19 Navigation Spoofing and ECD
By Professor Randall K. Nichols, Kansas State University
STUDENT OBJECTIVES
Students will understand four concepts:
- 1) That UAS / drones are mobile deployment agents. They are capable of Cyber-Spoofing navigation signals in the air by acting as a rogue access point, HAPs unit, mobile malicious signal generator, or interference medium to the ground control, friendly airborne unit, CBRN asset, or any other mechanism/system requiring localization or position fix via GPS / GNSS,
- 2) That GPS spoofing detection and mitigation for GNSS / GPS systems can be solved using the brilliant ECD algorithm for detection, mitigation, and recovery,
- 3) ADS-B is a subset of the larger receiver localization problem. Solutions that apply to the larger vector space, GNSS / GPS, also are valid for the subset, ADS-B, if computational hardware is available.
- 4) ECD does not effectively handle that indoor or city, or canyon localization
NAVIGATION SPOOFING AND ECD[1][2]
SUMMARY
GPS spoofing is a reasonably well-researched topic. Many methods have been proposed to detect and mitigate spoofing. The lion’s share of the research focuses on detecting spoofing attacks. Methods of spoofing mitigation are often specialized or computational burdensome. Civilian COTS anti-spoofing countermeasures are rare. This chapter highlights the brilliant value-added research by Dr. Manuel Eichelberger on the mitigation and recovery of GPS spoofing. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019) ECD implementation and evaluation show that the robustness of collective detection (CD) can be exploited to mitigate spoofing attacks with some modifications. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019) shows that multiple locations, including the actual one, can be recovered from scenarios in which several signals are present. Experiments based on the TEXBAT database show that various attacks can be mitigated. In the TEXBAT scenarios, an attacker can introduce a maximum error of 222 m and a median error under 19 m.[3] This is less than a sixth of the maximum unnoticed location offset reported in previous work that only detects spoofing attacks. (Ranganathan & al., 2016)
ECD does not track signals. It works with signal snapshots. It is suitable for snapshot receivers, which are a new class of low-power GPS receivers. (M.Eichelberger, 2019) (J. Liu & et al., 2012)
ADS-B’s high dependency on communication and navigation (GNSS) systems causes the system to inherit the vulnerabilities of those systems. This results in more opportunities (threats) to exploit those vulnerabilities. Advancements in computers, connectivity, storage, hardware, software, and apps are major aids to malicious parties who wish to carry out spoofing and other threats by exploiting the vulnerabilities of ADS-B. Another main vulnerability of ADS-B systems is their broadcast nature without security measures, which can easily be exploited to cause harm.
Definition: Spoofing – A Cyber-weapon attack that generates false signals to replace valid ones. GPS Spoofing is an attack to provide false information to GPS receivers by broadcasting counterfeit signals similar to the original GPS signal or by recording the original GPS signal captured somewhere else at some other time and then retransmitting the signal. The Spoofing attack causes GPS receivers to provide the wrong information about position and time. (T.E. Humphrees, 2008) (Tippenhauer & et al., 2011) GPS Spoofed UAS / drones may deliver signals against any target ( CBRN assets included) that requires accurate position fix or localization.
INTRODUCTION
It is important to understand that both GPS (part of the GNSS family) and ADS-B systems are vulnerable to spoofing attacks on both manned and unmanned aircraft. In general, GPS vulnerabilities translate down to the more specific ADS-B subset, which has vulnerabilities in its own right. This report will detail the brilliant work of Dr. Michael Eichelberger on Robust Global Localization using GPS and Aircraft Signals. He describes a functional tool known as CD to detect, mitigate and counter spoofing (and jamming) attacks on all stages of GPS. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
GPS is ubiquitous and is incorporated into so many applications (aircraft, ship, car /truck navigation; train routing and control; cellular network, stock market, CBRN assets, and power grid synchronization) that it makes a “rich” target for spoofing a receiver perceived location or time. Wrong information in time or space can have severe consequences.
ATC is partially transitioning from radar to a scheme in which aircraft (A/C) transmit their current location twice per second through ADS-B messages. This system has been mandated in Europe and has been well underway in the US since 2020. The A/C determine their location using GPS. If the onboard GPS receiver estimates a wrong location due to spoofing, wrong routing instructions will be delivered due to a wrong reported A/C location, leading to an A/C crash.
Ships depend heavily on GPS. They have few reference points to localize themselves apart from GPS. Wrong location indication can strand a ship, cause a collision, push off course into dangerous waters, ground a ship, or turn a ship into a ghost or a missile. Two thousand seventeen incidents in the Black Sea and South China Seas have been documented. (Burgess, 2017) (Nichols R. K.-P., 2019)
While planes and ships suffer spoofing attacks in the location domain, an attacker may also try to change the perceived time of a GPS receiver. Cellular networks rely on accurate time synchronization to exchange data packets between ground antennas and mobile handsets in the same network cell. Also, all neighboring network cells need to be time-synchronized for seamless call handoffs of handsets switching cells and coordinating data transmissions in overlapping coverage areas. Since most cellular ground stations get their timing information from GPS, a signal spoofing attacker could decouple cells from the common network time. Overlapping cells might send data simultaneously and frequencies, leading to message collisions and losses. (Anonymous, 2014) Failing communications networks can disrupt emergency services and businesses. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
SPOOFING
Threats and weaknesses show that large damages (even fatal or catastrophic) can be caused by transmitting forged GPS signals. False signal generators may cost only a few hundred dollars of software and hardware.
A GPS receiver computing its location wrongly or even failing to estimate any location can have different causes. Wrong localization solutions come from 1) a low signal-to-noise ratio (SNR) of the signal (examples: inside a building or below trees in a canyon); 2) reflected signals in multipath scenarios, or 3) deliberately spoofed signals. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019) discusses mitigating low SNR and multipath reflected signals. Signal spoofing (#3) is the most difficult case since the attacker can freely choose each satellite’s signal power and delay individually. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
Before discussing ECD – Collective detection maximum likelihood localization approach (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019), it is best to step back and briefly discuss GPS signals, classical GPS receivers, A-GPS, and snapshot receivers. Then the ECD approach to spoofing will show some real power by comparison. Power is defined as both enhanced spoofing detection and mitigation capabilities. [4]
GPS SIGNAL
The GPS system consists of a control segment, space segment, and user segment. The space segment contains 24 orbiting satellites. The network monitor stations, GCS, and antennas comprise the control segment. The third and most important are the receivers who make up the user segment. (USGPO, 2021)
Satellites transmit signals in different frequency bands. These include the L1 and L2 frequency bands at 1.57542 GHz and 1.2276 GHz. (DoD, 2008) Using code division multiple access protocols, signals from different satellites may be distinguished and extracted from background noise (CDMA). (DoD, 2008) Each satellite has a unique course/acquisition code (C/A) of 1023 bits. The C/A codes are PRN sequences transmitted at 10.23 MHz, which repeats every millisecond. The C /A code is merged using an XOR before being with the L1 or L2 carrier. The data broadcast has a timestamp called HOW, which is used to compute the location of the satellite when the packet was transmitted. The receiver needs accurate orbital information ( aka ephemeris) about the satellite, which changes over time. The timestamp is broadcast every six seconds; the ephemeris data can only be received if the receiver can decode at least 30 seconds of the signal.[5] (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
CLASSIC RECEIVERS
Classical GPS receivers use three stages when obtaining a location fix. They are Acquisition, Tracking, and localization.
