14 The Rise of Cyber Threats in Space – Future of Cyberwar [Farcot]
HISTORICAL OVERVIEW:
Cold war
At the end of the second world war, the rapid advancement of both jet and rocket technologies was overshadowed by the introduction of nuclear weaponry. The bombings of Hiroshima and Nagasaki demonstrated the raw destructive power of atomic bombs to the rest of the world. Shortly after, the Soviet Union conducted its own first successful nuclear tests. This, if anything, was the primary driver for the competition between the US and USSR that would soon become the Cold War. The race for military superiority eventually spilled beyond Earth’s atmosphere. Beginning with the Sputnik launch of 1957, a great fear of nuclear weapons being launched from orbit was now taking shape amongst both the public and governments alike. Although these types of weapons were never actually launched into space, surveillance soon became the real threat. Thus, both the United States and the Soviet Union began developing the first satellite killers. These anti-satellite weapons, often referred to as ASATs, were developed as early as May of 1958 during the Bold Orion program (Lethbridge, 1996). This saw the testing of the ALBM-199B, a ballistic missile launched from a B-47. In the decade that followed, other forms of ASAT weapons soon took shape. The USSR even went so far as to develop nuclear-tipped interceptors several years later (Grego, 2012). Eventually, international agreements were reached such as the Partial Test Ban Treaty of 1963. While these types of bans altered both the US and USSR’s approach to ASAT weapon development, they never fully put a stop to them. Within the first year of the so-called Space Race, threats against man-made satellites were already taking shape in the form of early ASAT systems. Many of these systems were designed by the Roscosmos group. Today, Roscosmos acts as the de facto continuation of the legacy soviet program and acts as the country’s federal space agency, functionally the same as NASA’s role in the US.
Figure 14-1: NASA’s Budget Since 1960
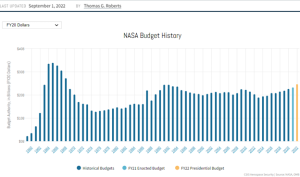
Source: (Roberts & Harrison, 2022)
CHINESE ENTRY
Despite the end of the first Cold War between the US and USSR, the situation in space has only become more complicated. This is largely due to the entry of new factions in space. The most significant example, at least on the international level, is China, which began its own space program shortly after the US and USSR. However, the program remained small due to limited funding for the majority of the Cold War. In 1970, the first Chinese satellite was successfully launched into orbit, making it the fifth nation to do so (Futron Corporation, 2003). Towards the end of the 20th century, there was a major upscale in Chinese space activity due to a rapid increase in funding. This activity has only intensified into the 21st century and, while the US still dominates in overall yearly spending on its space programs, China has been steadily closing the gap ever since the ~2000 spending boom. Additionally, the country has followed a similar path to the US and Russia with ASAT development. On January 11th, 2007, China’s first successful ASAT test using a ballistic missile was conducted, making it the third country to do so since the US and USSR in the 1980s (Kan, 2007). It is clear now that China has matured as the next national player of a newly revived space race.
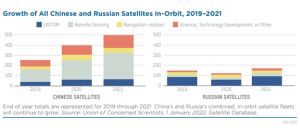
Figure 14-2: Satellite Capabilities by Country – 1966 to 2020
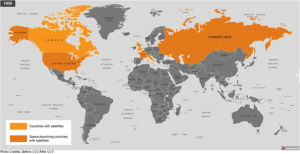
Source: (Union of Concerned Scientists, 2022)
Figure 14-3: Satellite Capabilities by Country – 1966 to 2020
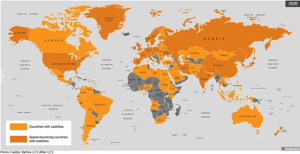
Source: (Union of Concerned Scientists, 2022)
CORPORATIZATION
Despite the entry of new international competitors, the US government has responded with little increases in spending on its own space programs. NASA was eventually forced to end the Space Shuttle program in 2011. While the US still maintained a presence on the International Space Station, it did so with the needed help of the Russian Soyuz rocket, which served to fill the void left by the Space Shuttle. However, NASA is no longer the only US-based organization specializing in space-bound missions. Private corporations that specialize in these types of missions are now often referred to as Launch Service Providers (LSP) (McCall, 2020), have emerged as a major game changer and have kicked off a new Space Race. This time, it is a race more specifically focused on satellite deployment. As of 2023, the largest corporate player so far, in terms of both overall rocket launches as well as satellite deployment, is SpaceX, which began operations in the early 2000s (SpaceX, 2023). Although new to the business of satellite deployment, SpaceX alone has made significant strides through an economically sustainable business model and the development of innovative rocket technology. In many ways, SpaceX, along with Blue Origin and United Launch Alliance, a cooperative between Boeing and Lockheed Martin, have effectively replaced NASA as the sole launch provider for satellites, especially in Low Earth Orbit (LEO). So far, these companies have yet to openly experiment with ASAT technologies, but they nonetheless pose a potential threat to foreign competition both on the national and corporate level.
Figure 14-4: Satellite Orbital Types

Source: (Defense Intelligence Agency, 2022)
In summary, while threats in space originated from two major powers (i.e., the US and USSR), those threats have since diversified to other, more independent groups. Although the US and Russia still maintain their dominance, they now largely do so with the help of their semi-affiliated corporate entities. In many ways, this has made the situation in orbit unprecedentedly complicated. The following sections will attempt to provide a breakdown of the most serious threats posed against satellites today.
THE CURRENT SITUATION:
Players involved, interests
The faction associated with the US and its post-Cold War allies is the most complicated so this will be assessed first, starting with the US government. While NASA still plays an active role in the deployment and maintenance of satellite systems, it no longer receives the same support as it once did before the end of the Cold War and subsequent collapse of the USSR. Over the course of the three decades since, federal funding for NASA has fluctuated, but overall alteration has been limited. Since 1991, the yearly budget has averaged at just over 20 billion USD (Roberts & Harrison, 2022). However, when adjusted for inflation and considering its shrinking proportion of the US government’s total budget, these figures do not seem as optimistic. While the NASA budget Inflation, in particular, can hinder an organization’s spending power with major consequences. As such, NASA has been faced with a diminishing capacity to procure necessary assets to maintain its operations. This has led to the termination of many programs, such as the Space Shuttle in 2011. NASA then turned to the Russian-made Soyuz to ferry astronauts to and from the international space station with no primary alternative. But this is just the tip of the iceberg. NASA became so desperate for affordable components that it turned to Russian and Ukrainian manufacturers to make its own rockets, as was the case with the Antares rocket system (Guinnessy, 2014). This partnership only came to an end with the Russian invasion of Ukraine in early 2022. In short, a lack of funding drives NASA to make trade deals with its former rivals, only for those agreements to deteriorate. It may seem like an uncertain situation for the US space program as a whole, but there is another side to this equation.
