Chapter 9: Non- Kinetic: Military Avionics, EW,CW,DE,SCADA Defenses
R. K. Nichols
Student Objectives
Chapter 9 is a potpourri of non-kinetic technologies for C-UAS. The student will be introduced to military avionics systems and the roles they play in the defense matrix. Avionics are the primary target of C-UAS efforts. A side-theme throughout this chapter is that most military manned aviation roles can be filled with the less costly unmanned option at reduced human liability. One of the most interesting roles is the maritime patrol aviation (MPA) and is singled out for coverage. Four areas will be explored in more detail: electronic warfare (EW), cyber warfare (CW), directed energy (DE) weapons and acoustic defenses. SWARMs continue to be a concern and are addressed. (Osborn, 2019)
What Is the Counter -UAS Problem?
The risk of successful terrorist attacks on USA Air Defense Systems (ADS) via sUAS/UASs is greater because of improving commercial capabilities and accessibility. Advanced small drones, capable of carrying sophisticated imaging equipment and significant payloads, are readily available to the public. A range of terrorist, insurgent, criminal, corporate, and activist threat groups have demonstrated their ability to use civilian drones and gather intelligence. How does the country defend against a growing UAS threat? This is also known as the counter – UAS Problem. General James D Mattis, SECDEF summed up the Problem succinctly: (Nichols, et al., 2019)
“Unmanned Aircraft are being developed with more technologically systems and capabilities. They can duplicate some of the capabilities of manned aircraft for both surveillance/ reconnaissance and attack missions. They can be small enough and / or slow enough to elude detection by standard early warning sensor systems and could pose a formidable threat to friendly forces.” (Chairman, 2012)
Operational Protection from Hostile UAS Attacks – A Helicopter View
“According to LCDR Boutros of the Navy War College, developing technologies do not paint a pleasant picture of counter – UAS problem (Boutros, Operational Protection 2015). UAS has seen a widespread proliferation among both state and non-state actors. This is a cause for concern to US Operational Commanders.” (Boutros, 2015) General James D Mattis, SECDEF concluded:
“The proliferation of low cost, tactical unmanned aerial systems demand we think about this potential threat now… we must understand the threat these systems present to our joint force and develop the tactics, techniques and procedures to counter the problem.” (Chairman, 2012) (Myer, 2013)
Joint Publication (JP) 3-01 identifies friendly assets that an adversary may attack during a campaign using UAS. A Theater Commander must plan for counter – UAS actions against air defense sites, logistics centers, and national critical infrastructure. (Boutros, 2015) “Due to their small size and unique flying signatures, many UAS are difficult to detect, identify, track, and engage with current joint air defense systems. The increasing proliferation of global UAS has exposed a critical vulnerability in the protection function of operational commanders, requiring joint efforts to include intelligence, Electronic Warfare (EW), cyber warfare, (CW) and FIRES.” (Boutros, 2015)
But UAS are not invincible. Neutralizing threats or mitigating risk includes active and passive defense methods with kinetic and non-kinetic FIRES.[1] (US DoD – JP 3-0, 2012)
Countering UAS Air Threats
Advanced UAS can carry large payloads great distances. US Predator and Global Hawk UAS, [See Figure 9-1] “Chinese Pterodactyl [See Figure 9-2] and Soring Dragon counterparts, and Iranian Ababil can carry at least 500 Kg payloads greater than 300 km.” (Boutros, 2015) “They can be armed or unarmed, with ISR payloads, communications relays, Over-The-Horizon (OTH) target acquisition, and precision strike capabilities.” (Boutros, 2015)
“Shorter range, tactical, small/micro UAS may not have the distance or payload capacity of more advanced systems, but they can impact a campaign (or US Homeland Defense) in equally serious ways. Because of their size, their heat signatures are almost nonexistent. They easily evade detection. They offer more freedom of action. They can be launched from within US air defense zones and fly to their targets in less time than it takes for a coordinated response.” (Boutros, 2015) [Nightmare alert: Imagine a SWARM of UAS carrying small potent binary bomb payloads attacking a US Carrier at port less than one mile away from the UAS launch point.] The enemy can effectively balance space, time, and force (arguably frequency too). (Beaudoin, 2011) “Small UAS (sUAS) can perform short-range ISR, be outfitted with explosive charges or chemical and biological agents for aerial dispersion, or simply fly over troops or civilians to demoralize.” (Boutros, 2015) [Nightmare alert: Given the effectiveness of enemy use of IEDs in Iraq and Afghanistan, a mobile, airborne version would take the Problem to an entirely new level!] (Nichols R.-0. , 2016)
Vulnerabilities Perspective
“sUAS are vulnerable to kinetic and non-kinetic outside influence in six different areas; their link to a ground station, the ground station itself, the aircrafts various sensors, avionics, cyber weapons, directed energy weapons (DE) and acoustical weapons (AW).” The military recognizes the first three factors, the authors concentrate on the latter group.
“In 2009 Iraqi insurgents successfully hacked into US Reaper drones, crashing them.” (Boutros, 2015) (Horowitz, 2014). “In September of 2011, ground control stations at Creech AFB were infected by a virus, temporarily grounding the entire UAS fleet.” (Boutros, 2015) (Hartman, 2013) UAS onboard sensors can be manipulated in many ways. “High intensity light directed at an optical sensor can blind it. GPS receivers can be cyber-spoofed, which consists of transmitting a stronger, but false, GPS signal to a receiver, resulting in inaccurate navigation. Influencing the local magnetic field can have adverse effects on both onboard hard drives and sensors that require magnetic orientation to operate correctly.” (Boutros, 2015) (Hartman, 2013) The object is to better understand UAS subsystems, to facilitate exploiting their weaknesses.
Figure 9-1 Global Hawk

Source: (Rogoway, 2018)
Figure 9-2 Chinese Pterodactyl

Source: (Defence, 2014)
The author’s research suggests that: The hostile technology of remote-controlled warfare is difficult to control or abort; the best defense (counter – UAS) is to address the root drivers of these threats. The threat-roots are SAA, SCADA and avionics. SAA and SCADA are vulnerable to both cyber and EW weapons. An EMS subset of special interest are acoustical countermeasures as research has confirmed their effectiveness against SWARMS. (Nichols, et al., 2019)
Conventional Vulnerabilities of Air Defense Systems (ADS), Attacks By sUAS and Countermeasures
A simplified, non-classified view of the US Air Defense System (ADS) against a hostile UAS attack occurs in two stages:
- Early Detection and Identification of “Danger Close” (Myer, 2013) [2]
- Applied appropriate countermeasures with secondary goal of restricted collateral damage.
The traditional ADS family of tools for Detection include:
- Active Radar Surveillance – generate waves, use rebound echoes on UAS to locate, estimate distance, approach speed, size, penetration vector and short-term trajectory, and
- Passive Monitoring – covers electromagnetic spectrum via visible, thermal infrared, radio waves on common communications channels.
When considering hostile UAS defense planners need to consider several issues. The US ADS is optimized for missiles and aircraft deployed at high altitude and speeds. ADS data fusion (detection, identification, weapon lock-on, execute countermeasures) works better with larger targets, not very small ones like UAS / sUAS. US ADS is effectively reactive for longer ranges. Close reactive engagements are sub-optimal. US ADS are not optimal for sUAS /UAS. (Nichols R.-0. , 2016) Neither were Saudi Arabian ADS against the Iranian attack on oilfields. (Gallagher, 2019)
“There are clear vulnerabilities of the US ADS to UAS:
- sUAS can be launched into action close to target(s), less than 1 mile.
- sUAS exhibit a small Radar signature. The detection phase is hindered.
- Reactive dictates quick response near target. This is not always possible.
- sUAS / UAS are designed for slow, low flight. Low flying sUAS avoids Radar identification.
- sUAS / UAS electric motors are both quiet and have limited thermal signature. This makes for difficult detection for noise.
- sUAS /UAS operate in urban areas. Urban sphere presents additional problems and potential collateral damage.” (Nichols R.-0. , 2016)
Conventional Countermeasures Against sUAS /UAS
There are two families of conventional countermeasures used to disrupt /destroy hostile UAS/sUAS systems (Regulatory ~ locked in firmware GPS No-Fly Zones, Registration, FAA rules excluded).
Active Measures – Designed to incapacitate, destroy the sUAS/UAS threat in a direct way (Ground-to- Air Defense (GTA), missiles or, acoustical gun, or simple cyber rifle or DE weapon )
However, there are some defensive issues to be considered:
- GTA efficiency against sUAS, reactive targets are reduced, even less efficient in urban zones where public at risk.
- Simultaneous attacks on multiple fronts very difficult to apply and defense measures are mitigated. [3]
UAS countermeasures research is improving. The goal is to increase ability of GTA to react and improve capabilities to a defined to a saturation limit. Team formation allows decoys and shields. SWARM formation is easier to detect. Arrival of a cloud of robot drones is hard to mask, but tough to neutralize. Commercial company Liteye has developed an Anti-UAV Defense System (AUDS) which are able to detect, track, and disrupt sUAS operation by pulsed, brief focused broadcast of direction frequency jamming. Liteye has also developed a mobile version call M-AUDS. (Liteye, 2018) China has developed a “5-sec” laser weapon to shoot down sUAS at low altitude (500 m) with a 10KW high energy laser beam. Its range is 1.2 mi and handles sUAS speeds up to 112 mph. (Nichols R.-0. , 2016)
Passive – Designed to protect indirectly; physical protections around target, decoys, shields, organized roadblocks, nets, jamming of sensors of the aggressor, GPS total or partial cyber-Spoof of signals. Passive countermeasures have some positive outcomes. Decoys can be effective if the ADS know what the sensors employed for sUAS Kamikaze attack and how they are used in the SAA subsystem. Communication jamming is effective against level 1 & 2 drones which require pilot interaction. It can disrupt inter–drone communications required for either team or SWARM formations. Sensor Jamming – especially GPS signals – giving false GPS information, camera/gimbal dislocation, and heading sensor demagnetization is effective regardless of automation.
The 2011 Iranian incident taught US ADS planner’s lessons about passive spoofing waypoints and Loss of Signal (LOS) via GPS. LOS is an emergency condition. sUAS/UAS have programmed responses. One of those responses may be,” return to waypoint”. Two types of spoofs were executed. A complete spoof uses the friendly SAA to estimate course, groundspeed, time to target to force a LOS and final waypoint change. A partial spoof reports false positions, during LOS and changes waypoints for perceived emergency conditions. Both spoofs are difficult to detect & effective (Editor, 2012)
Aggressor Counter-Countermeasures Specific to UAS Deployment – SWARM
The authors contend that a UAS SWARM attack is practically unstoppable unless the defender (US ADS) exhibits strong collaboration and ability to match/identify the SWARM locations in a timely matter. This requires combined active and passive measures. This portends the ADS computer networks must process, detect, identify, and target information (and make critical decisions) significantly faster and more effectively than their enemies. Cost is an additional vulnerability factor. SWARMS can be assembled, delivered, and targeted in a relatively inexpensive weapons package. A SWARM can use local counter jamming on target nets. (Nichols R.-0. , 2016)
Implications from Attack by Iran on Saudi Arabian Oil Fields
On 14 September 2019, Houthi rebels in Yemen claimed their attack on the Abqaiq and Khurais oilfields in Saudi Arabia. (Gallagher, 2019) The effect was to temporarily take out 5% of the global oil production capacity. (Gallagher, 2019) Houthi rebels claimed responsibility for the attack, saying that 10 drones (mixed origins) and 17 missiles were deployed. (Lister, 2019) See Figure 9-3. Ballistic missile attacks by the Houthis have been previously deployed using old Soviet and Iranian “Scud” SRBMs. No prior attack, since the Yemen conflict began four years ago, has interrupted oil supplies.
The Houthis have sent dozens of drones and short-range ballistic missiles against Saudi Arabia in the past two years. Many have been intercepted by Saudi Air Defenses; others have fallen harmlessly. Very few have caused limited damage and casualties. (Lister, 2019) The Abqaiq oilfield is 800 miles from Houthi-held parts of Yemen. The drones used were from North Korean Iranian and Chinese origins. (Lister, 2019) The Iranian drones were dubbed the UAV-X and have a range of 740 – 930 miles. This is a step up from the SRBMs that were based on North Korean technology with a maximum range of 186 miles. (Lister, 2019) The Chinese drones have several names: “Qaseth-1” (“Striker-1”), a rebrand of the Iranian Ababil-2 UAV and the “Mirsad-1” used by Hezbollah until 2018. (Gallagher, 2019) The step-up in the conflict game is the Iranian clone, KH-55 with a range of 1,550 miles. These were reportedly used in the Saudi Arabian oil field attacks. (Gallagher, 2019)
The take-away from this attack is not just the loss of global oil processing capacity but the vulnerability and exposure of the Saudi Arabian Advanced Air defenses. Most of the Saudi Arabian ADS are designed to defend against traditional threats and are ill-equipped to tackle the asymmetrical aerial threats such as drones. The vulnerability is enhanced when so many essential oil-related infrastructure parts are concentrated in a small area: storage, processing, compressor trains and distribution. (Lister, 2019)
Think of this problem more globally. China, North Korea and Iran [refer to as CNKI cooperation] are aggressively cooperating on drone technologies for use against a major oil production region. The technology is cost-effective as well as human capital efficient. Drones substituting for manned aircraft.