Acquisition. The relative speed between satellite and receiver introduces a significant Doppler shift to the carrier frequency. [6] GPS receiver locates the set of available satellites. This is achieved by correlating the received signal with satellites’ known C /A codes. Since satellites move at considerable speeds. The signal frequency is affected by a Doppler shift. So, the receiver must correlate the received signal with C/ A codes with different Doppler shifts. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
Tracking. After a set of satellites has been acquired, the data contained in the broadcast signal is decoded. Doppler shifts and C /A code phase are tracked using tracking loops. After the receiver obtains the ephemeris data and HOW timestamps from at least four satellites, it can compute its location. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
Localization. Localization in GPS is achieved using signal time of flight (ToF) measurements. TVs are the difference between the arrival times of the HOW timestamps decoded in the tracking stage of the receiver and those signal transmission timestamps themselves. [7] The local time at the receiver is unknown, and the localization is done using pseudo ranges. The receiver location is usually found using least-squares optimization. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019) (Wikipedia, 2021)
A main disadvantage of GPS is the low bit rate of the navigation data encoded in the signals transmitted by the satellites. The minimal data necessary to compute a location fix, which includes the ephemerides of the satellites, repeats only every 30 seconds. [8]
A-GPS (ASSISTED GPS) – REDUCING THE STARTUP TIME
Assisted GPS (A-GPS) drastically reduces the startup time by fetching the navigation data over the Internet, commonly connecting via a cellular network. Data transmission over cellular networks is faster than decoding the GPS signals and normally only takes a few seconds. The ephemeris data is valid for 30 minutes. The acquisition time can be reduced using that data since the available satellites, and their expected Doppler shifts can be estimated. The receiver still needs to extract the HOW timestamps from the signal with A-GPS. However, these timestamps are transmitted every six seconds, which translates to how long the A-GPS receiver takes to compute a location fix. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
COURSE – TIME NAVIGATION
Course-Time Navigation (CTN) is an A-GPS technique that drops the requirement to decode the HOW timestamps from the GPS signals. (Diggelen, 2009) The only information used from the GPS signals is the phases of the C/A code sequences detected by a matched filter. Those C/A code arrival times are unambiguously related to the sub-milliseconds; the deviation may be no more than 150 km from the correct values. [9] [10] Since the PRN sequences repeat every millisecond, without considering navigation data flips in the signal, CTN can, in theory, compute a location from one millisecond of the sampled signal. [11] Noise can be an issue with such short signal recordings because it cannot be filtered out the same way with longer recordings of several seconds. The big advantage is that signal processing is fast and power-efficient and reduces the latency of the first fix. Since no metadata is extracted from the GPS signal, CTN can often compute a location even in the presence of noise or attenuation. (Diggelen, 2009)
SNAPSHOT RECEIVERS
Snapshot receivers aim at the remaining latency that results from the transmission of timestamps from satellites every six seconds. Snapshot receivers can determine the satellite modulo 1 ms ranges, which corresponds to 300 km.
COLLECTIVE DETECTION
Collective Detection (CD) is a maximum likelihood snapshot receiver localization method, which does not determine the arrival time for each satellite but rather combines all the available information and decides only at the end of the computation. [12] This technique is critical to the (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019) invention to mitigate spoofing attacks on GPS or ADS-B. CD can tolerate a few low-quality satellite signals and is more robust than CTN. CD requires a lot of computational power. CD can be sped up by a branch and bound approach, which reduces the computational power per location fix to the order of one second even for uncertainties of 100 km and a minute. CD improvements and research has been plentiful. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019) (J.Liu & et.al., 2012) (Axelrod & al, 2011) (P. Bissag, 2017)
ECD
Returning to the spoofing attack discussion, Dr. Manuel Eichelberger’s CD – Collective detection maximum likelihood localization approach, his method not only can detect spoofing attacks but also mitigate them! The ECD approach is a robust algorithm to mitigate spoofing. ECD can differentiate closer differences between the correct and spoofed locations than previously known approaches. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019) COTS has little spoofing integrated defenses. Military receivers use symmetrically encrypted GPS signals, subject to a “replay” attack with a small delay to confuse receivers.
ECD solves even the toughest type of GPS spoofing attack, consisting of spoofed signals with power levels similar to the authentic signals. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019) ECD achieves median errors under 19 m on the TEXBAT dataset, the de-facto reference dataset for testing GPS anti-spoofing algorithms. (Ranganathan & al., 2016) (Wesson, 2014) The ECD approach uses only a few milliseconds worth of raw GPS signals, so-called snapshots, for each location fix. This enables offloading of the computation into the Cloud, allowing knowledge of observed attacks. [13] Existing spoofing mitigation methods require a constant stream of GPS signals and tracking those signals over time. Computational load increases because fake signals must be detected, removed, or bypassed. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
RESEARCH TO 2016: SURVEY OF EFFECTIVE GPS SPOOFING COUNTERMEASURES
Researchers have been trying to find a complete solution to meet the spoofing threat because of the overwhelming dependence on GPS in every sector, ranging from civilian to military. To understand that ECD ( following sections) is a brilliant departure from past efforts, briefly covering the prevailing common wisdom is necessary. Haider and Khalid 2016 published an adequate survey of spoofing countermeasures up through 2016. (Haider & Khalid, 2016)
Spoofing Techniques
According to (Haider & Khalid, 2016), there are three common GPS Spoofing techniques with different sophistication levels. They are simplistic, intermediate, and sophisticated. (Humphreys & al., 2008)
The simplistic spoofing attack is the most commonly used technique to spoof GPS receivers. It only requires a COTS GPS signal simulator, amplifier, and antenna to broadcast signals to the GPS receiver. It was performed successfully by Los Almos National Laboratory in 2002. (Warner & Johnson, 2002) Simplistic spoofing attacks can be expensive as the GPS simulator can run $400K and is heavy (not mobile). The available GPS signal does not synchronize simulator signals, and detection is easy.
In the intermediate spoofing attack, the spoofing component consists of a GPS receiver to receive a genuine GPS signal and a spoofing device to transmit a fake GPS signal. The idea is to estimate the target receiver antenna position and velocity and then broadcast a fake signal relative to the genuine GPS signal. This type of spoofing attack is difficult to detect and can be partially prevented by using an IMU. (Humphreys & al., 2008)
In sophisticated spoofing attacks, multiple receiver-spoofer devices target the GPS receiver from different angles and directions. The angle-of-attack defense against GPS spoofing in which the angle of reception is monitored to detect spoofing fails in this scenario. The only known defense successful against such an attack is cryptographic authentication. (Humphreys & al., 2008) [14]
Note that prior research on spoofing was to exclude the fake signals and focus on a single satellite. ECD ( next section) includes the fake signal on a minimum of four satellites and then progressively / selectively eliminates their effect until the real weaker GPS signals become apparent. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
According to (Haider & Khalid, 2016), six innovative research papers cover spoofing countermeasures.
- Multi-test Detection and Protection Algorithm against Spoofing Attacks on GNSS Receivers (Jovanovic & Botteron, 2014)
The CM presented in this paper relies on statistical properties of the GPS signal, signal power level, Doppler frequency offset, and carrier to noise ratio. [15] The method monitors the above statistical properties and checks for inconsistencies to detect the presence of a GPS spoofer signal. The test results show that the proposed CMs can successfully detect the presence of the GPS fake signal with a low probability of false alarm. Once the spoofed signal is detected, the method offers a protection module ( once the spoofed signal is detected). The tracking history is further evaluated to re-establish the lock on the correct signal. This method only works against simplistic spoofer attacks. However, it is cost-effective as it requires only changes to the classic GNSS receiver, not the whole GPS infrastructure. (Jovanovic & Botteron, 2014)
GPS Spoofing Countermeasures (Warner & Johnston, 2003)
This paper is good for anyone interested in learning about GPS spoofing CMs, but the techniques discussed were general, not specific. The effectiveness of the approaches and strategies to defend against spoofing mentioned cannot be measured because no tests were performed to evaluate the methods presented. None of the presented methods were implemented in the field. The majority of strategies discussed were based on the monitoring of signal properties. (Haider & Khalid, 2016)
An Asymmetric Security Mechanism for Navigation Signals (Kuhn, 2015)
The method described in Kuhn is based on cross-correlation and short-term information processing.[16] It is proposed that each satellite transmitter will transmit a signal known as a hidden mark signal at regular intervals of time with a power level lower than the receiver noise level. After each mark signal transmission, a signed ( encrypted) data signal is transmitted with a power level above the receiver noise level. GPS receivers can only assess the hidden mark signal after receiving the signed data signal. This approach is best for a spoofed-replayed attack. The crystal oscillators inside classic GPS receivers can easily measure the delay between the data signal and the hidden mark signal despite being less than accurate compared to the satellite’s onboard atomic clocks. The method fails for multiple spoofer antennas. (Kuhn, 2015)
A Cross-layer defense mechanism against GPS spoofing attacks on PMUs in Smart Grid (Fan & al., 2015)
The CM described a method to protect the electrical grid PMUs from possible GPS spoofing attacks. The protection method consists of cross-layer protection. The first layer (physical) receives signals from hybrid antennas and then measures the AOA of the signals of all the GPS receivers. AOA will be the same as a GPS receiver if sourced at the same satellite. Spoofed signals will have a different AOA. The second layer ( upper layer) receives input from the physical layer and then uses state-based estimation techniques to detect bad data. The technique is feasible and only requires an additional GPS receiver and antenna. The method works against simple and intermediate attacks. (Fan & al., 2015)
Detection and Mitigation of GPS Spoofing Based on Antenna Array Processing (Magiera & Katulski, 2015)
This paper focuses on a CM that uses spatial processing. It tests well for both detection and reducing the impact of spoofed receivers. The method uses multiple antennas for reception and combines with the AOA approach. The phase delay measurement is used to distinguish the fake and authentic signals. The accuracy of the CM was tested when 4-8 spoofed signals were in play. Accuracy prediction was 99% when carrier to noise ratio was at least 46 dB Hz. (Magiera & Katulski, 2015)
GPS Spoofing Detection via Dual-Receiver Correlation of Military Signals(Psiaki & al., 2013)
The authors proposed a cross-layer detection mechanism to detect multiple spoofing attacks against the smart grid. In the physical layer, an AOA-based mechanism is employed. The distribution of the normal to spoofed standard deviation of the difference of the C/No from different antennas is calculated. The prior probability of spoofing is calculated and fed into the upper layer for further detection. In the upper layer, a Kalman filter is applied to estimate the state of the power system and use the measurement error to calculate the trustworthiness value of being spoofed. The information is all combined and correlated / integrated into the cross-layer mechanism. Results have been posted well, but computation time is high. (Psiaki & al., 2013)
A-F ANALYSIS (Haider & Khalid, 2016)
Table 19.1, reprinted from (Haider & Khalid, 2016), shows the criteria used to evaluate each technique to find the most effective GPS spoofing CM. Table 19.2, reprinted from (Haider & Khalid, 2016), presents an A-F analysis concerning the criteria outlined in Table 19.1.