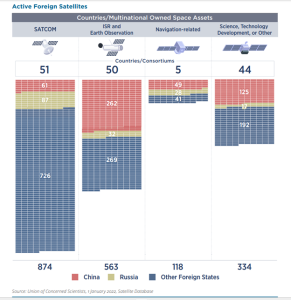
The newest factor to consider in the case of the US and the western powers is the emergence of corporate launch service providers (LSPs). As of this writing, the most notable of these in terms of development and contribution to satellite deployment is SpaceX. Founded in 2002, the company has blossomed into one of the biggest privately held companies in the world. It is important to note that, even without foreign resources, NASA relies on tech firms like Boeing, Northrop Grumman, and Pratt & Whitney to provide necessary components for every major space mission it plans to embark on. However, these companies have then so relied on Russian-made components due to their affordability. This was, of course, before SpaceX took over the market. Through heavy investments into research and development, improved supply chain management, and years of trial and error, the company has finally been making a name for itself by becoming a primary vendor for NASA and many other satellite operating organizations worldwide. In fiscal year 2022, SpaceX officially became the second largest seller to NASA after receiving just over $2 billion from the space agency (Berger, 2022). Only the California Institute of Technology receives more funding. Before turning the page to foreign adversaries and international competition, it is important to point out that as of May 2022, the US technically owns and operates at least 4529, more than 60% of the global total of 6718 (Union of Concerned Scientists, 2022). When critical of the risk of attacks against or disruptions of US satellite networks, these figures could be considered a vulnerability, as US satellites would be the target of attack or sabotage judging by quantity alone. It also makes these satellites difficult to manage and coordinate, while requiring excessive amounts of funding and resources to maintain. When looking at the total number of US-owned satellites, approximately 4000 are designated as commercial, meaning their operationality is primarily overseen by corporations. A recent spike in orbital objects, most notably payloads, has been attributed to various commercial actors such as ULA and BlueOrigin. However, SpaceX has been responsible for the majority of this growth through the Starlink program, by launching hundreds of satellites into Low Earth Orbit (LEO) since 2019. The company now owns approximately one third of the total number in orbit, making it the largest single satellite owner and provider by far. This new development has been regarded by analytical groups as NewSpace (Boley, 2021). This new era of satellite deployment brings unprecedented challenges, particularly having no one center of authority over private corporations and NASA alike, and the vast majority of satellites being deployed by corporations with no direct government ties. Analysts have also predicted that as many as 25,000 could be launched by 2031, the vast majority will be commercially (Garino, 2018).
Turning the page to foreign competition, the most obvious faction is the oldest known adversary to the US in the Space Race, and that is Russia. Despite being diplomatically and economically shunned by the international community since its invasion of greater Ukraine in February of 2022, Vladimir Putin has made repeated claims that the Russian space program would push on with its concurrent projects. These include the Soyuz and Luna-Glob programs, the latter of which focuses on the establishment of a lunar base and is a continuation of the soviet Luna program. Since the end of the Cold War, the country has ironically become one the USs’ largest foreign vendors in rocket and orbital technologies. The other side to this coin is China, which became significantly involved in satellite deployment recently. Through its worldwide initiative to invest in developing nations’ economies, often referred to as Belt & Road, China has been able to establish bases and staging areas overseas and in some instances on the polar opposite side of its default location on the globe. For example, the El Sombrero Station in Venezuela has been used as a satellite launching facility since as early as 2005, when the Venezuelan government signed an agreement with the Chinese state-owned Great Wall Industry Corporation to assist in Venezuela’s own satellite program (Krebs, 2023). It should also be noted that the Chinese have overseen the construction of as many as a dozen ground control stations across the South American continent in the time since. Chinese expansion in countries on the opposite side of the globe are indicators of a rapidly developing space program. The country recently established its fourth national launch facility on one of its southern islands. While Russia’s attention remains focused primarily on Ukraine and the military assets involved there, China’s ambitions for global hegemony are heavily affecting control over space. Between 2019 and 2021, the number of operational Chinese satellites doubled to 500, while major global investments have been drawn for Chinese startups intending to compete with the US and SpaceX (Garino, 2018). Both China and Russia believe superiority in space to be essential to their national security policy. Recent pacts between the two countries enforced by common geopolitical interests have created a common threat-actor for US and allied-owned LEO satellites.
Figure 14-5: Chinese Ground Stations
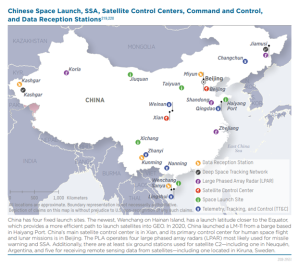
Source: (Defense Intelligence Agency, 2022)
Figure 14-6: Chinese Ground Stations

Source: (Defense Intelligence Agency 2022)
TECHNOLOGICAL ADVANCEMENTS AND CURRENT CAPABILITIES
As we move into a new chapter of space commercialization the global geopolitical landscape has shifted dramatically in large part due to the changing power dynamic in space. In contrast to the straightforward Red vs Blue, NASA vs Soviet matchup of the Cold War, the modern environment of high-tier outer-atmospheric actors has diversified significantly. Since the dissolution of the USSR, financial and technological resources along with the ingenuity to use such resources have expanded to corporate entities, specifically those based in North America, Europe, and Asia, with China entering as a new major player. While the US government still maintains overall authority in space, it must now channel that authority through a vast multitude of organizations, both federal and corporate. This has overcomplicated the way operations are coordinated in space. The voices of authority are no longer just emerging from the White House and the Pentagon. Executives of companies based around the country and with differing interests now control the means to deploy satellites. The capacity to do so and the capabilities of such satellites have dramatically increased throughout the 21st century. As a result, more reliable satellite networks like the GPS and NOAA as well as high speed internet have been introduced and/or maintained by government contracts, major tech companies, and private service providers alike. The introduction of satellite-based internet service has become highly disruptive both commercially and militarily. Improvements in the reusability of modern rockets is allowing more of these satellite networks to be deployed at LEO and other orbital levels.