Figure 9-3 shows A haze of smoke is seen from the attacked oil plant in Saudi Arabia

Source: (Sheena McKenzie, 2019) https://www.cnn.com/middleeast/live-news/saudi-oil-attack-dle-intl/h_1ab7e8469e98525f887c3a4e588dde8a
Let’s expand the threat. Refer to Figure 9-4. Note that the Strait of Hormuz lies between Iran and Saudi Arabia, with Bahrain, Qatar, UAE and Oman in the sandwich. Between the Gulf of Oran and the Persian Gulf, about 20% of the global oil movement / supply travels through the Strait of Hormuz. (EIA, 2019) The US 5th Fleet currently protects this oil flow. There have been several clashes between Iranian vessels and US Vessels. Drones cross over the US Fleet every day and test its patience.
The key theme for this chapter is non – kinetic C-UAS technologies. Remember, payloads can be anything: CBRN deployment devices, drugs, surveillance packages, shaped charges, lasers, super resolution cameras, weather instruments, GPS/GNSS cyber weapons, missiles, etc.
The problem is twofold: what is the risk assessment for CNKI drone technologies cooperation acted on either target (US 5th Fleet or Saudi Oil Fields -both in range of KH-55’s) and what countermeasure technologies are available to counter the threats presented and to mitigate those risks and system vulnerabilities?
Military Avionics
Avionics is a generic name for a diverse set of functions being provided by AVIation electrONICS. Moir and Seabridge provide a fair history of the Avionics since the word was coined in 1930s. (Moir I. &., 2006) As avionics systems have evolved, the level of functional integration has increased dramatically. Technology has actually blurred functional boundaries. The outcome of this evolution has been to increase performance; sensor types; functionality; cost; integration; complexity; supportability and reuse; software / executable programs; memory; throughput; reliability; data handling; data links; and obsolescence. (Moir I. &., 2006)
The result has been to decrease size; weight; power consumption; and technology windows. (Moir I. &., 2006) The basic military avionics system according to the DoD standards is shown in Figure 9-5.
Military Aviation Roles
The authors contend with all due respect to USAF, USN, USMC, USA that most manned (piloted) military aircraft roles can be replaced by unmanned aircraft systems. The military was quick to understand the opportunities offered to them by the ability to leave the ground and gain the advantage of height in the battlefield. Military aircraft perform a variety of aviation roles using fixed-wing and rotary-wing aircraft. The roles define the type of aircraft because of the specialist nature of the tasks. Several aircraft types are designed for multi-roles or to change roles during the mission (aka swing-roles). Military aviation roles are driven by advances in the technology of sensors and avionics not by pilot abilities. (Moir I. &., 2006) More sensitive and effective sensor systems are capable of detecting targets, the use of stealth techniques increases the effectiveness of delivery platforms and increased capability of on-board computing systems.
Drones compact these sensor technologies. They eliminate wasted space. They can process on-board data close to their manned counterparts. Clearly cheaper to produce, they are expendable in battle.
In a military defense environment, a variety of military avionics systems exist[4]:
1) Air Superiority – Deny the enemy the airspace over the battlefield, thus allowing ground forces to rein freely in destroying ground targets.
2) Ground Attack – Assist tactical situation on the battlefield [close air support (CAS)]. This role includes the ability of designating targets by laser and precision bombing.
3) Strategic Bomber -The mission is to penetrate deep into enemy territory and to carry out strikes to weaken defenses.
4) Maritime Patrol Aircraft (MPA) – The mission is huge, to cover 60% of the earth’s surface ( water). The MPA is the most complex of systems aircraft with the demanding role embracing a broad spectrum of tactical and strategic tasks / tools, as well as, support for civilian and humanitarian activities. (Moir I. &., 2006) It includes sub-roles of Anti-surface unit warfare (ASuW); and Anti-submarine Warfare (ASW); Search and Rescue (SAR); Exclusive Economic Zone Protection (EEZP); and Customs and Excise Cooperation (C&EC). Each of these are broken down further into associated tasks / architectures as shown in Table 9-1 & 9-2. Figures 9-6 & 9-7 show two examples (P-3 Orion and Saab Swordfish) MPAs.
MPA interests the author because of his work on UAVs and intelligence gathering by Chinese in the Spratly Islands and his research into acoustic defenses / countermeasures against hostile SWARMS. Even with all of its complexity a good portion of MPA missions can be accomplished by unmanned aircraft systems.[5] Table 9-2 shows typical MPA platform architecture. Figure 9-8 shows the MQ-4C Triton BAMS MPA (unmanned). Note how powerful the UAS is and how well it meets the requirements of the MPA role.
Figure 9-4 Strait of Hormuz
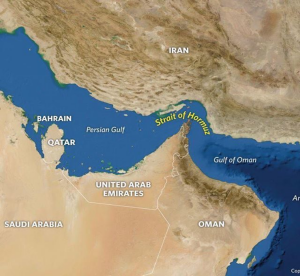
Source: (Stratfor, 2019)
5) Battlefield Surveillance -The mission is providing detailed knowledge if the tactical scenario on the battlefield with real-time intelligence of enemy and friendly forces.
6) Airborne Early Warning – Early detection and warning of airborne attack is critical to give air superiority and defensive forces sufficient time to prepare a sound defense. (Moir I. &., 2006)
7) Electronic Warfare (EW) – The role is composed of four subgroups: Electronic countermeasures (ECM) or jamming are common forms of EW used to disrupt communications or enemy radars. Electronic support measures (ESM) – actions taken to intercept, locate, record and analyze radiated electromagnetic energy for the purpose of gaining tactical advantage. Signals Intelligence (SIGINT) consists of Communications Intelligence (COMINT), Radar Intelligence (RADINT), Electronic Intelligence (ELINT) and Measurement and Signal Intelligence (MASINT).[6]
8) Photographic Reconnaissance – This role includes photographic imagery (IMINT) used to confirm SIGINT intelligence.
9) Air-to-air refueling – This role is required to extend range or endurance. This role is not easily replaced by UAS -to- UAS refueling. In 2018, Dr Saeed Kahn, Kansas State University, developed a method of drone-to-drone transfer of energy to replenish a UAV battery in flight.
10) Troop / material Transport – Logistics is the primary goal for this role . There is significant initial work on UAMs but as of this writing, this role is not replaceable (safely) by unmanned A/C.
11) Unmanned Aircraft Systems (UAS) – Many UAS have evolved to perform roles described in the previous list with ever-increasing performance and intelligence. (Nichols, et al., 2019)
The basic avionics system has the following major systems: Navigation, Communications, Sensors, Mission System and Displays and Control. Each major has several subsystems, for example, Sensors include Radar, ESM, Electro-Optical, Defensive Aids, and the author adds Acoustical. (Moir I. &., 2006)
Figure 9-5 A Military Avionics System
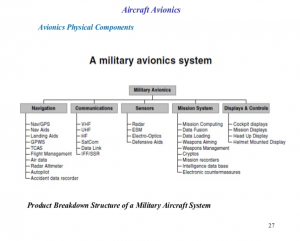
Source: p27, https://www.slideshare.net/solohermelin/8-fighter-aircraft-avionicspart-i
Table 9-1 MPA Roles and Tasks
| ASuW | ASW | SAR | EEZP | C&EC |
| Reconnaissance | CAS to task forces & convoys | Location of survivors | Oil rig surveillance | Anti-illegal immigration |
| Shadowing | Open ocean search | Dropping of survival equipment | Fishery protection | Anti-gun running |
| Strike against surface vessels | Extended tracking of submerged targets | Scene-of-action commander for rescue operations | Pollution detection & dispersal | Anti-terrorist operations |
| Tactical support of maritime strike aircraft | Deterrence of hostile submarines | Escort to rescue helicopters | Anti-drug smuggling | |
| Over-the-horizon targeting for friendly vessels | Cooperation with friendly submarines | Cooperation with rescue services | ||
| Intelligence collection | Intelligence collection | Escort of aircraft in difficulties | ||
| Communications relay | ||||
| Limited airborne early warning capability |
Source: (Moir I. &., 2006), pp.16-17
Table 9-2 Typical Maritime Patrol Aircraft Platform Architecture[7]
Source: (Moir I. &., 2006), p23
| Avionics | Communications | Mission System | Weapons |
| Navigation GPS /GNSS | VHF | Maritime Radar | Anti-ship missiles |
| FMS | UHF | Electro-optics turret | Torpedo’s |
| Autopilot | HF | ESM | Free-fall bombs |
| ADF | SHF SatCom | DASS | ASR Kit |
| DME | Link 16- | MAD | Flares |
| TACAN | Link 11 | Acoustic Systems | Smoke markers |
| TCAS | Marine Band | Mission Recording | Sonobuoys |
| Landing Aids | Shortwave | Data loader | Mines |
| GPWS | Cameras | Reflectors | |
| LPI RadAlt | Oceanographic database | ||
| Air data | Mission computing | ||
| Digital Map | Mission crew workstations | ||
| Homing | Intelligence databases | ||
| Direction Finding (DF) | |||
| MDP | |||
| Displays & Controls | |||
| IFF /SSR | |||
| Avionics data bus |
Figure 9-6 P-3 Orion MPA

Source: https://www.naval-technology.com/features/feature-the-top-10-maritime-patrol-aircraft/
P-3 Orion MPA Example
The P-3 Orion is a long-range maritime patrol aircraft (MPA) with multi-mission capabilities. Its 16-hour fly-time and high ferry range of 8,944 km make it the top MPA in the world. The aircraft was developed by Lockheed Martin principally for the US Navy. The aircraft entered service in 1962 and is currently in service with 21 operators in 17 countries worldwide.
The aircraft can conduct a variety of missions such as maritime / over-land patrol, anti-submarine warfare, anti-piracy, anti-terrorism, drug interdiction and the prevention of illegal immigration. Lockheed Martin offers a P-3 Mid-Life Upgrade (MLU) program to extend the aircraft’s service life by 20 to 25 years.
The aircraft can be equipped with infrared and electro-optical (EO) sensors, as well as special imaging radar to detect objects at long ranges. Its large internal weapons bay and ten external hardpoints can house a range of weapons. Four Allison T56-A-14 engines provide the P-3 Orion with a long-range cruise speed of 350k at 25,000ft. (Naval Technology Team, 2019)
Figure 9-7 MPA Example – Swordfish

Saab Swordfish MPA
The Saab Swordfish MPA is a multi-mission maritime patrol aircraft that is capable of conducting maritime ISR, maritime counterterrorism, anti-piracy, anti-submarine warfare (ASW) and anti-surface warfare (ASuW) missions. High dash speed and long endurance make the Saab Swordfish MPA an ideal maritime patrol aircraft.
The Saab Swordfish MPA comes with an advanced sensor and C4I package comprising 360° rotating multi-mode maritime surveillance radar, electro-optical sensors with laser payload, automatic identification system (AIS), identification friend or foe (IFF), electronic warfare and self-protection system, SATCOM, and tactical data links. It also features four weapon hardpoints to carry weaponry load.
Based on the Global 6000 business jet, the Swordfish MPA has a maximum cruise speed of 450k and a long-range cruise speed of 360k. It can remain airborne for 11.5 hours and conduct patrols. (Naval Technology Team, 2019)
Figure 9-8 MQ-4C Triton BAMS MPA (unmanned)

Source: (Naval Technology Team, 2019)
MQ-4C Triton BAMS MPA UAS
MQ-4C Triton is a new broad area maritime surveillance (BAMS) unmanned aircraft system (UAS) unveiled by Northrop Grumman for the US Navy. The UAS will complement the navy’s Maritime Patrol and Reconnaissance Force family of systems, delivering SIGNIT (signals intelligence), C4ISR and maritime strike capabilities. The US Navy intends to procure 68 MQ-4C Triton UAS to carry out surveillance missions, along with the manned P-8 Poseidon maritime patrol aircraft. Appendix 9-2 details the MQ-4C design features.