From Table 19.2, we can discern that almost all the techniques can offer protection against a simplistic spoofing attack (Kuhn, 2015) (Jovanovic & Botteron, 2014) (Fan & al., 2015) (Magiera & Katulski, 2015) (Psiaki & al., 2013). Only two techniques can offer protection against sophisticated types of attacks (Kuhn, 2015) (Psiaki & al., 2013). This represents a reasonable look at the state-of-the-art GPS spoofing CMs in 2016.
Then along comes Dr. Manuel Eichelberger and ECD!
Table 19.1& 19.2 Effectiveness Criteria
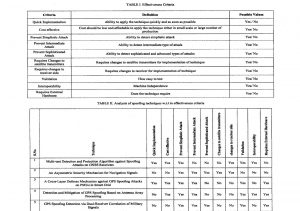
Source: Courtesy of (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019) Table 19.1, reprinted from Table I (Haider & Khalid, 2016), shows the criteria used to evaluate each technique to find the most effective GPS spoofing CM. Table 19.2, reprinted from Table II (Haider & Khalid, 2016), presents an A-F analysis concerning the criteria outlined in Table 19.1.
GPS SPOOFING RESEARCH: OUT OF THE BOX BRILLIANCE TO ECD DEFENSE
Three research tracks are most relevant to ECD / CD: Maximum Likelihood Localization, Spoofing Mitigation algorithms, and Successive Signal Interference Cancellation (SIC). Note that historical spoofing research focuses primarily on detecting singular SPS source attacks. The focus on mitigation, correction, and recovery attending to multiple spoofing signals on multiple satellite attack surfaces is the hallmark of ECD.
Maximum Likelihood Localization
CD is a maximum likelihood GPS localization technique. It was proposed in 1996 but considered computationally infeasible at that time. (Spilker, 1996) CD was first implemented by Axelrad et al. in 2011. (Axelrod & al, 2011) The search space contained millions or more location hypotheses. Improvements in the computational burden were found using various heuristics. (Cheong & al., 2011) (Jia, 2016) A breakthrough came with the proposal of a branch-and-bound algorithm that finds the optimal solution within ten seconds running on a single CPU thread. (P. Bissag, 2017)
Spoofing Mitigation
GPS spoofing defenses have intensively been studied. Most of them focus on detecting spoofing attacks. There is a paucity of prior research for spoofing mitigation and recovering from successful attacks by finding and authenticating the correct signals. (M.L. Psiaki & Humphreys, 2016) In contrast to the extensive research on GPS spoofing, there is a lack of commercial, civil receivers with anti-spoofing capabilities. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019) ECD inherently mitigates spoofing attacks.
Spoofing hardware performing a sophisticated, seamless satellite-lock takeover attack has been built. (Humphreys & al., 2008) Challenges associated with spoofing are matching the spoofed and accurate signals ‘ amplitudes at the receiver, which might not be in LOS and moving. (Schmidt & al, 2016)
It is practically feasible for a spoofer to erase the authentic signals at a 180-degree phase offset. (M.L. Psiaki & Humphreys, 2016) This is one of the strongest attacks that can only be detected with multiple receiver antennas or a moving receiver. (M.L. Psiaki & Humphreys, 2016) The spoofer needs to know the receiver location more accurately than the GPS L1 wavelength, 19 cm, for signal erasure to be feasible. Receivers with only a single antenna cannot withstand such an erasure attack. ECD targets single-antenna receivers and does not deal with signal erasure. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019) The original signals are still present in all other spoofing attacks, including signal replay and multiple transmission antenna implementations, and ECD remains robust. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019) Detecting multi-antenna receivers and differentiating signal timing consistencies are covered in (Tippenhauer & et al., 2011)
The GPS anti-spoofing work most relevant to ECD is based on the joint processing of satellite signals and the maximum likelihood of localization. One method can mitigate a limited number of spoofed signals by vector tracking of all satellite signals. (Jafarnia-Jahromi & al., 2012) A similar technique is shown to be robust against jamming and signal replay. (Y. Ng & Gao, 2016)
Successive Signal Interference Cancellation [17]
ECD uses an iterative signal damping technique with spoofing signals similar to SIC. SIC removes the strongest received signals to find the weaker signals and has been used with GPS signals before. (G. Lopez-Risueno & Seco-Granados, 2005) (Madhani & al., 2003) That work is based on a classical receiver architecture which only keeps a signal’s timing, amplitude, and phase. The ECD has its own snapshot receiver based on CD, which directly operates in the localization domain and does not identify individual signals in an intermediate stage. It is impossible to differentiate between authentic and spoofed signals, a priori, ECD does not remove signals from the sample data. Otherwise, the localization algorithm might lose the information from authentic signals/ Instead, ECD dampens strong signals by 60% to reveal weaker signals. This can reveal localization solutions with lower CD likelihood. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
GPS Signal Jamming
The easiest way to prevent a receiver from finding a GPS location is by jamming the GPS frequency band. GPS signals are weak and require sophisticated processing to be found. Satellite signal jamming considerably worsens the satellite signal acquisition results’ signal-to-noise ratio (SNR). ECD algorithms achieve a better SNR than classical receivers and tolerate more noise or stronger jamming. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
A jammed receiver is less likely to detect spoofing since the original signals cannot be accurately determined. The receiver tries to acquire any satellite signals it can find. The attacker only needs to send a set of valid GPS satellite signals stronger than the noise floor without synchronizing with authentic signals. [18] (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
There is a more powerful and subtle attack on top of the jammed signal. The spoofer can send a set of satellite signals with adjusted power levels and synchronize to the authentic signals to successfully spoof the receiver. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019) So even if the receiver has countermeasures to differentiate the jamming, the spoofer signals will be accepted as authentic. (Nichols R. K., 2020)
Two Robust GPS Signal Spoofing Attacks and ECD
Two of the most powerful GPS signal spoofing attacks are Seamless Satellite-Lock Takeover (SSLT) and Navigation Data Modification (NDM). How does ECD perform against these?
Seamless Satellite-Lock Takeover (SSLT)
The most powerful attack is a seamless satellite-lock takeover. The original and counterfeit signals are nearly identical in such an attack concerning the satellite code, navigation data, code phase, transmission frequency, and received power. This requires the attacker to know the location of the spoofed device precisely so that ToF and power losses over a distance can be factored in. After matching the spoofed signals with the authentic ones, the spoofer can send its signals with a small power advantage to trick the receiver into tracking those instead of the authentic signals. A classical receiver without spoofing countermeasures, like tracking multiple peaks, cannot mitigate or detect the SSLT attack, and there is no indication of interruption of the receiver’s signal tracking. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
Navigation Data Modification (NDM)
An attacker has two attack vectors: modifying the signal’s code phase or altering the navigation data—the former changes the signal arrival time measurements. The latter affects the perceived satellite locations. Both influence the calculated receiver location. ECD works with snapshot GPS receivers and is not vulnerable to NDM changes as they fetch information from other sources like the Internet. ECD deals with modified, wireless GPS signals.
