4 Radiological, Electromagnetic, Drone & Metaverse Risks and Issues
By Dr. Robert McCreight
STUDENT OBJECTIVES
Students will discuss, analyze and study:
- n the nature of intermingled radiological and electromagnetic risk today
- n the impact of drone technology and metaverse factors in shaping future risk
- n the significance of technology convergence and the emergence of CONV-CBRN
- n Indicators of threat CONV-CBRN dynamics and cognitive warfare threats after 2021
- n Radiological, electromagnetic security, CONV-CBRN, and drone risk scenarios
- n Unique future security risks and challenges
BACKGROUND
When examined side by side, the nature of radiological risk and electromagnetic security may appear discontinuous. At first glance, the impact and reciprocal effects of one upon the other may seem less than spectacular. However, they signal a trajectory of security challenges and risks not readily grasped separately and in combination. Radiological emanations deemed harmful to humans must be evaluated independently from the same considerations applied to electromagnetics. When operating together and in combination, we can find a unique set of risks and security issues that may elude conventional analysis but pose a difficult geostrategic array of threat dynamics deserving greater attention. In many ways, it depicts a massively complex and brand-new geostrategic threat puzzle that defies facile solutions. It is truly lethal to misunderstand it, incorrectly diagnose it, or underestimate it.
Radiological factors are one thing, but our imagination and the application of steadily improving technology dovetailed with neuroscience, electromagnetic, drones, and the metaverse change the entire dynamic of how we must reckon with and understand the future. Each area is arguably distinct, but they must be forced through the lens of convergence to appreciate their strategic implications. There are technologies today and emerging over the next few years; few can comprehend; however, they represent a challenge to society, security, and strategic stability. In every case, the application of dual-use technology that has every bit of potential to bring death, destruction, disruption, and decay to our world has always shown a benign face where cures, fixes, energy savings, and fantastic problem-solving technologies become the bright shiny object that distracts us from the evil side of science and tech.
Convergent strategic reality admits that in almost Newtonian logic, there is an equal and very opposite nefarious and dangerous side to the technology that wows us for every good thing that technology provides. Worst of all, when each liner technology such as robotics, nanotech, neurotech, proteomics, lasers, and hundreds of other futuristic technologies are extrapolated, you get one outcome. However, when you deliberately or accidentally blend several, you get something entirely different. (McCreight R., 2013)
When the issue of drones is added, whether air, sea, space, or via swarms directed by hostile personnel, the equation changes. Loitering drones with advanced convergence technologies usher in new immersive capabilities that define new operational realities. They open Pandora’s box of emergent behavioral influences, which require an innovative tactical response, quick adaptation, and evidence-based adjustments to a nascent threat. Suppose autonomous killer drones are assigned to devastate a target by lethal ubiquity, the overall threat equation changes. Drones enable the autonomous or indirectly managed controlled and focused assembly of independently equipped aerial vehicles about the size of a microwave oven, which can deliver medical supplies, pizzas, wonderful nature photos, or rain down death and mayhem from the sky. Dozens of drones can swarm collectively and create a legion that defies easy defense or nullifies haphazard protection by delivering harmful or lethal packages against its intended target. Again, everything we suspect is friendly and helpful is a subtly hidden monster when re-engineered for destructive purposes.
When convergent technology dynamics [CONV] are included with drones and combined with the radiology and electromagnetic factors, we have touched upon the entire analytical lens through which the threat is seen. That nefarious blend of various technologies represents a conglomeration of risks that dramatically alters the spectrum of potential threats we must address. Geopolitical rivals will exploit its alleged potential, unveiling a new array of threats capable of shifting the global balance of power to allow some insidious and evil entity to harness its latent capabilities in ways we don’t expect, plan for, or foresee. Myriad convergence bundling by itself unleashes deployed mayhem laden with unintended consequences requiring adaptive human-machine threat analytics we can only imagine.
We must reconsider our understanding of CBRN now that 2022 is upon us. Older traditional views of CBRN are insufficient for tomorrow’s risks. The deliberate blending of heralded breakthroughs that quantum computing offers, alongside robotics, nanotech, 5th generation chemical/biological weaponry, neuroscience, and other cutting-edge scientific fields, suggests insidious risks. Their inherent convergent risks magnify the presumptive threat equation and overall strategic terrain after 2022.
The scope and scale of CBRN after the 9-11 attacks were understood to mean one thing largely accurate for its time. Today it looks much different and is likely to morph further in character and complexity by 2030. Worse of all, complex intervening variables have made CBRN, as we once understood it, tougher to grasp, identify and defeat. We find ourselves amid the Convergent CBRN revolution or what the author calls—CONV-CBRN. The era of convergent CBRN [CONV-CBRN] vastly complicates our grasp of future threat and risk equations, theories, and geostrategic applications. Worst of all, we lack the metrics and technologies to subdue it. What is the scope and trajectory of CONV-CBRN? Can we posit it in revolutionary terms as a force multiplier and strategic game-changer after 2022, especially in a dangerous dual-use universe of illegal arms transfers, rampant technology theft, and perpetually contending political actors and interests? Can it be predicted? Controlled? Redirected? Curtailed? Managed?
One salient insight from infusing AI and cyber elements into the future threat scenarios involving CONV-CBRN is to factor in yet another geostrategic variable–the evolving issue of the metaverse. We focus on deliberate, engineered, and directed blends of CONV-CBRN, radiological and electromagnetic factors, and advanced drone technology into something entirely new and never before seen. Adding in the metaverse and its variables makes it mind-boggling and blending what is real with what is virtual taxes our discerning skills and senses to a degree of uncertainty and caution that creates a strategic gap using A/R plus V/R plus reality.
The metaverse is largely undefined with any precision. Yet, it presumptively suggests a computer-generated world in parallel with reality which features technologies enabling augmented reality [AR] and virtual reality [VR]. Future sponsors and architects of the metaverse can expand its capabilities without limits and boundaries between what is real and what is virtual, becoming harder to discern. Some refer to it as a place or a space where replicas of real life can be created, sustained, and interact. IT expert Matthew Ball claimed in 2020 that the metaverse is “an expansive network of persistent, real-time rendered 3D worlds and simulations that […] can be experienced synchronously by an effectively unlimited number of users, each with an individual sense of presence.” According to his definition, the metaverse is a product or service with seven core attributes: persistence, synchronicity, and interoperability with the arguable layer of 3D aspects. (Ball, 2020)
In effect, the metaverse comprises whatever can be inserted or attached to it from genuine reality or the sphere of AR/VR ever-shifting and chameleon-like character. Here we must add to the points already made to emphasize that the existence of CONV-CBRN, mixed with radiological and electromagnetic tech issues—while inserting the possibilities derived from drones—suggests a new and staggering threat and risk set of issues in 2022. As such, the net implications of which radiological and electromagnetic technologies inform, support, or guide the operational definition of the metaverse are largely unknown. However, it is arguably a strategic arena for battle as its IoT, AI, cyber, nanotech, neurotech, biotech, and robotic aspects are configured to compete for dominance in an undefined space. Are we even equipped to conduct an objective risk analysis of this aggregation? Can we deal comprehensively with its consequences and downstream effects? Likely not. (McCreight R., Convergent Technology and Future Strategic Threat, 2013)
This aggregate array of threats and risks will transform the global geostrategic landscape for at least another decade or longer. This creates a geostrategic puzzle of gigantic proportions where neither the diagnostic strategies nor technologies designed to fit the CONV-CBRN threat adequately address its evolving nature and immediate emergence. Puzzle ingredients mix CONV-CBRN with cutting-edge dual-use science and technology mixing in radiological, electromagnetic, and drone aspects, a keystroke from our less insulated reality.
