6 Machines Hacking Machines – Turing’s Legacy [Carter]
PREVIEW
This chapter provides an overview of how Alan Turing’s legacy has contributed to our current and future technological development. He is often credited as being one of the founders of Artificial intelligence (AI) and Computer Science. Turing is best known as being part of the team that cracked ENGIMA in World War II. His early research led to the development of theoretical computer science with the creation of the “Turing Machine.” This 1930’s research by Turing established the roots of our modern-day computers and software. Theoretical computer science assisted with building of the Bombe, the machine that would break the code of the German WWII ENGIMA encryption machine. Alan Turing continued researching and publishing throughout his life. In 1950, he authored an influential paper titled “Computing Machinery and Intelligence.”. This resulted in the “Turing Test,” an applied theory to measure machine intelligence and the ability to mimic human behavior. The “Turing Test” is still in use and applied by AI developers as AI technology continues to advance and grow.
STUDENT OBJECTIVES
After reading this chapter, students should be able to do the following:
- Explain how Alan Turing’s research of mathematics and algorithms led to the creation of different computer systems and a basis for developing software.
- Describe the significant impact on the field of encryption and encryption techniques used today when the Bombe mechanical device was used to crack the ENGIMA machine in World War II.
- Explain how the “Turing Test” is relevant today.
- Discuss how Alan Turing’s research and creations laid the foundation for computer science and artificial intelligence.
INTRODUCTION
As one of the founders of computer science and the father of AI Alan Turing’s legacy is endless. The “Turing Machine” laid the foundation for the development of modern computer architecture and the field of theoretical computer science. The development of theoretical computer science, the study of algorithms, computational complexity, and formal models of computation. Theoretical computer science gives an understanding of the fundamental limits of computation and to develop a mathematical theory of algorithms and computational processes. The cracking of the Enigma code during World War II had a significant impact on the field of encryption and laid the foundation for many of the encryption techniques used today. The process to break the German encryption required mechanical devices, such as the Bombe machine, to perform and highlight calculations. Turing had advanced cryptanalysis using statistical analysis. The protection key management was shown to be essential for future wars. The theory of the “Turing Test” went a step further to measure the machine’s intelligence and skill. This gave the foundation for testing and creating artificial intelligence.
THE TURING MACHINE
During Alan Turing’s two years (1936-38) at Princeton University, he cultivated the concept of theoretical computer science. Theoretical computer science is a field of computer science that studies the limits of computation and the foundations of computer science. It deals with abstract concepts and mathematical models that define the capabilities and limitations of computers and algorithms. Theoretical computer science encompasses a wide range of topics, including algorithms and computational complexity, automata theory, formal languages and grammars, and the study of algorithms for solving mathematical problems. It also includes the study of algorithms for solving problems in other fields, such as cryptography, game theory, and optimization. The goal of theoretical computer science is to understand the fundamental limits of computation and to develop a mathematical theory of algorithms and computational processes. This theory provides a basis for the design and analysis of algorithms and the development of new computing technologies.
The Turing machine is a theoretical machine proposed by Alan Turing in 1936. It is considered a mathematical model of computation and a cornerstone of computer science. The Turing machine is a theoretical machine that consists of an infinite tape divided into cells, each cell containing a symbol. It also has a read/write head that can read the symbol in the current cell and write a new symbol in that cell. The Turing machine operates in a series of steps, which are determined by a set of rules called the transition function. The transition function takes the current state of the machine, the symbol read by the read/write head, and determines the next state of the machine, the symbol to be written in the current cell, and the direction the read/write head should move.
The Turing machine can be thought of as a simple computer that can perform any calculation that is computationally feasible, given an appropriate set of rules and input. This is the basis of the Church-Turing thesis, which states that any computation that can be performed by any machine can also be performed by a Turing machine. Alan Turing studied under Alonzo Church in 1936 at Princeton University. Prior to meeting Turing, Church conducted research on a class of functions that coincide with the intuitively computable functions that can be evaluated by algorithms and computer programs (Deutsch & Marshall , 2022). Church also provided first example of a particular significant function that is not computable, meaning a certain problem of elementary number theory is unsolvable: there is no way it could be solved by algorithmic means (Deutsch & Marshall , 2022). The Turing Machine demonstrates the framework for the design and analysis of algorithms and computational processes, laying the foundation for computer science.