ECD ALGORITHM DESIGN
ECD is aimed at single-antenna receivers. Its spoofing mitigation algorithm object is to identify all likely localization solutions. It is based on CD because 1) CD has improved noise tolerance compared to classical receivers, 2) CD is suitable for snapshot receivers, 3) CD is not susceptible to navigation data modifications, and 4) CD computes a location likelihood distribution which can reveal all likely receiver locations including the actual location, independent of the number of spoofed and multipath signals. ECD avoids spoofing pitfalls and signal selection problems by joining and transforming all signals into a location likelihood distribution. Therefore, it defeats the top two GPS spoofing signal attacks. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
Relating to the 4th point, spoofing and multipath signals are similar from a receiver’s perspective. Both result in several observed signals from the same satellite. The difference is that multipath signals have a delay-dependent on the environment, while spoofing signals can be crafted to yield consistent localization solutions at the receiver. Classical receivers can be modified to track an arbitrary number of signals per satellite instead of only one to detect spoofing and multipath signals. (S.A.Shaukat & al., 2016) The set of authentic signals – one signal from each satellite – would have to be correctly identified in such a receiver. Any selection of signals can be checked for consistency by verifying that the resulting residual error of the localization algorithm is very small. This is a combinatorically difficult problem. For n satellites and m transmitted sets of spoofed signals, there are (m+ 1) n possibilities for the receiver to select a set of signals. Only m + 1 of those will result in a consistent localization solution representing the actual location and m spoofed locations. ECD avoids this signal selection problem by joining and transforming all signals into a location likelihood distribution. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
ECD only shows consistent signals since just a few signals overlapping (synced) for some location hypotheses do not significantly accumulate. All plausible receiver locations – given the observed signals – have a high likelihood. Finding these locations in four dimensions, space and time, is computationally expensive. (Bissig & Wattenhoffer, 2017)
Branch and Bound
A fast CD leveraging branch and bound algorithm is employed to reduce the computational load compared to exhaustively enumerating all the location hypotheses in the search space. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019) describes the modifications to the B&B algorithm for ECD in copious detail in chapter 6. Eichelberger also discusses acquisition, receiver implementation, and experiments using the TEXBAT database. [19] [20]
One of the key points under the receiver implementation concerns the correlation of C/A codes. [21]
The highest correlation is theoretically achieved when the C/A code in the received signal is aligned with the reference C/A code. Due to the pseudo-random nature of the C/A codes, a shift larger than one code chip from the correct location results in a low correlation value. Since one code chip has a duration of 1/1023 ms, the width of the peaks found in the acquisition vector is less than 2% of the total vector size. ECD reduces the maximum peak by 60% in each vector. A detection for partially overlapping peaks prevents changes to those peaks. Reducing the signal rather than eliminating it has a little negative impact on the accuracy. Before using these vectors in the next iteration of the algorithm, the acquisition result vectors are normalized again. This reduces the search space based on the prior iteration. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
ADS-B SECURITY
We next move into the subset problem, namely ADS-B systems on aircraft, both manned and unmanned. ADS-B ubiquitously uses GPS location and signal receiver technologies. ADS-B has a very high dependency on communication and navigation (GNSS) systems. This is a fundamental cause of insecurity in the ADS-B system. It inherits the vulnerabilities of those systems and results in increased Risk and additional threats. (Nichols R. K., 2020) (Nichols R. K.-P., 2019)[22] Another vulnerability of the ADS-B system is its broadcast nature without security measures. These can easily be exploited to cause other threats such as eavesdropping on aircraft movement with the intention to harm, message deletion, and modification. The systems dependency on the onboard transponder is also considered a major vulnerability shared by the SSR. Aircraft hijackers can exploit this vulnerability to make the aircraft movements invisible. (Busyairah, 2019)
ADS-B Standards
ICAO has stressed including provisions for protecting critical information and communication technology systems against cyberattacks and interference, as stated in the Aviation Security Manual Document 8973/8. (ICAO, 2021) This was further emphasized in ATM Security Manual Document 9985 AN/492 to protect ATMs against cyberattacks. (ICAO, 2021)
ADS-B Security Requirements [23]
Strohmeier et al. (Strohmeier, 2015) and Nichols et al. (Nichols R. K.-P., 2019) have outlined a set of security requirements for piloted aircraft and unmanned aircraft. Here are the combined security requirements for the ADS-B system in sync with the standard information security paradigm of the CIA:
- Data integrity [24]
The system security should ensure that ADS-B data received by the ground station or other aircraft (a/c) or UAS (if equipped) are the exact messages transmitted by the a/c. It should also detect any malicious modification to the data during the broadcast.
- Source integrity
The system security should verify that the ADS-B message received is sent by the message’s actual owner ( correct a/c).
- Data origin (location / position fix) authentication
The system security should verify that the positioning information in the ADS-B message received is the original position of the a/c at the time of transmission.
- Low impact on current operations
The system security hardware/software should be compatible with the current ADS-B installation and standards.
- Sufficiently quick and correct detection of incidents
- Secure against DOS attacks against computing power
- System security functions need to be scalable irrespective of traffic density.
- Robustness to packet loss
Vulnerabilities in ADS-B system
Vulnerability in this section refers to the Ryan Nichols (RN) equations for information Risk determination. A vulnerability is a weakness in the system that makes it susceptible to exploitation via a threat or various types of threats. (Nichols R. K.-P., 2019) ADS-B system is vulnerable to security threats.
Broadcast Nature of RF Communications
ADS-B principle of operation, system components, integration, and operational environment are adequately discussed in Chapter 4 (Busyairah, 2019). The ADS-B system broadcasts ADS-B messages containing a/c state vector and identity information via RF communication links such as 1090ES, UAT, or VDL Mode 4. The broadcast nature of the wireless networks without additional security measures is the main vulnerability in the system. (R.K. Nichols & Lekkas, 2002) [25]
No Cryptographic Mechanisms
The sender encrypts neither ADS-B messages at the point of origin nor the transmission links. There are no authentication mechanisms based on robust cryptographic security protocols. The ICAO (Airport’s authority of India 2014) has verified no cryptographic mechanism was implemented in the ADS-B protocol. (Airports Authority of India, 2014) [26]
ADS-B COTS
ADS-B receivers are available in COTS at affordable prices. The receiver can be used to track ADS-B capable a/c flying within a specific receiver range. The number of ADS-B tracking gadgets for all media is growing every year. They can be used to hack the systems on UAS. (Nichols R. K.-P., 2019)
Shared Data
As a result of COTS availability of ADS-B receivers, various parties, both private and public, are sharing real-time air traffic information on a/c on the Internet. Several websites on the Internet provide digitized live ADS-B traffic data to the public, e.g., flightradar24.com, radarvirtuel.com, and FlightAware. The availability of the data and the capability to track individual a/c movements open the door to malicious parties to perform undesired acts that may have safety implications. (Busyairah, 2019)
ASTERIX Data Format
All-purpose Structured EUROCONTROL Surveillance Information eXchange (ASTERIX) is a binary format for information exchange in aviation. (EUROCONTROL, 2016) ADS-B data is encoded into ASTERIX CAT 21 format and transmitted by ADS-B equipped a/c to ADS_B ground stations. And they are decoded into a usable form for ATC use. The ASTERIX format decoding guidance, source code, and tools are widely available in the public domain. (Busyairah, 2019)
Dependency On The On-Board Transponder
ADS-B encoding and broadcast are performed by either the transponder (for 1090ES) or an emitter (for UAT/ VDL Mode 4) onboard the a/c. Therefore, the ADS-B aircraft surveillance is dependent on the onboard equipment. There is a vulnerability (not cyber or spoofing) whereby the transponder or emitter can be turned off inside the cockpit. The a/c becomes invisible, and SSR and TCAS operation integrity is affected.
Complex System Architecture and Passthrough Of GNSS Vulnerabilities
ADS-B is an integrated system dependent on an onboard navigation system to obtain information about the state of the a/c and a communication data link to broadcast the information to ATC on the ground and other ADS-B-equipped a/c. The system interacts with external elements such as humans (controllers and pilots) and environmental factors. The integrated nature of the system increases the system’s vulnerability. The system inherited the vulnerabilities of the GNSS on which the system relies to obtain a/c positioning information! The ADS-B system also inherits vulnerabilities of the communications links. (Busyairah, 2019) (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019) (The Royal Academy of Engineering, 2011)
Threats to ADS-B system
Threats in this section refer to the Ryan Nichols (RN) equations for information Risk determination. A Threat is an action exploiting a vulnerability in the system to cause damage or harm specifically to a/c and generally to the Air Traffic Services (ATS), intentionally or unintentionally. (Nichols R. K.-P., 2019) ADS-B system is vulnerable to security threats.
