel Homeland Security. Retrieved March 12, 2016, from http://i-hls.com/2015/10/nanoradar-system-for-uavs-collision-avoidance-set-for-2016
Information Security Office Shared Services. (2015). Retrieved December 2, 2015, from http://www.cityofchicago.org/city/en/depts/doit/provdrs/security_and_datamanagement/svcs/information-security-office-shared-services.html
Intelligence Debates. (2016). Retrieved March 11, 2016,
Insurance Coverage for Unmanned Aerial Vehicles – UAV. (2015). Retrieved November 9, 2015, from http://www.transportrisk.com/uavrcfilm.html
Iran starts cloning of American spy drone. (2012, April 22). Retrieved December 3, 2015, from https://www.rt.com/news/iran-spy-drone-copy-667/
James, L. (2014, February 8). How do Beacon and Geo-Fencing Actually Work? Retrieved December 3, 2015, from http://www.mobiledonky.com/blog/how-do-beacon-and-geo-fencing-actually-work
Jansen, B. (2014, June 5). Drones will be revolutionary, but hurdles remain. Retrieved December 1, 2015, from http://www.usatoday.com/story/money/business/2014/06/05/drones-national-research-council-faa-clarke-lauber/10002007/
Jarzombek, J. (2012). Supply chain Risk Management. Retrieved from http://csrc.nist.gov/scrm/documents/workshop_oct2012/jarzombek_ict_supply_chain_workshop_oct-15-2012.pdf
Jenkins, D., and Vasigh, B. (2013, March 1). The economic impact of unmanned aircraft systems integration in the United States. Retrieved November 9, 2015, from https://higherlogicdownload.s3.amazonaws.com/AUVSI/958c920a-7f9b-4ad2-9807-f9a4e95d1ef1/UploadedImages/New_Economic Report 2013 Full.pdf
Kamkar, S. (2013). SkyJack. Retrieved February 24, 2016, from http://samy.pl/skyjack/
Kargo, D. (2012). Dad’s Toys. Retrieved December 5, 2015, from https://www.pinterest.com/pin/203365739393483039/
Karp, A. (2015, October 1). FAA warns of ‘a million drones under people’s Christmas trees’. Retrieved October 31, 2015, from http://www.suasnews.com/2015/09/38847/faa-warns-of-a-million-drones-under-peoples-christmas-trees/
Keller, J. (2014, July 24). U.S. spending on unmanned aerial vehicles (UAVs) to reach $15 billion by 2020, market researcher says. Retrieved December 1, 2015, from http://www.militaryaerospace.com/articles/2014/07/igi-uav-*forecast.html
King, S. T., Tucek, J., Cozzie, A., Grier, C., Jiang, W., and Zhou, Y. (2008). Designing and implementing malicious hardware [Scholarly project]. In Usenix. Retrieved February 24, 2016, from https://www.usenix.org/legacy/event/leet08/tech/full_papers/king/king_html/
Koebler, J. (2015, October 19). 8 Questions Raised by the FAA’s Decision to Register Every Drone in the US. Retrieved November 22, 2015, from http://motherboard.vice.com/read/8-questions-raised-by-the-faas-decision-to-register-every-drone-in-the-us
Kumar, M. (2015). Hacking Team and Boeing Built Cyber Weaponized Drones to Spy on Targets. Retrieved February 14, 2016, from http://thehackernews.com/2015/07/boeing-drone-hacking.html
Kumar, M. (2015). How Drones Can Find and Hack Internet-of-Things Devices from the Sky. Retrieved February 14, 2016, from http://thehackernews.com/2015/08/hacking-internet-of-things-drone.html
LeMieux, J. (2012). Alternative UAV Navigation Systems. Retrieved March 12, 2016, from http://m.electronicdesign.com/embedded/alternative-uav-navigation-systems
Lerner, M. (2014, August 5). The Chilling Effect of Domestic Spying (T. DeWeese, Ed.). Retrieved December 2, 2015, from http://americanpolicy.org/2014/08/05/the-chilling-effect-of-domestic-spying/
Lewis, J., and Caplan, L. (2015, July 28). Drones to satellites: should commercial aerial data collection regulations differ by altitude?
