15 Cyber Weapons and CBRNE
By Professor Randall K. Nichols, Kansas State University
Student Objectives
In this chapter, we will explore:
- 1) Threats to Air Defense Systems and CBRNE facilities by hostile use of sUAS / UAS,
- 2) A look at the history to demonstrate the increasing threat level that sUAS/UAS poses to ADS and CBRN?
- 3) Discuss the Infrastructure interdependencies and leveraging ability of cyber-attacks,
- 4) Classify Cyber-attacks by area on CBRN facilities
- 5) Discuss the Counter – UAS problem (how do we intercept the UAS headed for an ADS or CBRN facility. Emphasis will be on the ADS because the CBRN is low-hanging fruit without it.
- 6) Discuss the operational measures and active/passive measures against hostile-controlled sUAS /UAS targeting an ADS
Problem – The Risk of Terrorist Attack vs. U.S. Air Defense System or CBRN Facilities
The risk of successful terrorist attacks on U.S. Air Defense Systems (ADS) and CBRNE facilities by sUAS /UAS is growing because of increased commercial capabilities and accessibility of advanced small drones. They can carry sophisticated imaging equipment with significant and potentially lethal payloads, perform extensive Intelligence, Surveillance, and Reconnaissance (ISR) missions, and are readily available to civilians. A significant threat to civilian and military UAS operations, CBRN facilities, and safety is posed by UAS/drones controlled by hostile actors, including large potential threats to U.S. Air Defense Systems and CBRN facilities from UAS SWARMS. (Nichols R. K., Chapter 18: Cybersecurity Counter Unmanned Aircraft Systems (C-UAS) and Artificial Intelligence, 2022) Another significant threat is maritime operations and navigation / GPS / GNSS signals spoofing. (Nichols R. K., Chapter 14: Maritime Cybersecurity, 2021)
Think of the UASs / Drones as flying SCADA machines or flying advanced telephones. All the SCADA vulnerabilities or wireless communications vulnerabilities exist and can be exploited from a defensive POV. These vulnerabilities were discussed in detail in (Nichols R. R., 2020), (Nichols R. K. et al., 2019) and (Nichols R. K., Chapter 18: Cybersecurity Counter Unmanned Aircraft Systems (C-UAS) and Artificial Intelligence, 2022)
However, from the attack POV, UAS / drones are effective delivery systems, and the same SCADA vulnerabilities and wireless exploits are available on their targets. The weapon systems used in potential attacks on Critical Infrastructure Systems (CIS)[1] or Industrial Control Systems (ICS) are more powerful than the defenses when they involve CBRNECy payloads. Advancing technologies have integrated with ICS as one. Remote access to controlled equipment facilities has become the standard in almost every industry. (Martinelli, 2017)
Cybersecurity is defined as the protection of information systems from theft or damage to the hardware, the software, and the information on them, and from disruption or misdirection of the services they provide identified. (Gasser, 1988) CBRNE cybersecurity is defined as the practice of security of computer systems, ICS, and networks in the critical industry that involves CBRNE agents. CBRNECy introduces the cyber components, security, and management if damaged entails global danger.
For the special case of CBRNECy assets, whether attacked via UAS /drone, any nuclear or chemical facility is equal to a warfare attack. As of today, and as publicly revealed, the maximum damage caused by cyberattacks was related to:
- CBRNE agent device rendered unstable or non-fit to the purpose (Stuxnet, Iran),
- though theoretical analysis confirms that the attackers could physically
- destroy the device.
- Power distribution was rendered offline (BlackEnergy3, Ukraine), where the power supply
ply (APS) device was reconfigured to disable the power distribution.
- Communications disabled (BlackEnergy3, Ukraine). (Martinelli, 2017)
As per the predictions by Bruce Schneier and IEEE (Staff I., 2013), the possible cyber-
attack capabilities in the future will relate to (Schneier 2015):
- Hybrid warfare (Cyber and any other warfare domains)
- Global Denial of Service (e.g., Internet infrastructure collapse)
- Refined delivery via email (advancements in spam and spear phishing)
- Advanced malware delivery via web applications
- Substantially increased malware sophistication and AI
- Attacks on critical infrastructure will increase
- Lone-wolf terrorism
Cyber-attacks are already a threat to national security, and NATO recognizes cyberspace as one of the warfare domains. (Nichols R. R., 2020) With the exponential growth of cyber technologies, the threat to embedded devices and ICS will only increase and, if not prevented, will reach the global level. The authors predict that the next evolution of cyber weapons will be deployed from UAS/ drones against CBRNE assets. After the U.S. Afghanistan withdrawal debacle in 2021, the hard-core terrorists have a billion dollars plus of advanced military UAS toys to experiment with and plenty of offered technical help from its neighbors to the South and North. The Taliban have inherited some unmanned weapons from their fellow terrorists in Afghanistan. (DRONESEC, 2021)
CBRN Infrastructure Attacks
Not very public, not often, but CBRN infrastructure cyber-attacks / disruptions have occurred.[2] In January 2002, malware successfully breached the perimeter network defenses at Ohio’s Davis-Besse nuclear power plant, infiltrated the private networks, and disabled the safety monitoring system for five hours. (Poulsen, 2003) In October 2006, cyber attackers gained access to computer systems at Harrisburg, PA, water treatment plant. The ICS network was compromised, threatening the plant’s water treatment operations. (CIO Staff, 2006) In October 2008, the derailment of the tram in the city of Lodz injured 12 people. The attacker used a repurposed T.V. remote control to change the track points through an Infrared sensor. (Schneier on Security, 2008) The 2010 event in Iran confirmed that information technology could trigger remote CBRN attacks and be a direct threat to physical CBRN ICS equipment. Stuxnet was the first CYBERWEAPON. [3] It was designed to infiltrate and cause physical disruption in multiple ICS in the Natanz CBRN facility and other facilities. It slowed the Iranian nuclear ambitions by about six months. (Wilson, 2014) In 2011, the Trojan “Poison Ivy” was used to collect intellectual property from twenty-nine international chemical companies. (Dark Reading Staff, 2013) In 2014, Malware Shamoon wiped 30,000 workstations in Saudi Aramco’s corporate network by bypassing firewalls and intrusion detection systems (IDS) on a large scale. (Staff, 2014) Again, in 2014, 13 different types of malware disguised as ICS/SCADA software updates to major corporations’ systems were detected in spear-phishing emails. Forensic analysis determined that malware was a repurposed banking Trojan designed to capture private identifying information (PII) and credentials. (Higgins, 2015) In 2015, a BlackEnergy3 DOS attack on a power plant and multiple substations in Ukraine triggered a severe power outage. (Miller, 2022) Since 2015, it is estimated that corporations globally have suffered over 1,518 million ransomware attacks. (Johnson, 2022)
The events listed above indicate a constant evolution of attack CBRNECy capabilities of threat actors. The next evolution is swift, silent, and deadly by air delivered by UAS / drones.