The concept of the Turing machine can be applied to modern computing systems, and in this context, it is possible for machines to hack other machines. This can happen through a variety of means, such as exploiting vulnerabilities in software or hardware, using malware or other malicious software, or using social engineering techniques to trick a machine into revealing its secrets. In the field of cybersecurity, modern computers and networks can be vulnerable to hacking, and the development of advanced intrusion detection systems, which can analyze network traffic to identify and block malicious activities is a response to this problem. These systems can also learn from past attacks to improve their ability to detect and prevent future ones. Additionally, machine learning can be used to detect and analyze anomalies in the network to identify potential threats and can also be used to develop machine-learning-based malware detection systems. The concept of the Turing machine proves the possibility for machines to hack other machines.
ENIGMA MACHINE V. BOMBE MACHINE
As Britain faces World War II (WWII), Alan Turing’s research is vital to assist in changing the course of WWII. The Turing Machine as a foundation for computer science, the first machine hacking machine event (outside of theory) occurred between the German Army Enigma Machine and the Turing-Welchman Bombe Machine leading to the end of WWII. There were several factors that played into the success of machine hacking machine.
In 1938, British Secret Intelligence Service (MI6) set up the Government Code & Cypher School (GC&CS), a top-secret program at Bletchley Park. The converted private estate in Milton Keynes was home to thousands of WWII codebreakers, an elite team of mathematicians, linguists, classicists, and intelligence officers. The recruits were exceptional young men and women recruited from Britain’s elite universities (Giovanni, 2021). Others were recruited by GC&CS through the newspaper, Daily Telegraph. The paper hosted a contest of solving the cryptic crossword with-in twelve minutes (Bearne, 2018). The GC&CS was organized by collection of Huts. Each Hut was contained with their own function and purpose, not to distract from one another. Alan Turing oversaw Hut 8, Naval Ultra Enigma Machine Ciphers. Gordon Welchman led Hut 6, Army, and Airforce Ultra Enigma Machine Ciphers. Hut 6 additional was the Machine Room, plus the Decoding Room and Registration Room (Giovanni, 2021). Bletchley Park’s sole purpose was to crack the German Enigma Machine to save lives and stop Hitler’s movement.
Figure 6-1 German Enigma Machine

Source: (Oleksiak, 2014)
The German Enigma Cipher Machine was used to send encrypted messages during WWII. For each letter that was tapped in, another letter would come out so messages would be received in code (BBC News, 2011). In 1931, Hans-Thilo Schmidt, was an employee of the German Cipher Office. Tempted by greed, Schmidt sells the instruction manual and key setting instructions to French Intelligence. With a picture and related documents of the German Enigma Cipher Machine, the French notice a unique characteristic. The Enigma Cipher Machine was widely available to others, the German version had a front plug board. Schmidt, French code name Asché, provided additional German Enigma Machine information to the French for several years to follow.
Figure 6-2 The Enigma Plugboard
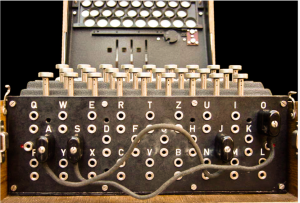
Source: (Oleksiak, 2014)
In 1932, France shared the German Enigma Machine information with Poland. Immediately Polish mathematician /cryptologist Marian Rejewski began his work to break the Enigma. In 1939, the French hosted a meeting with Britain and Poland to discuss intelligence cooperation, suggesting that all three countries working together would increase the probability of breaking the Enigma. An agreement was reached on sharing communications traffic intelligence, any problems with intelligence and any breakthroughs with the Enigma. A document is drawn assigning each country a letter, X for France, Y for London, and Z for Poland.