Liles, S. (2008). From Information operations to cyber warfare and a new terrain. Retrieved March 09, 2016, from http://selil.com/archives/336
Lockheed Martin awarded contract to enhance US Navy’s C4ISR collection and dissemination capabilities. (2014). Retrieved from http://uss-america.blogspot.com/2014/06/lockheed-martin-nyselmt-will-work-to.html
Louviere, G. (2006). Newton’s 3 Laws of Motion. Retrieved March 12, 2016, from http://teachertech.rice.edu/Participants/louviere/Newton/
Mahoney, D. (2015, November 10). Aviation insurer offers ground rules for drones. Retrieved November 17, 2015, from http://www.businessinsurance.com/article/20151110/NEWS06/151119989/aviation-insurer-offers-ground-rules-for-drones-faa-federal-aviation?tags=|71|76|80|83|329|302
Malicious Code Information. (n.d.) Retrieved January 30, 2016, from http://www3.safenet-inc.com/csrt/malicious-code-more.aspx
Merriam-Webster Dictionary. http://www.merriam-webster.com/dictionary/cybersecurity/
Miasnikov, E. (2011). The Threat of the Use of Small UAVs by Terrorists: Technical Aspects. Retrieved March 12, 2016, from http://www.armscontrol.ru/UAV/em040711.htm
MIMO Radar. (2015). Retrieved December 3, 2015, from http://www.androcs.com/mimo_radar.html
Muncaster, P. (2016). CIOs: Hackers Hiding in Encrypted Traffic is Major Threat. Retrieved March 12, 2016, from http://www.infosecurity-magazine.com/news/cios-hackers-hiding-encrypted/
Mulrine, A. (2015, July 28). Robots in war: Ethical concern, or a help for social ills? Retrieved November 23, 2015, from http://www.csmonitor.com/USA/Military/2015/0728/Robots-in-war-Ethical-concern-or-a-help-for-social-ills
Murphy, M. (2015, November 5). The future of drones is apps. Retrieved November 9, 2015, from http://qz.com/540559/the-future-of-drones-is-apps/
National Institute of Advanced Industrial Science and Technology. (2012). Side-channel Attack Standard Evaluation Board (SASEBO) -SASEBO-R. Retrieved March 09, 2016, from http://satoh.cs.uec.ac.jp/SASEBO/en/board/sasebo-r.html
New 50″ Mini Telemaster RC Plane Kit Remote Control R/C Airplane 50in Balsa. (2015). Retrieved December 5, 2015, from http://www.ebay.com/itm/New-50-Mini-Telemaster-RC-Plane-Kit-Remote-Control-R-C-Airplane-50in-Balsa-/181948366992
NSA planted Stuxnet-Type Malware Deep within Hard Drive Firmware. (2016) Retrieved January 31, 2016, from http://thehackernews.com/2015/02/hard-drive-firmware-hacking.html
O’Donnell, A. (2016). 4 Secrets Hackers Don’t Want You to Know. Retrieved March 12, 2016, from http://netsecurity.about.com/od/secureyourwifinetwork/a/4-Secrets-Wireless-Hackers-Do-Not-Want-You-To-Know.htm
Opinion: Jamming Is Needed Against Agile Radar Threat. (2014) Retrieved January 30, 2016, from http://aviationweek.com/defense/opinion-jamming-needed-against-agile-radar-threat
Paganini, P. (2013). Hacking Drones … Overview of the Main Threats – InfoSec Resources. Retrieved February 14, 2016, from http://resources.infosecinstitute.com/hacking-drones-overview-of-the-main-threats/
Paganini, P. (2014). Hack-Proof Drones Possible with HACMS Technology – InfoSec Resources. Retrieved February 14, 2016, from http://resources.infosecinstitute.com/hack-proof-drones-possible-hacms-technology/
Paganini, P. (2013). Hardware attacks, backdoors and electronic component qualification – InfoSec Resources. Retrieved February 24, 2016, from http://resources.infosecinstitute.com/hardware-attacks-backdoors-and-electronic-component-qualification/
Palermo, E. (2014, July 29). Drones Could Grow to $11 Billion Industry by 2024. Retrieved December 1, 2015, from http://www.livescience.com/47071-drone-industry-spending-report.html
Patel, D. (2014). How does Accelerometer and Gyro sensor work in digital gadgets? Retrieved March 11, 2016, from how does Accelerometer and Gyro sensor work in digital gadgets?