C-UAS Premise [8]
Let’s restate the major premise that almost all manned and unmanned systems used in military aviation are vulnerable to attack. (DTRA, 2019) Hostile actions are both kinetic and non-kinetic against the avionics systems. The following sections are concerned with the latter sphere which includes directed energy (DE), cyber warfare, (CW), electronic warfare, (EW), and a specialized EMS subset acoustical countermeasure (AC)s. [9] All these may defensively apply to hostile unmanned aircraft systems.[10]
Figure 9-9 High-Power Microwave Weapon to Destroy or Disable Swarms of Unmanned Aircraft

Source: (Military & Aerospace Electronics, 2019)
Effects of Directed Energy (DE) Weapons (EDEW)
Directed energy weapons make up diverse types of weapons such as lasers, particle beams, microwaves and even bullets. All DE weapons are just devices that deposit energy in targets, and that energy which must be deposited to achieve a given level of damage is relatively insensitive to the type of weapon employed. (Nielsen, 2012)[11] American DE weapons may, in fact, change the way future wars will be fought. (Beason, 2005)
Energy cannot be deposited in a target unless it is first delivered to the target. This is called propagation of energy. This subject was covered in: (Adamy D. , 2001), (Adamy D. , 2009), and (Nichols, et al., 2019) There is always some loss of energy during propagation. The DE must deliver more energy than needed to damage the target, to compensate for the loss along the way. DE weapon design depends on two factors: First, the anticipated target, which determines the energy required for damage. Second, the anticipated scenario (range, environment, time, etc. See Table 9-3) which determines how much energy must be produced to ensure that an adequate amount energy is delivered in the time available. (Nielsen, 2012)
Table 9-3 Battlespace Dimensions
| Dimension | Function | Action |
| Latitude | Friendly Force Location | Direction of Weapons
|
| Longitude | Enemy Force Location | Maneuver of Forces |
| Elevation
|
||
| Time | Speed of Maneuver | Timeliness of Attack |
| Timing of Weapon Release | Enemy Vulnerability | |
| Frequency | Bandwidth Required | Rate of Information Flow |
| Bandwidth Available | Interference | |
| Frequency of Transmissions | Vulnerability to Jamming
|
|
| Vulnerability to Intercept
|
Source: (Adamy D. -0., 2015)
Energy required for damage
Damage may be defined as Soft damage which is an upset to the UAS computers to hard damage meaning the complete vaporization of the UAS in the air. The former is sensitive to the details of the attack, the hardness of chips, the computer(s) details, communications, circuits and sub circuits. Vaporization produces immediate feedback as to target status – catastrophic. Determining how much energy a weapon must produce to damage a target, two things must be known: how much energy it takes to damage the target, and what fraction of the energy generated will be lost in propagating to it. (Nielsen, 2012)
Ice Cube
Consider the energy required (damage level) to vaporize an ice cube. [12] Pull an ice cube from the refrigerator. Its temperature is below the temperature it will melt. First, we must raise the temperature to melting temperature. The energy required is proportional to both the necessary ΔT rise and the amount of ice in the cube. From thermodynamics, the expression covering this is:
E = mC (Tm-Ti), where E is energy required in Joules, m = mass of ice cube in grams, Ti = the initial temperature in Celsius, Tm= melting temperature, C is the heat capacity constant of proportionality (J/gm x o C).[13] So, E = 2100 Joules of energy required to raise it to the melting point. This is not enough. We must melt the ice cube. Heat of fusion (Lm) is the amount of energy required to convert 1 gm of solid to 1 gm of liquid. With an additional 16,700 Joules, we now have a small water puddle. But our object is to vaporize the ice cube – hard damage. Using the specific heat equation again, E = mC (Tv-Tm), we require an additional 21,000 Joules to raise the ice cube as molten water to vapor at the same temperature by supplying the heat of vaporization, Lv = 2,440 Joules per gm of water. This means an additional 122,000 Joules of energy are required. The total amount of energy needed to vaporize an ice cube of 50 gm is 161,000 Joules. Lv accounts for about 75% of the required energy.
10,000 Joules
(Nielsen, 2012) gives a table of thermal properties of Aluminum, Copper, Magnesium, Iron and Titanium. It shows that most solid materials (See Table 9-4) have density on the order of 1 – 10 gm /cubic centimeter and that 10,000 Joules is sufficient energy to vaporize about one cubic centimeter of anything! 10,000 Joules is a magic number because it is close to the energy delivered by a wide range of DEs. (Nielsen, 2012) A typical rifle round has about 10 gm and is fired at a muzzle velocity of 1000 m/s. (Halsam, 1982) This corresponds to a kinetic energy (KE) of (mv 2 /2) of 5,000 Joules. A roman Catapult could throw a 20 Kg stone over 200 meters. The KE required for this use is about 40,000 Joules. (Foley, March, 1979) A medieval crossbow could launch an 85-gm bolt over 275 meters. This required 13,000 Joules. (Vernard Foley, January, 1985)
Table 9-4 Thermal Properties of Common Materials
| Material | Density
Gm/cm3 |
Melting Point, Tm
0C |
Vaporization Point, Tv
0C |
Heat Capacity
(J/gm0C) |
Heat of Fusion
(J/gm) |
Heat of Vaporization
(J/gm) |
| Aluminum | 2.7 | 660 | 2500 | 0.9 | 400 | 1100 |
| Copper | 8.96 | 1100 | 2600 | 0.38 | 210 | 4700 |
| Magnesium | 1.74 | 650 | 1100 | 1.0 | 370 | 5300 |
| Iron | 7.9 | 1500 | 3000 | 0.46 | 250 | 6300 |
| Titanium | 4.5 | 1700 | 3700 | 0.52 | 320 | 8800 |
Source: Table 1-1 (Nielsen, 2012)
Energy Alone Sufficient for Hard Damage?
In a nutshell, no. A nuclear bomb releases a lot of energy. One Kiloton yields 4,000,000,000,000 Joules. Well above the 10,000 Joule criterion, but at a distance of less than a mile from detonation, a concrete structure is undamaged. Over the same range an artillery shell with only 10,000 Joules of energy could easily destroy such a structure. Consider also the sun. It delivers about 5,000 Joules of energy over every square centimeter of the earth’s surface, yet we see no cars melting or people fried. Clearly, the energy must be delivered over a small region and in a short time to the target. Energy is not the silver bullet for damage. We must consider also density of energy on the target (Joules per square centimeter),[14] the rate of energy delivery, or power (Joules/ sec or Watts). The nuclear bomb is not a DE weapon like the artillery shell. Much of the energy released does not intersect with the concrete structure and is “wasted”. The artillery shell is a DE and concentrates all of its energy right to the target in question. If we spread the energy of the bomb over a surface of a sphere at a range of one mile, the energy density is only 13 Joules per square centimeter, far less that the DE artillery shell density of 10,000 Joules per square centimeter. With the spreading of blast energy accounted for, the nuclear bomb is consistent with other weapon types. (Nielsen, 2012)[15]
Energy Delivery Rate
If energy is delivered over too long a period, it is not effective in damaging the target UAS. The target can shed energy as rapidly as it is deposited. Cars in a parking lot, (unfortunately fatal to youngsters or animals left in the car) until they become so hot that they radiate energy away as rapidly as its deposited, so they don’t heat up to a point of sustained damage. After that they heat up to a constant temperature. Only if energy is delivered more rapidly than the target can handle it will damage ensue. (Nielsen, 2012)
From thermodynamics, we know that energy can be transferred away (lost in propagation) from a target by conduction, convection and radiation.
Thermal conduction losses (energy flow or “downhill” temperature gradient (slope of curve of temperature v distance) from hot regions to cold regions moving the temperature to equilibrium in the system). The equation for thermal conduction is
U = -k(dT / dx) Equation 9-1
Where U = rate of flow of energy across a surface, J/cm2 sec
dT /dx = the slope of the temperature curve, degrees / cm
k = constant of proportionality called thermal conductivity[16] in J/ sec cm deg
Energy flows until the temperature is the same everywhere in the system.
Convection (heat loss by macroscopic motion of molecules). Think of an attic fan moving hot air out of the attic, where motion is induced by the fan blades. The expression for wind induced convection for temperature v distance:
dT /dt = – V dT/ dx Equation 9-2
Where V = wind velocity
T = temperature in time at point x
dT /dx is the rate of change of Temperature in time at point x
For a target to lose energy by conduction or convection, it must be immersed in the atmosphere, water or some fluid medium to supply the necessary molecules to carry the energy away.
Black Body[17] radiation can occur in space or in a vacuum. Molecule movement is not just random, they vibrate, rotate and incorporate energy in their internal structure.
The total intensity of radiation emerging from the surface of a Black Body, S (Watts/cm2) is:
S = σ T4 Equation 9-3
Where σ = Stefan-Boltzmann constant = 5.67 x 10-12 (Watts/cm2 K4), K= Kelvin temperature.
Implications
Damaging targets depends not only on delivering energy, but also concentrating the energy in both space and time. In space we deliver about 10,000 Joules per cm2 of target surface, either at a single point, (bullet) or over the whole surface, as in a nuclear weapon. In time, energy must be delivered more rapidly than the target can shed energy through conduction, convection and radiation loss mechanisms. The fluence (Joules / cm2) or Intensity (Watts /cm2) necessary to damage a target will vary with time or pulse width that the weapon engages the target.[18]
Energy Losses in Propagation
There are two types of energy losses in propagation: the spreading of energy such that it does not interact with the target, and the wasting of energy in interactions with a physical medium, such as the atmosphere, through which it passes to destroy the target. Type one occurs whether the weapon or target is located on earth or in the vacuum of space. Type two occurs primarily when weapon or target lies within the atmosphere. Table 9-5 shows the Energy losses in propagation as a function of weapon type and loss mechanisms.
Table 9-5 Energy losses in Propagation
| Weapon Type | Energy Loss Mechanism |
| Kinetic Energy (bullets, rockets) | Atmospheric Drag |
| Lasers | Absorption by molecules |
| Scattering by molecules | |
| Absorption by aerosols (small particles) | |
| Scattering by aerosols | |
| Microwaves | Absorption by molecules |
| Scattering by molecules | |
| Absorption by water droplets | |
| Scattering by water droplets | |
| Particle Beams | Energy losses to electrons |
| Scattering from nuclei | |
| Scattering from electrons | |
| Radiation |
Source: (Nielsen, 2012)
Advanced DE research is both fascinating and mostly classified. Below are examples of military systems that may be used for C-UAS defenses.
Directed Energy (DE) Counter Weapons, High-Powered Microwave (HPM) Defenses, High-Power Lasers (HPL)
The US Air Force Research Laboratory is investing US$16 million in further field assessment of Raytheon’s Phaser High Power Microwave System outside the continental U.S. [See Figure 9-9] The testing phase will span over 12 months in which the Phaser will engage simulated and real unmanned aerial systems threats. The evaluation will explore the effectiveness of Phaser’s counter-drone engagement without disrupting the necessary installation operations.
The effectiveness of Phaser against drones has already been demonstrated at the Army MFIX exercise in 2018, when the system eliminated 33 drones, 2-3 at a time. Currently mounted on a shipping container-like box, Raytheon plans to significantly reduce the size in future versions.
AFRL already evaluates two other HPM systems – the Tactical High-Power Operational Responder (THOR), [ See Figure 9-10] that deploys as a means to provide base defense against drones, and ‘Counter-Electronic High-Power Microwave Extended-Range Air Base Air Defense’ system, or CHIMERA, designed to engage multiple targets over a larger area.
The HPM contract follows a separate Air Force contract in which Raytheon will build two prototype high-energy laser systems, also to be deployed overseas. The HPM and HEL systems can be used independently or together to counter-unmanned aerial system threats. “There’s more than one way to defeat a drone,” said Dr. Thomas Bussing, Raytheon Advanced Missile Systems vice president. “We are delivering the world’s first defensive directed energy systems that can be used alone or in tandem to defeat enemy drones at the speed of light.” (Eshel, 2019)
Figure 9-10 THOR

Source: (Eshel, 2019)
Raytheon announces delivery of first laser counter-UAS system to U.S. Air Force
U.S. defense contractor Raytheon Co announced that it successfully delivered the first high-energy laser counter-unmanned aerial system to the U.S. Air Force earlier this month.
In recent years, the Defense Department has assessed directed energy weapons—more commonly known as “lasers”—as an affordable alternative to traditional firepower to keep enemy drones from tracking and targeting troops on the ground. The system will be deployed overseas as part of a year-long Air Force experiment to train operators and test the system’s effectiveness in real-world conditions. See Figure 9-11.
Raytheon’s high-energy laser weapon system uses an advanced variant of the company’s Multi-spectral Targeting System, an electro-optical/infrared sensor, to detect, identify and track rogue drones. Once targeted, the system engages the threat, neutralizing the UAS in a matter of seconds.
“Five years ago, few people worried about the drone threat,” said Roy Azevedo, president of Raytheon Space and Airborne Systems. “Now, we hear about attacks or incursions all the time. Our customers saw this coming and asked us to develop a ready-now counter-UAS capability. We did just that by going from the drawing board to delivery in less than 24 months.”