Eavesdropping
The broadcast nature of ADS-B RF communication links without additional security measures (cryptographic mechanisms) enables the act of eavesdropping on the transmission. Eavesdropping can lead to serious threats such as targeting specific a/c movement information to harm the a/c. This can be done with more sophisticated traffic and signal analysis using available sources such as Mode S and ASDS-B capable open-source GNU Radio modules or SDR. Eavesdropping is a violation of confidentiality and compromises system security. (Busyairah, 2019)
Data-Link Jamming
Datalink jamming is an act of deliberate / non-deliberate blocking, jamming, or causing interference in wireless communications. (R.K. Nichols & Lekkas, 2002) Deliberate jamming aims to disrupt information flow ( message sending /receiving) between users within a wireless network using a radio jammer device. Jammer devices can be easily obtained as COTS devices. (Strohmeier, 2015) (R.K. Nichols & Lekkas, 2002) Using the Ryan Nichols equations, the impact is severe in aviation due to the large coverage area (airspace), which is impossible to control. It involves safety-critical data; hence the computed Risk/lethality level is high. (R.K. Nichols & Lekkas, 2002) (Busyairah, 2019) The INFOSEC quality affected is availability because jamming stops the a/’c or ground stations or multiple users within a specific area from communicating. On Air Traffic Control
Jamming is performed on ADS-B frequencies, e.g., 1090MHz. The targeted jamming attack would disable ATS at any airport using ATCC. Jamming a moving a/c is difficult but feasible. (Strohmeier, 2015)
ADS-B system transmitting on 1090ES is prone to unintentional signal jamming due to the use of the same frequency (Mode S 1090 MHz) by many systems such as SSR, TCAS, MLAT, and ADS-B, particularly in dense space. (Busyairah, 2019) [27] Not only is ADS-B prone to jamming, but so is SSR. (Adamy, 2001)[28]
Two Types of Jamming Threats for ADS-B
Apart from GNSS (positioning source for ADS-B) jamming, the main jamming threats for the ADS-B system include GS Flood Denial and A/C Flood Denial.
Ground Station Flood Denial (GSFD)
The GSFD blocks 1090 MHz transmissions at the ADS-B ground station. There is no difficulty in gaining close proximity to a ground station. Jamming can be performed using a low-power jamming device to block ADS-B signals from A/C to the ground station. The threat does not target individual a/c. It blocks ADS-B signals from all A/C within the ground station range.
Aircraft Flood Denial (A/C FD)
A/CFD blocks signal transmission to the a/c. This threat disables the reception of ADS-B IN messages, TCAS, and interrogation from WAM/MLAT and SSR. It is very difficult to gain close proximity to a moving A/C. The attacker needs to use a high-powered jamming device. According to (D. McCallie, 2011), these devices are not easy to obtain. MAYBE (see author note).[29] What is true is that the jamming function will be ineffective as soon as the A/C moves out of the specific range of the jamming device. Better attempts can be made from within the A/C. [30]
ADS-B SIGNAL SPOOFING
ADS-B signal spoofing attempts to deceive an ADS-B receiver by broadcasting fake ADS-B signals that resemble a set of normal ADS-B signals or by re-broadcasting genuine signals captured elsewhere or at a different time. Spoofing an ADS-B system is also known as message injection because fake (ghost) a/c is introduced into the air traffic. The system’s vulnerability – having no authentication measures implemented at the systems data link layer – enables this threat. Spoofing is a hit on the security goal of Integrity. This leads to undesired operational decisions by controllers or surveillance operations in the air or on the ground. The threat affects both ADS-B IN and OUT systems. (Busyairah, 2019) Spoofing threats are two basic varieties: Ground Station Target Ghost Injection / Flooding and Ground Station Target Ghost Injection / Flooding.
Ground Station Target Ghost Injection / Flooding
Ground Station Target Ghost Injection / Flooding is performed by injecting ADS-B signals from a single a/c or multiple fakes ( ghost) a/c into a ground station. This will cause single /multiple fake (ghost) a/c to appear on the controller’s working position (radar screen). [31]
Aircraft Target Ghost Injection / Flooding
Aircraft Target Ghost Injection / Flooding is performed by injecting ADS-B signals from a single a/c or multiple fake (ghost) a/c into an airplane in flight. This will cause ghost a/c to appear on the TCAS and CDTI screens in the cockpit to go haywire. Making the mess worse, the fake data will also be used by airborne operations such as ACAS, ATSAW, ITP, and others for aiding a/c navigation operations. (Busyairah, 2019)
ADS-B message deletion
An a/c can look like it has vanished from the ADS-B-based air traffic by deleting the ADS-B message broadcast from the a/c. This can be done by two methods: destructive interference and constructive interference. Destructive interference is performed by transmitting an inverse of an actual ADS-B signal to an ADS-B receiver. Constructive interference is performed by transmitting a duplicate of the ADS-B signal and adding the two signal waves ( original and duplicate). The two signal waves must be of the same frequency phase and traveling in the same direction. Both approaches will result in being discarded by the ADS-B receiver as corrupt. (Busyairah, 2019)
ADS-B message modification
ADS-B message modification is feasible on the physical layer during transmission via datalinks using two methods: Signal Overshadowing and Bit-flipping. Signal overshadowing is done by sending a stronger signal to the ADS-B receiver, whereby only the stronger of the two colliding signals is received. This method will replace either the whole target message or part of it. Bit flipping is an algorithmic manipulation of bits. The attacker changes bits from 1 to 0 or vice versa. This will modify the ADS-B message and is a clear violation of the security goal of Integrity. (Strohmeier, 2015) This attack will disrupt ATC operations or a/c navigation.
Circling back to ECD
The ADS-B vulnerabilities and threats above are amenable to ECD mitigation if sufficient computing horsepower is available. For an a/c or ground station, this condition bodes well. For a UAS or sUAS, not necessarily so.
INDOOR LOCALIZATION WITH AIRCRAFT SIGNALS USING ECD VS COMPETITIVE TECHNOLOGIES
GPS does not work well indoors due to the low signal strength. GPS satellite gets its energy from a dual solar array, which generates about 400-2900 W of power (depending on the satellite generation).[32] With an altitude of about 12,427 miles, this relatively weak signal barely makes it to earth. (Accuracy, 2021) The free space path loss is on the order of 180 dB. (anonymous, 2021) (Eichelberger & Tanner, Indoor Localization with Aircraft Signals, 2017)
Airplanes and other aircraft fly at an altitude below 8.5 miles. They also have ample power leaving for communications.[33] For safety reasons, airplanes and helicopters repeatedly transmit their location ( like GPS satellites). These ADS-B signals are strong enough to be received indoors, even with cheap hardware. But are these air traffic control signals (ATC) precise enough to locate the aircraft and any mobile device? ATC signals have not been designed for indoor localization. Three challenges present: (Eichelberger & Tanner, Indoor Localization with Aircraft Signals, 2017)
- 1) Aircraft do not fly in orbit. Aircraft do not have accurate predetermined flight paths, and unexpected changes to their route are always possible (i.e., holding pattern, weather, crowded airport)
- 2) Aircraft are not uniformly distributed in the sky. GPS satellites cover the sky in a regular pattern to maximize use position fixing ( localization).
- 3) Aircraft position signals are not precise. An aircraft has an unpredictable delay between learning its position from the GPS satellites and retransmitting this position. (Cornell – LII, 2021) [34] Unlike GPS satellites with their atomic clocks, aircraft transmissions may not include complete time information; some aircraft do not even include precise position information.
There are key differences in “accuracy” and “precision” and “absolute” and “relative” accuracy when it comes to discussions of GNSS/ GPS position fixing, mapping, and surveying. Schaefer devotes Chapter 19 Accuracy and Precision of GNSS in the field in his book, GPS and GNSS Technology in Geosciences (2021). (Schaefer & Pearson, 2021)
Eichelberger points out a few mitigating factors. Aircraft do not fly in orbits, but passengers and crew certainly do not appreciate abrupt flight path changes. Aircraft positions are not optimized for ground user-localization but rather for air traffic safety. In urban areas, there are more aircraft available than satellites. This increases the number of signals and reduces statistical uncertainty in position estimation from noisy measurements (item 3 above). (Eichelberger & Tanner, Indoor Localization with Aircraft Signals, 2017) However, at night, the frequency of received A/C signals is substantially lower than during the daytime.