The greatest feat that SpaceX has ever accomplished in the grand scheme of the Space Race itself is its contributions to advancing reusable rocket technology. Currently we are seeing its attempts at advancing the Starship initiative which is, as of this writing, still in the testing phases of development. Unsurprisingly these attempts have thus far resulted in the spectacularly fashioned explosions that the company is now well known for. However, this is SpaceX’s biggest virtue. Its willingness to push boundaries while also being able to financially whether the inevitable failures that initially arise are what have propelled it to become one of the most successful privately held tech companies thus far. Without trial, there may be no error, but there is also no success, and no entity in the United States has undergone such an intense amount of trial and error as SpaceX has since NASA during the 1960s. While the Space Shuttle program was the first to actively reuse rocket boosters at least once after the initial launch, a private company became the first to autonomously return them directly to the launch pad. The B1049 reusable rocket booster, unveiled by SpaceX in 2018 for the Falcon 9, set a record of six consecutive launches with minor refurbishments needed in between with another being used at least fifteen times in total (Reed, n.d.) This and many other B10 boosters have been partly responsible for the deployment of not only the Starlink satellite network, but those of various other companies including SkySat, Telstar, and Iridium (Thompson, 2020). The biggest seller of these rocket systems, and a major economic reason to develop reusable rockets in the first place, is their ability to make satellite launches excessively affordable to a growing pool of potential customers. The result was an unprecedented spike in satellite deployments over the past decade, attributed to the so-called NewSpace revolution (Union of Concerned Scientists, 2022).
Figure 14-7: SpaceX Starlink Satellite Deployment

Source: (Malik, 2022) & (SpaceX, 2023)
This technological revolution was obviously highly disruptive, especially due to the rapid establishment of satellite-based internet and communication networks by private LSPs. This can be seen as an economic threat to potential competitors on the international level, within the private sector but also Chinese-controlled companies that serve similar functions. Geely, for example, now owns several major automotive groups under its umbrella, including Volvo, but has been rapidly expanding to satellite manufacturing, and has boasted plans of producing at a rate of 500 per year by 2025. Another Chinese startup known as GalaxySpace intends on competing directly with SpaceX’s Starlink program by providing an integrated satellite/terrestrial 5G network via at least 1,000-satellites (Garino, 2018). The true concern isn’t the absorption of foreign industries or even the rapid growth of startups, but rather the Chinese central government having far more control over its domestic companies than that of the US. The security risks that come with Chinese tech companies involve espionage, sabotage, and general data mining which have been demonstrated by ByteDance (Roth, 2021), through TikTok, and DJI (Upward, 2022), the world’s top producer of small UAS. Both companies are accused of mishandling user data as well as for their roles in Chinese surveillance and censorship campaigns against the Uyghur minorities in Xinjiang. These incidents show how cooperative Chinese companies are with the CCP itself. The same comparison obviously cannot be made for the US government and US-based corporations.
In a sense, the previous reliance on foreign government technologies in order to send US assets into orbit e.g., Russia’s Soyuz rocket, would have been considered a major vulnerability. The potential threat of souring diplomatic relations, whether due to a war in Ukraine or otherwise, could result in a major disruption of an already questionable method of ISS astronaut ferrying. Thus, the transition to relying on US-based firms in times of reduced government funding is a necessary countermeasure to reduce the risk of losing a reliable transportation system to and from the ISS. However, the US government’s newfound reliance on private corporations can be seen as a double-edged sword, at least from a diplomatic standpoint. According to the 1967 Outer Space Treaty, the US government technically holds responsibility for these firms’ activities (Zedalis, 1978). Incidents such as the supposed near collision between Starlink satellites and a Chinese space station are just tastes of how easily this treaty can encourage excessive exchanges of blame and accusations between factions without any actual attack even happening (Hitchens, 2022). This is why the increasing congestion of space stations, vehicles, debris, and satellites in orbit can be seen as a major threat to both the unhindered operation of satellites in orbit and the US’s international image as a competent world leader in space. Man-made debris is also an example of how human activity in space can contribute to environmental hazards. This problem will only continue to worsen, as the introduction to satellite-based Wi-Fi internet has triggered a race to establish the best satellite-based Wi-Fi network in the world. This opens the door for not only cyberattacks and satellite killers, but the environmental threat of mid-orbit collisions. Tens of thousands of additional satellites are expected to be launched by the end of the decade.
Figure 14-8: Current and Future Projection of Active Satellites in Orbit
Source: (Defense Intelligence Agency, 2022)
Figure 14-9: Current and Future Projection of Active Satellites in Orbit
Source: (Defense Intelligence Agency, 2022)
Figure 14-10: Current and Future Projection of Active Satellites in Orbit
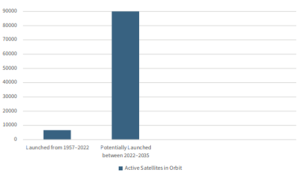
Source: (Garino, 2018)
In addition to improved payload deployment, ASATs have continued to evolve long after the end of the Cold War. As of today, there are four major nations that are actively researching anti-satellite weaponry. The US and Russia have been developing ASAT weapons since the 1960s, while China and India began around the end of the Cold War (Garino, 2018). The most surprising modern problem involving ASATs, however, did not involve their destructive potential of other satellites, but the creation of the majority of all man-made debris currently in LEO. Since 2007, about half of all the debris currently LEO was generated by man-made events, two of which were direct-ascent, kinetic kill ASAT tests (Defense Intelligence Agency, 2022). Despite Cold War-era international agreements discouraging the use of these types of weapons, it has not stopped these four powers from testing and further developing them for use in the near future. Today, the real hazard of using these types of ASATs is in the potential fallout of debris generated by the target’s destruction. This, in turn, further increases the environmental threat of debris and potentially destructive space objects overall. Given today’s worsening geopolitical climate over disputes such as Taiwan and Ukraine, the possibility of these weapons being used cannot be ignored
SATELLITE SYSTEM OVERVIEW ; RELATION BETWEEN GROUND, LINKS, & SPACE
A typical satellite system, such as the US Global Positioning System, consists of the following segments: User, Control, and Space. In the case of the American GPS satellite network, the User segment is considered the most secure, as it primarily receives signals from the satellites rather than transmits back. The Space and Control segments, on the other hand, are monitored and maintained by the US Space Force. In the case of US government-maintained systems, the only control points of the Control segment are staffed by US personnel and tasked with tracking the network’s satellites as well as updating and uploading navigational data (US Government, 2021). This leaves the Space segment, which primarily consists of the physical satellites themselves. Among the most common threats in this segment are obvious environmental hazards including small rocks of various origins and debris created from destroyed older satellites. These types of threats are always constant, yet they are oftentimes overlooked, at least more so than the ASAT and cyber/remote threats. While theoretically, these hazards will be slowly mitigated with the gradual improvement of monitoring and detecting equipment over time, increasing human activities, particularly those at LEO levels, are driving the threat far in the opposite direction, but this is a threat that will be elaborated in a later subsection. The more immediately mitigatable threats are those imposed by hostile foreign powers (i.e., China, Russia, Iran, & North Korea) including but not limited to: Cyber-weapons, Kinetic-Kill ASAT weapon systems, and Electronic Warfare. One of the most common manifestations of these threats is remote jamming. Such as GPS jammers employed by Russia.