Raytheon installed its high-energy laser weapon system on a small all-terrain vehicle. On a single charge from a standard 220-volt outlet, the HELWS can deliver intelligence, surveillance and reconnaissance capability and dozens of precise laser shots. It can also be paired with a generator to provide a nearly infinite number of shots.
Raytheon Company is integrating multiple proven technologies to counter the unmanned aerial system threat across a wide range of scenarios – from commercial airports to forward operating bases to crowded stadiums. Raytheon’s portfolio of sensors, command and control systems, and kinetic and non-kinetic effectors covers all aspects of the UAS threat. (Raytheon, 2019)
Figure 9-11 Raytheon announces delivery of first laser counter-UAS system to U.S. Air Force

Source: (Raytheon, 2019)
Modern Communication Threats to UAS
Unmanned Aerial Systems (UAS) are in widespread use for reconnaissance, EW, and weapons delivery. They are extremely dependent on interconnection with ground stations by command and data links. (Adamy D. , 2001) The increased use of Low Probability Intercept (LPI) has become a significant challenge to electronic warfare (EW) communication links. (Adamy D. , 2001) This chapter explores LPI and Jamming. The student should then have enough background to understand the criticality of LPI and Jamming of UAS communication links. Air defense missiles and associated radars make significant use of interconnecting links. (Adamy D. , 2001) SUAS sometimes use cellphones to command and control the UAVs. Cell phones are widely used for command and control function in nonsymmetrical warfare situations. (Adamy D. , 2001) ISIS and other terrorist groups use cell phones to trigger improvised explosive devices.
Cybersecurity attacks on data communications links are highly classified. Similarly, modern radar threats to hostile installations are also generally classified. Before examining LPI and communications signals/link- jamming, we first review the EW environment specific to UAS. Time for a few definitions of terms.[19]
Information Operations (IO) and the part EW plays
Figure 9-12 shows the global view of Information operations. Note how nicely all the prior definitions fit into the puzzle? Note that EW is a key component of IO, but not the singular dominant puzzle piece. [20]
Figure 9-12 Information Operations
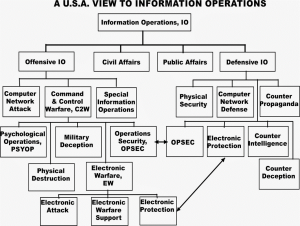
Source: http://c4isys.blogspot.com/2013/11/basics-of-information-operations-24.html also Source: JP 3-13 (Joint Publication) and pertains to Information Operations (IO) in the United States. http://www.dtic.mil/doctrine/new_pubs/jp3_13.pdf
Autonomy vs. Automation
Table 9-6 shows the normal five levels of automation that characterize UAS systems with examples of commercial vehicles. NASA presents a more detailed level of automation breakdown based on the OODA (Observe, Orient, Decide and Act) decision loops. (Barnhart, 2012) However, Table 9-6 should suffice to understand the cyber-purview. Level 1 slave and Level 2 Automated (minimal) are commonly found on UAS sold at Amazon, Walmart, and similar outlets. The pilot makes all the decisions and has complete control of flying orders. Level 3 steps up the navigation capabilities using an a priori mission plan.
Levels 4 and 5 add higher-level decision-making capabilities; collision avoidance without human intervention, complex mission planning in all weather conditions, expert systems intelligence without human intervention i.e. Artificial Intelligence (AI) and advanced Sense and Avoid systems (SAA). Level 5 is not commercially available; many designers are well on their way to a fully operational Level 5 UAS.
Table 9-6 UAS Automation Scale
Level 1: Slave – assisting piloting, reaction to disturbance
Level 2: Automated – maintains its flying orders and receives higher level orders
For Levels 1 and 2 are common, require pilot intervention and continuous communication link;
reasonable prices < $1500 US, small, weight < 10lbs: Drone Parrot, Quad Flyer GAUI
Level 3: Automated Navigation (a priori mission plan)
For Level 3 micro-UAS premium (< $20,000 US): Dragonfly, Microdrone Gmbh,
Fly-n-Sense, Mikrokopter
Level 4: Response from contextual data Collision Avoidance (CA) (w/o human intervention)
For Level 4 minimum knowledge of surrounding environment, reacts to events, perform CA,
uses active SAA, requires mission plan
Level 5: Decision-Maker (expert system) from contextual data: navigation in unknown environment,
complex missions, coordination and collaboration of signals
For Level 5 AI, decision making with heavy networked computer support, perceptive sensors
for space and time, complex mission in unknown environments, capable of intelligent adjustments
including mission rescheduling, keyword- adaptive control Levels 4 and 5 are confined
to laboratories. (Nichols R.-0. , 2016)
Table 9-7 UAS Collaboration shows four types of possible UAS collaboration. At the lower end of a threat scale is the isolated UAS or a small group of UAS. The advantages lie in a specific mission, which may be piloted or autonomous. They carry light payloads and are affordable. They are easy to assemble in the field. An example is the Raven used by US Special Forces. The disadvantage (countermeasure applied) is to identify the pilot or leader vehicle and destroy/disable it. A UAS attack team is particularly effective against divided attack targets, Level 3 allows automatic navigation, synchronized actions, and limited updated mission information. With increased team members, synchronization is not guaranteed. Disabling part of the UAS Team does not guarantee that mission failure. The real vulnerability of the UAS team is the Chief. All synchronization and updates go through the Chief. Disable/destroy the Chief and the Team is rendered useless. Determining who the Chief is critical.
Far more dangerous is the Swarm configuration especially in the higher levels of autonomous engagement. Swarms have several advantages. They are efficient based on numbers; they demonstrate emergent large group behaviors and reactions. Even not controllable or automated, they show a decentralized intelligence – think shoal of fish with evolving local rules. UAS Swarms are a highly resistant form, not changing based on survivability of members. There is no hierarchy like a team. Destroy part of the swarm and the rest will continue their mission without abatement.
The two known countermeasures are: 1) Disrupt / Change the Strategic Global View of Swarm (its only real vulnerability) and 2) Force defender collaboration. (Nichols R.-0. , 2016) China appears to be the leader in innovative UAS swarm intelligence, through the efforts of the Chinese Electronics Technology Group Corporation (CETC). (Kania, 2017) This is not a threat to be underestimated.
Table 9-7 UAS Collaboration
Type 1: Isolated Individual UAS
Advantages: piloted or autonomous w/ specific mission to perform. Small, easy to assemble, affordable, light payloads.
Countermeasures: Stop, Disable or Destroy Pilot, Threat removed.
Type 2: Group of Individual UASs (Isolated with own mission but not coordinated)
Advantages: sphere of action may be different for each mission, increased numbers, and increases success of attacks by defenses saturation
Countermeasures: Stop, Disable, Discover and Deter or Destroy Pilot(s), Threat(s) may be removed.
Type 3: Team of UASs (All members assigned specialized tasks and coordinated by Chief)
Advantages: Particularly effective against divided attack targets, Level 3 allows automatic navigation, synchronized actions, but no update to mission plans based on field activities.
Disadvantages: Level 4 (w/o humans) yields surrounding reactions but may lose synchronization between team members. Level 5 permits continuous updates, communications, commando style.
Countermeasures: Stop, Disable or Destroy Team members. Determine behavior logic and intervene. Survival of team members is critical to defense actions. Threat mitigated.
Type 4: UAS Swarm (Uniform mass of undifferentiated individual’s w/o Chief at level 4 or 5)
Advantages: Efficient based on numbers, emergent large group behaviors and reactions, not controllable or automated, decentralized intelligence – think shoal of fish w/ evolving local rules; highly resistant form, not changing based on survivability of members, no hierarchy
Countermeasures: Disrupt / Change the Strategic Global View of Swarm (its only real vulnerability). Defender collaboration. (Kania, 2017)
Commercial Small Unmanned Aircraft Systems (sUAS) Overview
There is a natural tendency to think that small unmanned aircraft systems present no threat, especially to US defenses. They are simply recreational or commercial toys. But they present a threat to National Airspace (NAS) – especially near airports. Figure 9-13 shows the results of a sUAS crashing into a jetliner in 2016.
Figure 9-13 Drone Crash into 737-700 passenger jet while landing at Mozambique

Source: UK Express, http://www.express.co.uk/travel/articles/751165/drone-boeing-737-plane-crash-mozambique. Also See: https://youtu.be/2jzx8BpDuHE
USA FAA Part 107 special rule forbids use of sUAS within a five-mile radius of an airport. (FAA, 2018)
Table 9-8 shows some of the available options and each year more capabilities are being added. Imaging, camera capabilities, weatherproofing, and payloads all can be used to gather intelligence, provide reconnaissance or deliver a lethal payload. They are radar resistant and deploy with a very small heat signature, so they can be in close target quickly, before defenders can activate countermeasures.
Table 9-8 Commercial sUAS Parameters
- “Flying Characteristics Available as RTF (off-the-shelf Ready to Fly); BNF (Bind and Fly –with custom transmitter); PNF (Plug and Fly with custom transmitter, receiver, battery, and charger). RTF and BNF – no prior flight experience required.
- Models most rotary multicopter – quad (4), hexa (6) octo (8) variants. Fixed wing used for deployments in agriculture, public safety, emergency response and ISR (Intelligence, Surveillance, and Reconnaissance) many fully customizable to achieve specific capabilities, flight time, payload capacity, programmable flight, maximum speed and weather hardening.
- Average SUAS flight time 18 minutes, average range approximately one mile, cost $600 US, dry conditions” (Angelov, 2012)
Specifications affecting hostile UAS operations
- Payload capacity function (weight and size more than gimbal, camera, battery) LIDAR or infrared or experimental sensors require larger capacity and subject to easier detection.
- Range function (signal transmission, LOS, image relay distance, battery and power constraints).
- Weather Proofing function (limited operating conditions, mostly dry. Upgradable to near military grade to operate in extreme conditions) Retrofit to harden for weather is a trade-off for weight, cost, flight time and payload capacity unless no of rotors increases.
- Imaging function (available medium –high resolution cameras of > 12 megapixels, with still and video) Infrared and LIDAR installable.
- Automated and Programmable Pilot / Follow Me settings function (predetermined flight mission path based on GPS coordinates (Fly-by-wire). Some with Follow Me autopilot settings enable the SUAS to automatically follow the operator. (Angelov, 2012)
Airborne Sensing Systems
There are two technologies available for airborne sensing of other aircraft; cooperative and non-cooperative. Cooperative technologies receive radio signals from other aircraft’s onboard equipment. Two requirements for cooperative behavior. First ATC Transponder, which responds to ground-based secondary radar interrogations for air traffic control (ATC) usage. Traffic Alert Collision Avoidance System (TCAS) uses the same technology in FAA classes of airspace. Second is the Automatic Dependent Surveillance – Broadcast systems (ADS-B). ADS-B technology uses the Global Positioning System (GPS) or alternative navigational source to make broadcasts of its own aircraft position, velocity, and data required to avoid collisions. (Angelov, 2012) Table 9-9 shows typical sensor coordinate systems. The first three cooperate with each other, the latter five are non-cooperative technologies. (Angelov, 2012)
Table 9-9 Typical Sensor Coordinate Systems
Sensor Technology Coordinate System
Active interrogation of Mode A/C transponder Relative range, altitude
TCAS Relative range, altitude
ADS-B Latitude, longitude, altitude, velocity
Electro-Optical Bearing (azimuth and elevation)
Laser /LIDAR Relative range
Onboard radar Relative range, Bearing (azimuth & and elevation)
Ground-based radar Range and bearing from ground-reference
Acoustic Bearing
Sensor Parameters
Sensor technologies use standard parameters to provide a basis for comparison and ISR performance. Table 9-10 Standard Sensor Parameters shows the base set:
Table 9-10 Standard Sensor Parameters
Sensor Function
“Field of View Describes angular sector within sensor making measurements. Outside this field of view, sensor is blind.
Range Distance measured by sensor, within which some good probability of detection of targets
Update Rate Interval at which sensor provides measurements
Accuracy Uncertainty of position measurement – usually single dimension
Integrity Probability that measurement falls beyond some normal operation limit
Data Elements Cooperative sensors – specific data to enhance ISR platform, ex: trajectory, identity, intent” (Angelov, 2012)
SAA Critical Control Systems include circuitry to affect UAS movement, landing, control of direction, detection, and correction of the aircraft. Many of these functions are incorporated into a UAS Autopilot, if capable.
Autopilot
Table 9-11 shows the common components found in UAS autopilots. These provide the means for UAS to affect movement, control, communications, detection, emergency operations, battery, waypoint delivery, and payloads.