RADIOLOGICAL THREATS—EVERYTHING OLD IS NEW AGAIN
When the spectrum of radiological threats is examined at the end of 2021, we find a mix of old traditional and some new issues deserving of attention. This would necessarily include measures and technologies designed to mitigate anything resembling a nascent radiological threat. But the spectrum of radiological threats—both real and imagined—is larger and more complex. CDC says radiologic threat agents can issue from intentional or unintentional releases of dangerous radioactive materials. Unintentional emergencies include Nuclear Reactor Accidents and Transportation Accidents like a spill of radioactive material from a truck or train. However, intentional acts can include:[1]Contaminating food and water with radioactive material; [2] Spreading radioactive material into the environment; [3] Using conventional explosives mixed with highly radioactive substances – this is called a dirty bomb; [4] dispersing radioactive elements via wind currents or natural weather traffic patterns; [5]bombing or destroying a nuclear reactor; [6] causing nuclear material to spill while in transit as waste products from nuclear plants; [7] theft of radioactive materials and course [8]exploding a nuclear weapon. (CDC, 2022)
After the infamous 9-11 attacks, there were profound fears that terrorists could either create an improvised nuclear device [IND] or somehow match-high explosives with radioactive material or fissile material. The central fear was rooted in the risks of Radiological Dispersion Devices [RDD] and the parallel concern about direct attacks on nuclear power plants where surprise assaults by terror groups could trigger. Chornobyl or Fukushima tragedies release tons of radioactive steam via penetration of the processing core, disabling its safety controls or otherwise enflaming outdoor pools of spent nuclear fuel points to other risks. It was also assumed that terror groups after 9-11 were inclined to acquire, purchase, or steal enough radiological or nuclear material to fabricate a real or ‘dirty’ bomb. (Bunn, 2021) (DHS, Radiological Attack Fact Sheet, 2022)
A politically-charged chameleon type aphorism like the metaverse invites scrutiny. On the one hand, people would like to confine the metaverse to an extrapolation of the internet and praise it as simply the IoT and nothing more. However, other legitimate aspects of the metaverse, such as its 3-D properties exploiting neuromechanics and biomechanics, are not well understood. It blends spatial computing capabilities, game engine capabilities, brain-computer interface options, digital twin potential, and parallel replica utility using engineered virtual reality. Its tendency to employ advanced algorithms to exclude humans from controlling or monitoring their covert activities—or making them virtually undetectable—is not beyond comprehension. So, sorting out aspects of hidden connectivity between RF, radiological, and the electromagnetic spectrum remains puzzling exactly because their relationships are opaque and diffuse. Not easy to identify, decode or discern. Their obvious and unintended outcomes linger to haunt us.
Radiological must be understood in this way– a radiological weapon means any device, other than a manufactured nuclear explosive, specifically designed to employ radioactive material by disseminating it via crude explosion, aerosol, injection, dispersion, or aerial spraying to cause human destruction, damage, or injury, employing the emitted gamma or beta radiation over the years produced by the decay of such material.
This term encompasses most objects created expressly to distribute harmful radioactive materials as broadly and extensively as possible by various means. This is quite different from the risks and security implications of EMP attacks. Electromagnetic Pulse triggered by a high-altitude nuclear blast inflicts widespread electronic failure and chaos on organized society with minimal radiation effects. (Reports, 2018)
Likewise, it is also important to vehemently disprove those who mistakenly claim Iraq had no WMD—the fact is Iraq’s technical infrastructure. Its resident nuclear science experts had the sophisticated capability to do so eventually without ever devising a tested weapon. In effect, the capability to produce WMD is sacrosanct and cannot be severed conveniently from the possession of actual WMD weaponry. (Scientists, 2009)
Good radiation can play a part in cancer therapy, blood irradiation, medical and food sterilization, structure and equipment testing, geologic exploration, and instrument calibration. Gamma rays emitted by cesium and cobalt can kill germs multiplying in your meat and make your apples last longer. Affirming the positive value of radiological is important. (Scoles, 2022)
Finally, the related issue involving the possible effects of radiofrequency-electromagnetic field (RF-EMF) on the human body requires an appreciation for several factors which indicate harmful EMF impact on animal models. RF-EMF can induce changes in central nervous system nerve cells, including neuronal cell apoptosis, changes in the function of the nerve myelin and ion channels. Therefore, it is necessary to study the biological response to RF-EMF in consideration of the comprehensive exposure concerning the use of various devices by individuals. In this review, we summarize the possible biological effects of RF-EMF exposure. ((Seoul), 2018) (Ju Hwan Kim, 2019)
Security and safety are paramount with just over the 25 research reactors on college campuses. These reactors have a limited amount of radioactive material on site and pose a low risk from radiation and the theft of nuclear material. The NRC inspects the reactor’s security and emergency plans and its operations and design to ensure public health and safety protection with increasing requirements for material that is less attractive for theft or diversion. The NRC continues to inspect research and test reactors to ensure compliance with all NRC regulations to protect t public health and safety. (NRC, 2017)
In sum, the risks of radiological weapons today after 2022, just as they were at the end of WWII, remain embedded in the variety of mechanisms and inventions which enable the widest possible distribution of harmful radioactivity and which are inextricably linked to evolving technology that more precisely and reliably magnifies that distribution. While the overall threat of radiological emergency or deliberate attack seems relatively low, the risk of accident, sabotage, terrorism, or system malfunction cannot be easily dismissed. Since events like Three Mile Island, Chornobyl, and Fukushima, we have learned that natural disasters, operator error, and systems malfunction can cause a serious radiological emergency with contaminant radiation dwelling in the affected area for many decades rendering the compromised area uninhabitable. Future radiological weapons will grow in complexity and residual lethality as future enabling and supporting advanced technologies further magnify and directly target human groups in cities and heavily populated areas of industrial activity where radioactive contamination can harm many.