Contributing Technologies
Commercial and military UAS are integrally linked to the payload, navigation, communications, and control linkages from the ground, air, or satellite. These advanced small /medium-sized drones are vulnerable to cyber-attack and hostile takeover, so UAS designers and operators must be aware of cybersecurity countermeasures and defenses to reduce the risk of takeover and penetration by hostile or negligent forces on either ADS or CBRN facilities. (Nichols, Mumm, Lonstein, Ryan, & and Carter, 2018)
UAS are being designed with increasingly advanced Artificial Intelligence (AI) and automation capabilities that can be beneficial and harmful. The increased automation and AI capabilities can be used to complete Dull, Dangerous, and Dirty (DDD) missions in all weather conditions and are capable of longer flying times and endurance at more effective altitudes. Unfortunately, when human decisions are taken out of the loop, software and firmware code can be intercepted, replaced, re-engineered, spoofed, exploited, destroyed, and used against the originator. Iran accomplished this in 2011 (Jaffe & Erdbrink, 2011).
The number and type of possible cyber exploits against UAS key CBRN control systems (payloads, navigation, rotors, battery) represent a large, diverse, and lethal attack vector set. However, the UAS designer and operator are not without an effective arsenal of Counter Unmanned Aircraft Systems (C-UAS) measures. (Nichols R. R., 2020)
Attack / Defense Scenarios
When hostile forces fly a UAS against ADS or CBRN facilities, the cyber risk analyst’s mission is to determine the Risk, Threats, Vulnerabilities, Impacts, and Countermeasures that may apply in an attack/defense scenario. The attacker has the advantage of flexibility, source, type of cyber-vector, location, height, frequency, and lethality of his cyber-attack. The more difficult job of the defense includes identifying the intruder and intrusion measure and applying the correct countermeasure [cybersecurity (non-kinetic), physical (kinetic), or electronic] in real-time.
AI[4] plays a role on both sides of this attack/defense scenario. It speeds up the decision-making capabilities of both attacker and defender and can determine the risk mismatch between opposing forces. Cybersecurity attacks on UAS or CBRNE assets should never be underestimated; damage to ships, navigation systems, commercial airplanes, property, and privacy is possible. (Nichols, Mumm, Lonstein, Ryan, & and Carter, 2018)
Description of the sUAS/UAS Landscape – What’s available for Deployment against CBRNE Assets?
Autonomy v Automation Levels
sUAS/UAS automation is divided into five classes of technology. Table 15.1 shows a breakdown of the automation landscape.
Table 15.1 Automation Levels
| Automation Level | Name | Characteristics | Examples |
| Level 1 | Slave | Assist with piloting, reacting to disturbance, Remote Control Tethers (R.C.) | Drone Parrot, Quad Flyer GAUI |
| Level 2 | Automated | Maintains its flying orders and receives higher-level orders and commands.
Levels 1 and 2 are commonplace in the market. They require pilot intervention and a continuous communication link(s). Reasonable prices <$1500 US, small size, weight < 10 lbs.: |
Chinese Dove, DJI Phantom series, Raven, Scan Eagle, Harpy |
| Level 3 | Automated -Navigation | Automated navigation (pre-programmed flight plan, based on GPS coordinates). Some with Follow Me autopilot settings enable the sUAS to follow the operator automatically. Micro-UAS premium cost < $20,000 US.
|
Dragonfly, Microdrone GMBH, Fly-n-Sense, Micro copter,
ASN-205, GJ-1, aka Wing Loong I. Fire Scout, WASP III, Shadow, Heron, Hermes, Barracuda |
| Level 4 | Contextual Response
CA[5] |
Response from contextual data (w/o human intervention) for Collision Avoidance (C.A.). They use active SAA and require a mission plan. Costs and missions are classified. | Predator, Reaper, Avenger, Global Hawk, BZK-005, Mantis, Soaring Dragon, Sentinel
|
| Level 5 | Decision Maker | Full AI does not require human intervention. Includes AI Decision-making with heavily networked computer support, has perceptive sensors for space and time. Can complete complex missions in unknown environments, capable of intelligent adjustments including mission rescheduling and key word-adaptive control. Decision-Maker (expert system) works from contextual data with coordination and collaboration of signals [Think “Terminator”]
|
Levels 4 and 5 are confined to laboratories.
X47C series
Classified Cost and Missions |
Source: (Nichols R. K., Drone Wars: Threats, Vulnerabilities and Hostile Use of UAS, 2017) and (Nichols, Mumm, Lonstein, Ryan, & and Carter, 2018)
Table 15.1 shows the normal five levels of automation that characterize UAS systems with some examples of commercial vehicles at each level. NASA has a more detailed automation breakdown based on the OODA (Observe, Orient, Decide, and Act) decision loops (Barnhart, 2012).
Level 1 Slave and Level 2 minimally automated UASs are commonly sold by Amazon, Walmart, and similar outlets. The human pilot makes all the decisions and has complete control of the flying orders. Level 3 steps up the navigation capabilities with the ability to use a mission plan.
Levels 4 and 5 add higher-level decision-making capabilities; collision avoidance without human intervention, complex mission planning in all weather conditions, expert systems intelligence without human intervention [i.e., Artificial Intelligence (AI) and advanced Sense and Avoid systems (SAA)]. Level 5 is not commercially available, but many designers are well on their way to a fully operational Level 5 UAS. Much of the information on Level 5 designs and capabilities are classified. In the author’s opinion, removing humans from the decision loop in weaponized Level 5 UASs is a very risky venture.
UAS Collaboration
Table 15.2 UAS Collaboration shows four types of possible UAS collaborations. At the lower end of a threat scale is the isolated attack by one UAS or a small group of UAS. The Type 1 specific missions may be piloted or autonomous. They carry light payloads, are affordable, and are easily assembled in the field. An example is the Raven used by U.S. Special Forces. The countermeasure for this type of attack is to identify the pilot or leader vehicle and destroy or disable it.
A UAS attack team is particularly effective against divided attack targets since disabling part of the UAS Team does not guarantee mission failure. The real vulnerability of the UAS team is the Chief; all synchronization and updates go through the Chief. If the Chief is disabled or destroyed, the team is rendered useless. Identifying the Chief is critical and is normally accomplished through intercepting communications (Nichols, Mumm, Lonstein, Ryan, & Carter, 2018).