Peck, M. (2016). Army will test 3-D printed UAVs. Retrieved March 12, 2016, from http://www.c4isrnet.com/story/military-tech/uas/2016/02/24/army-3d-printed-uav-drone/80858028/
Peterson, S. (2011, December 9). Downed US drone: How Iran caught the ‘beast’ Retrieved December 3, 2015, from http://www.csmonitor.com/World/Middle-East/2011/1209/Downed-US-drone-How-Iran-caught-the-beast
Petrovsky, O. (2015). Attack on the drones: Security vulnerabilities of unmanned aerial vehicles. Retrieved February 23, 2016, from https://www.virusbulletin.com/conference/vb2015/abstracts/attack-drones-security-vulnerabilities-unmanned-aerial-vehicles
Perlman, A. (2015, November 22). DJI Introduces New Geofencing System for Its Drones. Retrieved December 3, 2015, from http://uavcoach.com/dji-introduces-new-geofencing-system/
Pomerleau, M. (2015, October 28). How to do air traffic control for drones. Retrieved November 3, 2015, from https://gcn.com/articles/2015/10/28/latas-drone-control.aspx
Posel, S. (2013). Anti-Drone Tech Corp To Begin Selling to Public While Working with DARPA – Top US and World News | Susanne Posel. Retrieved March 11, 2016, from https://occupycorporatism.com/anti-drone-tech-corp-to-begin-selling-to-public-while-working-with-darpa/
Powers, R. (2014). What Is a 15W – Unmanned Aerial Vehicle Operator? Retrieved March 11, 2016, from http://usmilitary.about.com/od/enlistedjobs/a/96u.htm
Purchase, D. (2015). Clearing the air: Study examines human-wildlife conflicts in crowded airspace. Retrieved March 11, 2016, from http://www.swansea.ac.uk/media-centre/news-archive/2015/clearingtheairstudyexamineshuman-wildlifeconflictsincrowdedairspace.php
Radic, D. (n.d.). 7.9. C4ISR, Basic Principles of C4 System. Retrieved March 09, 2016, from http://www.informatics.buzdo.com/p939-c4isr.htm#n1
Radio. (2002) Retrieved January 30, 2016, from http://www.encyclopedia.com/topic/radio.aspx
Ranjan, A. (2015). Ethacklesias. Retrieved February 25, 2016, from http://ethacklesias.blogspot.com/
Rakshasa: The hardware backdoor that China could embed in every computer. (2012) Retrieved January 30, 2016, from http://www.extremetech.com/computing/133773-rakshasa-the-hardware-backdoor-that-china-could-embed-in-every-computer
Reagan, J. (2014, December 15). 11 States Enacted New Drone Laws in 2014. Retrieved November 17, 2015, from http://dronelife.com/2014/12/15/11-states-enacted-new-drone-laws-2014/
Real Clear Technology. (2016). How to Hack a Smartphone with a Fake Fingerprint. Retrieved March 12, 2016, from http://www.realcleartechnology.com/video/2016/02/24/how_to_hack_a_smartphone_with_a_fake_fingerprint.html
Ribeiro, J. (2014, August 20). US senator to introduce proposal for mandatory drone geofencing. Retrieved November 17, 2015, from http://www.cio.com/article/2973586/us-senator-to-introduce-proposal-for-mandatory-drone-geofencing.html
Road to the Future Part 2. (n.d.) Retrieved January 30, 2016, from http://www.onfinalblog.com/2015/08/darpas-vision-of-joint-future.html
Rogawski, M., Gaj, K., and Homsirikamol, E. (2013). A high-speed unified hardware architecture for 128 and 256-bit security levels of AES and the SHA-3 candidate Grøstl ☆. Retrieved March 09, 2016, from http://www.sciencedirect.com/science/article/pii/S0141933113000847?np=y