THE NATURE OF RADIOLOGICAL, ELECTROMAGNETIC, AND DRONE RISK INSIDE THE METAVERSE
It is now a broad and ill-defined strategic question connected to several technical challenges, asking how the risk terrain after 2022 should be understood for CONV-CBRN events and its connection to other emerging technology? No easy answer comes to mind as the blended and re-engineered mix of convergent technologies, supported and enabled by AI. Cyber enhancements create a milieu of threat dynamics never before seen. Risk estimation becomes a blend of alchemy, science, technology, countermeasures, and conjecture supplanted by the imperfections of warning intelligence. Victims of targeted epigenetic neuromodulation rooted in electromagnetic, nano pulsed RF [radio frequency], and acoustic pulse combinations cannot fathom how they have been neurologically compromised or wounded. The medical profession has no diagnostic framework or treatment architecture and therapeutic strategy to treat these victims of so-called Havana Syndrome and tends to write them off as psychotic or hallucinogenic. The key is that a precise neuro-cognitive strike has been inflicted. Nobody can verify it has happened—neither the victim nor the so-called medical professional who examines the victim. So, we dwell in an era of neurocognitive warfare, ignorant of its effects.
If we absorb targeted neurological attacks which go undetected and evidence of covert neurological harm cannot be verified, we are in a season of strategic jeopardy. This is gradual and insidious as propaganda, disinformation, deceit, information warfare, and social media manipulation slowly and deliberately chisel away our rational thought and analysis filters. We fall victim to Psychological Operations [PsyOp] without realizing we have been duped until too late. Deep Fake technology using President Obama’s voice artificially imposed on another’s body and face exemplifies the calculated deception aimed at mass influence. The fact that many millions can fall victim to this ‘deep fake’ scheme and be falsely manipulated is technologically possible. However, we would like to believe otherwise.
One chief issue involves strategic warning and the specific indicators and sensors which reflect a robust technology designed to signal and alert friendly nations of impending CONV-CBRN incursions and attacks of a non-kinetic nature. How should that be done? How would future societies discern when they are under real-time vs. virtual threats of immediate attack? How would the virtual and the real components of such a threat be sorted out? What merged versions of radiology, electromagnetics, drones, and the metaverse can be ably diagnosed as a threat and deterred given the near-term availability of their CONV-CBRN options 2022—2025??
How has the existence of CONV-CBRN itself changed the very definition of a strategic threat? What is the near-term vs. long-term impact on society and security? What is infrastructure governance necessary to curtail and control its worst effects? What optional and viable countermeasures and deterrent technologies can be assembled to thwart the incipient CONV-CBRN threat after 2022? When the AI, cyber, and metaverse aspects are included in such an analysis, does this signify an unbounded mix of virtual and real weapons platforms that can have both a biophysical and a neurophysiological effect? If combined radiological, electromagnetic, and drone technologies inflict widespread neuro-cognitive harm in undetectable ways, what does that imply for reserve use of kinetic firepower? If a target population is rendered incapable of performing basic human behavioral tasks or rational analysis by such technology can, we say the attacker has ‘won the battle without firing a shot, as ancient Chinese philosopher Sun Tzu argued in the 6th century BC essay ‘The Art of War.’ (Tzu, 475 – 221 B.C.E.)
Given the pervasive global existence of CONV-CBRN technologies among the world’s leading military and economic superpowers, this begs how geostrategic risk should be constructed and defined. If this threshold threat dynamic is another decade distant, we may have enough time to contend with it. However, the CONV-CBRN warfare era augmented by drones is already upon us then our efforts to deflect or mitigate its worst effects will be a perpetual catch-up game. Therefore, risk analysis itself is hampered, blinded, and constrained by a myopic vision of what convergent technology suggests is possible.
Failure to imagine the most sweeping scope of high-tech threats immediately as derived from the CONV-CBRN risk terrain coupled with AI, cyber, metaverse and drone technology is to miss the most colossally disruptive tidal wave of the 21st century. Who can reliably estimate the strategic risks and nuanced implications of a carefully engineered and convergent blend of quantum, robotics, nanotech, biotech, drones, AI, cyber, and its operational significance in a mixed metaverse? Are we even equipped to conduct and calibrate an objective risk analysis of this aggregation? (McCreight R., Convergent Technology and Future Strategic Threat, 2013)
RADIOLOGICAL AND ELECTROMAGNETIC RISKS AND THE ERA OF COGNITIVE WARFARE
Technologies derived from the electromagnetic spectrum can damage the human brain, especially if targeted nano pulsed RF and acoustic waves are used to adversely affect cognition and normal brain function. Neurological vulnerability [NV], the dawn of what the author terms “NeuroStrike’, and the era of cognitive warfare are here now. Not decades away as some would view it. The central thesis is that we have been amid hostile brain hacking and elementary forms of cognitive warfare for at least 12 years. NV attacks via the mastoid bone, vestibular, and otolith systems and our proprioceptive systems by harmful externally based technologies have been targeting persons for quite some time. This is integral and crucial to grasping future CONV-CBRN conflict rather than seeing it as excessive. (McCreight R., NeuroStrike Weapons and the Strategic Domain after 2020: Caution, 2021)
While IO and influence operations in 2014 were not seen strictly as ‘cognitive warfare,’ the overall intent was to steer popular confusion towards an empathetic view of Russia’s invading forces in Crimea, offering important clues for the interplay between IOs kinetic activity. The course of events – from the takeover of parliament in Simferopol and dismantling of the Ukrainian military presence on the peninsula to the disputed referendum and the de facto annexation of the area to the Russian Federation – was accompanied by intense activity aimed at controlling the flow of information and influence public opinion in ways designed to divert civil attention away from Russia’s operational battle aims. This activity extended across the entire spectrum of communication and included kinetic, cyber, and IOs targeting the physical, logical, and social layers of communication. This must be understood as part of Russia’s Information Warfare [IW] campaign. The interplay between different levels of information – from the political leadership of President Putin at the tip, via the traditional media to the grassroots level in social media – and propaganda appears to be an important core element of Russian IW.
One of the core narratives surrounds Russia’s position in the world: a misunderstood counterweight to Western liberal values and a misjudged historic superpower. This narrative is slim and can be easily absorbed by the general population and even groups abroad. For example, nationalist groups focus on Russia’s historical position of power, while communist groups discuss Russian antagonism to capitalism regarding the Soviet era. (Jaitner, 2014) Today we witness it daily in the bloody Ukraine conflict as a necessary companion to outright murder.