Figure 6-3 Agreement Between France, Great Britain, and Poland

Source: (Turning, 2016)
The French suspected Poland was not sharing their breakthroughs, their suspicion was correct. The Polish mathematician /cryptologist Marian Rejewski began to formulate equations for the Enigma rotor, leading a break into the Enigma machine since the handoff of intelligence in 1932. The British and French codebreakers did not have much success in reading the German Enigma messages. Polish authorities did not reveal their work to the British and French until July 1939 when the advance of war was getting serious in Poland (BBC News, 2011). The three countries met in Warsaw to review Poland’s discoveries in breaking the German Enigma Machine. Poland’s hand was forced into calling the meeting, the small collective of Polish codebreakers became overwhelmed by the German Army changing the Enigma settings each day and adding two new rotors into rotation for their Enigma Machines. The Polish explained their mockup of the German Enigma Machine, which became obsolete with the recent changes from Germany. The original German Enigma Machine had 3 rotors; rotors assisted with the increasing the difficulty of the encryption. Three rotors produced 6 permutations. Adding two additional rotors into rotation resulted in 60 permutations, strengthening the German encryption beyond the number of codebreakers in Poland. German commanders had the ability to communicated with field units encoded by messages encoded on Enigma machines and sent by wireless using Morse code (The National Museum of Computing, n.d.). Each German high command, about 24 in all, had its own wireless network and daily key settings (The National Museum of Computing, n.d.). Additionally, Poland shared with the French and British Intelligence other codebreaking efforts to entice their allies into assisting with solving their engineering problem.
Figure 6-4 WWII Polish Mathematician Marian Rejewski

Source: (Oleksiak, 2014)
The Polish intelligence gave enough information for Turing to build a new Bombe. His approach was based on the use of ‘cribs’ (comparing patterns of the encrypted message and a known portion of plain text) to break the key (The National Museum of Computing, n.d.). British listing posts, Y Stations, copied the German messages and sent them to Bletchley Park to be run through the Bombe. The Bombe was working but the processing speed was inconstant and could not provide real-time data. In 1940, Gordon Welchman added a diagonal board to Turing’s Bombe, (which dramatically reduced the number of invalid stops – false positives) increased throughput to the point that the Bombe became a major success (The National Museum of Computing, n.d.). The addition of the digital board led Bletchley Park to break the first German Enigma Machine code. Coined the Turing-Welchman Bombe machine, the digital board became a permanent part of the build. By 1941, the codebreakers of Bletchley Park were understanding more of the code, a consistent combination of letters could be traced back to German military units. This was groundbreaking, now the codebreakers were able to understand the movement of the German Military, switching the allies’ militaries to offense verses defense.
Figure 6-5 Bletchley Park Codebreakers

Source: (BBC News, 2020)
Figure 6-6 Polish Enigma Machine

Source: (BBC News, 2011)
The United States partnered with the United Kingdom codebreakers at Bletchley Park with the approval of Winston Churchill. The top secret “Sinkov Mission” team was led by former Brooklyn math teacher U.S. Army Capitan Abraham Sinkov, expert in Italian cipher systems (Spyscape, 2023). Other team members were U.S. cryptanalyst Leo Rosen, the Japanese cipher recreator (codename Purple); Navy Lieutenant Prescott Currier specialized in radio intelligence collection involving the Japanese Navy; Navy Rear Admiral Robert H. Weeks, experienced in communication security posts in Washington D.C. (Spyscape, 2023).
Figure 6-7 The Purple Machine

Source: (Spyscape, 2023)
Since the U.S. was not technically at war, the Sinkov team had limited access to Bletchley Park during their visit. However, Leo Rosen worked closely with the Bletchley and engineers and noted improvements for the Turing-Welchman Bombe machine. Rosen would later introduce electrical switches into the design after returning to the U.S. (Spyscape, 2023). The U.S. and U.K. intelligence bond would strengthen after the bombing of Pearl Harbor.
It is estimated 159 quintillion different German encryption permutations (The Parallax View, 2018) were read by the codebreakers of Bletchley Park (75% women), with some support of 100,000 U.S. Navy WAVES (Women Accepted for Volunteer Emergency Service) codebreakers. On May 8, 1945, the Germany surrendered, Churchill took part in the U.K. celebrations and warned that war was not over, Japan needed to be defeated. After the U.S. deployment of the Atomic Bomb, Japan surrendered on August 15th, 1945.
Figure 6-8 In Dayton Ohio, U.S. Navy women worked in three shifts a day constructing the many gears and gadgets that make up the Bombes

Source: (Wei-Haas, 2017)
ENIGMA: LESSONS LEARNED
The lessons learned of the WWII codebreakers can be applied to modern day operational security. German enigma operator’s mistakes played into the hands of the codebreakers at Bletchley Park. Human mistakes were made of mundane routine combined with difficult bureaucratic processes. The enigma operators did not understand why their role was important in the bigger picture of the war. Potentially if the operators understood the mistakes in their job posed vulnerabilities and threats for the entire German military, the operators would be aware they are mission critical. The same principle can be applied to the military leaders, respecting and applying operator feedback regarding routine.