Table 9-11 Common components found in UAS autopilots
- “Main Program/Processor: processing sensor data & implementation
of control of UAV
- Magnetometer: measuring direction
- GPS: determine global position
- Airspeed/Altimeter: measure air speed & altitude
- UAV Wireless Communication: communicating with ground station
- Power System: provides power to UAV
- Inertial Measurement Unit: measures movement of UAV
- Boot Loader Reset Switch loads programs into main program board
- Actuators: receives commands from main processing board & moves control surfaces
- Manual Flight Control: overrides autopilot & gives control of UAV control surfaces to ground station” (Clothier R. R., 2011) (Boutros, 2015)
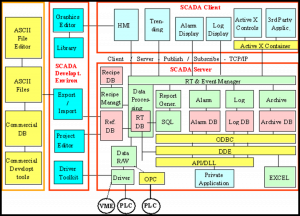
SCADA
The security fault “low hanging fruit” in UAS systems is SCADA. There are hundreds of millions of SCADA systems. They are used to control every practical machine you can imagine. SCADA stands for Supervisory Control and Data Acquisition. SCADA started in the 1940’s to control manufacturing processes such as flow rates, temperatures, valves, pressure, density, chemical, mechanical processes of all kinds. See Figure 9-14 for Legacy SCADA system for Chemical Plant. (Nichols R., Nov 28-30, 2006)
SCADA systems have improved significantly over the decades in all areas except one – SECURITY. SCADA systems are a security sieve. Figures 9-15 & 9-16 show examples of SCADA Architectures. (Nichols R., Nov 28-30, 2006) An interesting example are the automated/computerized systems in modern cars.
Figure 9-14 for Legacy SCADA system for Chemical Plant.
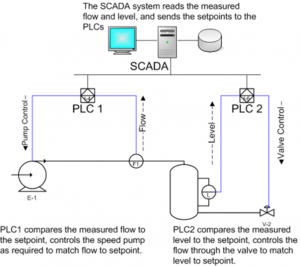
Source: (Nichols R. , Nov 28-30, 2006)
Everything is controlled by SCADA; tires, engine, seat belts, safety bags, oil pressure, even door locks. However, cyber hackers can exploit SCADA to disable a car remotely, with the driver still in it! Greenburg, Wired (2015). Hackers Remotely Kill a Jeep on the Highway—With Me in It. (Greenburg, 2015)
“UAS ARE JUST FLYING SCADA MACHINES!” (Nichols R.-0. , 2016) Table 9-12 SCADA shows the principle functions that apply to all SCADA systems, especially UAS.
Table 9-12 SCADA Functions
- Supervisory Control and Data Acquisition (SCADA) systems facilitate management with remote access to real-time data
- Channel to issue automated or operator-driven supervisory commands to remote station control devices
- A human–machine interface (HMI) is responsible for data presentation to human operator
- Composed by a console that makes it possible to monitor & control process
- Remote terminal units (RTUs) are microprocessor-controlled electronic devices that interface sensors to SCADA by transmitting telemetry data
- Is a process control system for computerized real-time monitoring and control
- Typically consists of:
- Master Control Unit (MCU)
- Remote Terminal Unit (s) (RTU)
- Communication Links
- Supervisory system is responsible for:
- Data acquisition
- Control activities on process
- Programmable logic controllers (PLCs) are final actuators used as field devices
- Communication infrastructure connecting supervisory system to RTUs
- Various process & analytical instrumentation
- RTU’s Alarm Systems
- Doors
- Battery Backup
- Low Power/Loss of Power Alarm
- Power Protection
- Passwords for Keypads, PC ports
- Log Alarm (or Event) When Local User Plugs PC in or Signs On
- Log Event when Local User Changes Values
Figure 9-15 UAS SCADA System Internals
Source: (Nichols R. K., Hardening US Unmanned Systems Against Enemy Counter Measures, 2019)
SCADA systems have plenty of cyber related vulnerabilities. Most are connected to computers. Those vulnerabilities multiply when connected to the Internet. SCADA systems differ from the IT structures. (Shapiro, 2006) Table 9-13 Sample SCADA Design Vulnerabilities apply to all systems including UAS. (Nichols R. , Nov 28-30, 2006)There are so many design flaws and vulnerabilities in SCADA systems that the US government has a special SCADA testing lab in Utah and has published copious recommendations to improve security. (NTSB, 2009)
Table 9-13 Examples of SCADA Design Vulnerabilities
- Ease of operation outweighs security
- Commonly set up on operating systems with known vulnerabilities
- Poor authentication systems in place
- Remote access allowed for maintenance &/or IT support
- Interconnectivity to vulnerable corporate networks
- Weak access control lists on firewalls
- Proper Network Access Control (NAC) is most crucial to prevent unauthorized connection within network
- First target of compromise for an attacker
- No use of standard IT defense software
- Wireless technology common
- System connect to unsecured remote processors
- SCADA software not designed with robust security features
- Public information often available on specific systems
- Poor physical security on remote access points
- No use of standard IT defense software
- Wireless technology common
- System connect to unsecured remote processors
- SCADA software not designed with robust security features
- Public information often available on specific systems
- Poor physical security on remote access points. (Kilman, 2003)
Attack Vectors
A brief overview of UAS Attack Vectors (by no means the exhaustive list) is demonstrated in Table 9-14. (Nichols R.-0. , 2016)
Table 9-14 Common Attack Vectors
“Common Vectors
- Backdoors & holes in network perimeter
- Protocol vulnerabilities
- Attacks on field devices through cyber means Database attacks
- Communications hijacking & Man-in-the-middle attacks
- Cinderella attack on time provision & synchronization
- Bogus input data to controller introduced by compromised sensors &/or exploited network link between controller & sensors
- Manipulated & misleading output data to actuators/reactors from controller due to tempered actors/reactors or compromised network link between controller & actuators
- Controller historian changes – feed forward control
- Distributed Denial of Service – missing deadlines of needed task actions
- Backdoors and holes in network perimeter
- Vulnerabilities in common protocols
- Attacks on field devices through cyber means
- Database attacks
- Communications hijacking and Man-in-the-middle attacks
- Cinderella attack on time provision and synchronization
- To a control engineer, possible attacks can be grouped into following categories:
- Bogus input data to controller introduced by compromised sensors and/or exploited network link between controller and sensors
- Manipulated and misleading output data to actuators/reactors from controller due to tempered actors/reactors or compromised network link between controller and actuators
- Controller historian
- Denial of Service – missing deadlines of needed task actions
Attacks on Software:
- No Privilege Separation in Embedded Operating System
- Buffer Overflow
- Structured Query Language Injection
Possible UAS Attack Hardware / Software
- SkyJack© [21]
- Aircrack-ng© [22]
- Node-ar-drone©
- Raspberry Pi©
- Parrot AR. Drone -2©
- Alfa© AWUS036H wireless adapter
- Edimax© EW-7811Un wireless adapter
- Snoopy© [23]
Attacks on Communication Stack
- Network Layer
- Transport Layer
- Application Layer
Auxiliary tools:
- Password Theft
- Wireshark
- Man-In-the-Middle Attacks
- Trojan Horse Virus
- Distributed Denial of Service Attacks” (Nichols R.-0. , 2016)
Cyber – Attack Taxonomy
UAS SCADA systems susceptible to a broad range of cyber and network specific attacks on the SAA modules in the aircraft and communication structures from the ground or satellite links. These represent system threats and vulnerabilities of the UAS structure, increasing the risk of hostile use or takeover. (Nichols R. , Nov 28-30, 2006)A UAS Cyber Attack Taxonomy is an organized view of potential cyber threats to UAS assets. The Taxonomy is a list of agents that increase risk of a successful attack on US UAS ADS assets. The risk of success of terrorist attacks on USA Air Defense Systems (ADS) via UASs is higher because of improving commercial capabilities and accessibility.
A qualitative view of information risk (also a measure of cyber-attack lethality) in a system such as SAA or computer network is expressed as:
Risk = (Threats x Vulnerabilities x Impact / Countermeasures) Equation 9-4
And at time state 0, this equation can be reduced to
Risk ~ function (Threats / Countermeasures) Equation 9-5
(Nichols R.-0. , 2016)[24]
At time state =0, where Vulnerabilities & Impact are constants and drop out of the equation.
Threats are real, and if applied in the absence of appropriate countermeasures, will increase the likelihood of a successful cyber-attack. Vulnerabilities are weaknesses in the system that a threat may or may not exploit. Vulnerabilities essentially in the system, ab initio. Threats can be mitigated or improved based on the attack circumstances. Impact is an after-the-fact accounting of the cyber-attack. No matter what the magnitude, it is a constant. Countermeasures are a host of technologies that can be applied to mitigate threats and reduce Risk. Increased Threats means increased Risk. Increased Countermeasures means decreased Risk. In practice, these equations require a qualitative legend to make comparable cases. Conversely, decreased threats means decreased Risk and decreased countermeasures means increased Risk. (Nichols R.-0. , 2016)Some authors use Vulnerabilities to assess Risk. (Garcia, 2006) Therefor our cyber-attack taxonomy must work for either Risk approach. There are many approaches to evaluating Risk. The authors choose the simplest approach to understand the attack vectors.
Software – Based Vulnerabilities
“Military UAS defense systems deploy widely used software in their network devices: Operating systems, open source software, routers, radio frequency devices, Internet Connection Sharing (ICS) and SAA SCADA.” (Sood A.K. & Enbody, 2014) UAS ground system network software may have the standard vulnerabilities; “hardcoded passwords, backdoors in firmware, insecure protocols, Remote Command Execution (RCE), default passwords for Human-Machine Interfaces (HMIs), Insecure authentication and authorization, malicious hardware, critical infrastructure systems have hardcoded passwords embedded in firmware which may allow attackers to gain complete access to system.” (Sood A.K. & Enbody, 2014) It doesn’t end there.
Other software-based vulnerabilities: “Backdoors exist for support or remote access purposes, Hardcoded passwords easily obtained by: Reverse engineering firmware, analyzing functional components,” (Sood A.K. & Enbody, 2014) Remote Code Execution (RCE) which is an attacker’s ability to execute attacker’s commands on target machine or target process remotely. Another RCE vulnerability is a software bug that gives attacker way to execute arbitrary code or ability to trigger arbitrary code execution from one machine on another. (Nichols R.-0. , 2016)
Unfortunately,” Remote Code Execution (RCE) can be triggered by exploiting security flaws in: Operating system components, browsers,” ICS, SCADA, routers, Microsoft Office, Adobe Reader, and Java. Remote Code Execution (RCE) is a powerful threat to UAS and supporting computer systems. “Attackers exploit security issues; buffer overflows (stack, heap, integer), use-after free errors, race conditions, memory corruption, privilege escalations and dangling pointers.”
Remote Code Execution (RCE) vulnerabilities keeps growing and RCE vulnerabilities allow “attackers to execute arbitrary code on compromised systems, drive-by downloads, spear phishing attacks.” (Sood A.K. & Enbody, 2014)
ICS/SCADA is particularly vulnerable to remote code execution vulnerabilities. Another form is SQL injections, “which exploits weaknesses in web applications to allow attackers’ queries to be executed directly in backend database” and allow attackers to extract sensitive information such as credentials, emails, critical documents, intelligence. “Data stolen using SQL injection can provide critical information for advanced UAS targeted attacks.” (Sood A.K. & Enbody, 2014)
The final group in the software- based vulnerabilities set is “insecure authentication and file uploading flaws. These allow remote attackers to access critical systems by exploiting weak authentication design and uploading malicious code or firmware. This security issue persists due to inability of systems to implement granular control through proper authentication and authorization checks. File uploading attacks exploit a system’s inability to determine type of files being uploaded on server.” (Sood A.K. & Enbody, 2014)
Hardware-based Vulnerabilities
The US sometimes picks the wrong vendors to supply its UAS critical hardware. Hardware imported from China includes backdoor access to hardware after deployment. “Exported Chinese manufacturing units compromised military-grade FPGA computer chips, circuits, and counterfeit devices, such as scanners.” “Zombie Zero malware has been implanted in software of scanner hardware manufactured in China as part of attack targeting shipping and logistics industries, especially printers. When scanners are connected to networks, they provide platforms for compromising networks. Counterfeit devices and circuits developed in China for U.S. military and defense contractors to be used in warships, missiles, airplanes and UAS.” (Sood A.K. & Enbody, 2014) (Threat to all nations that receive hardware pre-installed with malware.) (Nichols R.-0. , 2016)
“Hardware based vulnerabilities observed in actual attacks on military defense systems (Army) and applications include the following; backdoors and hardcoded passwords, compromised
GPS Satellite Communication (SATCOM) systems,” SCADA systems vulnerable to buffer overflows, and compromised GPS SATCOM systems. The Navy had its share of hardware-based threats; Remote Code Execution – “XMLDOM Zero-day vulnerability was exploited to attack U.S. Veterans of Foreign Wars’ website, SQL injections, Royal Navy website hacked, U.S. Army website hacked, insecure protocols, spoofing and hijacking and attacks to spoof GPS communication to control U.S. drones.” (Sood A.K. & Enbody, 2014)
Wireless attacks are the most generic form of hacking. “Strategies to compromise a system’s ability to be controlled by rightful owner include:
- Password Theft
- Wireshark
- Man-In-the-Middle Attacks
- Trojan Horse Virus
- Gain Scheduling Fuzzing,
- Digital Update Rate,
- Distributed Denial of Service,
- Buffer Overflow.”(Rani, 2015)
Forms of MIM attacks are:
- URL manipulation
- Rogue Domain Name Server
- Address Resolution Protocol poisoning
- Duplication of Media Access Control
- False Emails” (Rani, 2015)
Gain Scheduling attack methods Sensor spoofing to cause mode confusion,
- Overriding gains through hacking,
- Infinite switching between gains, will cause loss of control,
- Causing Denial of Service (DOS) between controller gain block, and UAS controller block by overloading the on-board processor.” (Kim, 2012)
Other possible Attacks on UAS Systems
- Autopilot Hardware Attack. (Kim, 2012)
- Wireless Attack. (Nichols R.-0., 2016)
- Control System Security. (Kim, 2012)
- Application Logic Security. (Nichols R.-0. , 20
Electronic Warfare (EW) – UAS Purview[25]
Warfare is conducted by adversaries who go to great pains to understand their enemy’s intentions, strengths, weaknesses, and to minimize the threats to their own forces and territory.