The more sophisticated and the non-kinetic aspects of stealthily influencing perception, thinking, and normal brain functions created an invisible and undetectable technology that Russia used systematically on our diplomats in Havana, Cuba-known as AHI. The use of covert technology designed to disable and degrade human thought, induce psychomotor disruption and a variety of discernible symptoms like loss of balance, speech erosion, tinnitus, frequent headaches, and other documented issues must be viewed as the current generation of cognitive warfare technology which continues to puzzle neuroscience experts and seasoned medical professionals. (Sciences, 2020)(Haines, 2022) Even today, we wrestle with the bona fides of those complaining of AHI and how best to diagnose and treat them. The absence of a consensus case definition and divergent theories on therapeutic strategies loom. In the interim, the threat continues to our diplomats, IC staff, and military leadership posted overseas and a few disturbing cases here at home. As long as the enemy targets our personnel and attacks them in small groups of 12 or less, we can safely relegate these bizarre events to the bottom of the priority pack. (Nelson, 2022)
Radiation-induced brain injury can result in cognitive dysfunction, including hippocampal-related learning and memory dysfunction that can escalate to dementia. Our current understanding of the mechanisms behind radiation-induced brain injury, focusing on the role of neuroinflammation and reduced hippocampal neurogenesis, remains useful. (Turnquist, 2020) (Linda Douw, 2009) Risk assessments of the radiological and electromagnetic impact on normal brain function and neurological well-being are not as further in research as we might expect or desire. Now 2022 finds us in an unrestricted cognitive warfare battlefield where multi-domain operations must somehow account for these factors blended with various non-kinetic technologies. Where are we then? The array of radiological risks arising from fissures in nuclear plant containment towers, mixing high explosives with radiological elements, and ambient radiation from various medical and food processing sites are reflective of well-known risks. Do we grasp the full array of radiological risks which may arise? What about the radiological risks in our immediate environment, such as radioactive isotopes in potable water systems or derived cadmium from disturbing sandy grounds, which may be more prevalent than imagined. (EPA, 2012)
FIGURE 4.1 Where Do Mobile Phones Fit?
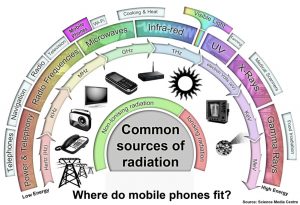
Source: https://www.sciencemediacentre.co.nz/infographics/ (sciencemediacentre.co.nz, 2022)
The fact that US military briefings and reports referred to this phenomenon in 2015 and 2016 as an ambiguous yet burgeoning hostile and clandestine threat that US forces and allies must contend with doesn’t alter the fact that simple awareness of cognitive warfare in its earliest stages took a back seat to sexier and more sophisticated weapons systems. Hypersonics, cyber-attacks, and other systems crowded out sustained attention to cognitive warfare so consistently that the interim response was limited, cautious, and late by the time we had verifiable victims of it. This briefing slide from 2015 illustrates the limited strategic view our SOCOM leaders attributed to the risks of cognitive warfare. (SOCOM, 2015) If the threat is recognized as valid, but no countermeasures are formed to neutralize it, the net result will grant a battlefield advantage to those possessing this disruptive technology.
Figure 4.2 Cognitive Key Terrain Within a Generational Struggle
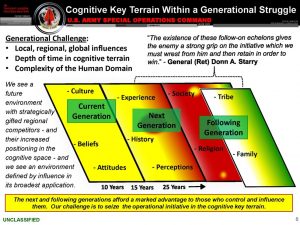
Source: (Ryan, 2014)
THREAT DYNAMICS—RADIOLOGICAL AND ELECTROMAGNETIC ISSUES POST 2021
The spectrum of radiological risk to society and security has become obscure, opaque, and otherworldly. Obscure that many believe radiological risk, including the prospect of such weapons as a ‘dirty bomb,’ is a distant worry dwarfed and stoked by seven decades of apocalyptic nuclear war fears. The radiological risk was also seen as opaque by many. Some experts saw a radiological weapon’s technical requirements and instrumental risks as low probability, unlikely and speculative. However, events like Chornobyl, Fukushima, and the environmental calamity involving Cesium-137 at Goiania made us reckon with the radiological risks we tolerate in exchange for a measure of reliable nuclear power and the application of nuclear medicine technologies. To define our terms for this purpose, a widely cited descriptive definition of a radiological weapon reads– a radiological weapon means any device, other than a manufactured nuclear explosive, specifically designed to employ radioactive material by disseminating it via crude explosion, aerosol, injection, dispersion or aerial spraying to cause human destruction, damage, or injury, through the emitted gamma or beta radiation over the years produced by the decay of such material. This term encompasses most objects created expressly to distribute harmful radioactive materials as broadly and extensively as possible by various means. (DHS, countering-weapons-mass-destruction, 2022)
Congressional, press, and academic discussions were gradually discounted in favor of the increasingly complex, insidious, and divergent future technologies expected to damage our security more readily or effectively. This was underscored in great detail by the NERC EMP task force report to Congress in 2019. (NERC, 2019) This report drew attention, however temporary, to the implied crisis of radiological risks emanating from a poorly understood radiological threat. (NERC, 2019). In addition, we are aware of the so-called ‘dirty bomb’ issue where high explosives can be attached to detonate with highly radioactive substances like Cobalt 60 or Strontium 90 and render an entire area of many square miles contaminated for decades. Imagine where other radiological risks and dangers can eventually be linked to CONV-CBRN, electromagnetic, drone, and metaverse exploitation. That intent on evil is well aware of it.
We saw the significance and impact of using passive nuclear power plants in the Russo-Ukraine war in 2022 as pivotal in changing the threat dynamics of the battlefield. There are claims and counterclaims about whose weaponry and artillery targeted the main reactors at Ukraine’s largest nuclear plant. On February 5, 2022, Russia took control of Europe’s largest nuclear power station in Ukraine after a shelling hit it. Both sides argued the other put the plants’ safety in jeopardy. Ukrainian officials said a fire started at the Zaporizhian plant after being shelled by Russian troops. The Russians claim their part. They did not shell the facility at all. To everyone’s relief, the UN’s nuclear watchdog IAEA said radiation levels and the safety of reactors were not affected. Here the sterling issue is the contending and contradictory claims which cannot be readily verified and if containment was breached. Sadly, the issuance of radioactive gas and fumes or setting spent fuel ponds afire would have triggered a radiological disaster of international proportions. That crisis would have thwarted serious attempts to discern who attacked the site. So, post-disaster attribution, where responsibility is assigned to those held liable for the attack, becomes an ambiguous and ill-defined mess. (News, 2022)
Zeal for upgrading interest in radiological issues waned as experts concentrated on the power of nuclear weapons alone. When one inspects the electromagnetic spectrum in detail, we find the following distribution of phenomena which identify where certain electromagnetic technologies exert a radiological series of effects—some lethal and harmful—others much less so.