Do the mitigations above outweigh the communications issues using just aircraft signals to retransmit the GPS signals to ground stations and users? No. Eichelberger presents an infrastructure-free indoor localization method using ECD. It requires only a network of receivers, [ground stations]; a receiver whose position should be determined [handset]; and a server that connects the handset. There is no silver bullet here. His entire approach, mathematics, field tests, and conclusions may be found in (Eichelberger & Tanner, Indoor Localization with Aircraft Signals, 2017).
ECD vs. minimum US government GPS standards
The GPS Performance Standard, the US government, currently lists a worse-case horizontal accuracy of better than 17 meters (~55.8 ft) in 95% of all cases. (USGPO, 2020) Depending on the receiver’s quality and available correction methods, the horizontal can be substantially better, on the order of 3-7 meters (~9.8 – 23 ft).[35] Usually, indoor localization methods attempt to be more accurate, such as military targeting or user in a large mall.
ECD cannot compete with other indoor localization methods. ECD prototype implementation has a median error of about 25 m (82 ft). ECD works very well outdoors and marginally for indoor localization on the plus side. ECD does not report well for indoor localization operations. Rather than describe the indoor ECD implementation, prototype methods, simulations, and detailed results, the reader is guided to the primary paper for further discussion. (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
Related Work
Much research on indoor localization focuses on providing accurate position fixes (localization), for instance, room level or sub-meter accuracy. The cost factors to get so accurate are ITE:
- Installation of dedicated infrastructure like beacons in each building or room (ex., hospital neo-natal or heart surgery recovery),
- Training or initialization phase to gather data, which is necessary for subsequent localization,
- Usage of Expensive user equipment.(Eichelberger & Tanner, Indoor Localization with Aircraft Signals, 2017)
Most methods do not suffer all three drawbacks. But less cost is a trade-off for less accuracy. Liu et al. provide an overview of indoor localization methods. They differ by fundamental measurements, which are received signal strength (RSS), time of arrival (TOA), time difference of arrival (TDOA),[36] or angle of arrival (AOA). (Liu & al, 2007) Below are briefly listed the main ECD competitors with ITE drawbacks in brackets.
WiFi [T]
WiFi signals are popular for indoor localization because of the wide use of WiFi hotspots. No dedicated infrastructure like beacons is needed. WiFi-based approaches generally have an accuracy of a few meters ( “few” x 3.280 = ft). WiFi localization methods require a training phase in which positions or fingerprints of the access points are determined at different locations. Infrastructure changes must be detected, and the database needs to be updated regularly. (Liu & al, 2007)
Ultrasound [I]
Ultrasound-based methods require dedicated hardware—cheap equipment with excellent results. Ultrasound systems have proven to be very accurate, achieving centimeter-level accuracy. (1 cm= 0.393 in) The drawbacks are limited effective distance prone to ambient noise. (Oberholzer & et.al, 2011)
Light [T,E]
The most accurate results are achieved by laser- and camera-based methods. The best system in 2016 achieved an accuracy of 5 cm (1.968 in) using two lasers and multi high-end cameras. It costs a quarter-million dollars. (Microsoft, 2016) LEDs and miniaturization have opened up the visible light spectrum to communication and localization techniques. Pathak et al. give an extensive overview of current methods. (Pathak & al, 2015)
Bluetooth [T, I]
Bluetooth, like WiFi, uses a 2.4 GHz frequency band. WiFi may take tens of seconds to identify base stations; faster response times can be achieved with Bluetooth. (Mair, 2012) Bluetooth pairing presents a delay before users can exchange information. The accuracy of Bluetooth methods approaches 3 m (9 ft).
RFID [I]
RFID systems are either active or passive. They have limited capacity energy and require many units to communicate over short distances. Bouet and Dos Santos explore RFID localization systems. (Bouet, 2008)
Sensor Fusion
Sensor-assisted localization methods are favored in smartphone applications because all these devices feature an inertial measurement unit (IMU) comprising an accelerometer, a gyroscope, and a compass. (Ye & al, 2012) Accuracy ranges are dependent on local conditions, tower availability, and 4 or 5G / LTE available networks.
HAPS
Of special interest to this reviewer is the possibility of using High Altitude UAS Platforms for wireless communications (HAPS) to replace the aircraft in retransmitting GPS signals and acting as the primary agent for indoor and outdoor localization procedures. Two important references detail the advantages and disadvantages of HAPS for communication systems and localization use. (Alejandro Aragon-Zavala, 2008) Nichols et al. provide an especially strong analysis of HAPS capabilities compared to terrestrial and satellite systems for telecommunications; HAPS platform advanced telecommunications services in various stages of engineering and development, HAPS link budgets, and characteristics of terrestrial, satellite, and haps systems. (Nichols R. K.-P., 2019)
Security of GNSS (Shrivastava, 2021) (Ochin & Lemieszewski, 2021)
In 2021 (Ochin & Lemieszewski, 2021), Ochin & Lemieszewski penned an excellent update on the spoofing threat covering air, land, and sea operations in Europe and Asia. Some interesting topics covered were self-spoofing or limpet spoofing technologies; DIY GNSS spoofer’s; [37] GNSS interference modalities; complementary countermeasures like INS; [38] GNSS jamming techniques, GNSS meaconing, and detailed sections on cloud-based GNSS positioning. Modern satellite navigation is based on the use of NO-Request range measurements between the navigation satellite and the user. It means that the information about the coordinates of the satellites given to the user is included in the navigation signal. The range measurement is based on calculating the receiving signal time delay compared with the signals generated by the user’s equipment. (Ochin & Lemieszewski, 2021) Chapter 3 divides Cloud-based spoofing detection into four classes and mathematically defines the antenna distances and navigation modes based on those classes. These detection modes are based on a single antenna spoofer and do not consider mitigation and recovery steps. This is compared to ECD, which does all three steps in the security solution.
Ochin & Lemieszewski (Ochin & Lemieszewski, 2021) present a fascinating picture of the history of anti-spoofing from 1942 patent to fight the American radio-controlled sea-based torpedoes with a radio jamming of German boats and submarines. (US Patent No. 2,292,387, 1942) They continue with a European view of security measures for the six satellite constellations. They conclude with a Postscript on the drama behind the taking by Iran of the US RQ-170 Sentinel and how they did it! (Goward, April 21, 2020) The Ochin & Lemieszewski chapter supports the risk opinions presented earlier. “The Risk of losing GNSS signal (to spoofing) is growing every day. The accessories necessary for the manufacture of systems for GNSS “jamming” and/or “spoofing” are now widely available, and this type of attack can be taken advantage of by not only the military but also by terrorists.” (Ochin & Lemieszewski, 2021)
CONCLUSIONS
The purposes of this chapter were to introduce the problem of Navigation Cyber-Spoofing; to recognize that GNSS / GPS / ADS-B systems, including CBRN mobile assets, are susceptible to Cyber Spoofing; that research has focused on detection rather than mitigation and recovery efforts; and finally, that ECD is a brilliant solution to part of the Cyber Spoofing problem as it does not exclude false signals but encompasses them into the algorithm.
Bibliography
Accuracy, G. G.-G. (2021, July 16). Official U.S. government information about the Global Positioning System (GPS) and related topics. Retrieved from https://www.gps.gov/: https://www.gps.gov/systems/gps/performance/accuracy/#problems
Adamy, D. (2001). EW 101: A First Course in Electronic Warfare. Boston: Artech House.
Airports Authority of India. (2014). Security Issues of ADS-B Operations. ICAO. Hong Kong, China: ICAO.
Alejandro Aragon-Zavala, J. L.-R.-P. (2008). High-Altitude Platforms for Wireless Communications. Chichester, West Sussex, UK: John Wiley & Sons.
Ali, e. a. (2014). ADS-B system failure modes and models. The Journal of Navigation, 67: 995-1017.
anonymous. (2021, July 16). GPS newsgroup. Retrieved from http://gpsinformation.net/main/gpspower.htm: http://gpsinformation.net/main/gpspower.htm
Anonymous. (2014). Timing & Synchronization for LTE-TDD & LTE-Advanced Mobile Networks; Technical Report, Microsemi. Retrieved from www.microsemi.com: https://www.microsemi.com/document-portal/doc_download/133615-timing-sync-for-lte-tdd-lte-a-mobile-networks
Axelrod, P., & al, e. (2011). Collective Detection and Direct Positioning Using Multiple GNSS Satellites. Navigation, pp. 58(4): 305-321.