The detection and interception of messages/data, combined with ground observations, provide an ability to observe troop movements and facilitate counteractions by opposing forces. UAS plays a significant role in these missions.
Communication Links for UAS are critical and must be secured
Modern warfare is conducted in a rich electromagnetic environment with radio communications and radar signals from many sources. Unmanned aircraft systems (UAS) / UAV / UUV / Drones are an integral part of modern warfare. UAS communications networks and links to ground stations are critical to the successful military use of UAS. Securing UAS links from EW attacks is a fundamental concern to military planners and civilian authorities. UAS BLOS communications require stable communications. Disrupting these communications links is a goal of hostile forces.
The key role of EW is to search these radio-frequency bands to cull information that can be used for intelligence analysis or by front-line operators. The information gathered may affect a tactical advantage on the battlefield, or in any stage before or after. (Moir I. a., 2006)
Adamy (2001) is correct when he suggests that the, “key to understanding EW principles (particularly the RF) part is to understand radio propagation theory. Understanding propagation leads logically to understanding how they are intercepted, jammed or protected.” [26]
Main Contention
It is the author’s contention that UAS communication links are vulnerable and must be evaluated to protect US Unmanned Aircraft in the cyber or electronic domain. Further, those links may be electronically jammed, cyber-spoofed (especially navigational), or made ineffective with electronic or cyber or directed energy or acoustic interference.[27]
Communications Jamming -UAS
The purpose of communication is to move information from one location to another. All the following types of transmitted signals are communications:
- “Voice or non-voice communications (video or digital format)”;
- “Command signals to control remotely located assets;”
- “Data returned from remotely located equipment”;
- “Location and motion of friendly or enemy assets (land, sea, or air);”
- UAS communications links from it ground station for control of the aircraft;
- UAS communications links from another aircraft or satellite affecting its flying characteristics;
- UAS communication signals (from any source) that affect the SAA / navigation / payload / waypoints;
- Computer-to-computer communications;
- Data links;
- Weapon-firing links;
- ISR data links;
- Cell phones.
Figure 9-16 High -Level C4 Operational Concept Incorporating UAS
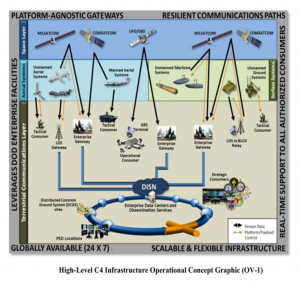
Source: (DoD-03, 2015)
“The purpose of communications jamming is to prevent the transfer of information. Communications jamming requirements depend on the signal modulation (strength), the geometry of the link, and the transmitted power.” (Adamy D. , 2009) Another way to think of jamming is a method to “interfere with the enemy’s use of the electromagnetic spectrum. Use of EMS involves the transmission of information from one point to another”. (Adamy D. , 2009)
“The basic technique of jamming is to add an interfering signal,” along with the desired signal, into an enemy’s receiver. “Jamming becomes effective when the interfering signal is strong enough to overwhelm the desired signal.” This prevents the enemy from recovering the information from the desired signal. (Adamy D. , 2009) There are two possible methods for a successful jam: either the jamming signal is stronger than the desired “signal or the combined signals received have characteristics that prevented the processor from properly extracting the desired information.” (Adamy D. , 2009) A simple case of jamming unintentionally is when your AM news station (listening in the car) becomes overwhelmed by junk music. You can hear the beginning of the interference as noise, then the junk signal is strong, then as the car moves out of the area, the AM news station regains its status. (Adamy D. , 2009)
The cardinal rule of jamming is that you jam the receiver, NOT the transmitter. (Adamy D. , 2001)
“The primary difference between radar and communication jamming is in the geometry. Whereas a typical radar has both the transmitter and the associated receiver at the same location, a communication link, because its job is to take information from one location to another, always has its receiver in a different location from that of the transmitter.” (Adamy D. L., 2004)
Communication is often done using transceivers (each including both transmitter and receiver), but only the receiver at location B in the figure is jammed. If transceivers are in use and one desires to jam the link in the other direction, the jamming signal must reach location A.” (Adamy D. L., 2004)
Another difference of radar jamming is that the radar signal makes a round trip to the target, so the received signal power is below the transmitted power by the fourth power of the distance (often stated as 40 log range). Since the jammer power is transmitted one way, it is only reduced by the square of distance.” (Adamy D. L., 2004) Table 9-15 shows the Types of Jamming. (Adamy D. , 2001)
To be effective, the jammer must get its signal into the enemy’s receiver – through the associated antenna, input filters, and processing gates. This depends on the signal strength the jammer transmits in the direction of the receiver and the distance and propagation conditions between the jammer and the receiver. (Adamy D. , 2009)
Table 9-15 Types of Jamming
| Type of Jamming | Purpose
|
| Communications jamming | Interferes with enemy ability to pass information over a communication link
|
| Radar jamming | Causes radar to fail to acquire its target, to stop tracking target, or to output false information
|
| Cover jamming | Reduces the quality of the desired signal so that it cannot be properly processed, or the info is lost / unrecoverable |
| Deceptive jamming | Causes radar to improperly process its return signal to indicate the correct range or angle to target
|
| Decoy | Looks like the target more than the actual target; causes a guided weapon to attack the decoy rather than intended target
|
Source: (Adamy D. , 2001)
Jammer-to-Signal Ratio
The real test of jammer effectiveness is the effectiveness with which information flow is stopped. “A jammer interferes with communication by injecting an undesired signal into the target, receiver along with any desired signals that are being received.” (Adamy D. , 2009) “The obstructing signal must be strong enough that the receiver cannot recover the required information from the desired signals.” The ratio of the jamming signal to the desired signal is known as the jamming–to-signal ratio (J/S), stated in dB.[28] Effective J/S depends on the transmitted modulation, but the Adamy formula works in general. (Adamy D. , 2001)
The formula for communication J/S is:
J / S = ERPJ – ERPS – LJ + LS + G RJ – G R Equation 9-6
Where: J/S = the ratio of the jammer power to the desired signal power at the input to the receiver being jammed in dB
ERPJ the effective radiated power of the jammer in dBm
ERPS the effective radiated power of the desired signal transmitter, in dBm
LJ the propagation loss from jammer to receiver, in dBi[29]
LS The propagation loss from the desired signal transmitter, in dBm
GRJ the receiving antenna gain in the direction of the jammer, in dBi
GR The receiving antenna gain in the direction of the desired signal transmitter, in dBi.” (Adamy D. , 2001)
Many UAS (especially UAV or sUAS ) have a target receiving antenna with a 360-degree azimuth coverage. They use whips or monopoles. They are inexpensive. With a 360-degree antenna, the communications J/S equation simplifies to:
J / S = ERPJ – ERPS – LJ + LS Equation 9-7
The receiving antenna has the same gain toward the jammer and the desired signal transmitter. The two gain terms cancel out. (Adamy D. , 2009)
A J /S calculation would indicate a successful jam when the desired signal fully compromised. (Adamy D. , 2001) The terminology is slightly different for the power terms (removing the “effective radiated” and using “power total” instead). The principle is still the same. (Adamy D. , 2009) See Appendix 9-3 for example J/S calculation.
US Army Field Manual FM 34-40-7 (23 Nov 1992) Communications Jamming Handbook, presents three alternative methods for calculating the jamming power required and distance to target. For the designer of an anti-UAS Drone gun, (Figure 9-17) which transmits a jammer signal to a UAS to overwhelm the desired ground station command signals, one needs the know the power and height of the drone. Since the drone is moving the jammer signal must radiate in such a manner that it covers a volume of space until target “UAS lock.”
Drone gun – Chinese alternative
A Chinese firm makes an anti-drone gun that costs about $35,000 USD and operates on 5.8 GHz and 2.4 GHz.[30] 80% of consumer drones operate on these frequencies. “The gun tricks the drone into thinking it has lost connection with its controller.” “RC signal lost” is flashed on drone screen – aircraft returning to home point.” The drone can be recovered intact. This gun has an operational limit of about 700 meters (0.43496 miles).
Figure 9-17 Drone Jammer Model KWT-FZQ.

Source: Tri-band Anti Drone Rifle KWT-FZQ/DG10-A
Manufacturer: Globaldroneuav.com https://globaldroneuav.com/Product/Police-drone-jammer-effective-drone-controller.html Appendix 9-1 details this anti-drone gun.[31]
Calculating the minimum of “amount of jammer power output required in watts” for this easy drone capture would be of interest. (Army, 1992) Appendix 9-4 of FM 34-70 (Army, 1992)gives a slightly different version of the Adamy equation 9-5:
P j = P t x K x (H t / H j )2 x (D j / D t )N Equation 9-8
Where:
P j = Minimum amount of jammer power output required , in watts
P t = Power output of the enemy drone, in watts
H j = Elevation of the jammer location above sea level, feet
H t = Elevation of enemy transmitter location above sea level, in feet
D j = Jammer location – to-target receiver location distance, in km
D t = Enemy transmitter location -to- target receiver location, in km
K = 2 for jamming frequency modulated receivers (jamming tuner accuracy)
N = Terrain and ground conductivity factors
5 = very rough terrain with poor ground conductivity
4 = Moderately rough terrain with fair to good ground conductivity
3 = Farmland terrain with good ground conductivity
2 = Level terrain with good ground conductivity
F = Frequency in MHz (Army, 1992)
“Note: The elevation of the jammer location and the enemy transmitter location does not include the height or length of the antenna above the ground. (Army, 1992) It is the location deviation above sea level.
Given the following parameters:
P j = Minimum amount of jammer power output required , in watts = (SOLVE)
P t = Power output of the enemy transmitter -to drone, in watts = 5 watts
H j = Elevation of the jammer location above sea level, feet, use 385m =.385 km
H t = Elevation of enemy transmitter location above sea level, in feet use 386m =.386 km
D j = Jammer location – to-target receiver location distance, in km = 700 m = 0.700 km
D t = Enemy transmitter location -to- target receiver location, in km = 372m = 0.372 km
K = 2 for jamming frequency modulated receivers (jamming tuner accuracy) = 2
N = Terrain and ground conductivity factor = Use 4 for moderate terrain with fair to good ground conductivity (Army, 1992)
F = Frequency in MHz, use 37.5 MHz in the band
Parameters were chosen so that the height ratio would drop-out and the distance would induce some ground conductivity effects consistent with the FM 34-40-7 examples.