Figure 14-11: Legacy GPS Jammer

Source: (Garino, 2018)
EFFECT OF SURFACE CONFLICTS ON SPACE SYSTEMS
Satellites have become essential to successfully conducting large-scale modern warfare. From navigation to surveillance to communication, satellites have become smaller and far more numerous in just the past several decades (Smith, 2011). This is because of the simple strategic advantage of relying on many cheaper, smaller units to fulfill a purpose rather than a few, more sophisticated and expensive ones. It is also in part the same reason so many mobile network providers, such as Verizon, continue to expand and develop their own infrastructure, which is to simply increase and improve overall coverage. With the rise of private LSP companies, overall satellite deployment expenses have significantly declined, opening the financial door to many big tech and government groups planning to launch their own networks. The “Starlink” internet network has been undergoing significant expansion, receiving a significant boost with the 2022 Russian Invasion of Ukraine. As of May 2023, there are more than 3500 operational SpaceX Starlink satellites in orbit (Dobrijevic, 2023). While the idea of mass-production and deployment may in many ways improve the overall reliability of a satellite network, it also simultaneously increases the vulnerability of that system being attacked from an external force, whether it be environmental (asteroid, debris) or man-made (anti-sat, cyberattack). The more operational satellites in a constellation, the more difficult it will be to manage each satellite as more resources and manpower will be needed to successfully maintain network operations.
In Wartime, satellite control has become essential, and not just merely for surveillance. Russia’s targeting of SpaceX satellites to disrupt the Starlink network over Ukraine was just a taste of what could come in future conflicts elsewhere as satellite internet networks become globally established. These new satellite fleets have become critical communication arteries for militaries in situations like Ukraine’s. In this case the strategic value was so high for Ukraine that Russian officials expressed concern over Starlink’s military capabilities months before the February 2022 invasion of Ukraine and proceeded to launch cyber-attacks against the network once Musk announced its operationality over the country (Kolovos, 2022). Russia even flirted with the idea of using kinetic ASATs against Starlink satellites, even though doing so would be considered an act of war. This is still a threat worth considering though, as the invasion of Ukraine is one of the only ongoing military conflicts that directly involve at least one major space power. Losing an advantage on any front, including LEO satellite coverage, can be a major strategic disadvantage. Therefore, it can be assumed that Russia, or any other nation in a similar position, would resort to violating any agreements barring the use of ASATs against foreign-owned satellites if it felt pushed to do so.
KNOWN THREAT ASSESSMENT
Relationship between Threats & Risk
There are four factors that should be considered when determining Risk: Threats, countermeasures, impacts, and vulnerabilities. (Nichols R. K., 2022) (Nichols, et al., 2023) Threats increase overall risk while countermeasures reduce it, thereby acting against each other. Vulnerabilities and impacts also increased risk and compound to each other along with threats. Here is an example of these factors affecting Risk: Suppose a large cluster of SpaceX satellites is being deployed in LEO, but on the same day, an unannounced CCP anti-satellite weapons test is occurring at a similar altitude. This would increase the Risk of asset loss during the deployment stages of the already massive satellite fleet because of the vulnerability of a high target count and the possible impact of the company being set weeks behind schedule, not to mention the billions of dollars in assets lost. The threat in this scenario is the unpredictable debris fragmentation generated by the ASAT test. A potential countermeasure could be an early warning system that somehow detects the debris and delays further deployments. But given the poor timing and lack of coordination between the parties at play, Risk of asset loss would still be significant during this event. This chapter, and the research conducted for it, is dedicated to threat assessment, specifically any threat that significantly increases the Risk of losing US and allied satellites currently operating in orbit along with those that rely on them. Research was focused on anything that was meant to increase the likelihood of destruction, damage, or sabotage of friendly satellites. Vulnerabilities are also heavily acknowledged as they serve to provide a better understanding of the threats discussed in this chapter. A threat exploits a vulnerability, amplifying the effect on overall Risk. From early assessment all known threats against operational satellites in LEO come in three forms: Environmental, Remote, or Physical. A significant increase in overall human activity and general congestion in LEO have contributed to worsened environmental hazards, i.e., debris. Remote attacks with cyber and/or electronic weaponry can also be made directly on satellites in orbit or the ground segment of satellite systems through the respective control station(s). Other miscellaneous threats include the ever-present possibility of internal satellite system failures, which are less likely and more dependent on the reliability of the provider(s). (Way, 2022)
THREAT EVOLUTION
Threat 1: Kinetic Kill Anti-Satellite Systems
Commonly referred to as ‘ASATs,’ these weapon systems follow one of two principles: either direct-ascent or co-orbital, the former of which seems by far the more prevalent concept in reality. Direct-ascent weapons use some form of trajectory to intercept a target in orbit without putting itself into orbit as well. On the other hand, a co-orbital weapon system does just that by placing itself in an identical or similar orbital pattern as the target in order to eventually eliminate it through either direct collision or some form of sabotage (Defense Intelligence Agency, 2022). The vast majority of the weapons systems being developed for ASAT purposes are in the direct-ascent category. In the 21st century, new actors have been garnering more attention with these types of weapons. China’s 2007 test of a ballistic missile destroying an old PLA weather satellite in LEO was the nation’s first successful demonstration of a direct-ascent ASAT in action (Kan, 2007). This brings to light a new arms race that isn’t limited to two superpower states and aims to reshape near-Earth space. A lack in international law and defense agreements pertaining to anti-satellite weaponry has allowed the technology to boom unchecked. One of the biggest reasons the threat of anti-satellite weaponry is ever-increasing is due to escalating tensions between major powers, not just between the US, Europe, and Russia, but also specifically China, Pakistan, and India. While the concept of anti-satellite weapons is by no means unique to the 21st century, there has been renewed interest in the technology for two primary reasons: the first is that any treaties or agreements that do pertain to anti-sats, the rules are not specific or up to date on terminology (e.g., what constitutes as “Arms”) (Sönnichsen, 2020). A more recent example of ASAT testing was India’s ‘Mission Shakti,’ demonstrated when a ground-launched interceptor missile was used to destroy an Indian earth observation satellite in LEO on 27 March 2019. The ‘Mission Shakti’ test destroyed Microsat-R, which was deployed as an intentional target as it had itself only just been deployed two months prior. The usage of evident ‘dummy’ satellites and their relative ease of deployment combined with an ever-intensifying surface-to-air weapons arms race highlights the impending threat of a rapidly deployable ASAT system with surface-to-air capabilities. The vulnerability of highly dense satellite ‘mega-constellations’ presents a target-rich environment. The future of ASATs poses an even more concerning outlook for the safety and operation of satellite networks. China, for example, has begun development of laser-based direct energy weapons (DEW), which could potentially damage or destroy satellite sensors, both optical and non-optical (Defense Intelligence Agency, 2022). As the usage of ballistic ASAT weapons becomes less practical for all major powers, the transition to DEWs may come well within the next decade.