Figure 4.3 Radiological Spectrum//Earth, Sky, Net
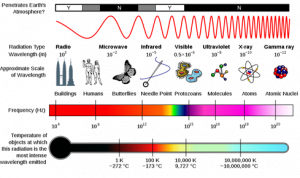
Source: (EarthSky – Earth, 2019)
From a quick scan of this chart Figure 4.3, one can readily point to areas on the electromagnetic spectrum where divergent waves and beams can affect human life in a harmful or benign way. When the electromagnetic set of issues is seen through radiological threats, we must also accept the proven negative influence of pulsed radiofrequency [RF] signals to inflict both biophysical and neurophysiological harm. A 1950s-era program known as “Atoms for Peace ” that US President Eisenhower launched to encourage a larger role for private industry in developing nuclear-power plants worldwide allowed nations bereft of nuclear weapons to pursue nuclear power still covertly and slowly use their nuclear power stations. They could enrich uranium and engage in covert processing of fissile material outside conventional inspection and review systems. In addition, the history of intelligence theft of nuclear technology contributed to the increase of nuclear weapons states to well over 12 nations. [US, Russia, China, UK, France, North Korea, Iran, South Africa, Brazil, India, Pakistan, and Israel possessed robust nuclear infrastructures with other undesignated nations. (Library, 2022)
In physics, electromagnetic radiation (EMR) consists of electromagnetic (EM) waves propagating through space, carrying electromagnetic radiant energy. It includes radio waves, microwaves, infrared, (visible) light, ultraviolet, X-rays, and gamma rays. These waves form part of the electromagnetic spectrum and span the risk intensity from serious to harmless, including frequencies used for communications signals (as for radio and television broadcasting and cellphone and satellite transmissions) or radar systems. (Scarpati, 2021) (AARL, 2022) (FCC, 2022) See Figure 4.1. (sciencemediacentre.co.NZ, 2022)
Non-nuclear weapons states which have nuclear power plants on their soil number 314 according to the IAEA, which oversees global nuclear power reactors. (IAEA, 2018) Here the raw significance of these power reactors is the inherent risk of operational accident, terrorism, system safety breach triggered by natural disasters, and disintegration of safety systems in aged reactors approaching 50 years of useful life. They also reflect a potential nuclear weapons option.
In sum, the risks of radiological weapons today after 2021, just as they were emerging at the end of WWII, remains embedded in the variety of mechanisms and inventions which enable the widest possible distribution of harmful radioactivity due to terrorism accidents, operator error, or natural disaster. The overall risks from residual radiation after a nuclear blast are significant and overwhelming—so too are the many other radiation risks arising from the focused application of emerging technologies. (FAS, 1998) (globalsecurity.org, 2022) (NATO)
GRASPING THE NON-KINETIC ASPECTS OF CONV-CBRN
Added to the scope and depth of CONV-CBRN when drones, AI, Cyber, and electromagnetic are infused into the threat picture is to assess the significance of non-kinetics in the milieu. Here we suggest a wide variety of non-kinetic but truly disabling, disruptive, and debilitating technologies orchestrated by a determined foe who seeks to undermine and weaken his political civilian and corporate executive ranks via these measures. A wide variety of effects-based operations [EBO], which often go unnoticed or ignored in protracted ‘ghost guerilla warfare’ efforts, can occur outside notice. This is the emerging domain of non-kinetic warfare [NKW]. Nonkinetic warfare [NKW] options available to an enemy who can influence, persuade, enflame, discourage, overwhelm, weaken, or confuse targeted populations as part of a broader geopolitical offensive running over several years exerts its insidious and impressive effects where the focus is more psychological, more sociocultural, and more subtle as it stealthily undermines the fabric of social cohesion and identity. NKW disturbs and exploits the popular civil-social-urban environment behind an unsuspecting military to the extent that it erodes the foundation of community support for its forces and their strategic disposition.
NKW is not ‘asymmetric warfare’ as we often define it, where a battle between unequal belligerents is balanced via a determined insurgency or resistance movement capable of equivalent destructive outcomes inflicting harm on a superior force with unsophisticated tools and technologies that can be exercised frequently and covertly to acquire an unseen and undetectable strategic edge among a target population. Some experts have viewed NKW as a smoothly integrated mix of information, electromagnetic, and cyber warfare inside a digital environment to generate unique battlefield capabilities. (Henselmann, 2022)
The challenge to advocates of deterrence theory is that NKW is not easily thwarted until it has done its intended damage. Nonkinetic systems operate within frontiers of conflict beyond normal imagination. This reflects the so-called phigital world where digital and human characteristics patterns and essential ingredients overlap in indiscernible ways. The deceptive curtain of A/R or V/R intrudes on our layered perception impeding our ability to discern fact from illusion.
Science has recently demonstrated almost no barriers linking common human functional biology to artificially created neurons. Brain implants, advanced prosthetics, and a wide range of medical implants and wearable devices rely on links between the body’s autonomic nervous system and electronic circuits. Swedish researchers have found a better alternative to creating artificial neurons and synapses—the basic linking structures that connect two neurons—out of organic semiconductors that are biocompatible, biodegradable, soft, and can carry both electronic and ionic signals. The main pieces of natural biology can be merged and coupled with engineered materials to create operational and functional links. Scientists showed that the synapses were capable of Hebbian learning, which is how the strength of the connection between any two neurons increases or decreases based on activity. This means neurons are activated and connected with other neurons, forming a neural network that at first starts weak but grows stronger and stronger with each stimulus. The new hybrid cell becomes more intuitive with the strengths of connections between neurons controlling the function of different brain circuits. We have far beyond the idea of a brain-computer interface which brings us closer to a genuine cyborg option in defense matters. (Gent, 2022)
A world where RF radiation and electromagnetics are merged via engineering creates a unique defensive challenge. Here the value of ‘anechoic’ chambers, which means ‘without echo,’ creates chambers are spaces designed to have minimal wave reflection from the walls, ceiling, and floor. Understanding Anechoic Chambers for Electromagnetic and RF Testing (Arar, 2022). Electronics engineers use anechoic chambers for electromagnetic compatibility (EMC) or electromagnetic interference (EMI) and RF testing. The interior walls of these chambers are treated with special material to absorb electromagnetic waves and thwart emanations that absorb sound waves rather than electromagnetic energy. See Figure 4.4.
Figure 4.4 a&b Two different anechoic chambers—one large and one small.