The U.K. used the combination of intelligence and military to break codes, physically surround targets and use Allies. Once a German code was deciphered there was no further protection leaving the German military’s plans in plain view. Additionally with the joining force of intelligence and military, the U.K. and allies were able to attack German forces repeatedly without relief. Applying the lessons learned to modern day, clearly multiple layers of encryption with strong security architecture can prevent an attacker from getting into the “crown jewels.”
Overall, the ignoring of vulnerabilities from insider threat to not evaluating the strength of security in place, can be detrimental. The lessons learned from WWII German ENIGMA contributed to cybersecurity theories of modern day.
THE TURING TEST
In 1950 Alan Turing published, “Computing Machinery and Intelligence” in the quarterly philosophy and analytic tradition journal, Mind. The paper introduced the concept of the “The Turing Test.” The phrase “The Turing Test” is most effectively used to refer to as a way of dealing with the question whether machines can think (Stanford University, 2003). The Turing Test is considered the method of inquiry in artificial intelligence (St. George & Gillis, 2023). Turing proposed the test as a game to gauge if a computer is mimicking human intelligence under specific conditions. The test has one human judge that has a test conversation with other unseen players. The judge evaluates the players responses, it the judge is unable to detect a computer response, then the Turing Test is passed. Failure of the Turing Test would occur if the judge were able to pick out a response from a computer (University of Manchester Department of Science and Engineering, 2022). There are two groups of theory regarding the Turing Test, one believes it is obsolete another believes it is relevant.
Figure 6-9 Diagram of the Turing Test
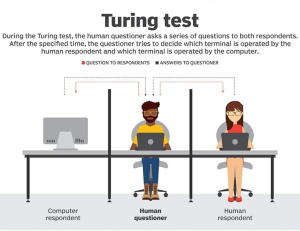
Source: (St. George & Gillis, 2023)
The obsolete proponents of the Turing Test use bot ELIZA as an example. The ELIZA bot used psychotherapist tactics with the human. Some believe this passed the Turing Test other believe it was using trickery and played on the naïve humans. In 1991, the Loebner Prize was created, named after its founder and philanthropist Hugh Loebner, is an annual world-wide contest to evaluate the state-of-the-art in artificial intelligence (AI) (University of Exeter, 2023). The Loebner Prize is supported by several universities and organizations such as the Cambridge Center for Behavioral Studies and Bletchley Park. The Loebner Prize has recognized winning contestant bots as passing Turing Test. By recognizing the winners of this contest, a portion of the population believes the Turing Test is obsolete. Since the last Loebner Prize contest in 2019, two implementations, Google’s AI LaMDA and ChatGPT have been recognized (albeit controversially) as having passed the Turing Test. (Mark,2023) (Orf, 2023) The replacement is the Marcus Test, a measure of the computer’s comprehension of a television show. Also, an additional replacement to the Turing Test is the Lovelace Test 2.0. The Lovelace Test 2.0 measures the intelligence of the computer’s ability to create an art artifact. Mustafa Suleyman, who co-founded the AI Lab DeepMind which was acquired by Google, argues that the ChatGPT’s large language model approach allows it to pass the Turing Test by mimicking a human yet it doesn’t indicate any understanding about what the system can actually understand. He proposes a more modern Turing test based on entrepreneurship, asking the A.I. to turn $100,000 in seed money into $1million by devising an original product idea. (Shin, 2023)
Figure 6-10 Cartoon the Turing Test

Source: (Cornell University, 2023)
The other side of the population believes the Turing Test is relevant and has not been achieved as of today. This population views the Turing Test as a concept testing machines response to human speech. To have a conversation as humans do this would prove artificial intelligence. The argument is that Artificial Intelligence does not exist today. Instead, there are machines that have a response to stimulus, kicking off the process of the machine to perform an action. We know that computers can follow an algorithm to accomplish a task. However, this does not prove the machine is thinking. The summer of 2022, Blake Lemoin, a Google engineer claimed Google had created a sentient machine. Lemoin believed the Language Model for Dialogue Applications (LaMDA), system he has been working on as sentient, with a perception of, and ability to express, thoughts and feelings that was equivalent to a human child (Reed, 2022). Google and many leading scientists were quick to dismiss Lemoine’s views as misguided, saying LaMDA is simply a complex algorithm designed to generate convincing human language (Reed, 2022). Algorithms and ancillary items are too primitive to create human intelligence (Roitblat, 2021).