Plugging the numbers and solving for P:
P j = 5 x 2 x (1)2 x (0.7 / 0.372)4 = 10 x (1.88) 4 = 10 x 12.46 = 125 watts
So, under these hypothetical conditions the jammer gun requires 125 watts (2 60-watt light bulbs) to take down the drone. Theoretically, if the jammer was using a log periodic array (LPA) the power could be cut in half to 62.5 watts (1 bulb). Now if this calculation is reasonable, the buyer is spending $35,000 USD to take down a small irritating drone (invasion of privacy) using a 60-watt bulb. A double-aught shotgun shell with a 12-gauge Remington and yellow shooter sunglasses will have the same effect (might even be more satisfying) for 1/100 the cost. The medium size drones present a more interesting case. More power is needed to lock on to the higher altitude UAS. The term of interest in the jamming equation from FM 34-40 -7 is the ratio of the distances to the fourth power (or second power for perfect terrain). That can have a major impact on jammer output power. (Army, 1992)
Radar Range Equation
Equation 9-9 is not the only place we see a term taken to the 4th power. The famous “Radar Range Equation is dominated by the R4 factor in the denominator. There is no corresponding function in the numerator of equation 9-9, with an exponent greater than unity. (Toomay, 1982) There is no magic bullet to achieve a high-performance system. If low cross section targets are to be engaged, a combination of high-power, high gain, large aperture, and low noise needs to be dictated.” (Toomay, 1982)
The standard Radar Range Equation (RRE) is:
S / N = (P GTArσ ) / [(4π)2 R4 KTS LS ] Equation 9-9
Where:
S / N = is one pulse received signal to noise ratio, dB
P = Isotropic source of an electromagnetic pulse of peak power, Mw
GT = Gain of the transmit antenna, dB
Ar = Receive antenna effective area, m2
σ = Radar Cross Sectional Area, m2
R4 = Energy density received at detected target range, R, nm
K = Boltzmann’s constant (Noise component)
TS = Measured noise temperature, Kelvin units above absolute zero
LS = Losses existing in the system (lumped together), dB
Inherent in equation 9-9, is the fact that the range of the radar to a “detected object can be calculated by: R = ct / 2, where c is the speed of light (3 x 108 m/s) x time , in sec. also, λ = c / f, where λ is the wavelength in Hz, and frequency, f is the cycles/second for the sinusoidal oscillator.” (Toomay, 1982)
The point of this diversion into Radar history was that the performance of both the jamming equation and the radar range equation are affected by a power of 4th exponent. This affects equipment design, cost, effectiveness of detection or capture.
“The principles of a primitive radar are formed. Figure 9-18 diagrams its functions. A burst of electromagnetic energy, oscillating at a predetermined frequency is generated and radiates into free space from an antenna. A clock is started. The electromagnetic energy propagates outward at the speed of light, reradiating (scattering) from objects it encounters along its path. Part of the scattered energy returns to the radar (is received) and can be detected there because it imitates the frequency and duration of the transmitted pulse.” (Toomay, 1982)
Figure 9-19 shows a simple surveillance RADAR. Compare this to 2019 version in Figure 9-20 which requires computer simulations to sort out the parameters.
Figure 9-18 Simple Radar Block Diagram
Source: Simple Radar PPTX by Linkedin SlideShare (2018) https://www.slideshare.net/remotesensor1/radar-transmitter-4-1
A full derivation of all the terms, the radar spherical geometry and derivations of subset equations are in all legacy and modern radar texts and papers.
Figure 9-19 Simple Surveillance Radar
Source: Encyclopedia Britannica, (1994)
Complex RADAR / RES Simulations
Figure 9-20 shows that RADARS can be quite complex. They lend themselves to computer simulation to determine optimum parameters for a variety of systems.
Advancement of computer technologies and computer networks opens the possibilities of effective modeling of progressively sophisticated electronics. Nowadays, the time spent on the procedures of modeling complex radio electronic systems (RES) has been tangibly shortened. The shortened time spent on computation and steadily promoted adequacy of computer models to real systems and waveforms make it possible to transform the process of designing sophisticated systems (radars, air defense missile systems, their components and subsystems) based on modeling. Information circulates about real facts of full-scale designing of large-size aerial vehicles using adequate computer models.
Objects of modeling:
- RES with easily changeable structure and parameters;
- various signals circulating in radio electronic systems and in air;
- objects controlling such systems, for example, missiles in the process of guidance;
- influence of physical factors on quality and parameters of the processes described (ambient temperature, humidity, pressure, influence of the atmosphere on propagation of radio waves, etc.).
Computer modeling radically simplifies and saves time expenditure on developing complex RES, considerably alleviates the designer’s qualification requirements, minimizes physical modeling and financial costs.
They are used for:
- optimization of the structure and parameters of newly developed radars, ADMS, EW assets;
- analysis of effectiveness of operation of Radars (ADMS), EW assets in complex jamming environments, facing the use of intensive maneuvers by the targets, etc.;
- researching the principal operational and technical characteristics of radars, ADMS, EW assets (detection envelope, kill envelope, tracking accuracy, etc.)
ADMS computer modeling systems are designed for:
- analysis of the processes of target detection and tracking in surveillance radars
- analysis of the processes of detection, reception of targeting, detection and acquisition of targets (lock-on) by tracking radars;
- analysis of the process of target lock-on and tracking by an air defense missile (SAM);
- analysis of the process of missile flight, collision with target, warhead detonation and effectiveness of the kill;
- selection and substantiation of the ADMS structure and parameters.
The modeling system comprises:
- models of the detection radar;
- models of the tracking radar;
- models of the missile motion;
- models of the missile signal;
- models of influence of the atmosphere on propagation of radio waves;
- models of motion of the target(s);
- models of target echoes;
- models of clutters induces by volume- and surface-distributed reflectors;
- models of jamming;
- models of multipath caused by influence of the Earth;
- models of the atmosphere.
Figure 9-20 Computer modeling of sophisticated radio electronic systems
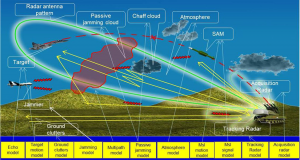
Source: (radiotechnika – Republic of Belarus, 2019)
Conclusions
UAS are vulnerable to a variety of non-kinetic defenses, to wit: IO, cyber, EW, and as we shall see next chapter, acoustic. UAS are also vulnerable to DE weapons[32] UAS avionics is a prime target for both cyber and EW C-UAS defenses. SAA and SCADA systems are most susceptible to cyber-attacks.
Discussion Question
- There is a closely related science that intersects with EW and that is Cyber. There are distinct parallels and intersections between Cyber and EW. For instance, the sister of signal spreading techniques is encryption. See Figure 9-21 showing the intersection of Cyber, EW, and Spectrum Warfare designated as Cyber Electromagnetic Activities (CEA)[33] [34] [35] [36] The reader will research all major C-UAS intersections viewed in Figure 9-21 and provide examples.
Figure 9-21 Cyber Electromagnetic Activities
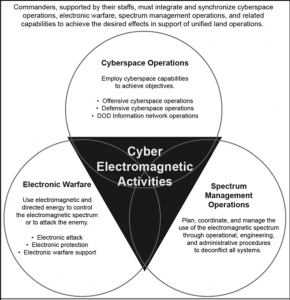
Source: FM 3- 38 (2014)
References
Adamy, D. -0. (2015). EW 104 EW against a New Generation of Threats. Boston: Artech House.
Adamy, D. (2001). EW 101 A First Course in Electronic Warfare. Boston, MA: Artech House.
Adamy, D. (2009). EW 103 Tactical Battlefield Communications Electronic Warfare. Boston, MA: Artech House.
Adamy, D. L. (2004). EW 102 A Second Course in Electronic Warfare. Boston: Artech House.
Adamy, D.-9. (1998, Jan). Lesson 4: the basic link for all EW functions. (electronic warfare)(EW Reference & Source Guide). Journal of Electronic Defense, Jan 1998 Issue.
Administrator. (2015, June 15). Standing Wave and Fundamental Frequency. Retrieved from Electronics Hub: https://www.electronicshub.org/?s=fundamental+frequency
Alford, L. (2000). Cyber Warfare: Protecting Military Systems. Acquisition Review Quarterly.
Angelov, P. (2012). Sense and avoid in UAS research and applications. Hoboken: NJ.
Army, U. (1992, November 23). US Army Field Manual FM 34-40-7. Communications Jamming Handbook.
Austin, R. (2010). “Design for Stealth”, Unmanned Aircraft Systems UAVS Design Development and Deployment. New York: John Wiley and Sons.
Barker, W. (2003, August). SP 800-59 Guidelines for Identifying an Information System as a National Security System. Retrieved from NIST: https://csrc.nist.gov/publications/detail/sp/800-59/final
Barnhart, R. K. (2012). Introduction to Unmanned Aircraft Systems. New York: CRC Press.
Beason, D. (2005). The E-Bomb: How America’s new directed energy weapons will change the way future wars will be fought. Cambridge, MA: Da Capo Press.
Beaudoin, L. e. (2011). Potential Threats of UAS Swarms and the Countermeasures Need. ECIW.
Boutros, D. (2015, May 15). US Navy War College. Retrieved from Operational Protection from Unmanned Aerial Systems: http://www.dtic.mil/dtic/tr/fulltext/u2/a621067.pdf
Brenner, J. (2011). America the Vulnerable: Inside the New Threat Matrix of Digital Espionage, Crime, and Warfare. New York: Pilgrim Press.
Burch, D. (2015). RADAR for Mariners. New York: McGraw-Hill.
C4ISystems. (2013). basics-of-information-operations. Retrieved from Blogspot: http://c4isys.blogspot.com/2013/11/basics-of-information-operations-24.html
Carter, A. (2012, May 24). EEWeb. Retrieved from The Sound Intensity: https://www.eeweb.com/profile/andrew-carter/articles/the-sound-intensity
Chairman, U. (2012, March 23). Countering Air and Missile Threats, final coordination, JP 3-01. CJCS.
Clothier, R. (2017, April 02). The Smart Skies Project: Enabling Technologies for UAS Operations in Non-segregated Airspace. Retrieved from QUT ePrints: http://eprints.qut.edu.au/40465/3/40465.pdf
Clothier, R. F. (2010). The Smart Skies Project: Enabling technologies for future airspace. . Clothier, R.A., Frousheger, D., Wilson, M., (2010). The Smart Skies Project: Enabling technologies for future airspace. Australian Research Center for Aerospace Automation, Commonwealth Scientific and Industrial Research Organization, Boeing Research an. Australian Research Center for Aerospace Automation, Commonwealth Scientific and Industrial Research Organization.
Clothier, R. R. (2011). The Smart Skies project. IEEE Aerospace and Electronic Systems Magazine.
DAU. (2018, July 2). Cyber Tabletop Guidebook. Retrieved from DOD / DAU: https://www.dau.mil/cop/test/_layouts/15/WopiFrame.aspx?sourcedoc=/cop/test/DAU%20Sponsored%20Documents/The%20DoD%20Cyber%20Table%20Top%20Guidebook%20v1.pdf&action=default&DefaultItemOpen=1
Defence, P. (2014, May 7). China’s Pterodactyl drone. Retrieved from defence.pk: https://defence.pk/pdf/threads/saudi-arabia-signs-deal-for-chinas-pterodactyl-drone.312761/
DoD. (2018). Dictionary of Military Terms. Retrieved from JCS.Mil: http://www.jcs.mil/doctrine/dod_dictionary/
DoD-01. (2018). JP 1-02. Retrieved from Department of Defense Dictionary of Military and Associated Terms: www.dtic.mil/doctrine/new_pubs/jp1_02.pdf
DoD-02. (2018). Information Operations (IO) in the United States. Retrieved from JP 3-13 : http://www.dtic.mil/doctrine/new_pubs/jp3_13.pdf
DoD-03. (2015). Unmanned Systems Roadmap 2013 to 2038. Retrieved from DTIC: http://www.dtic.mil/dtic/tr/fulltext/u2/a592015.pdf
Drones, Q. S. (2017, July 11). quadcopters-have-hit-the-sound-barrier/. Retrieved from quadstardrones.com: https://quadstardrones.com/2017/07/11/quadcopters-have-hit-the-sound-barrier/
DTRA. (2019, October 18). Private Communication re Aviation Vulnerabilities. (Nichols, Interviewer) Retrieved from https://www.dtra.mil/
Editor. (2012, April 22). RT Question More. Retrieved from Iran starts cloning of American spy drone: https://www.rt.com/news/iran-spy-drone-copy-667/
EIA. (2019, June 20). The Strait of Hormuz is the world’s most important oil transit chokepoint. Retrieved from EIA – US Energy Information Administration: https://www.eia.gov/todayinenergy/detail.php?id=39932
Entokey, a. G. (2019, May 16). entokey.com/acoustics-and-sound-measurement/. Retrieved from entokey.com/acoustics-and-sound-measurement/: https://entokey.com/acoustics-and-sound-measurement/
Eshel, T. (2019, September 14). AFRL to Test a Drone-Swarm Killer HPM. Retrieved from Defense Update: https://defense-update.com/20190923_hpm.html
FAA. (2018, February 1). Part 107 Rule for sUAS. Retrieved from Fly under the Special Rule for Model Aircraft: https://www.faa.gov/uas/getting_started/model_aircraft/
Filbert, F. &. (2014, (July – August). Joint Counter Low, Slow, Small Unmanned Aircraft Systems Test. Fires PB644-14, no 4. Washington: DoD.
Fitts, R. (1980). The Strategy of Electromagnetic Conflict. Los Altos, CA: Peninsula Publishing.
Foley, W. S. (March, 1979). Ancient Catapults. Scientific American, 240, 150.
Gallagher, S. (2019, September 16). Missiles and drones that hit Saudi oil fields: Made in Iran, but fired by whom? Retrieved from Arstechnica.com: https://arstechnica.com/tech-policy/2019/09/missiles-and-drones-that-hit-saudi-oil-fields-made-in-iran-but-fired-by-whom/
Garcia, M. (2006). Vulnerability Assessment of Physical Protection Systems. Albuquerque: Sandia National Laboratories,BH.