RT. (2012). Drone hack explained: Professor details UAV hijacking. Retrieved March 12, 2016, from https://www.rt.com/usa/texas-professor-drone-hacking-249/
Satellite Missions. (n.d.). Retrieved March 09, 2016, from http://www.nesdis.noaa.gov/about_satellites.html
Schwarz, T. (2004). 1. How Input Can Be Bad. Retrieved March 12, 2016, from http://www.cse.scu.edu/~tschwarz/coen152_05/Lectures/BufferOverflow.html
Sifton, J. (2012, February 7). A Brief History of Drones. Retrieved December 1, 2015, from http://www.thenation.com/article/brief-history-drones/
Sense and Avoid for Unmanned Aerial Vehicles. (n.d.). Retrieved December 1, 2015, from http://www.frc.ri.cmu.edu/projects/senseavoid/technology.html
September 11th Flights. (2008, May 21). Retrieved December 2, 2015, from http://911research.wtc7.net/planes/sept11.html
Shapiro, J. (2015). Cybersecurity. Retrieved February 14, 2016, from http://slideplayer.com/slide/4545982/
Shukla, M., Chen, Z., and Lu, C. (2015). Distributed Drone Flight Path Builder System. Retrieved November 1, 2015, from http://europa.nvc.cs.vt.edu/~ctlu/Publication/2015/GISTAM-2015-Proceedings.pdf
SkyGrabber is offline satellite internet downloader. (2008). Retrieved December 2, 2015, from http://www.skygrabber.com/en/skygrabber.php
Skaves, P. (2015, April 1). Retrieved October 25, 2015 from http://www.cabaa.com/documents/FAA_Aircraft_System_Information_Security_Protection_Overview_4-1-2015_Jim_Skaves.pdf
Sky Safe. (2016). Sky Safe. Retrieved March 12, 2016, from http://www.skysafe.io/
Snow, C. (2014, February 6). The Yellow Brick Road of FAA Drone Regulations. Retrieved November 17, 2015, from http://droneanalyst.com/2014/02/06/the-yellow-brick-road-of-faa-regulations/
Sood, A. K., and Enbody, R. (2014). U.S. Military Defense Systems: The Anatomy of Cyber Espionage by Chinese Hackers. Retrieved February 13, 2016, from http://journal.georgetown.edu/u-s-military-defense-systems-the-anatomy-of-cyber-espionage-by-chinese-hackers/
Tesla, C. (2014, June 17). The past and the future of drones. Retrieved November 17, 2015, from http://www.tumotech.com/2014/06/17/the-past-and-the-future-of-drones/
The Drones Report: Market forecasts, regulatory barriers, top vendors, and leading commercial applications. (2015, May 27). Retrieved December 3, 2015, from http://www.businessinsider.com/uav-or-commercial-drone-market-forecast-2015-2
Timeline for Domestic Drone Integration. (2012, June 13). Retrieved November 28, 2015, from https://www.eff.org/document/timeline-domestic-drone-integration
The Drones Danger. (2015, August 19). Retrieved November 22, 2015, from http://www.askthepilot.com/the-drone-danger/
Thurber, M., (2012). ADS-B Is Insecure and Easily Spoofed, Say Hackers. Retrieved from http://www.ainonline.com/aviation-news/aviation-international-news/2012-09-03/ads-b-insecure-and-easily-spoofed-say-hackers
Tomiuc, E. (2012, January 31). Drones – Who Makes Them and Who Has Them? Retrieved December 1, 2015, from http://www.rferl.org/content/drones_who_makes_them_and_who_has_them/24469168.html
Tomkins, R. (2014, May 13). Frost and Sullivan forecasts five-year rise in spending for UAVs. Retrieved December 1, 2015, from http://www.upi.com/Business_News/Security-Industry/2014/05/13/Frost-Sullivan-forecasts-five-year-rise-in-spending-for-UAVs/5631400008680/