Could it be that we do not have artificial intelligence that can pass a Turing Test? The University Manchester Professor Steve Furber states we have yet to see any convincing demonstration of a machine that can pass his test (Furber, 2016). Professor Furber, believes we need to return to the natural intelligence, the human brain to solve for Turing’s concept of “thinking” (Furber, 2016). Professor Furber is currently building a computer to support real-time models of the brain subsystems (Christopherson, 2022). Professor Furber masterpiece, ‘Spiking Neural Network Architecture’ known as SpiNNaker is the world’s largest neuromorphic supercomputer designed and built to work in the same way a human brain does has been recently fitted with its landmark one-millionth processor core. With a price tag of £15million, 20 years in conception and over 10 years in construction starting 2006 (University of Manchester Department of Science and Engineering, 2022). Project funding began with Engineering and the Physical Sciences Research Council (EPSRC), currently funding is coming from the European Human Brain Project.
Figure 6-11 SpiNNaker

Source: (University of Manchester Department of Science and Engineering, 2022)
SpiNNaker is unique because, unlike traditional computers, it doesn’t communicate by sending large amounts of information from point A to B via a standard network. Instead, it mimics the massively parallel communication architecture of the brain, sending billions of small amounts of information simultaneously to thousands of different destinations (University of Manchester Department of Science and Engineering, 2022). Professor Furber’s ultimate goal for SpiNNaker’s is understanding the information processing principles at work in natural intelligence. SpiNNaker could satisfy Turing’s concept of “Thinking” per Professor Furber theory.
The Turing Test does not recognize functional Intelligence in a computer. The revelation of simulated intelligence by machine can be found using the Turing Test. The Turing Test can be said to reveal judgement by humans who come to conclusions using feelings, intuition, and imperfect information. The Turing Test will continue to be debated among scientists, programmers, and philosophers.
Figure 6-12 Alan Mathison Turing

Source: (Mullen, 2014)
CONCLUSIONS
Alan Turing research was influential during his time, modern day, and in the future. His early research of mathematics and algorithms led to the creation and of different computer systems and a basis for developing software. Turing remains popular in our minds for co-creating the Turing-Welchman Bombe machine leading to the breaking of German ENGIMA encryption machines resulting in an early end of WW II. Turing’s life contributions have led to the development of theoretical computer science, the study of algorithms, computational complexity, and formal models of computation. Turing was boundless with creative mathematical concepts and theories. Alan Turing remains relevant today and for the development of artificial intelligence and technology for the future.
REFERENCES
BBC News. (2011, July 14). Bletchley Park Remembers Polish Code Breakers. Retrieved from BBC News: https://www.bbc.com/news/uk-england-beds-bucks-herts-14141406
BBC News. (2020, October 20). BBC News. Retrieved from Bletchley Park’s contribution to WW2 : https://www.bbc.com/news/uk-54604895
Bearne, S. (2018, July 24). Meet the Female Codebreakers of Bletchley Park. Retrieved from The Guardian: https://www.theguardian.com/careers/2018/jul/24/meet-the-female-codebreakers-of-bletchley-park
Christopherson, C. (2022, January 31). ARM Community: SpiNNaker: Next-level thinking. Retrieved from ARM Community: https://community.arm.com/arm-research/b/articles/posts/spinnaker-next-level-thinking
Cornell University. (2023). Numb3rs 517: First Law. Retrieved from Cornell University Department of Math: http://pi.math.cornell.edu/~numb3rs/spulido/Numb3rs_season5/Numb3rs_517.html
Deutsch, H., & Marshall , O. (2022, March 21). Alonzo Church. Retrieved from The Stanford Encyclopedia of Philosophy: https://plato.stanford.edu/archives/sum2022/entries/church/
Furber, S. (2016). The SpiNNaker project. Unconventional computation and natural computation : 15th International Conference, UCNC 2016, Manchester, UK, July 11-15, 2016, Proceedings (p. 9726). Manchester: Spring Nature.