Figure 14-12: ASAT Testing Timeline
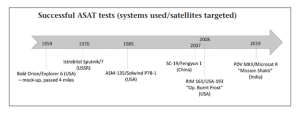
Source: (Sönnichsen, 2020)
Threat 2: Electronic/Cyber Attack
One of the more overlooked threats against satellites is that of a cyberattack, in fact, it is the greatest general threat when determining risk. This is because every satellite, regardless of purpose, must have some type of established radio-communication link with at least one control point or ground station on Earth in order to be useful in some form. This very link alone represents a serious vulnerability by default, and therefore allows for the specific threat of malicious actors broadcasting signals that could impede the proper functionality of a satellite network. The aforementioned ground stations are often considered less secure than the satellites themselves simply due to the ground station’s need for network connectivity. This is why many previous cyberattacks, such as the ViaSat attack on the eve of the Russian invasion of Ukraine, have explicitly and successfully targeted the ground segment of these networks (Boschetti, 2022). In the rapidly expanding small-satellite industry, the combination of Commercial Off The Shelf (COTS) and open-source software brings additional security vulnerabilities to the satellites themselves. In large arrays of small satellites, the software and hardware rely on some form of redundancy for each satellite to be compatible and communicative with each other. These so-called “satellite constellations” are often considered larger targets than standalone satellites not just due to the size of the fleets but the high number of ground control points needed to communicate with them. Other cyber-security-related vulnerabilities include poor encryption, inconsistent software patching, and the usage of older, legacy equipment for operations (Holmes, n.d.). Prime targets for cyberweapons and cyberattacks in general are ground control stations and the personnel that work there. Generally speaking, the majority of cyberattacks can be attributed to breaches from, usually unwitting, insiders. When focusing on satellite systems, however, entire nation states are attempting to breach these networks. These obviously include Russia and China as they each follow policies adhering to the pursuit of data and information “superiority” (Defense Intelligence Agency, 2022). Russian jamming of Starlink satellites in light of the Invasion of Ukraine prompted SpaceX to ramp up its operations over the nation. This, of course, has since made the network a prime target for Russian jamming efforts throughout the ongoing invasion. The Starlink V1 network itself proved to be highly insecure, allowing Russian military units to single in on user positions in minutes, prompting the company to relay warnings on how to use the service as it became the only non-Russian provider operational in the whole of Ukraine shortly after the invasion began (Malik, 2022). SpaceX boasts that the Starlink V2 fleet being deployed was designed to provide additional security with increased traffic, but the reliability of jamming techniques has persisted as it will continue to do so in the foreseeable future. This remains the case for all communications-based satellite networks. In regard to more complex, direct cyberattacks aimed at stealing information or data, the target will far more likely be a ground control station and/or its staff.
Threat 3: Orbital Collisions
A new threat has emerged recently regarding the rapid influx of hazardous LEO objects in little over a quarter century. This was initially a minor threat early during the Cold War, but increased human activities in space and LEO in particular are gradually turning this issue into one of the primary threats against operational satellites. It is also a universal threat, unlike those previously assessed, meaning a threat posed to every stakeholder of operational satellites worldwide. The reason for this is the destructive potential of LEO collisions, whether it be with another satellite or debris. This threat was brought to reality when, on 10 February 2009, a decommissioned Russian communications satellite, Cosmos 2251, collided with the operational Iridium 33 satellite, owned, and operated by a Virginia-based telecoms company of the same name. The collision generated over 1300 documented pieces of debris (Kelso, 2009). Objects generated from events such as these are tracked and recorded individually by groups including the US Space Surveillance Network (SSN) and the European Space Agency. However, potentially lethal objects that are not tracked by these groups are the most unpredictable and most concerning threat concerning orbital collisions. While groups like the SSN are not able to directly monitor the objects in LEO, they can at least make estimates based on previous events, such as orbital explosions and collisions that occurred and the fragmentation generated by them. The SSN designates these objects as lethal non-trackable debris (LNT). As of January 2022, it was estimated that between 600,000 and 900,000 LNTs exist in LEO (Defense Intelligence Agency, 2022). There are also 1300 objects, each with a mass exceeding that of an automobile, which are currently being tracked in LEO
Figure 14-13: Man-Made Space Objects
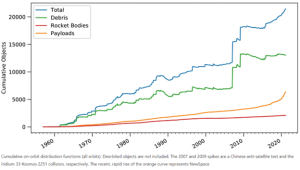
Source: (Boley, 2021)
Vulnerabilities acknowledgement
When assessing variables in pertinence to Risk, it is essential to note that Vulnerabilities multiply the magnitude of Threats. Age, and the resultant decline of sophistication, is an often severely overlooked vulnerability when referring to satellites in orbit. A more unexpected threat may target decommissioned legacy satellite systems. These satellites are by no means dead and are still in orbit to this day. The biggest issue with these systems is that, while they may no longer be used by the entities that were responsible for deploying and maintaining them, there could very well still be entities using them for their own gain. This is because satellites rely on ground stations to establish and maintain a stable communication link, otherwise the satellite would be useless. But ground-based links can easily be manipulated once the founding party has turned its attention away from so-called “retired” satellite systems. In 2022, researchers intentionally hacked the Anik F1R satellite launched in 2005 and successfully broadcasted malicious signals (Zarley, 2022). Generally speaking, the older the system, the more vulnerable it becomes to these types of attacks. Ground station security is also a major factor in determining the vulnerability of the respective satellite system. Any software glitch that can be exploited in a potential cyberattack is a vulnerability. When discussing satellites in LEO, first of all, an immediate vulnerability would be the proximity to most ASAT systems capable of reaching orbital levels. Since LEO is the lowest general orbital altitude attainable, it is cheaper to launch satellites at this level than at higher altitudes like GEO. There are also thousands of other satellites also operating in LEO, making it highly congestive and contested. In short, these are vulnerabilities of any satellite currently in LEO. The age and capabilities of the satellite systems in question would further determine the overall vulnerability of the system. For example, a twenty-year-old legacy GPS satellite would be far more susceptible to remote sabotage due to outdated systems and communications capabilities than a modern one. Furthermore, many of these satellites in orbit today are operating at up to four times their original life expectancy. The GPS network in particular is made up of thirty-one operational satellites, the network still operates with at least six designated “legacy satellites” launched prior to 2005 (US Government, 2022). Under the correct circumstances, the GPS network itself could be spoofed and an attacker would be able to inject false data into the communications systems. This could trick the system into calculating incorrect position, resulting in false data being presented to the user (King, 2020). While GPS operates at medium Earth orbit, other networks in LEO rely on hundreds of satellites to provide their services. SpaceX’s Starlink network is considered the largest by far, reaching over 1200 units in just the initial two years of deployment (Garino, 2018). In doing this, SpaceX has presented an interesting strategy to address Russian cyber-attacks. By mass-producing and deploying hundreds and eventually thousands of satellites in order to achieve maximum coverage, the overall vulnerability of losing service in targeted attacks is reduced, at least for SpaceX and its Starlink users. This is due to the idea that the producers can develop and deploy units faster than they can be decommissioned. Nonetheless, this does not escape the ever-present reality that as a system ages, it becomes gradually more vulnerable to attack. This is a reality faced by every satellite network. In short, when considering the vulnerability of a satellite system, age, altitude, satellite and control station quantity, and strategic importance are all factors that should be immediately considered, whether for networks like Starlink or GPS.