Far more dangerous is the SWARM configuration, especially at the higher levels of autonomous engagement. SWARMS have several advantages. They are efficient through sheer numbers, and even when not controlled or automated, they display a decentralized intelligence, much like a shoal of fish that moves together synchronously. UAS SWARMS are not dependent on the survival of all of the members. Destroy part of the SWARM, and the rest will continue their mission without abatement (Nichols, Mumm, Lonstein, Ryan, & Carter, 2018).
Known countermeasures for a SWARM are:
1) Disruptors change the Strategic Global View of SWARM (its only real vulnerability)
2) Force defender collaboration
3) Long-range acoustical weapons aimed at MEMS to disrupt SCADA and rotor subsystems
4) Classified / OPEN methods involving DEW, Drone catchers, Lasers, GPS spoofing (Nichols R. K. et al., Counter Unmanned Aircraft Systems Technologies, and Operations, 2020)
Research on acoustic countermeasures indicates that they are successful against SWARMS and have the secondary advantage of being able to Identify Friend or Foe (IFF) using searchable sound frequency libraries (Nichols R. K. et al., 2019). (Nichols R. K. et al., Counter Unmanned Aircraft Systems Technologies, and Operations, 2020) China appears to be the leader in innovative UAS SWARM intelligence through the Chinese Electronics Technology Group Corporation (CETC) (Kania, 2017).
Table 15.2 UAS Collaboration
| Type | Name | Advantages | Disadvantages | Countermeasures |
| 1 | Isolated Individual UAS | Piloted or autonomous w/ a specific mission to perform. Small, easy to assemble, affordable, light payloads.
|
Stop, disable, or destroy the pilot and remove the threat. | |
| 2 | Group of Individual UASs | Each UAS has its mission, but the group is not a coordinated team.
An increased number of attackers increases the potential for success by saturating the defenses. |
The sphere of action may be different for each UAS’s mission. Mission will not be fully completed when individual UASs are destroyed.
|
Stop, disable, discover, and deter or destroy pilot(s), and threat(s) may be removed.
|
| 3 | Team of UASs (All members assigned specialized tasks and coordinated by Chief) | Particularly effective against divided attack targets. Level 3 allows automatic navigation and synchronized actions but no update to mission plans based on-field activities.
Level 5 permits continuous updates and communications, commando style.
|
Level 4 (w/o humans) yields surrounding reactions but may lose synchronization between team members. | Stop, disable, or destroy team members. Determine behavior logically and intervene. The survival of team members is critical to defense actions. Mitigate the threat.
|
| 4 | UAS SWARM (Uniform mass of undifferentiated individuals w/o Chief at level 4 or 5) | Efficient based on numbers, emergent large group behaviors and reactions, not controlled or automated, decentralized intelligence – think shoal of fish w/ evolving local rules. A highly defense resistant form, not based on the survivability of individual members, with no hierarchy.
Strategic Weapon
|
None except maybe cost and launch coordination | Disrupt/Change the Strategic Global View of SWARM (its only real vulnerability). Defender collaboration. (Kania, 2017)
Subject to Acoustic Countermeasures up to a mile. Research at short distances and loud sound at resonance is particularly effective against MEMS and rotor systems (Nichols R. K. et al., 2019) |
Source: (Nichols R. K., Drone Wars: Threats, Vulnerabilities and Hostile Use of UAS, 2017)
Cyber Related CBRNE Attacks
A cyberattack against ADS or CBRN launched from a UAS / drone, or SWARM can be conducted in many ways and for many reasons. Cyber-attacks on CBRNE can be classified by area, industry, perceivable damage, and possible attack scenario. Cyber-attack vectors have many custom-designed exploits such as flying false routers, access points, network layers, and specialized software/malware/ransomware. (Martinelli, 2017) Nichols presents a taxonomy of wireless cyber-attacks which can be launched against or by UAS. (Nichols R. K., Chapter 18: Cybersecurity Counter Unmanned Aircraft Systems (C-UAS) and Artificial Intelligence, 2022) (Nichols R. K. et al., Counter Unmanned Aircraft Systems Technologies, and Operations, 2020)
Table 15.3 reflects potential CBRNECy cyber-attacks by area.
There are four attack vectors on any facility as a structure. Attacks #s 1-3 may be launched by air vehicle / UAS. Attack 4 may be assisted by UAS. Cyber-attack: the attackers have no physical access to the systems or devices.
- Physical attack: the attackers have no remote access to systems or devices.
- Cyber-enabled physical attack: security system is compromised to enable easy physical access for the attackers.
- Physical-enabled cyber-attack: physical actions allow remote access to unreachable computer systems or networks. (Martinelli, 2017)
- Physical-enabled cyber-attack: physical actions allow remote access to unreachable computer systems or networks (rogue devices or rogue access points or spy)
See Figure 15.1 and 15.2 for a view of CIS interrelations and dependencies. (Peerenboom, 2001)
Figure 15.1 CIS Shared Threats
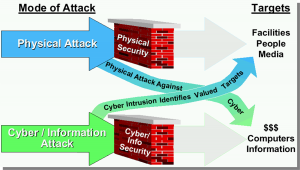
Source: (Peerenboom, 2001)
Figure 15.2 Infrastructure Interdependencies
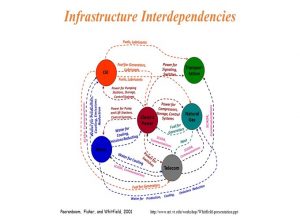
Source: (Peerenboom, 2001)
Table 15.3 Cyber-attacks by area of CBRNE
| CRBNECy Industry | Applications | Perceivable Damage | Possible Airborne Attack Scenarios[6] |
| Chemical | Chemical production
Logistics Storage |
Destruction
Area contamination Loss of life industrial |
Industrial espionage
ICS controlling chemical delivery |
| Biological | Medical facilities
Research facilities |
Destruction
Area contamination Disease outbreak Loss of life |
Espionage
Fake medical details Reputation loss based on false information |
| Radioactive | Production
Storage Logistics Decontamination |
Destruction
Area contamination Loss of life |
Espionage
Denial of Service (DOS) |
| Nuclear | Power production destruction | Destruction
Area contamination Planet scale disaster Loss of life |
Espionage
Destruction Loss of life Terrorism Guerrilla warfare Civil war |
| Explosives | Production
Logistics Demolitions Excavation Warfare |
Destruction
Area contamination Terrorism act Loss of life |
Espionage
Counterespionage Psychological warfare Cyberwarfare Warfare support Electronic warfare synchronization / vector intersection |
| Cyber Domain | Cyber command | Misinformation
False signals Destruction Area contamination Loss of life formation
|
Source: Modified by the author from (Martinelli, 2017)
Drones as Rogue Access Points
The fourth Cyber-attack vector is particularly interesting ( Physical-enabled cyber-attack: physical actions allow remote access to unreachable computer systems or networks (rogue devices or rogue access points or airborne spy). The drone acts as a mobile airborne access point. Cyber techniques that incorporate physical access to internal systems and networks are:
- Wired network physical access (wiretapping or remote keylogging)
- Wireless network physical access [long-range antenna’s, HAPS, [7] WiFi attack vectors, BYOD) – connecting to the network by the physical proximity of the wireless routing device (Access point or Router)]
- Insider threat by an employee flying a drone inside the security perimeter. The drone can communicate with other drones or a command post. It may be used as a jump-off station to deploy malware. (Martinelli, 2017)
CBRNE Attack Scenarios
The Norwegian Defense Research Establishment developed the following CBRNE attack scenarios. (Heireng, 2015):
- Chemical attack in the city center – Explosion and dispersion of Sulphur mustard
- Chemical transport accident – Train derailment causing chlorine dispersal
- Radiological dispersal in the city – Radioactive cesium spread in fire
- Radiological attack on public transportation – hidden radioactive source
- Nuclear power plant accident – Release of fission products
- Nuclear submarine accident – Onboard fires
- Hoax – Unknown powder in the congress center
It is easy to contemplate how a UAS Team or SWARM could force multiply (WMDD) most of the scenarios above, especially number 7!