Source: (Schwarz) (Okula)
EMF radiation refers to low-frequency magnetic fields emitted by powerlines, household appliances, and power outlets. RF radiation refers to high-frequency electromagnetic radiation emitted by wireless equipment like cell towers, cellphones, GPS, televisions, and radios. Wireless networks inside our homes and workspaces have also become a major source of RF radiation. Although both EMF radiation and RF radiation have many similarities, they also have several key differences that affect how these electromagnetic energy forces interact with our bodies. (NIEH, 2022) Other things that emit EMF radiation may include Cellphones, Laptops, TV, Computers, Microwave Ovens Wi-Fi Devices; you can see there may be several common household and workplace items exposing you to EMF radiation. Consistent exposure to EMF radiation can have significant health consequences. Tests have shown that the closer you are to an object emitting EMF radiation, the higher the amount of EMF radiation you will be exposed to.
Chaos theory may be helpful as it tackles apparent randomness involving complex systems with underlying patterns, interconnectedness, constant feedback loops, repetition, and self-organization. According to Chaos Theory, changes arising inside tiny things or events can change the world. Examples include the stock market, weather, human psychology, and natural disaster cycles. Chaos Theory does not provide a comprehensive answer to dealing with a complex threat environment where CONV-CBRN, electromagnetic, NKW, drones, and radiological factors intermingle. (Straussfogel, 2009 )]
The scope and scale of ever-widening avenues for mixed applications of diverse technologies after 2022 creating hybrid systems and semi-human pathways to magnify what ordinary persons can perform or demonstrate and utilize it in both helpful and harmful ways, are eye-opening. Having said all of these views are legitimate and persuasive to a degree, we remain stuck with the realities of CONV-CBRN today, where drones, electromagnetic, radiological, and non-kinetics appear to dominate the threats we face after 2022. We find ourselves inside a complex, multi-dimensional, inherently multifaceted dilemma, requiring a broad and sweeping appreciation for unlimited technology convergence’s immediate and long-term implications. The evolution of CONV-CBRN as its morphs after 2022 is unlikely to be static or unchanging. A crazy combination of CONV-CBRN, electromagnetic, NKW, and radiological phenomena is possible. The unknown effects of routine and unrestricted technology convergence are not well understood, and thematic steps invoked to govern and regulate what happens in that space will defy easy solutions. Arguably, it begins with a realistic vision of the full spectrum, themes, and issues when we try to define that threat. If seen in combination with cascading influence and affect, the picture acquires greater complexity; to assume we have enough data and information is incorrect.
Figure 4.5 CONV-CBRN Threat Dynamics
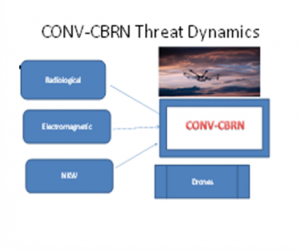
Source: (McCreight R., 2013)
Is it the special mix of lethal and non-kinetic technologies which draw their collective and convergent power from each other based on cutting-edge dual-use science? Or instead, can we posit the argument that they constitute a threat only when combined and engineered in unison, unlike any we have seen before? Grasping threat issues post-2022 requires a sharper, more focused, and comprehensive lens to know what this set of geostrategic challenges signifies.
SPECIAL DELIVERY OF DEATH AND DESTRUCTION: —ADDING DRONE RISK FACTORS POST 2021
On the one hand, drones appear to have some benign characteristics delivering pizzas, packages for Amazon, snapping powerful aerial nature photos, emergency rescue, standoff environmental monitoring, precision agriculture, and much-needed medications to isolated areas. However, their insidious dual-use nature allows them to be used as special delivery vehicles for death and destruction as their inherent value in wartime appears both appealing and overwhelming. The prospect of using drones in strictly beneficial and socially pleasing ways runs counter to their diligent, appealing, and expansive use as expedient instruments of warfare.
Experts warn of drone swarms numbering in hundreds, all designed to deliver a damaging payload powered by remote signals and near autonomy in their designated target options. As such, recognizing them, defending against them, and neutralizing their combined effect becomes the artful and scientific blend of anti-drone warfare and related technology. This is being emphasized simply because all we have summarized and described thus far—CONV-CBRN, NKW, electromagnetic, and conventional weaponry can be mounted on drones to maximize their harmful and lethal capabilities. The list of conceivable drone-based threats is virtually unlimited in scope. Several persuasive examples come to mind here as just a few battlefield scenarios are cited
–Turkish drones supplied to Ukraine to fend off Russian attacks during the 2022 war indicate their utility and lethality (Malsi, 2022)
–Some experts claim that drone use leads to unlimited and unexpected scenarios where repetitive international drone warfare continues relentlessly simply based on their ubiquity and ease of operation. (Martin, 2016)
–Avenger # UAS was recently integrated with a virtual swarm of other UAS, which in unison searched and tracked an artificially generated adversary through the use of AI/ML algorithms, deciding which aircraft would autonomously ‘break’ from the pack and perform closed-loop, air-to-air tactics displaying autonomy by using a blend of simulated threats, real-world sensors, and live aircraft where robust autonomy was combined with machine learning to validate unmanned aircraft illustrating complex kill chains. (Grinter, 2021)
–Unintentional or deliberate GPS interference and jamming, along with the capability to detect and geolocate origins and sources of GPS interference, enables technologically equipped forces to detect and nullify frequent disruptions to friendly UAVs and thereby thwart the ‘global commons’ that all modern economies depend upon. Launching GPS signal interference can disrupt air travel, logistics, finance, transportation, communication, and many other aspects of ordinary life, preventing people, vehicles, ships, and planes from determining their accurate position or confirming their targeted locations. Such jamming can cripple the government and commercial operations over thousands of square miles. (hawkeye-360, 2022)
— Use of multiplatform counter-UAS system (CUS), relying on a team of mini-drones acting as a cooperative defensive system for sensing, mitigation, and C2 control systems that generally comprise a counter-drone network. (Castrillo, 2022)
–AFRL is building a system to zap small unmanned aerial systems with high-powered microwaves and disable them called THOR for Tactical High Power Operational Responder. (Losey, 2022)
–Unmanned drones monitoring the skies watching from multiple perspectives, using multiple sensors can loiter using its infrared search-and-track sensor to spot any hostile aircraft as they climb out from the clouds. AI-enabled autonomous systems onboard the drones can verify the location of the hostile jet’s launch, its speed, and other features to confirm its ‘friend or foe’ status. Data relayed in real-time to human commanders seeking combat response decisions allow the human-occupied aircraft can stay in touch. Hence, every human pilot in the area gets an alert immediately after the friendly UAVs identify the suspect plane and conclude whether attack conditions are right. (SYSTEMS, 2022)
As platforms for delivering lethality and related strike packages, drones are an option with real tactical leverage in combat. They are not invincible, but the variety of their military application is beyond the limit. The issue of armed drones and combat-equipped UAVs has become the principal instrument of tactical battlefield leverage since 2015, with extensive use of drones in the theaters of war in the Mid-East and Afghanistan. The real question is, how do drones maximize combat lethality in specific ways after 2022?