UAS / UAV Research and Advisors – Drone Analyst. (2015). Retrieved November 9, 2015, from http://droneanalyst.com/
UAV Communications Equipment. (n.d.). Retrieved from http://www.hse-uav.com/communications.htm
UAV Navigation. (2015). Sensor Fusion and Estimation. Retrieved March 12, 2016, from http://www.uavnavigation.com/support/kb/general/general-system-info/sensor-fusion-and-estimation
UAV Protect. (2014, December 23). Retrieved December 3, 2015, from http://www.uav-protect.com/
UAV Tracking Systems | UAV Tracking and Recovery by Marshall. (2015). Retrieved December 3, 2015, from http://www.unmannedsystemstechnology.com/company/marshall-radio-telemetry/
Ulanoff, L. (2016). Drone lands on moving car like it’s no big deal. Retrieved March 09, 2016, from http://mashable.com/2016/01/21/drone-lands-on-car/#ixU6piag5aqX
Unmanned System Common Control System (CCS). (2016). Retrieved February 11, 2016, from http://www.navair.navy.mil/index.cfm?fuseaction=home.displayPlatform
United States Air Force RPA Vector. (2014) Retrieved January 30, 2016, from http://www.defenseinnovationmarketplace.mil/resources/USAF-RPA_VectorVisionEnablingConcepts2013-2038_ForPublicRelease.pdf
USA Army Magazine definition of Danger Close: www.benning.army.mil/infantry/magazine/issues/2013/May-June/Myer.html.
USAF Operating Next-Generation Remotely Piloted Aircraft for Irregular Warfare | Public Intelligence. (2011). Retrieved March 09, 2016, from https://publicintelligence.net/usaf-drones-in-irregular-warfare/.
Using Botnets to provide security for safety critical embedded systems – a case study focused on UAVs.
(Unknown) Retrieved January 30, 2016, from http://iopscience.iop.org.er.lib.k-state.edu/article/10.1088/1742-6596/633/1/012053/pdf.
Drone Crash into Boeing 737 in Mozambique. (6 Jan 2017) (UK Express, http://www.express.co.uk/travel/articles/751165/drone-boeing-737-plane-crash-mozambique. Also See: https://youtu.be/2jzx8BpDuHE
UST. (2015). UAV Navigation | Navigation and Guidance Systems for UAVs, ROVs, Ground Robots. Retrieved March 12, 2016, from http://www.unmannedsystemstechnology.com/category/supplier-directory/navigation-systems/
Vanden Brook, T. (2015). U.S. loses drone in Iraq. Retrieved March 11, 2016, from http://www.usatoday.com/story/news/world/2015/05/29/drone-isil-iraq/28177803/
Variable Vectoring Technique for Propeller-Powered UAVs – UAS VISION. (2016). Retrieved February 11, 2016, from http://www.uasvision.com/2016/01/15/variable-vectoring-technique-for-propeller-powered-uavs/
Vintage RC. (2012). Retrieved December 5, 2015, from http://www.rcuniverse.com/market/item.cfm?itemid=813625
Wallace, R. (2015, June 16). SciTech Tuesday-First V-1 rockets launched June 1944. Retrieved December 5, 2015, from http://www.nww2m.com/2015/06/scitech-tuesday-first-v-1-rockets-launched-june-1944/
Welch, G. (2016). The Kalman Filter. Retrieved March 12, 2016, from http://www.cs.unc.edu/~welch/kalman/
Welcome to Homeland Surveillance and Electronics LLC Unmanned Aerial Vehicle (UAV) Website! (2015, September 17). Retrieved November 2, 2015, from http://www.hse-uav.com/
Williams, M. (2015, July 28). Amazon proposes drone superhighways in sky. Retrieved December 3, 2015, from http://www.pcworld.com/article/2953952/government/amazon-proposes-drone-superhighways-in-sky.html