(Martinelli, 2017) provides a palatable set of Cyber-attack scenarios on CBRNE infrastructure. They are listed in Table 15.4. UAS Cyber-attacks can enable or support conventional attacks by enhancing the remote access on Table 15.4 CIS facilities. They can:
- Provide information about city traffic, mass gatherings, emergency events to plan the attack on the target;
- Enable false alarms or disable the positive alarms to better control the municipal response during the attack;
- Trigger remote detonation devices or electronically controlled release valves on chemical tanks. (Martinelli, 2017)
Table 15.4 Cyber Attack Scenarios by Area in CBRNE
| AREA | THREAT | SCENARIO |
| Chemical | Denial of Service (DoS) and area contamination | DoS in ICS may cause the shutdown, critical malfunction, and/or chemical leakage, contaminating the area inside or outside a facility. |
| Chemical | Water supply contamination | Tampering with the configuration of the water purification system, endangering consumer lives |
| Biological | Public figure setup | Medical records of a public figure accessed, edited with compromising values, and widely released to the public as truth |
| Medical | Pharmaceuticals formula change biological | Biological research facility accessed. Critical information is tampered with to divert funds or slow down research |
| Radioactive | Terrorist attack causing | Causing the radiation outbreak with the physical or remote attack, and by accessing the ICS switching off the radiation sensors, prevents it from triggering alarms, thus preventing timely response, and multiplying the damage. |
| Nuclear | Equipment corruption production | Production of valuable material is intentionally slowed down nuclear power blackouts |
| Nuclear | Power blackout | ICS of the power plant is accessed to disable power distribution |
| Nuclear | Meltdown | The critical scenario of disabling the reactor cooling system, causing the meltdown and explosion and eradiation. |
Source: (Martinelli, 2017)
The use of drones to plan CBRNECy attack scenarios is not far afield. A special report by DRONESEC Notify on the Taliban in August 2021 confirms the Taliban’s serious interest, operational planning, and aborted attempts. (DRONESEC, 2021)
(Nichols R. R., 2020) and (Nichols R. K., Chapter 18: Cybersecurity Counter Unmanned Aircraft Systems (C-UAS) and Artificial Intelligence, 2022) provide a detailed discussion of SCADA, ICS, and Cyber-attack taxonomy for threats and countermeasures involving these systems.
What Is the Counter
Picture one hundred plus hostile UASs headed toward a military target, ADS, or CBRN facility with lethal payloads. How do military planners envision defenses against a hostile UAS SWARM attack? The author will concentrate on the ADS side of the equation for defense because if the ADS is disabled, the CBRN facility is low-hanging fruit based on its physical defenses. From our previous discussion, we note that CBRN facilities can be attacked from the air using UAS and leveraging cyber technologies.
The risk of successful terrorist attacks on U.S. Air Defense Systems (ADS) or CBRN facilities by hostile UASs increases by improving commercial capabilities and accessibility. Advanced small drones, capable of carrying sophisticated imaging equipment and significant payloads, are readily available to the public. A range of terrorist, insurgent, criminal, corporate, and activist threat groups have demonstrated their ability to use civilian drones and gather intelligence. How does the country defend against a growing UAS threat? This is known as the Counter-UAS Problem. General James D. Mattis, SECDEF (U.S. Secretary of Defense), summed up the problem succinctly:
“Unmanned Aircraft are being developed with more technological systems and capabilities. They can duplicate some of the capabilities of manned aircraft for both surveillance/reconnaissance and attack missions. They can be small enough and/or slow enough to elude detection by standard early warning sensor systems and could pose a formidable threat to friendly forces.” (Chairman, 2012)
Operational Protection from Hostile UAS Attacks – A Helicopter View
According to LCDR Boutros of the Navy War College, developing technologies do not paint a pleasant picture of the Counter-UAS problem (Boutros, Operational Protection 2015). UAS has seen a widespread proliferation among both state and non-state actors. This is cause for concern to U.S. Operational Commanders. (Boutros, 2015). General James D. Mattis, SECDEF, concluded:
“The proliferation of low cost, tactical unmanned aerial systems demands we think about this potential threat now… we must understand the threat these systems present to our joint force and develop the tactics, techniques, and procedures to counter the problem.” (Chairman, 2012) (Myer, 2013)
It can be argued from the quantity and diversity of products that China is the current leader in this technology, and China is thoroughly exercising its UAS capabilities in the Spratly Islands (Nichols, Mumm, Lonstein, Ryan, & and Carter, 2018). However, more than 90 countries and non-state actors have UAS technology and foster terrorism. “Most of the UAS systems, except for China, Russia, USA, Turkey, Saudi Arabia, and Iran inventories are low-technology, Intelligence, Surveillance, and Reconnaissance (ISR) platforms” (Boutros, 2015). Experts believe that by 2025 China will produce over 50% of UAS systems (Yan, 2017). Yan predicts that China’s commercial drone market will top USD 9B in 2020 (Yan, 2017). The market value will triple to 180 billion yuan by 2025, according to the guidelines from the Chinese Ministry of Industry and Information Technology. This estimate is much higher than a forecast by an iResearch report last year (iResearch, 2016), which said that the overall market of UAVs, commonly known as drones, could reach 75 billion yuan by 2025 in China (Yan, 2017).