Giovanni, J. d. (2021, July 5). How World War II Code-Breakers Created the Modern Digital World . Retrieved from Foreign Policy: https://foreignpolicy.com/2021/07/05/geniuses-at-war-david-a-price-book-review-bletchley-park-alan-turing-computer-technology-world-war-ii-hitler-nazis-london-blitz-battle-of-britain-luftwaffe-enigma-secret-code/
Mark. (2023, May 9). ChatGPT Passes Turing Test: A Turning Point for Language Models. Retrieved July 12, 2023, from mlylearning.com: https://www.mlyearning.org/chatgpt-passes-turing-test/
Mullen, J. (2014, August 19). CNN: Alan Turing, code-breaker castrated for homosexuality, receives royal pardon. Retrieved from CNN: https://www.cnn.com/2013/12/24/world/europe/alan-turing-royal-pardon/index.html
Oleksiak, W. (2014, July 3). The Hacker Who Saved Thirty Million Lives. Retrieved from CluturePL: https://culture.pl/en/article/the-hacker-who-saved-thirty-million-lives
Orf, D. (2023, March 16). The Turing Test for AI Is Far Beyond Obsolete. Retrieved July 12, 2023, from Popular Mechanics: https://www.popularmechanics.com/technology/robots/a43328241/turing-test-for-artificial-intelligence-is-obsolete/
Reed, B. (2022, July 23). The Guardian:Technology:Google fires software engineer who claims AI chatbot is sentient. Retrieved from The Guardian Technology : https://www.theguardian.com/technology/2022/jul/23/google-fires-software-engineer-who-claims-ai-chatbot-is-sentient
Roitblat, H. L. (2021, October 4). AI Is No Match for the Quirks of Human Intelligence. Retrieved from The MIT Press Reader: https://thereader.mitpress.mit.edu/ai-insight-problems-quirks-human-intelligence/
Shin, R. (2023, June 20). The Turing test for measuring A.I. intelligence is outdated because of ChatGPT’s wizardry, and a new test would be better, DeepMind cofounder says. Retrieved July 12, 2023, from Fortune: https://fortune.com/2023/06/20/turing-test-proposed-update-ai-chatgpt-deepmind-cofounder/
Spyscape. (2023). Bletchley Park: The Top Secret Mission to Crack the Enigma Code. Retrieved from Spyscape: https://spyscape.com/article/bletchley-park-the-top-secret-us-mission-to-crack-the-enigma-code
St. George, B., & Gillis, A. S. (2023, April). What is the Turning Test? Retrieved from Techtarget: https://www.techtarget.com/searchenterpriseai/definition/Turing-test
Stanford University. (2003, April 9). Stanford Encyclopedia of Philosophy. Retrieved from stanford.edu: https://plato.stanford.edu/entries/turing-test/
The National Museum of Computing. (n.d.). The Turing Welshman Bombe. Retrieved from The National Museum of Computing: https://www.tnmoc.org/bombe
The Parallax View. (2018, August 1). Bletchley Park’s WWII Lessons for Today’s Hackers. Retrieved from The Parallax: https://www.the-parallax.com/bletchley-park-wwii-lessons-hackers/
Turning, D. (2016, February 1). Alan Turing Decoded: An Evening with Sir Dermot Turing (ENGIMA). (I. S. Museum, Interviewer)
University of Exeter. (2023). LOEBNER PRIZE. Retrieved from University of Exeter : https://loebner.exeter.ac.uk
University of Manchester Department of Science and Engineering. (2022, June 23). Passing as a Human – What is the Turning Test? Retrieved from University of Manchester Department of Science and Engineering: https://www.mub.eps.manchester.ac.uk/science-engineering/2022/06/23/passing-as-human-what-is-the-turing-test/#:~:text=Back%20to%20the%20future&text=Interestingly%2C%20Turing%20predicted%20that%20by,successful%2C%20and%20mostly%20through%20trickery.
Wei-Haas, M. (2017, October 5). How the American Women Codebreakers of WWII Helped Win the War. Retrieved from Smithsonian Magazine: https://www.smithsonianmag.com/history/how-women-codebreakers-wwii-helped-win-war-180965058/
Williams, A. (2023, June 22). ASK HACKADAY: THE TURING TEST IS DEAD: LONG LIVE THE TURING TEST! Retrieved July 12, 2023, from Hackaday: https://hackaday.com/2023/06/22/ask-hackaday-the-turing-test-is-dead-long-live-the-turing-test/