What is cyberterrorism? (2010, May 1). Retrieved December 3, 2015, from http://searchsecurity.techtarget.com/definition/cyberterrorism
What is Remote Code Execution? How to Hack Websites – Hacking-Sec. (2014). Retrieved February 24, 2016, from http://www.hackingsec.in/2014/02/what-is-remote-code-execution-how-to.html
What is SCADA (supervisory control and data acquisition)? (2005, September 1). Retrieved December 3, 2015, from http://whatis.techtarget.com/definition/SCADA-supervisory-control-and-data-acquisition
Whitlock, C. (2014, January 22). Crashes mount as military flies more drones in U.S. Retrieved December 1, 2015, from http://www.washingtonpost.com/sf/investigative/2014/06/22/crashes-mount-as-military-flies-more-drones-in-u-s/
Wolff, C. (n.d.). Radar Basics. Retrieved March 12, 2016, from http://www.radartutorial.eu/20.airborne/ab08.en.html
Staff (2017) Xinhua news. See: http://www.xinhuanet.com/english/2017-12/23/c_136847826.htm
Zaharia, M., Das, T., Li, H., Shenker, S. and Stoica. (nd) DLA: 07252108 from https://www.usenix.org/system/files/conference/hotcloud12/hotcloud12-final28.pdf
- FIRES definition (US DoD – JP 3-0) the use of weapon systems to create a specific lethal or nonlethal effect on a target. ↵
- Danger Close Definition www.benning.army.mil/infantry/magazine/issues/2013/May-June/Myer.html Nov 14, 2013 – 1) Danger Close is included in the “method-of-engagement” line of a call-for-fire request to indicate that friendly forces are close to the target. … Danger close is a term that is exclusive from risk estimate distance (RED) although the RED for 0.1 percent PI is used to define danger close for aircraft delivery. Pi = Probability of incapacitation. 2) Definition of “danger close” (US DoD) In close air support, artillery, mortar, and naval gunfire support fires, it is the term included in the method of engagement segment of a call for fire which indicates that friendly forces are within close proximity of the target. ↵
- Skyjack Drone hack. Drone that flies around seeking Seeks wireless signal of any other drone in area. Forcefully disconnects wireless connection of true owner of target drone. Authenticates with target drone pretending to be its owner. Feeds commands to it and all other zombie drones SkyJack primarily a Perl application which runs off a Linux. Detect drones by seeking out wireless connections from MAC addresses. ↵
- Aircrack-ng© To put wireless device into monitor mode to find drones and drone owners. De-authenticate true owner of drone. Once de-authenticated, connect as drone waiting for owner to reconnect. ↵
- Snoopy is Software that can hack into Wi-Fi and steal data – attached to drones. Comprised of various existing technologies. Uses Distributed tracking and profiling framework. Runs client-side code on any device that has support for wireless monitor mode. Collects proberequest and uploads to a central server. Exploits handsets looking for wireless signal. Most leave their device Wi-Fi setting on Spoof network available to Wi-Fi searchers to use. Once connected to rogue network, data is stolen. Differs from other rogue access points in way data is routed. Traffic is routed via an OpenVPN connection to a central server. Able to observe traffic from all drones in field at one point. Traffic manipulation only done on server. Allows basic data exploration and mapping. ↵