Iran has supplied long-range, low technology Ababil UAS weapons systems to Syria and Sudan and extremist groups like Hezbollah, Hamas, and ISIS. Hezbollah’s inventory is estimated at over 200 UAS, which concerns the Israeli military commanders (Zwijnwenburg, 2014).
The DOD’s 2018 Joint Publication (J.P.) 3-01 “Countering Air and Missile Threats” identifies friendly assets that an adversary may attack during a campaign using UAS. A theater commander must plan counter-UAS actions against air defense sites, logistics centers, and critical national infrastructure (Boutros, 2015). “Due to their small size and unique flying signatures, many UAS are difficult to detect, identify, track, and engage with current joint air defense systems. The increasing proliferation of global UAS has exposed a critical vulnerability in the protection function of operational commanders, requiring joint efforts to include intelligence, electronic warfare (EW), cyber warfare (CW), and FIRES (the use of weapons systems to create a specific lethal or non-lethal effect on a target)” (Boutros, 2015). But UAS are not invincible. Neutralizing threats or mitigating risk includes active and passive defense methods with kinetic and non-kinetic FIRES.[8] (DoD, J.P. 3-0 Joint Operations, 2018).
Countering UAS Air Threats
Advanced UAS can carry large payloads at great distances. U.S. Predator and Global Hawk UAS, “Chinese Pterodactyl and Soar Dragon counterparts, and Iranian Ababil can carry at least 500 Kg payloads greater than 300 km” (Boutros, 2015). “They can be armed or unarmed, with ISR payloads, communications relays, Over-The-Horizon (OTH) target acquisition, and precision strike capabilities” (Boutros, 2015).
“Shorter range, tactical, small/micro UAS may not have the distance or payload capacity of more advanced systems, but they can seriously impact a campaign (or U.S. Homeland Defense). Because of their size, their heat signatures are almost nonexistent and easily evade detection. They offer more freedom of action. They can be launched from within U.S. air defense zones and fly to their targets in less time than it takes for a coordinated response” (Boutros, 2015). [Nightmare alert: Imagine a swarm of UAS carrying small, potent binary bomb payloads attacking a U.S. carrier at port less than one mile away from the UAS launch point.] The enemy can effectively balance space, time, force, and arguably frequency. (Beaudoin, 2011). “Small UAS (sUAS) can perform short-range ISR, be outfitted with explosive charges or chemical and biological agents for aerial dispersion, or simply fly over troops or civilians to demoralize” (Boutros, 2015). Given the effectiveness of enemy use of IEDs in Iraq and Afghanistan, a mobile, airborne version would take the problem to an entirely new level! (Nichols R.-0. , 2016).
Vulnerabilities Perspective
sUAS are vulnerable to kinetic and non-kinetic outside influence in four different areas: their link to a ground station, the ground station itself, the aircraft’s various sensors, and cyber weapons. The military recognizes the first three factors; the authors will concentrate on the fourth.
“In 2009, Iraqi insurgents successfully hacked into U.S. Reaper drones, crashing them.” (Boutros, 2015) (Horowitz, 2014). “In September of 2011, ground control stations at Creech AFB were infected by a virus, temporarily grounding the entire UAS fleet.” (Boutros, 2015) (Hartman, 2013). UAS onboard sensors can be manipulated in many ways. “High-intensity light directed at an optical sensor can blind it. GPS receivers can be cyber-spoofed, transmitting a stronger, but false GPS signal to a receiver, resulting in inaccurate navigation. Influencing the local magnetic field can adversely affect both onboard hard drives. Would it be best to call them a processor/chipset/ or form factor? and sensors that require magnetic orientation to operate correctly.” (Boutros, 2015) (Hartman, 2013).
The attacker’s objective is to understand better UAS subsystems, which facilitates exploiting their weaknesses. The author contends that the hostile technology of remote-controlled warfare is difficult to control or abort; the best defense (counter-UAS) is to address the root drivers of these threats. Cyber offensive weapons against UAS SAA and SCADA targets (Nichols, Mumm, Lonstein, Ryan, & Carter, 2018).
Conventional Vulnerabilities of Air Defense Systems (ADS), Attacks By sUAS, and Countermeasures
A simplified, non-classified view of the U.S. Air Defense System (ADS) against a hostile UAS attack occurs in two stages: [9]
- Early Detection and Identification of “Danger Close” (Myer, 2013) [10]
- We have applied appropriate countermeasures with the secondary goal of restricting collateral damage.
The traditional ADS family of tools for detection include:
- Active Radar Surveillance – generate waves and use rebound echoes from the UAS to locate and estimate distance, approach speed, size, penetration vector, and short-term trajectory.
- Passive Monitoring – cover the electromagnetic spectrum of visible, thermal infrared, and radio waves on common communications channels.
When considering hostile UAS defense, planners need to consider several issues. The U.S. ADS is optimized for missiles and aircraft deployed at high altitudes and speeds. ADS data fusion (detection, identification, weapon lock-on, execute countermeasures) works better with larger targets, not very small ones like UAS/sUAS. The U.S. ADS is effectively reactive for longer ranges; close reactive engagements, such as sUAS /UAS, are sub-optimal. (Nichols R.-0. , 2016).
There are clear vulnerabilities of the U.S. ADS to UAS:
- sUAS can be launched into action close to the target(s), less than 1 mile.
- sUAS exhibit a small radar signature, which hinders the detection phase.
- Reactive action dictates a quick response near the target. This is not always possible.
- sUAS/UAS are designed for slow, low flight. Low flying sUAS avoid radar identification.
- sUAS/UAS electric motors are quiet and have a limited thermal signature. This makes for difficult noise detection, especially if stealth technologies have been employed. (Nichols, Mumm, Lonstein, Ryan, & and Carter, 2018)
- sUAS /UAS operates in urban areas. The urban sphere presents additional problems and potential collateral damage. (Nichols R.-0. , 2016)
Conventional Countermeasures Against sUAS / UAS
Two families of conventional countermeasures are used to disrupt and destroy hostile UAS/sUAS systems. (Excluding FAA Regulations, locked in firmware GPS No-Fly Zones, Registration, FAA rules and the like)
Active Measures
Active measures are designed to incapacitate and/or directly destroy the sUAS/UAS threat. This method may employ Ground-to-Air Defense (GTA), missiles, acoustical guns, or a simple cyber rifle.
However, there are some defensive issues to be considered:
- GTA efficiency against sUAS reactive targets is reduced and is even less efficient in urban zones where civilians are at risk.
- Simultaneous attacks on multiple fronts (See: Team or SWARM formats, Table 15.2) make countermeasures very difficult to apply, and defense measures are mitigated,
- Commercial company Liteye has developed an Anti-UAV Defense System (AUDS), which can detect, track, and disrupt sUAS operations using pulsed, brief focused broadcasts of directional frequency jamming. Liteye has also developed a mobile version called M-AUDS (Liteye, 2018).