Figure 14-14: GPS Satellite Fleet
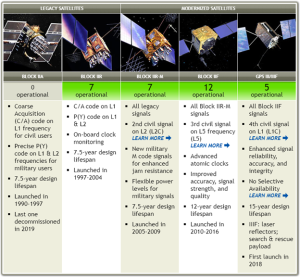
Source: (US Government, 2022)
THREAT SUMMARIES & CONCLUSIONS
Anti-satellite weaponry
An ASAT in this context serves the purpose of disabling a satellite by any physical means. These disabling techniques can involve either dismantling or destroying the device, or simply knocking it off of its orbital path and into a decaying one that eventually results in its destruction. Examples of Direct-Ascent ASAT weapons include Surface/Air-to-Space missiles, Kinetic Kill vehicles, Direct Energy Weaponry, and potentially any lethal projectile capable of reaching LEO altitudes. One of the most well-known demonstrations of these weapons was the destruction of the Chinese PLA weather satellite Fengyun-1C, which occurred in January 2007 at an altitude of over 800 kilometers (Defense Intelligence Agency, 2022). Co-orbital weapons are not as prevalent but can include space mines, robotic arms (used to either dismantle or push), as well as other satellites. The vast majority of ASAT tests is surface-based projectiles, similar to those used in the 2007 and 2021 incidents. So far, ASATs have been used solely on one faction’s own assets either to evaluate their capabilities or to physically destroy decommissioned satellites still in orbit, the numbers of which still rival currently active satellites (Slofer, 2022). The use of ASATs against another nation’s satellite would increase tensions beyond a reasonable level, so much so that even Russia will not even risk it. In a way, an ASAT can be analyzed in a similar sense to a hypersonic missile, EMP, or even a tactical nuke; it is likely that they will only be used as a last resort and any use of such weapons will be limited. When accounting for debris fragmentation in LEO, however, the incentive to avoid using these weapons to attack enemy satellites in space heavily outweighs those for not doing so. This is because of the vast amount of orbital debris that has accumulated due to ASAT tests in the past quarter century. For this reason, the threat of ASAT usage is surprisingly lower than initially expected, but the ability for this type of weaponry to create other threats in space, i.e., debris, boosts their final threat level and this time for all parties involved.
Remote Threats
One could, in a sense, consider cyberweapons and electronic warfare components to be remote ASATs. Their end purpose is more complicated, however. Rather than decommission a given satellite system by physically destroying its assets, these threats seek to gain access to the system and hijack it for another purpose. These methods include hacking and spoofing, which can be committed in a variety of ways including targeting the ground control stations established to maintain the satellite system through the ‘ground’ segment. In most cases these facilities are the key to gaining access to the rest of the satellite system. These stations could vary in quantity and defense capabilities depending on the satellite network in question, but these stations remain more vulnerable and prone to attack than the satellites they manage in orbit (Garino, 2018). Furthermore, as satellite-deploying companies expand on the services they provide, i.e., internet, they have made themselves far more prone to cyberattack and attempts to sabotage through remote means. We’ve seen a perfect example of this happening to SpaceX’s Starlink network during the first year of Russia’s invasion of greater Ukraine. These types of attacks, which mostly involve jamming techniques, have been conducted by Russia in other nations long before the 2022 invasion, but it is a method Moscow has settled into during times of war. On the other hand, no ASAT attack of kinetic or any other direct or co-orbital approach has been conducted on another party’s satellite, even over Ukraine. Meanwhile, EW and cyber-based threats have significantly influenced Chinese military reforms over the past decade, often employing cyberespionage against rival space powers, mostly European and North American satellite, and aerospace industries (Defense Intelligence Agency, 2022). As demonstrated by Russian jamming of SpaceX Starlink satellites over Ukraine, jamming technology remains the most probable threat based on experimental analysis. While it may pose a lower lethality when compared directly to ASATs, satellite communication disruption is a useful tactic often practiced heavily by Russia since the beginning of the Space Race and is currently one of the biggest threats against satellites over Ukraine right now. As a final note, it is important to consider the unique role that the ground segment plays and its, therefore, increased likelihood to be targeted in an attack.
Figure 14-15: GPS Ground Control Stations
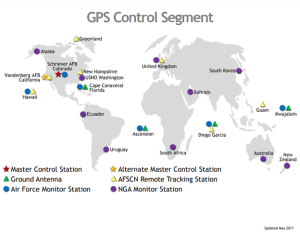
Source: (US Government, 2021)
Environmental elements
By far the most viable environmental threat in Earth’s orbit is the debris that has accumulated due to human activity in the past half century or so. In fact, overall congestion, particularly in LEO, is a hazard that everyone now needs to deal with. Upon concluding this research, it was surprising to see just how congested the overall environment at LEO has become with debris and satellite fragments as well as just how much human activity has contributed to this congestion. Specifically, human-generated debris within just the past two decades is deteriorating LEO conditions and has become one of the most prominent threats highlighted in this chapter. Man-made debris can worsen conditions in space by impairing abilities to monitor and track naturally occurring and potentially more hazardous objects, i.e., meteors. Debris can also significantly damage and/or destroy satellites and even create collisions if the fragments are large enough. Typically, the largest contributors to debris fragmentation have been segments of spent rocket stages and body parts. However, the continued reliance on reusable components is gradually changing these statistics. On the other hand, a more worrisome cause for debris fragmentation is the occurrence of orbital collisions, a threat expected to intensify due to concerns over worsening LEO congestion (European Space Agency, n.d.) Previous incidences of orbital collisions, such as the 2009 US-Russia satellite collision, and increased traffic in space due to increasing launch affordability enforces these concerns. Another recent source of overall LEO debris was the testing of direct-ascent ASATs. The now infamous ASAT demo on Fengyun-1C in 2007 is suspected of having contributed to increasing debris fragmentation and the overall number of trackable space objects by about 25%. The accidental collision between a US and a dead Russian satellite in 2009 as well as the Russian Nudol ASAT test in 2021 were also amongst the biggest contributors. In total, two ASAT tests and one accidental orbital collision between two satellites have nearly doubled the amount of all categorized debris in under fifteen years (Defense Intelligence Agency, 2022). Other environmental hazards include meteor showers and solar storms, but these are sporadic and rare. The more severe variants are also far easier to track and anticipate, providing time for preparations. Meanwhile, the threat of hazardous debris in LEO is only expected to worsen with overall object count expected to grow dramatically into the 2030s. From both a military and non-military perspective, the ongoing explosion of man-made debris has become a top threat concerning spacecraft and satellites in orbit.