CONV-CBRN DRONE AUGMENTED THREAT AND RISK POSSIBLE SCENARIOS
Certain drone-enabled scenarios can be considered mechanisms for executing a combined CONV-CBRN attack where mixes of electromagnetic, radiological, and NKW elements can be added. These notional scenarios seem plausible and surface the overall implications for defensive strategies to offset their initial advantages. See Figure 4.6.
–drone bore laser attack on spent fuel ponds involving targeted explosives at a nuclear plant
–drone – borne laser or precision explosive attack on spent fuel truck convoys
–drone- borne laser or augmented kinetic attacks on nuclear waste storage sites
–drone -borne precision explosive attacks at University research nuclear labs
–drone- bore NKW Electromagnetic attack on nuclear plant safety operators
–drone-bore NKW attacks on spent fuel convoy drivers and security personnel
— drone-borne targeted CW attack on nuclear-reprocessing facilities and security staff. (McCreight M. S., 2020)
In addition, one more terrifying thought: Swarming drones equipped with EW enhanced platforms to beam sustained hostile RF pulsed waves can prepare the battlefield in a comprehensive nonkinetic operation, adversely affecting civilians and military personnel for which limited defense options exist.
The task of doctrinal writers and strategic military planners is to estimate what this scenario entails and requires as we confront a future battlefield where the mind is a preferred target over anything else. (McCreight R., Another future scenario, 2022)
Figure 4.6 Setting the Stage for NV
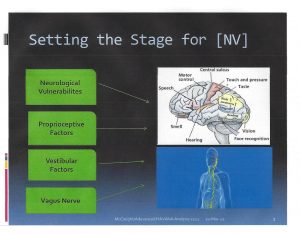
Source: (McCreight R., 2013) (McCreight M. S., 2020)
CONV-CBRN–ONWARD SECURITY AND RISK CHALLENGES POST-2021
Mixing CONV-CBRN, electromagnetics, drones, NKW, and the metaverse would create an imaginary fabrication of threats confronting us after 2022 to the extent that many experts would view this risk as highly regarded improbable or evidence of science fiction. This would be a strategic blunder of the first order. Failing to recognize or characterize these threats—even in speculative wargames where risk scenarios are deeply explored—is a must. A world where these mixed technologies proliferate is central to future conflict and bedrock for strategic imagination. The issues and technologies covered in this chapter are meant to foster greater awareness of the Dual-Use Science and Technology threat [DUST], which is relentless as advances in science and technology hold no rational filter against nefarious and destructive purposes. As national and sovereign designs on greater military power where no apparent defenses or strategic warning systems exist, one can expect this space to become increasingly crowded. It is important to probe and define the entire threat spectrum where these issues and challenges remain a strategic challenge for the next decade. Experts dedicated to discerning the scope and scale of tomorrow’s expected and unexpected areas of disruption, chaos, crisis, and calamity owe it to themselves to rigorously examine the warnings included here. (McCreight T.-F.-C. T., 2020)
DISCUSSION QUESTIONS
1-What is the strategic significance that can be assigned to CONV-CBRN?
2-How do electromagnetic and radiological issues affect our understanding of strategic threats?
3-Why should we be concerned about NKW and the technologies it represents?
4-What aspects of radiological threats combined with electromagnetic warrant further research?
5- Does it make sense to include considerations of the metaverse when assessing how a mix of advanced technologies such as CONV-CBRN, radiological, electromagnetics, and NKW can be seen independently as threats by themselves?
6-What threat and risk scenarios involving drones and the technologies discussed in this chapter pose unique strategic threats?
Bibliography
(Seoul), B. T. (2018, November 27). RF-EMF Exposure. Retrieved from Published online 2018 Nov 27. doi: 10.4062/biomolther.2018.152: doi: 10.4062/biomolther.2018.152
AARL. (2022, March 18). RF Radiation and Electromagnetic Field Safety. Retrieved from https://www.arrl.org/: https://www.arrl.org/rf-radiation-and-electromagnetic-field-safety/
Arar, S. (2022, Feb 9). All About Circuits Understanding. Retrieved from www.allaboutcircuits.com/technical: HTTPs://www.allaboutcircuits.com/technical
Ball, M. (2020, January 13). The Metaverse: What It Is, Where to Find It, and Who Will Govern it. Retrieved from https://www.matthewball.vc/all/themetaverse/: https://www.matthewball.vc/all/themetaverse/Jan 13, 2020
Bunn, M. (2021). The evolving global threat to nuclear and radiological. Retrieved from https://scholar.harvard.edu: https://scholar.harvard.edu/files/matthew_bunn/files/transport-threat-brief-2021.pdf
Castrillo, V. (2022, Feb). A Review of Counter UAS Technologies for Cooperative Defense Teams of Drones. Italian Aerospace Research Center. Drones, p. 6.
CDC. (2022, March 18). CDC, Radiological Threat Agents, 2015. Retrieved from CDC: https://www.cdc.gov/
DHS. (2022, March 18). countering-weapons-mass-destruction. Retrieved from www.dhs.gov/: https://www.dhs.gov/countering-weapons-mass-destruction-office
DHS. (2022, March 18). Radiological Attack Fact Sheet. Retrieved from https://www.dhs.gov/publication/: https://www.dhs.gov/publication/radiological-attack-fact-sheet]
EarthSky – Earth, S. H. (2019). EarthSky – Earth, Space, Human World, Tonight. Retrieved from earthsky.org//2019: https://earthsky.org//2019
EPA, [. (2012). Radiation Facts, Risks, and Realities—US Government. Washington: [US EPA – US Government].
FAS, M. /. (1998). Nuclear Weapons Effects Technology Militarily Critical Technologies List (MCTL). Retrieved from irp.fas.org/threat: https://irp.fas.org/threat/mctl98-2/
FCC. (2022, March 18). The effects of radiofrequency electromagnetic radiation on Human Health. Retrieved from https://ecfsapi.fcc.gov/: https://ecfsapi.fcc.gov/file/1093016723166/RF
Gent, E. (2022, February 25). Scientists Create Artificial Neurons that Power a Venus Fly Trap. Retrieved from techbely.com: http://techbely.com/scientists-created-synthetic-neurons-that-can-make-a-venus-flytrap-snap/
globalsecurity.org. (2022, March 18). Weapons of Mass Destruction (WMD). Retrieved from www.globalsecurity.org: https://www.globalsecurity.org/wmd/intro/nuke.htm
Grinter, P. (2021, Aug 25). Avenger UAS Autonomously Tracks and Follows Target Aircraft. Unmanned Systems Technology.