- China has developed a “5-sec” laser weapon to shoot down sUAS at low altitude (500 m) with a 10KW high-energy laser beam. Its range is 1.2 mi and handles sUAS at speeds up to 112 mph (Nichols R.-0. , 2016).
UAS countermeasure research is improving. Latency via AI has been greatly reduced. The goal is to increase the ability of Ground-to-Air (GTA) to react and improve their capabilities to a defined saturation limit. Team formation allows decoys and shields. SWARM formation is easier to detect; the arrival of a cloud of robot drones is hard to mask but tough to neutralize.
Passive Measures
Passive measures are designed to use physical protection around the target to protect it indirectly. Some methods used are decoys, shields, organized roadblocks, nets, jamming the aggressor’s sensors, or total or partial GPS signal cyber-spoofing. Passive countermeasures have some positive outcomes. Decoys can be effective if the ADS knows which sensors are employed for an sUAS Kamikaze attack and how they are used in the SAA subsystem. Communication jamming, which can disrupt the inter–drone communications required for the team or swarm formations, is effective against level 1 and 2 drones (Table 15.1), which require pilot interaction. Sensor Jamming is effective regardless of automation. It is especially effective when false GPS signals give false GPS information, cause camera/gimbal dislocation, and demagnetize the heading sensor (Nichols, Mumm, Lonstein, Ryan, & Carter, 2018).
The 2011 Iranian incident taught the U.S. ADS planners some lessons about passive spoofing waypoints and Loss of Signal (LOS) via GPS. LOS is an emergency condition that causes sUAS/UAS to execute programmed responses. One of those responses may be “return to waypoint .”Two types of spoofs can be executed. A complete spoof uses the friendly SAA to estimate course, groundspeed, and time to target, then force a LOS and change the final waypoint. A partial spoof reports false positions and changes waypoints for perceived emergency conditions during LOS. Both spoofs are difficult to detect and effective (Editor, 2012).
Conclusions
Unmanned Aircraft Systems represent some of the most advanced U.S. air assets. They are critical to the USA ADS and the defense of CBRN facilities. Based on the sheer diversity and number of potential cyber weapons that can be deployed at every stage of the UAS mission and the significant growth of UAS for defense purposes, the risk of their hostile use against U.S. ADS or CBRN facilities is steadily increasing. Coupled with the huge growth and increased sophistication of the UAS commercial technologies, the threat of hostile use cannot be minimized. (Nichols R. K. et al., 2019) (Nichols R. K. et al., Counter Unmanned Aircraft Systems Technologies, and Operations, 2020)
Discussion Topics
Consider the following real case scenario and theory about U.S. Navy Vessel Collisions in the Pacific:
Given Facts:
In 2017, a chain of incidents/collisions involved four U.S. Warships and one U.S. Submarine. On August 20, the guided-missile destroyer USS John S McCain collided with the 600-foot oil and chemical tanker Alnic MC at 0624 JST. Ten sailors died. On June 17, the destroyer USS Fitzgerald collided with the ACX 30,000-ton container ship at 1330 JST, leaving seven dead. Records show that the ACX turned sharply right at the time of the collision. The route of the destroyer is not shown on maps because commercial tracking data does not include military ships. Damage to the starboard side of the USS Fitzgerald indicates it would have been on a bearing of approximately 180 deg. (South). The captain of the Philippine-flagged container ship accused the Navy destroyer of failing to heed warning signs before the crash. On May 9, the guided-missile cruiser USS Lake Champlain collided with a South Korean fishing boat off the Korean Peninsula. There were no injuries. On January 31, the guided-missile cruiser USS Antietam ran aground, dumping more than 1000 gallons of oil into Tokyo Bay. On August 18, the ballistic- missile submarine USS Louisiana collided with the Navy Offshore Support Vessel in the Strait of Juan de Fuca. No injuries. (Office of CNO, 2020) (Lagrone, Chain of Incidents Involving U.S. Navy Warships in the Western Pacific Raise Readiness, Training Questions, 2017)
U.S. Navy Official Response
The U.S. Navy blamed its field leadership for not responding appropriately in all five incidents. Court marshals and relief from duty are the punishments of the day. The Navy blames funding, lack of readiness, and lack of training. Investigations and maintenance “hold” has been initiated. Reading between the lines, this response would imply that the Skipper/XO/COB and at least five watch sailors on each Naval vessel (roughly –forty to fifty personnel including bridge staff) were judged incompetent. Many U.S. Navy careers were finished. Further, this would also imply that all five vessels’ radar, emergency positioning alert systems, AIS, sonar, and long-range collision avoidance equipment must have been functioning perfectly, without a catastrophic failure or interference of any kind. (Office of CNO, 2020)
The Case for a Cyber Weapon
There appears to be valid evidence to support the theory that at least two of the U.S. Navy Warships above and the commercial vessels they struck were on the wrong end of a hostile cyber-weapon. (Lagrone, Cyber Probes to be Part of All Future Navy Mishap Investigations After USS John S. McCain Collision, 2017) They were receiving the wrong GPS-generated positional information (GPS Spoofing). Our research theorizes that UAS may have deployed the Cyber Weapon off a small, nearby vessel by an adversary. The subject cyber weapon may be an advanced modular entity that can spoof the GPS signals received by all vessels in its range. Vessels given misleading data will make incorrect decisions in terms of navigation and emergency responses – potentially leading to collisions and deaths. Contemplate and comment on the viability of the researcher’s cyber-weapon theory. Research and choose one specific cyber threat / or cyberweapon deployed against SCADA systems used by UAS. Discuss the chosen SCADA threat and how it exploits the vulnerabilities of the target system, the implications (impact) of the attack, and what defenses and countermeasures might be used to defend or mitigate the threat to the target.
Bibliography
A.A. Zavala, J. R. (2008). High-Altitude Platforms for Wireless Communications. West Sussex, UK: John Wiley.
Beaudoin, L. e. (2011). Potential Threats of UAS Swarms and the Countermeasures Need. ECIW.
Boutros, D. (2015, May 15). U.S. Navy War College. Retrieved from Operational Protection from Unmanned Aerial Systems: http://www.dtic.mil/dtic/tr/fulltext/u2/a621067.pdf
Chairman, U. (2012, March 23). Countering Air and Missile Threats, final coordination, J.P. 3-01. CJCS.