Bissig, P., & Wattenhoffer, M. E. (2017). Fast & Robust GPS Fix using 1 millisecond of data. 16 ACM / IEEE Int Conf on Information Processing in Sensor Networks (pp. 223-234). Pittsburg, PA: IPSN.
Bouet, M. &. (2008). RFID Tags: Position Principles and localization techniques. IEEE 1st IFIP Wireless Days, pp. 1-5.
Burgess, M. (2017, September 21). When a Tanker Vanishes, all evidence points to Russia. Retrieved from https://www.wired.co.uk/: https://www.wired.co.uk/article/black-sea-ship-hacking-russia
Busyairah, S. A. (2019). Aircraft Surveillance Systems: Radar Limitations and the Advent of the Automatic Dependent Surveillance-Broadcast. New York: Routledge.
Cheong, J., & al., e. (2011). Efficient Implementation of Collective Action. In IGNSS Symposium, 15-17.
Closas, P., & al., e. (2007). Maximum likelihood estimation of position in GNSS. IEEE Signal Processing Letters (pp. 14(5): 359-362). IEEE.
Cornell – LII. (2021, July 16). ADS-B law. Retrieved from https://www.law.cornell.edu/: https://www.law.cornell.edu/cfr/text/14/91.227#e
- McCallie, e. a. (2011). Security analysis of the ADS-B Implementation in the NEXT generation Air transport system. Inter J. of Critical Infrastructure Protection, 4: 78-87.
Diggelen, F. V. (2009). A-GPS: Assisted GPS, GNSS, and SBAS. NYC: Artech House.
DoD. (2008). Global Positioning System Performance Standard 4th edition (GPS SPS PS). Washington, DC: DoD.
Eichelberger, M. (2019). Robust Global Localization using GPS and Aircraft Signals. Zurich, Switzerland: Free Space Publishing, DISS. ETH No 26089.
Eichelberger, M., & Tanner, S. L. (2017). Indoor Localization with Aircraft Signals. ACM -Sen Sys -17, ISBN: 978-1-4503-5459-2.
EUROCONTROL. (2016, June). part_1_-_eurocontrol_specification_asterix_spec-149. Retrieved from https://www.eurocontrol.int/sites/: https://www.eurocontrol.int/sites/default/files/2019-06/part_1_-_eurocontrol_specification_asterix_spec-149_ed_2.4.pdf
Fan, Y., & al., e. (2015). A Cross-layer defense mechanism against GPS spoofing attacks on PMUs in Smart Grid. IEEE Trans on Smart Grid, Vol 6. No. 6 November.
- Lopez-Risueno & Seco-Granados, G. (2005). Cn/sub 0/ estimation and near-far mitigation for GNSS indoor receivers. In 2005 IEEE 61st Vehicular Technology Conf., V4: 2624-2628.
Goward, D. (April 21, 2020). GPS circle spoofing was discovered in Iran. GPS World.
Haider, Z., & Khalid, &. S. (2016). Survey of Effective GPS Spoofing Countermeasures. 6th Intern. Ann Conf on Innovative Computing Technology (INTECH 2016) (pp. 573-577). IEEE 978-1-5090-3/16.
Humphreys, T., & al., e. (2008). Assessing the spoofing threat: Development of a portable GPS civilian spoofer. In Radionavigation Laboratory Conf. Proc.
ICAO. (2021, June 2). atm_security_manual 9985. Retrieved from http://www.aviationchief.com/: http://www.aviationchief.com/uploads/9/2/0/9/92098238/icao_doc_9985_-_atm_security_manual_-_restricted_and_unedited_-_not_published_1.pdf
ICAO. (2021, June 2). Aviation Security Manual Document 8973/8. Retrieved from https://www.icao.int/Security/: https://www.icao.int/Security/SFP/Pages/SecurityManual.aspx
IS-GPS-200G. (2013, September 24). IS-GPS-200H, GLOBAL POSITIONING SYSTEMS DIRECTORATE SYSTEMS ENGINEERING & INTEGRATION: INTERFACE SPECIFICATION IS-GPS-200 – NAVSTAR GPS SPACE SEGMENT/NAVIGATION USER INTERFACES (24-SEP-2013). Retrieved from http://everyspec.com/: http://everyspec.com/MISC/IS-GPS-200H_53530/
J.Liu, & et.al. (2012, November). Energy Efficient GPS Sensing with Cloud Offloading. Proceedings of 10 ACM Conference on Embedded Networked Sensor Signals (SenSys), pp. 85-89.
Jafarnia-Jahromi, A., & al., e. (2012). Detection and mitigation of spoofing attacks on a vector-based tracking GPS receiver. ION ITM.
Jia, Z. (2016). A Type of Collective Detection scheme with improved pigeon-inspired optimization. Inter. J. of Intelligent Computing and Cybernetics, 9(1):105-123.
Jovanovic, A., & Botteron, C. (2014). Multi-test Detection and Protection Algorithm against Spoofing Attacks on GNSS Receivers. PLANS IEEE/ION Position, Location and Navigation Symposium (pp. 5-8 May). Monterey, CA 5-8 May: IEEE/ION.
Kuhn, M. G. (2015). An Asymmetric Security Mechanism for Navigation Signals. 6th Info Hiding Workshop. Toronto, CA: Univ of Cambridge. Retrieved from https://www.cl.cam.ac.uk/~mgk25/ih2004-navsec.pdf
Liu, H., & al, e. (2007). Survey of wireless indoor positioning techniques and systems. IEEE TX on systems, man and cybernetics, Part C ((applications & reviews), pp. 37, 6: 1067-1080.
M.Eichelberger, v. H. (2019). Multi-year GPS tracking using a coin cell. In Proc. of 20th Inter.Workshop on Mobile Computing Systems & Applications ACM, 141-146.
M.L. Psiaki & Humphreys, T. (2016). GNSS Spoofing and Detection. Proc. of the IEEE, 104(6): 1258-1270.
Madhani, P., & al., e. (2003). Application of successive interference cancellation to the GPS pseudolite near-far problem. IEEE Trans, on Aerospace & Elect. Systems, 39(2):481-488.
Magiera, J., & Katulski, &. R. (2015). Detection and Mitigation of GPS Spoofing Based on Antenna Array Processing. J. of Applied Research & Technology, Vol 13. pp 45-47.
Mair, N. &. (2012). A collaborative Bluetooth- based approach to localization of mobile devices. IEEE 8th Inter Conf. on Collaborative Computing: Networking, Applications, and work sharing, pp. 363-371.
Microsoft. (2016). Microsoft Indoor Localization Competition. Retrieved from www.microsoft.com: https://www.microsoft.com/en-us/research/event/microsoft-indoor-localization-competition-ispn-2016/#official-results
Nichols, R. K. (2020). Counter Unmanned Aircraft Systems Technologies & Operations. Manhattan, KS: www.newprairiepress.org/ebooks/31.
Nichols, R. K.-P. (2019). Unmanned Aircraft Systems in the Cyber Domain, 2nd Edition. Manhattan, KS: www.newprairiepress.org/ebooks/27.
Nichols, R., & al., e. (2020). Unmanned Vehicle Systems and Operations on Air, Sea, and Land. Manhattan, KS: New Prairie Press #35.
Oberholzer, & et.al. (2011). Spiderbait: Augmenting wireless sensor networks with distance and angle information. Proc of 10th ACM/IEEE Int Conf on Information Processing in Sensor Networks, pp. 211-222.
Ochin, E., & Lemieszewski, &. L. (2021). Chapter 3 Security of GNSS. In G. P. PETROPOULOS, & &. P. SRIVASTAVA, GPS and GNSS Technology in the Geosciences (51-73). NYC: Elsevier.
- Bissag, E. M. (2017, April). Fast and Robust GPS Fix Using One Millisecond of Data. Proc of the 16th ACM /IEEE International Conference on Information Processing in IPSN, 223-234.
Pathak, H. P., & al, e. (2015). Visible light communication, networking, and sensing: a survey, potential, and challenges. IEEE Communications Surveys & Tutorials, pp. 17, 4: 2047-2077.
Psiaki, M., & al., e. (2013). GPS Spoofing Detection via Dual-Receiver Correlation of Military Signals. IEEE Tran of Aerospace & Electrical systems, vol 49, issue 4, pp. 2250-2260.
R.K. Nichols & Lekkas, P. (2002). Wireless Security; Threats, Models & Solutions. NYC: McGraw Hill.
R.K. Nichols, e. a. (2020). Unmanned Vehicle Systems & Operations on Air, Sea & Land. Manhattan, KS: New Prairie Press #35.