Haines, D. (2022). Executive Summary, Feb 2, 2022, Analysis of Pending AHI Cases – Redacted. Washington: DNI.
hawkeye-360. (2022, March 4). hawkeye-360-signal-detection-reveals-GPS-interference-in-Ukraine. Retrieved from www.he360.com/: https://www.he360.com/hawkeye-360-signal-detection-reveals-gps-interference-in-ukraine/
Henselmann, M. L. (2022, March 18). Non-Kinetic Warfare: The New Game Changer in the Battle Space. Retrieved from University of Jyväskylä, Finland : DOI: 10.34190/ICCWS.20.033].
IAEA. (2018). IAEA Safety Standards: Regulations for the Safe Transport of Radioactive Material. Retrieved from www-pub.iaea.org/: https://www-pub.iaea.org/MTCD/Publications/PDF/PUB1798_web.pdf
Jaitner, M. (2014). Russian Information Warfare. Conference Paper, Swedish Defense Research Agency. Swedish Defense Research Agency.
Ju Hwan Kim, J.-K. L.-G. (2019, May 1). PMCID: PMC6513191PMID: 30481957 Possible Effects of Radiofrequency Electromagnetic Field Exposure on Central Nerve System. Retrieved from https://pubmed.ncbi.nlm.nih.gov/: https://pubmed.ncbi.nlm.nih.gov/30481957/
Library, E. P. (2022, March 18). Atoms for Peace. Retrieved from www.eisenhowerlibrary.gov/research/: www.eisenhowerlibrary.gov/research/online-documents/atoms-peace]
Linda Douw, M. K. (2009). Cognitive and radiological effects of radiotherapy in patients with low-grade glioma. Lancet Neurology, Sept.
Losey, S. (2022, Feb 28). Killing drones with Thor’s hammer: Air Force eyes counter-UAS Weapon. Defense News.
Malsi, B. F. (2022, February 27). Ukraine Says It Used Turkish-Made Drones to Hit Russian Targets. WSJ.
Martin, J. (2016). Drone Nation-America’s New Way of War. Lexington Books.
McCreight, M. S. (2020, Sept). Quantum Conundrum: Multi-domain Threats, Convergent Technology & Hybrid Strategy, US Amy Futures Command. Mad Scientist #268.
McCreight, R. (2013, October). Convergent Technology and Future Strategic Threat. Strategic Studies Quarterly, pp. 10-18.
McCreight, R. (2013, March ). Convergent Technology Threats. Strategic Studies Quarterly, USAF Air University.
McCreight, R. (2022, April 6). Another future scenario. Private email to Managing Editor, R. K. Nichols.
McCreight, R. (2021). NeuroStrike Weapons and the Strategic Domain after 2020: Caution. Academia Letters, 2021.
McCreight, T.-F.-C. T. (2020, February 24). Twenty-First-Century Threats in a Complex World: Dealing with DUST in the Wind. Wild Blue Yonder / Maxwell.
NATO. (n.d.). NATO HANDBOOK ON THE MEDICAL ASPECTS OF NBC DEFENSIVE. Retrieved from http://large.stanford.edu/courses/2019/ph241/abbate2/docs/fm8-9.pdf: http://large.stanford.edu/courses/2019/ph241/abbate2/docs/fm8-9.pdf
Nelson, K. (2022, February 20). What Could be Causing Havana Syndrome Cases on US Soil? CBS News.
NERC. (2019, November 5). nerc_emp_task_force_report.pdf. Retrieved from nerc.com/pa/: https://nerc.com/pa/stand/emp%20task%20force%20posting%20dl/nerc_emp_task_force_report.pdf
News, B. (2022, February 5). Nuclear Plant Under Attack by Artillery. BBC News.
NIEH. (2022, March 18). EMF Radiation? Retrieved from https://www.niehs.nih.gov/: https://www.niehs.nih.gov/health/topics/agents/emf/index.cfm
NRC. (2017). NRC Backgrounder on Research and Test Reactors. Retrieved from https://www.nrc.gov/…/research-reactors-bg.html: www.nrc.gov/…/research-reactors-bg.html}
Okula, C. (n.d.). Small anechoic chamber. Edwards Air Force Base.
Reports, E. C. (2018, February 27). EMP Report February 27, 2018. Retrieved from highfrontier.org: highfrontier.org/february-27-2018-publish-emp-commission-reports].
Ryan, S. (2014, November 4). USASOC-CognitiveJointForceEntry.pdf. Retrieved from info.publicintelligence.net/: https://info.publicintelligence.net/USASOC-CognitiveJointForceEntry.pdf
Scarpati, J. (2021, Feb 25). What is a radio frequency (RF)? Retrieved from https://techtarget.com: https://techtarget.com/searchnetworking/definition/radio-frequency Feb 25, 2021
Schwarz, R. a. (n.d.). Two different anechoic chambers—one large and one small. Image used courtesy of Rohde and Schwarz.
sciencemediacentre.co.NZ. (2022, March 18). Sources of Radiation: Where do mobile phones fit in? Retrieved from https://www.sciencemediacentre.co.nz/infographics/: https://www.sciencemediacentre.co.nz/infographics/
Sciences, N. A. (2020). An Assessment of Illness in U.S. Government Employees and Their Families at Overseas Embassies. Washington: National Academy of Sciences.
Scientists, B. o. (2009, May 19). Iraq FFCD report – what-we-found-at-al-tuwaitha. Retrieved from https://thebulletin.org: https://thebulletin.org/2009/05/what-we-found-at-al-tuwaitha
Scoles, S. (2022, March 11). Radioactive Material Is Everywhere. Scientific American.
SOCOM. (2015). SOCOM Leaders attribute risks to cognitive warfare. Ft Bragg NC: SOCOM Unclassified brief.
Straussfogel, C. v. (2009 ). International Encyclopedia of Human Geography. Amsterdam: Elsevier.
SYSTEMS, G. A. (2022, March 3). How AI and supervised autonomy will change combat. GENERAL ATOMICS AERONAUTICAL SYSTEMS.
Turnquist, C. (2020). Radiation-induced brain injury: current concepts and therapeutic strategies targeting neuroinflammation. Neuro-Oncology Advances, Volume 2, Issue 1, January-December.
Tzu, S. (475 – 221 B.C.E.). The Art of War. Retrieved from http://classics.mit.edu: http://classics.mit.edu/Tzu/artwar.html