Figure 14-16: Space Object Accumulation
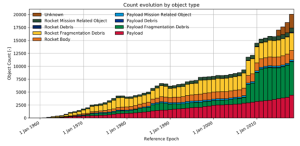
Source: (European Space Agency, n.d.)
Figure 14-17: Man-Made Threats Overview

Source: (Defense Intelligence Agency, 2022)
CONCLUSIONS
The so-called NewSpace era has begun with commercial actors becoming the main providers for LEO launches. This resulted in the doubling of both active and defunct satellites in just two years (Boley, 2021). Based on the deals made between SpaceX and the FCC for increased Starlink network development, this trend is likely to continue to intensify at least for the short future. SpaceX’s disruptive impact on the satellite industry as a whole has in turn helped generate threats against it. Many of these threats existed long before NewSpace, but some are more unprecedented. The issues of debris and overall congestion in LEO is a new issue that have not exploded in severity until recently. These are environmental threats that were boosted in part by the general spike in LEO activity often attributed to NewSpace. The biggest contributor to this boost, however, were kinetic-based ASAT missile tests, making even ASAT assesses a threat in a completely new way (Defense Intelligence Agency, 2022). On the other hand, remote attacks are the only threat that has consistently demonstrated itself thus far. Jamming remains a common technique used by foreign actors such as Russia, while cyberattacks have often targeted the ground segment of satellite networks through ground control stations. Nationally, China’s rapid rise as a space power can be seen as a major challenge to SpaceX and other western corporate LSPs who have surpassed NASA’s capacity to establish and manage satellite networks. One recommendation, from a policy perspective, is to formally designate space systems as a critical infrastructure sector vital to both the economy and national security (Gillette, 2021). While relations with China and Russia are currently deteriorating, some level of cooperation must be maintained in order to ensure the space remains a stable playing ground. This has been previously achieved through international agreements effectively de-weaponizing space for at least a time. However, the unprecedented involvement of private LSPs has complicated the dynamic between opposing factions in space. A common system of communication will be essential for moving forward. While individual threats spanning from weaponry to debris will continue to worsen, countermeasures will inevitably need to be developed to further deal with them as corporations and governments alike come to terms with the developing situation in orbit.
REFERENCES
Berger, E. (2022, Oct 26). SpaceX becomes NASA’s second-largest vendor, surpassing Boeing. . Retrieved from Ars Technica. arstechnica.com/science/: https://arstechnica.com/science/2022/10/spacex-becomes-nasas-second-largest-vendor-surpassing-boeing/
Boley, A. B. (2021, May 20). Satellite mega-constellations create risks in Low Earth Orbit, the atmosphere and on Earth. Retrieved from Sci Rep 11, 10642. https://www.nature.com/: https://www.nature.com/articles/s41598-021-89909-7#citeas
Boschetti, N. G. (2022). Space Cybersecurity Lessons Learned from The ViaSat Cyberattack. Retrieved from Johns Hopkins University. https://www.researchgate.net/: https://www.researchgate.net/profile/Gregory-Falco/publication/363558808_Space_Cybersecurity_Lessons_Learned_from_The-ViaSat-Cyberattack.pdf
Defense Intelligence Agency. (2022, March). Challenges to Security in Space. Retrieved from DIA.mil. www.dia.mil/: https://www.dia.mil/Portals/110/Documents/News/Military_Power_Publications/Challenges_Security_Space_2022.pdf
Dobrijevic, D. (2023, April 21). Starlink satellite train: How to see and track it in the night sky. . Retrieved from Space.com. https://www.space.com/: https://www.space.com/starlink-satellite-train-how-to-see-and-track-it
European Space Agency. (n.d.). About space debris. . Retrieved from European Space Agency. https://www.esa.int/: https://www.esa.int/Space_Safety/Space_Debris/About_space_debris
Futron Corporation. (2003, Oct 15). China and the Second Space Age. . Retrieved from www.futron.com/: https://web.archive.org/web/20120419165427/http://www.futron.com/upload/wysiwyg/Resources/Whitepapers/China_n_%20Second_Space_Age_1003.pdf
Garino, B. &. (2018, Sept). Space system threats – aerospace security. Retrieved from csis.org. https://aerospace.csis.org/: https://aerospace.csis.org/wp-content/uploads/2018/09/Space-System-Threats.pdf
Gillette, A. (2021, Sept 16). From Supply Chains to Spacecraft: Taking an Integrated Approach to Cybersecurity in Space. Retrieved from The Wilson Center.