Ranganathan, A., & al., e. (2016). SPREE: A Spoofing Resistant GPS Receiver. Proc. of the 22nd ann Inter Conf. on Mobile Computing and Networking, ACM, pp. 348-360.
S.A.Shaukat, & al., e. (2016). Robust vehicle localization with GPS dropouts. 6th ann Inter Conf on Intelligent and advanced systems (pp. 1-6). IEEE.
Schaefer, M., & Pearson, A. (2021). GPS and GNSS Technology in Geosciences. NYC: Elsevier.
Schmidt, D., & al, e. (2016). A Survey and Analysis of GNSS Spoofing Threat and Countermeasures. ACM Computing Surveys (CSUR), 48(4).
Shrivastava, G. P. (2021). GPS and GNSS Technology in the Geosciences. NYC: Elsevier.
Spilker, J. (1996). Fundamentals of Signal Tracking Theory. Prog in Astronautics & Aeronautics, 163:245-328.
Strohmeier, M. (2015). On the security of the automatic dependent surveillance-broadcast protocol. IEEE Communications Surveys & Tutorials, 17:1066-1087.
The system, H. K. (1942). US Patent No. 2,292,387.
T.E. Humphrees, e. (2008). Assessing the Spoofing Threat: Development of a portable GPS Spoofing Civilian Spoofer. ION (pp. Sept 16-19). Savana, GA: ION.
The Royal Academy of Engineering. (2011). Global Navigation Space Systems: Reliance and Vulnerabilities. London: The Royal Academy of Engineering.
Tippenhauer, N., & et.al. (2011). On the requirements for successful spoofing attacks. Proc. of the 18th ACM Conf. on Computing and communications security (CCS), 75-86.
Tsui, J. B. (2000). Fundamentals of Global Positioning Systems Receivers – A Software Approach. NYC: John Wiley & Sons.
USGPO. (2020, April). Global Positioning System (GPS) Standard Positioning Service (SPS) 5th ed. Retrieved from https://www.gps.gov/technical/ps/: https://www.gps.gov/technical/ps/2020-SPS-performance-standard.pdf
USGPO. (2021, June 14). What is GPS? Retrieved from Gps.gov: www.gps.gov/sysytems/gps
Warner, J. S., & Johnston, R. (2003). GPS Spoofing Countermeasures. Journal of Security Administration. Retrieved from https://www.semanticscholar.org/paper/GPS-Spoofing-Countermeasures-Warner-Johnston/36e17f723bff8d429aca4714abe54500a9edaa49
Warner, J., & Johnson, &. R. (2002). A Simple Demonstration that the system (GPS) is vulnerable to spoofing. J. of Security Administration. Retrieved from https://the-eye.eu/public/Books/Electronic%20Archive/GPS-Spoofing-2002-2003.pdf
Wesson, K. (2014, May). Secure Navigation and Timing without Local Storage of Secret Keys. Ph.D. Thesis.
Wikipedia. (2021, June 2). Global Positioning System. Retrieved from https://en.wikipedia.org/wiki/: https://en.wikipedia.org/wiki/Global_Positioning_System
- Ng & Gao, G. (2016). Mitigating jamming & meaconing attacks using direct GPS positioning. In Position, Location & Navigation Symposium (PLANS) IEEE/ION, 1021-1026.
Ye, H., & al, e. (2012). track: Infrastructure-free floor localization via mobile phone sensing. IEEE Inter Conf. on Pervasive computing and communications, pp. 2-10.
Endnotes
[1] ECD – Dr. Manuel Eichelberger’s advanced implementation of CD to detect and mitigate spoofing attacks on GPS or ADS-B signals (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
[2] The detailed ECD Navigation model and supporting equations are found in the primary reference (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
[3] The results are defined and graphically presented in (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019) p87-ff.
[4] The author has nicknamed it to Honor Dr. Manuel Eichelberger’s brilliant doctoral research, ECD. ECD is Dr. Manuel Eichelberger’s advanced implementation of CD to detect and mitigate spoofing attacks on GPS or ADS-B signals
[5] This is a key point. CD reduces this timestamping process significantly.
[6] Data is sent on a carrier frequency of 1575.42 MHz. (IS-GPS-200G, 2013)
[7] GPS satellites operate on atomic frequency standards; the receivers are not synchronized to GPS time.
[8] Because the receiver must decode all that data, it must continuously track and process the satellite signals, which translates to high energy consumption. Furthermore, the TTFF on startup costs the user both latency and power.
[9] The deviation is defined as the time offset multiplied by the speed of light plus the location distance.
[10] For those who insist on SI / metric, 1 km = ~ 0.62 mi (miles)
[11] Data bit flips can happen. The normal practice is 2 milliseconds of sample time.
[12] The vector/tensor mathematics for localization are reasonably complex and can be found in Chapter 5.3 of (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
[13] Cloud offloading also makes ECD suitable for energy-constrained sensors.
[14] (Nichols & al., 2020) have argued the case for cryptographic authentication on civilian UAS /UUV and expanded the INFOSEC requirements.
[15] To evaluate the performance of the (Jovanovic & Botteron, 2014) CM, an attack was performed on a GNSS receiver through a GSS8000 full constellation simulator attached to a rooftop antenna.
[16] This cross-correlation portion of this CM method syncs well as a forerunner of ECD.
[17] This is a key section to understanding the beauty of ECD. The entire SIC algorithm and ECD implications are found in detail in (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019) p81-ff.
[18] This is what makes jamming a lesser attack. The jamming is detectable by observing the noise floor, in-band power levels, and loss of signal-lock takeover.
[19] See (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019) Sections 6.5 – 6.7 pages 84-94.
[20] See (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019) Sections 5.34 – 5.5 for extended discussions on space discretization, satellite visible set V, time discretization, averaging over likely hypotheses, hypothesis h, coding, efficient implementation of the B&B, local oscillator bias, criteria and test evaluations of ECD, computational considerations, and conclusions. (Closas & al., 2007)(J. Liu & et.al., 2012) (Diggelen, 2009)
[21] This is accomplished in the acquisition stage of a GPS receiver. The received signals are correlated with the C/A codes.
[22] (Nichols R. K., 2020) presents a model of Risk as a function of Threats, Vulnerabilities, Impact, and Countermeasures known as the Ryan- Nichols equations, that models the qualitative effects of information flow through the communications and navigation systems in UAS. The model is based on the brilliant INFOSEC work of Dr. Julie J.C.H. Ryan and Dr. Daniel J. Ryan, described in many of the authors’ NPP books.
[23] These INFOSEC goals are admirable but considering that most GPS and UAS COTS do not have sufficient GPS spoofing countermeasures or cybersecurity protections (most are legacy), the list is more of a wish list. [Author opinion]
[24] Please note the word “should.” Hackers just love this word.
[25] Wireless networks present few obstacles to access and can easily be attacked by open-source software. (R.K. Nichols, 2020)
[26] This is still true in legacy systems. Newer implementations have additional protections. UAS systems are notoriously weak in terms of security.
[27] Ali et al. identified that jamming of GPS transmissions from the satellite affected the ADS-B system. (Ali, 2014)This is a rather obvious statement of research considering that we have also established that the vulnerabilities of GNSS/GPS pass down to ADS-B systems because they are a subset of the larger problem.
[28] Dave Adamy is the leading global expert in EW. He teaches it is more difficult to jam a PSR due to its rotating antenna and higher transmission power. (Adamy, 2001)
[29] This might have been true in 2011, a decade of change, growth, cost-effective COTS, and state-sponsored hackers. Say this observation is severely dated. (Author comment)
[30] Author comment based on experience. Jamming devices are as small as your cell phone and more powerful than computers available in 2011. (Nichols R. K., 2020)
[31] This is a headache. Consider a SWARM of 100 + UAS bursting onto the controller’s screen at a busy airport.
[32] This is about the consumption of a GSM base station.
[33] A Boeing 747 has an average power consumption of 140 MW, leaving power to spare for GPS communications.
[34] Uncompensated latency of up to 0.6 s. (Cornell – LII, 2021)
[35] 1 m = 3.280 ft
[36] TDOA is also called multilateration.
[37] DIY – Do it yourself
[38] INS- an inertial navigation system is composed of motion sensors (accelerometer, gyrometer, and magnetometer), allowing the determination of the absolute movement of a platform. Using this information and knowledge of the last position, it is possible to use dead reckoning to estimate the platform’s position, velocity, and time after spoofing or jamming detection.