CIO Staff. (2006, November 1). Pa. Water-System Network Hacked. Retrieved from https://www.cio.com/: https://www.cio.com/article/262869/it-strategy-pa-water-system-network-hacked.html
Dark Reading Staff. (2013, April 22). Poison Ivy Trojan Just Won’t Die. Retrieved from https://www.darkreading.com/: https://www.darkreading.com/attacks-breaches/poison-ivy-trojan-just-won-t-die
DoD. (2018). Dictionary of Military Terms. Retrieved from JCS.Mil: http://www.jcs.mil/doctrine/dod_dictionary/
DoD. (2018). J.P. 3-0 Joint Operations. Washington, DC: DoD.
DRONESEC. (2021). Taliban UAS Threat Actor Special Report. Melbourne, AU: DRONESEC Notify (Dronsec.com).
Editor. (2012, April 22). R.T. Question More. Retrieved from Iran starts cloning of American spy drone: https://www.rt.com/news/iran-spy-drone-copy-667/
Gasser, M. (1988). Building a Secure Computer System. New York City: Van Nostrand Reinhold.
Hartman, K. a. (2013). The Vulnerability of UAVs to Cyber Attacks – An Approach to the Risk Assessment. 2013 5th International Conference on Cyber Conflict. Tallinn: NATO CCD COE Publications.
Heireng, H. S. (2015). The development and use of CBRN Scenarios for Emergency Preparedness Analysis. FOI Research Institute, Norwegian Armed Forces.
Higgins, K. J. (2015, January 23). Banking Trojans Disguised As ICS/SCADA Software Infecting Plants. Retrieved from https://www.eetimes.com/: https://www.eetimes.com/banking-trojans-disguised-as-ics-scada-software-infecting-plants/#
Horowitz, M. C. (2014). Droning On Explaining the Proliferation of Unmanned Aerial Vehicles. The University of Pennsylvania and Texas A&M Universities. The University of Pennsylvania and Texas A&M Universities.
iResearch. (2016, June 21). iResearch Forecasts China’s Civilian Small Drone Trend. Retrieved from iResearch: http://www.iresearchchina.com/content/details7_23815.html
Jaffe, G., & Erdbrink, T. (2011, December 5). Iran says it downed U.S. stealth drone; Pentagon acknowledges aircraft downing. The Washington Post.
Johnson, J. (2022, July 22). The number of Ransomware attacks per year 2016-2020. Retrieved from www.statista.com: www.statista.com
Lagrone, S. (2017, August 21). Chain of Incidents Involving U.S. Navy Warships in the Western Pacific Raise Readiness, Training Questions. Retrieved from news.usni.org/2017: https://news.usni.org/2017/08/21/chain-incidents-involving-u-s-navy-warships-western-pacific-raise-readinesstraining-questions
Lagrone, S. (2017, September 14). Cyber Probes to be Part of All Future Navy Mishap Investigations After USS John S. McCain Collision. Retrieved from https://news.usni.org: https://news.usni.org/2017/09/14/cyber-probes-part-future-navy-mishap-investigations-uss-john-s-mccain-collision
Liteye. (2018, August 25). AUDS. Retrieved from Liteye Corporation: http://liteye.com/products/counter-uas/auds/
Martinelli, S. A. (2017). Selected Issues of Cyber Security Practices in CBRNECy Critical Infrastructure. In M. &. Malizia, Cyber and Chemical, Biological, Radiological, Nuclear, Explosives Challenges (pp. 11-34). Rome: Springer International.
Miller, C. (2022, January 22). throwback Attack: BlackEnergy attacks the Ukrainian power grid. Retrieved from https://www.industrialcybersecuritypulse.com/: https://www.industrialcybersecuritypulse.com/throwback-attack-blackenergy-attacks-the-ukrainian-power-grid/
Myer, G. (2013, May-June). Danger Close Definition. Retrieved from U.S. Army Magazine: www.benning.army.mil/infantry/magazine/issues/2013/May-June/Myer.html
Nichols, R. K. (1996). Classical Cryptography Course, Volume I. Laguna Hills, CA: Aegean Park Press.
Nichols, R. K. (2008, September 5). Counterintelligence & Sensitive Compartmented Information Facility. (SCIF) Needs – Talking Points.
Nichols, R. K. (2017, October 4). Drone Wars: Threats, Vulnerabilities and Hostile Use of UAS. 2nd Annual Cyber Forum Event. Wichita, KS, USA: Wichita State University.
Nichols, R. K. (2019, March 14). Hardening U.S. Unmanned Systems Against Enemy Counter Measures. Invited Speaker / Panelist (13-14 March 2019) 7th Annual DoD UAV Countermeasures Summit (p. Hardening USA Unmanned Systems Against Enemy Countermeasures). Alexandria, VA: Proceedings of 7th Annual UAV Countermeasures DoD Summit.
Nichols, R. K. (2021). Chapter 14: Maritime Cybersecurity. In R. K. Nichols, & J. J. Ryan, Unmanned Vehicle Systems & Operations on Air, Sea, Land (pp. 330-356). Manhattan, KS: New Prairie Press #35.
Nichols, R. K. (2022). Chapter 18: Cybersecurity Counter Unmanned Aircraft Systems (C-UAS) and Artificial Intelligence. In D. M. R. K. Barnhart, Introduction to Unmanned Aircraft Systems, 3rd Edition (pp. 399-440). Boca Raton, FL: CRC.
Nichols, R. K., Mumm, H. C., Lonstein, W. D., Ryan, J. J., & and Carter, C. (2018). Unmanned Aircraft Systems (UAS) in the Cyber Domain: Protecting USA’s Advanced Air Assets. Manhattan, KS: New Prairie Press (NPP) eBooks. 21.
Nichols, R. K., Ryan, J. J., Mumm, H., Lonstein, W., Carter, C., & Hood, J. P. (2019). Unmanned Aircraft Systems in the Cyber Domain: Protecting USA’s Advanced Air Assets, 2nd ed. Manhattan, KS: https://www.newprairiepress.org/ebooks/27.
Nichols, R. K., Ryan, J., Mumm, H., Lonstein, W., Carter, C., & Hood, J. (2020). Counter Unmanned Aircraft Systems Technologies and Operations. Manhattan, KS: Pressbooks: https://kstatelibraries.pressbooks.pub/counterunmannedaircraft/.
Nichols, R. K., Ryan, J., Mumm, H., Lonstein, W., Carter, C., & Hood, J. P. (2018). Unmanned Aircraft Systems (UAS) in Cyber Domain: Protecting USA’s Advanced Aircraft Assets. Manhattan, KS: New Prairie Press (NPP) Ebooks. Retrieved from https://newprairiepress.org/ebooks/21
Nichols, R. (Nov 28-30, 2006). Cyber Terrorism, Critical Infrastructure, & SCADA Presentation. In R. Nichols (Ed.), Defense Threat Reduction Agency Conference. Shirlington VA: Utica College, Utica NY.