Grego, L. (2012, Jan). A History of Anti-Satellite Programs. Union of Concerned Scientists. Retrieved from www.ucsusa.org/: https://www.ucsusa.org/sites/default/files/2019-09/a-history-of-ASAT-programs_lo-res.pdf
Guinnessy, P. (2014, May 8). Ukraine crisis hits US space industry. Retrieved from Physics Today. pubs.aip.org/physicstoday: https://pubs.aip.org/physicstoday/online/10200/physicstoday/search-results?f_Subjects=Politics+%26+Policy&fl_SiteID=1000045
Hitchens, T. (2022, Feb 3). US rejects charge that Starlink satellites endangered China’s space station. Retrieved from Breaking Media, Inc. https://breakingdefense.com/: https://breakingdefense.com/2022/02/us-rejects-charge-that-starlink-satellites-endangered-chinas-space-station/
Holmes, M. (n.d.). The Growing Risk of a Major Satellite Cyber Attack. Retrieved from interactive.satellitetoday.com: https://interactive.satellitetoday.com/the-growing-risk-of-a-major-satellite-cyber-attack/
Kan, S. (2007, April 23). China’s Anti-Satellite Weapon Test. . Retrieved from Congressional Research Service: https://apps.dtic.mil/sti/pdfs/ADA468025.pdf
Kelso, T. (2009). ANALYSIS OF THE IRIDIUM 33-COSMOS 2251 COLLISION. Retrieved from celestrak.org/publications/: https://celestrak.org/publications/AAS/09-368/AAS-09-368.pdf
King, M. &. (2020, Oct 8). Cybersecurity Threats in Space: A Roadmap for Future Policy. Retrieved from The Wilson Center https://www.wilsoncenter.org/: https://www.wilsoncenter.org/blog-post/cybersecurity-threats-space-roadmap-future-policy
Kolovos, A. (2022). Commercial Satellites in Crisis and War: The Case of the Russian-Ukrainian Conflict. Retrieved from Hellenic Air Force Academy. https://www.researchgate.net/: https://www.researchgate.net/profile/Alexandros-Kolovos/publication/368806976_Commercial_Satellites_in_Crisis_and_War_The-Case-of-the-Russian-Ukrainian-Conflict.pdf
Krebs, G. D. (2023, Jan 14). VENESAT 1 (Simon Bolivar 1). Retrieved from Gunter’s Space Page. https://space.skyrocket.de/: https://space.skyrocket.de/doc_sdat/venesat-1.htm
Lethbridge, C. (1996). BOLD ORION FACT SHEET. Spaceline, Inc. . Retrieved from www.spaceline.org/: https://www.spaceline.org/cape-canaveral-rocket-missile-program/bold-orion/
Malik, T. (2022, Mar 5). Elon Musk says SpaceX focusing on cyber defense after Starlink signals jammed near Ukraine conflict areas. Retrieved from Space.com. https://www.space.com/: https://www.space.com/elon-musk-spacex-starlink-cyber-defense-ukraine-invasion
McCall, S. M. (2020, Feb 3). National Security Space Launch. Retrieved from Congressional Research Service: https://www.everycrsreport.com/files/20200203_R46211_746668d39ebc17bb2860c8271e3a907a138bfef6.pdf
Nichols, R. K. (2022). SPACE SYSTEMS: EMERGING TECHNOLOGIES AND OPERATIONS. Manhattan, KS: NPP #47.
Nichols, R., Carter, C., Diebold, C., Drew, J., Farcot, M., Jackson, M., . . . & Toebes, J. (2023). Space Electronic Warfare. In R. Nichols, CYBER HUMAN SYSTEMS, SPACE TECHNOLOGIES AND THREATS (p. Chapter 10). Manhattan: New Prairie Press. Accepted for Publication, 2023; NPP#TBN.
Reed, J. G. (n.d.). Vulcan Reuse . Retrieved from American Institute of Aeronautics and Astronautics. https://ntrs.nasa.gov/: https://ntrs.nasa.gov/api/citations/20205008263/downloads/ASCEND-Vulcan%20Reuse%20R2%20FMC_V2.docx.pdf
Roberts, T. G., & Harrison, T. (2022, September 1). History of the NASA budget – aerospace security project – CSIS. Retrieved from aerospace.csis.org/: https://aerospace.csis.org/data/history-nasa-budget-csis/
Roth, S. M. (2021). DATA SNATCHERS: ANALYZING TIKTOK’S COLLECTION OF CHILDREN’S DATA AND ITS COMPLIANCE WITH MODERN DATA PRIVACY REGULATIONS. Retrieved from Journal of High Technology Law and Samuel M. Roth. https://bpb-us-e1.wpmucdn.com/: https://bpb-us-e1.wpmucdn.com/sites.suffolk.edu/dist/5/1153/fi
Slofer, W. (2022). SATELLITE KILLERS AND HYPERSONIC DRONES. In R. K. Nichols, & C. M. Carter, Space Systems: Emerging Technologies & Operations. Manhattan, KS: NPP #47. Retrieved from https://kstatelibraries.pressbooks.pub/spacesystems/chapter/satellite-killers-and-hypersonic-drones-slofer/
Smith, M. V. (2011). Spacepower and Warfare. U.S. Air Force. Retrieved from apps.dtic.mil/sti/: https://apps.dtic.mil/sti/pdfs/ADA536586.pdf
Sönnichsen, A. &. (2020, Jan 1). A Developing Arms Race in Outer Space? De-Constructing the Dynamics in the Field of Anti-Satellite Weapons*. Retrieved from S&F Security and Peace. https://www.nomos-elibrary.de/: https://www.nomos-elibrary.de/10.5771/0175-274X-2020-1/s-f-sicherheit-und-f-sicherheit-und-frieden-jahrgang-38-2020-heft-1?page=1
SpaceX. (2023). SpaceX Mission. Retrieved from SpaceX.com: https://www.spacex.com/mission/
Thompson, A. (2020, Aug 24). SpaceX’s most-flown Falcon 9 rocket booster yet returns to Florida home port. . Retrieved from Space.com. https://www.space.com/: https://www.space.com/spacex-falcon-9-rocket-booster-six-time-flier-returns-home.html
Union of Concerned Scientists. (2022, May 1). UCS Satellite Database. Retrieved from Union of Concerned Scientists www.ucsusa.org: https://www.ucsusa.org/resources/satellite-database
Upward, S. E. (2022). The American Security Drone Act: America’s Paper Tiger vs. China’s Trojan Horse. Retrieved from American University National Security Law Brief. https://digitalcommons.wcl.american.edu/: https://digitalcommons.wcl.american.edu/cgi/viewcontent.cgi?article=1143&context=nslb
US Government. (2021, Aug 9). Control segment. Retrieved from GPS.gov. https://www.gps.gov: https://www.gps.gov/systems/gps/control/
US Government. (2021, Feb 22). GPS Overview. Retrieved from GPS.gov. https://www.gps.gov/systems/gps/: https://www.gps.gov/systems/gps/
US Government. (2022, June 28). Space segment. Retrieved from GPS.gov. https://www.gps.gov/systems/gps/space/: https://www.gps.gov/systems/gps/space/
Way, T. (2022). Counterspace Weapons 101. . Retrieved from Center for Strategic and International Studies. https://aerospace.csis.org/: https://aerospace.csis.org/aerospace101/counterspace-weapons-101/
Zarley, B. D. (2022, April 14). An old satellite was hacked to broadcast signals across North America. Retrieved from Freethink Media Inc. https://www.freethink.com/: https://www.freethink.com/space/decommissioned-satellite-hacking
Zedalis, R. J. (1978). ANTI-SATELLITE WEAPONS AND THE OUTER SPACE TREATY OF 1967 . Retrieved from CWSL Scholarly Commons. https://scholarlycommons.law.cwsl.edu/: https://scholarlycommons.law.cwsl.edu/cgi/viewcontent.cgi?article=1947&context=cwilj