Nichols, R. R. (2020). Counter Unmanned Aircraft Systems Technologies and Operations. Manhattan: New Prairie Press #31.
Nichols, R.-0. (2016, March 29). NCIE UAS SAA Final Rev 4. 2016 INFOWARCON conference presentation April 4-7, Nichols, R.K. et al. (3-29-2016) Presentation to INFOWARCON April 4-7 on NCIE UAS SAA Final Rev 4, presented to 2016 INFOWARCON conference, Memphis TN. Available as PPTx presentation download from the author or in CANVAS. Memphis, TN, USA: INFOWARCON16.
Office of CNO, U. N. (2020, May 14). Collision Reports for USS Fitzgerald and USS John S McCain 2017 Incidents in Pacific. Retrieved from https://s3.amazonaws.com/CHINFO: https://s3.amazonaws.com/CHINFO/USS+Fitzgerald+and+USS+John+S+McCain+Collision+Reports.pdf
Paske, E. L. (2015). Cybersecurity of Industrial Control Systems. Global Conference on Cyberspace.
Peerenboom, F. a. (2001). CIS Shared Threats. Retrieved from http://www.ari.vt.edu/: http://www.ari.vt.edu/workshop/Whitfield-presentation.ppt
Poulsen, K. (2003, August 20). Slammer Worm Crashed Ohio Nuke Plant Network. Retrieved from https://rense.com/: https://rense.com/general40/worm.htm
Randall K. Nichols and Lekkas, P. C. (2002). Wireless Security: Threats, Models, Solutions. New York City, NY: McGraw Hill.
Randall K. Nichols, D. (2018). Chapter 20 Acoustic CM & IFF Libraries V SWARMS Rev 1 05142019. In R. K. Nichols, H. C. Mumm, W. D. Lonstein, & J. S. Hood, Unmanned Aircraft Systems (UAS) in the Cyber Domain: Protecting USA’s Advanced Air Assets, 2nd ed. Manhattan, KS: NPP Press.
Randall K. Nichols, J. J. (2018). Unmanned Aircraft Systems (UAS) in the Cyber Domain: Protecting USA’s Advanced Air Assets. Manhattan, KS: New Prairie Press.
Randall K. Nichols, J. R. (2000). Defending Your Digital Assets Against Hackers, Crackers, Spies, and Thieves. New York City, NY: McGraw Hill.
Richard K. Barnhart, S. B. (2012). Introduction to Unmanned Aircraft Systems. Boca Raton, FL: CRC Press.
Schneier on Security. (2008, 01). Hacking Polish Trams. Retrieved from https://www.schneier.com/: https://www.schneier.com/blog/archives/2008/01/hacking_the_pol.html
Schneier, B. (2015). Vizsec 2015. IEEE 12th Symposium on Visualization for Cyber Security. IEEE.
Staff. (2014, April 28). Infosecurity Europe 2014 Case Study: Shamoon, a two-stage targeted attack. Retrieved from https://www.slideshare.net/: https://www.slideshare.net/Seculert/case-study-shamoon-a-two-stage-targeted-attack
Staff, I. (2013). IEEE Communications Surveys & Tutorials: Introduction to Industrial Control Networks. IEEE.
Technopedia. (2019, May 28). Technopedia. Retrieved from Artificial Intelligence: https://www.techopedia.com/definition/190/artificial-intelligence-ai
Wilson, C. (2014). Cyberterrorism: Understanding, Assessment, and Response. Wales: Swansea University.
Yan. (2017, December 23). China’s commercial drone market to top 9 bln USD by 2020. Retrieved from Xinhuanet: http://www.xinhuanet.com/english/2017-12/23/c_136847826.htm
Zwijnwenburg, W. (2014, October 8). ZwijnwenbDrone-tocracy? Mapping the Proliferation of Unmanned Systems. Retrieved from Sustainable Security.org.
Endnotes
[1] CRITICAL INFRASTRUCTURE (CI) is the production, storage, logistics of CBRN materials and devices, and reconnaissance and disaster response. CBRNE Infrastructure is CI that produces, handles, transports recycles, decontaminates, or otherwise incorporates CBRNE agents. (Paske, 2015) (Martinelli, 2017)
[2] None of the CIS cyber attacks have been deployed via drone. But that is the whole point they can be, and it would be more effective to do so!
[3] Sources described it as a worm or malware. Nothing could be further from the truth. It was a joint Israeli – USA operation creating a powerful Cyber Weapon involving multiple attack surfaces, counter defenses, zero-day exploits, false flags, etc. The development was both sensitive and compartmentalized and carried out in several locations. The only two drawbacks were it was discovered and then re-engineered to hit additional targets.
[4] Artificial intelligence (AI) is an area of computer science that emphasizes the creation of intelligent machines that work and react like humans. Some of the activities computers with artificial intelligence are designed for include:
Speech recognition, learning, planning, problem-solving, and decision-making. Research associated with artificial intelligence is highly technical and specialized. The core problems of artificial intelligence include programming computers for certain traits such as knowledge, reasoning, problem-solving, perception, learning, planning, and
the ability to manipulate and move objects. (Technopedia, 2019)
[4] Dr. Julie J.C.H. Ryan is a superstar in the INFOSEC community. Her research is prolific. See https://www2.seas.gwu.edu/~jjchryan/research.html. So is Dr. Dan J. Ryan. See: https://security.iri.isu.edu/ViewPage.aspx?id=926and rebuild=true
[5] Some Level 3 UASs have capabilities that fall into the Level 4 category. Datasheets do not necessarily follow neatly into the author’s taxonomy.
[6] Adapted for UAS deployment from Table 1, Chapter 2, page 21 (Martinelli, 2017)
[7] Consider HAPP applications using High Altitude Drones. (A.A. Zavala, 2008)
[8] FIRES definition (U.S. DoD – J.P. 3-0) is the use of weapon systems to create a specific lethal or nonlethal effect on a target. (DoD, Dictionary of Military Terms, 2018)
[9] ADS is emphasized because CBRN facilities are low-hanging fruit if these defenses fail.
[10] Danger Close Definition www.benning.army.mil/infantry/magazine/issues/2013/May-June/Myer.html November 14, 2013 – 1) danger close is included in the “method-of-engagement” line of a call-for-fire request to indicate that friendly forces are close to the target. … Danger close is a term that is exclusive from risk estimate distance (RED) although the RED for 0.1 percent P.I. is used to define danger close for aircraft delivery. Pi = Probability of incapacitation. 2) Definition of “danger close” (U.S. DoD) In close air support, artillery, mortar, and naval gunfire support fires, it is the term included in the method of engagement segment of a call for the fire which indicates that friendly forces are within close proximity of the target.