Gelfand. (2004). “Physical Concepts”, Hearing an Introduction to Psychological and Physiological Acoustics, 4th ed. New York City.
Gelfand, S. A. (2009). Essentials of Audiology, 3rd Edition. Stuttgart, DE: Thieme.
Glasstone, S. &. (1977). The Effects of Nuclear Weapons, 3rd Edition. In S. &. Glasstone, Chapter V, Figures 5.20, 5.22 & 5.23. Washington, DC : UGPO.
Greenburg, H. (2015). Hackers Remotely Kill a Jeep on the Highway—With Me in It. Retrieved from Wired : https://www.wired.com/2015/07/hackers-remotely-kill-jeep-highway/
Halsam, C. M.-S. (1982). Small Arms and Cannons. Oxford: Brassey’s Publishers.
Hartman, K. a. (2013). The Vulnerability of UAVs to Cyber Attacks – An Approach to the Risk Assessment. 2013 5th International Conference on Cyber Conflict . Tallin: NATO CCD COE Publications.
Horowitz, M. C. (2014). Droning On: Explaining the Proliferation of Unmanned Aerial Vehicles. University of Pennsylvania and Texas A&M Universities. University of Pennsylvania and Texas A&M Universities.
Howard, C. (2019, June 21). What is the Strait of Hormuz, where Iran shot down US Navy drone? Retrieved from Fox News: https://www.foxnews.com/world/whats-the-strait-of-hormuz-iran-shot-us-navy-drone
Hubbard, R. K. (1998). Boater’s Bowditch. Camden, MA: International Marine.
Kania, E. (2017, July 6). Swarms at War: Chinese Advances in Swarm Intelligence. China Brief Volume: 17 Issue 9. China Brief Volume: 17 Issue 9.
Kaye, T. a. (2001, September 30). ACHIEVING INFORMATION DOMINANCE:. Retrieved from DODCCRP-Space and Naval Warfare Systems Center San Diego: http://www.dodccrp.org/events/2002_CCRTS/Tracks/pdf/026.PDF
Kilman, D. &. (2003). Framework for SCADA Security Policy. Albuquerque, NM: Sandia National Laboratories. Retrieved from Energy.gov: https://www.energy.gov/sites/prod/files/Framework%20for%20SCADA%20Security%20Policy.pdf
Kim, A. G. (2012, June). Cyber Attack Vulnerabilities Analysis for Unmanned Aerial Vehicles. Retrieved from Infotech@Aerospace.com: https://www.researchgate.net/publication/268571174_Cyber_Attack_Vulnerabilities_Analysis_for_Unmanned_Aerial_Vehicles
Kirk, J. (2015, August 5). sounds-can-knock-drones-sky. Retrieved from www.computerworld.com.au/article/581231: https://www.computerworld.com.au/article/581231/sounds-can-knock-drones-sky/
Lister, T. (2019, September 16). Attack is a game-changer in Gulf confrontation. Retrieved from CNN: https://www.cnn.com/middleeast/live-news/saudi-oil-attack-dle-intl/h_3e647100fa720927c962d7643472b12d
Liteye. (2018, August 25). AUDS. Retrieved from Liteye Corporation: http://liteye.com/products/counter-uas/auds/
LRAD. (2019, May 189). LRAD 450XL Datasheet. Retrieved from LRADX: http://www.lradx.com/wp-context/uploads/2015/05/LRAD_datasheet_450XL.pdf
LRAD Corporation. (2019, October 18). Product sheet LRADS 1000x. Retrieved from LRAD Corporation : https://lradx.com/lrad_products/lrad-1000xi/
Marshall, D. M. (2016). Introduction to Unmanned Aircraft Systems, 2nd Edition. New York: CRC Press.
Merriam-Webster. (2019, May 17). Merriam-Webster Online Dictionary.
Merrick, K. (2016). Future Internet. 10.3390/fi8030034 Review, 8(3), p. 34.
Military & Aerospace Electronics. (2019, October 14). Air Force researchers to test high-power microwave weapon to destroy or disable swarms of unmanned aircraft. Retrieved from Military & Aerospace Electronics: https://www.militaryaerospace.com/unmanned/article/14068535/high-power-microwave-unmanned-aerial-vehicle-uav-swarms
Moir, I. &. (2006). Military Avionics Systems. New York City, NY: Wiley.
Moir, I. a. (2006). Military Avionics Systems. New York: Wiley Aerospace Series.
Monahan, K. (2004). The Radar Book: Effective Navigation and Collision Avoidance. Anacortes, WA: Fineedge Publications.
MORS. (2018). Military Operations Research Society . Retrieved from http://www.mors.org/meetings/oa_definition.htm
Myer, G. (2013, May-June). Danger Close Definition. Retrieved from US Army Magazine: www.benning.army.mil/infantry/magazine/issues/2013/May-June/Myer.html
NASA. (2018). Unmanned Aircraft Systems (UAS) Integration in the National Airspace System (NAS) Project. Retrieved from NASA: https://www.nasa.gov/feature/autonomous-systems
Naval Technology Team. (2019, June 11). feature-the-top-10-maritime-patrol-aircraft/. Retrieved from https://www.naval-technology.com: https://www.naval-technology.com/features/feature-the-top-10-maritime-patrol-aircraft/
Naval Technology Team. (2019, October 18). MQ-4C Triton Broad Area Maritime Surveillance (BAMS) UAS. Retrieved from Naval Technology: https://www.naval-technology.com/projects/mq-4c-triton-bams-uas-us/
Nichols, R. K. (1996). Classical Cryptography Course, Volume I. Laguna Hills, CA: Aegean Park Press.
Nichols, R. K. (2008, September 05). Counterintelligence & Sensitive Compartmented Information Facility . (SCIF) Needs – Talking Points.
Nichols, R. K. (2019, March 14). Hardening US Unmanned Systems Against Enemy Counter Measures. 7th Annual Unmanned Systems Summit. Alexandria, VA, USA: PPTX presentation , self.
Nichols, R. K., Mumm, H. C., Lonstein, W. D., Ryan, J. J., Carter, C., & and Hood, J.-P. (2019). Unmanned Aircraft Systems in the Cyber Domain, 2nd Edition. Manhattan, KS: NPP eBooks. 27. Retrieved from www.newprairiepress.org/ebooks/27
Nichols, R. (Nov 28-30, 2006). Cyber Terrorism, Critical Infrastructure, & SCADA Presentation. In R. Nichols (Ed.), Defense Threat Reduction Agency Conference. Shirlington VA: Utica College, Utica NY.
Nichols, R.-0. (2016, March 29). NCIE UAS SAA Final Rev 4. 2016 INFOWARCON conference presentation April 4-7, Nichols, R.K. et. al. (3-29-2016) Presentation to INFOWARCON April 4-7 on NCIE UAS SAA Final Rev 4, presented to 2016 INFOWARCON conference, Memphis TN. Available as PPTx presentation download from author or in CANVAS. Memphis, TN, USA: INFOWARCON16.
Nielsen, P. E. (2012). Effects of Directed Energy Weapons. Middletown, DE: CreateSpace Independent Publishing Platform.
NTSB. (2009, September 16). National SCADA testbed Documents and Media. Retrieved from National SCADA Testbed Fact Sheet: https://www.energy.gov/sites/prod/files/oeprod/DocumentsandMedia/NSTB_Fact_Sheet_FINAL_09-16-09.pdf
Osborn, K. (2019, October 15). Swarm Hell: Can the U.S. Army Stop Hundreds of Drones Armed with Explosives? Retrieved from National Interest: https://nationalinterest.org/blog/buzz/swarm-hell-can-us-army-stop-hundreds-drones-armed-explosives-88206
Pettit, R. (1982). ECM and ECCM Techniques for Digital Communication Systems. Belmont, CA: Lifetime Learning Publications .
Pierson. (2019, May 16). tuning-fork-waves-sound. Retrieved from airfreshener.club – Pierson Education: https://airfreshener.club/quotes/tuning-fork-waves-sound.html
radiotechnika – Republic of Belarus. (2019, October 20). Computer modeling of sophisticated radio electronic systems. Retrieved from http://radiotechnika.by/: http://radiotechnika.by/en/products/radar/computer_model_difficult_systems/
Randall K. Nichols, D. J. (2000). Defending Your Digital Assets against Hackers, Crackers, Spies and Thieves. New York: RSA Press.
Rani, C. M. (2015). Security of unmanned aerial vehicle systems against cyber-physical attacks. The Journal of Defense Modeling and Simulation: Applications, Methodology, Technology.
Raytheon. (2019, October 23). Raytheon announces delivery of first laser counter-UAS system to U.S. Air Force. Retrieved from Defense Blog: https://defence-blog.com/news/raytheon-announces-delivery-of-first-laser-counter-uas-system-to-u-s-air-force.html
Rogoway, T. (2018, September 5). Global Hawk. Retrieved from www.thedrive.com: https://www.thedrive.com/the-war-zone/23383/exclusive-u-s-air-force-rq-4-global-hawk-drone-crashed-off-spain-last-june
Said Emre Alper, Y. T. (December 2008). A Compact Angular Rate Sensor System Using a Fully Decoupled Silicon-on-Glass MEMS Gyroscope. JOURNAL OF MICROELECTROMECHANICAL SYSTEMS, VOL. 17, NO. 6.
Shapiro, J. (2006, February 14). Slideplayer.com. Retrieved from Cybersecurity: http://slideplayer.com/slide/4545982/
Sheena McKenzie, M. W. (2019, September 17). Saudi attacks send oil prices soaring. Retrieved from CNN: https://www.cnn.com/middleeast/live-news/saudi-oil-attack-dle-intl/h_1ab7e8469e98525f887c3a4e588dde8a
Singer, P. W. (2010, February 25). Will Foreign Drones One Day attack the US? . Newsweek.
Sood A.K. & Enbody, R. (2014, December 19). https://www.georgetownjournalofinternau-s-military-defense-systems-the-anatomy-of-cyber-espionage-by-chinese-hackers. Retrieved from georgetownjournalofinternationalaffairs.org/online-edition: https://www.georgetownjournalofinternationalaffairs.org/online-edition/u-s-military-defense-systems-the-anatomy-of-cyber-espionage-by-chinese-hackers
Stratfor. (2019, October 20). strait-of-hormuz-chokepoints. Retrieved from https://www.stratfor.com: https://www.stratfor.com/sites/default/files/styles/wv_small/public/strait-of-hormuz-chokepoints.jpg?itok=xSgx6Hhi
Studios, D. D. (2017). Boaters Ref. USA.
Toomay, J. (1982). RADAR for the Non – Specialist. London; Lifetime Learning Publications. London: Lifetime Learning Publications.
TRS, S. (2018, July 10). Tontechnic-Rechner-Sengpielaudio. Retrieved from Tontechnic-Rechner-Sengpielaudio Calculator: www.sengspielaudio.com/calculator-wavelength.htm
Uni-wuppertal. (2019, May 15). Inverse Square Law, General. Retrieved from hydrogen.physik.uni-wuppertal.de/hyperphysics/: http://hydrogen.physik.uni-wuppertal.de/hyperphysics/hyperphysics/hbase/forces/isq.html
Usenix.org. (2019, 6 9). MEMS, Drones, & Sound Sourcing. Retrieved from Usenix.org: www.usenix.org
Vernard Foley, G. P. (January, 1985). The Crossbow. Scientific American, 252, 104.
Weise, E. (2017, August 23). could-hackers-behind-u-s-navy-collisions. Retrieved from USATODAY: https://www.ruidosonews.com/story/tech/news/2017/08/23/could-hackers-behind-u-s-navy-collisions/594107001/
Wikipedia. (2018, August 26). Human Hearing Range. Retrieved from Wikipedia: https://en.wikipedia.org/wiki/Hearing_range
Wiley, R. G. (1993). Electronic Intelligence: The Analysis of Radar Signals, 2nd ed. Norwood, MA: Artech House.
Wilson, M. (2012). The Use of Low-Cost Mobile Radar Systems for Small UAS Sense and Avoid. Sense and Avoid in UAS Research and Applications.
Yan. (2017, December 23). China’s commercial drone market to top 9 bln USD by 2020. Retrieved from Xinhuanet: http://www.xinhuanet.com/english/2017-12/23/c_136847826.htm
Yu, X. &. (2015). Sense and avoid technologies with applications to unmanned aircraft systems: Review and prospects. Progress in Aerospace Sciences, 74, 152-166.
Yunmonk Son, H. S. (2015, August 12-14). Rocking Drones with Intentional Sound Noise on Gyroscopic Sensors. Proc. 24th Usenix Security Symposium. Washington, DC: USENIX. Retrieved from https://www.usenix.org/conference/usenixsecurity15/technical-sessions/presentation/son
Zaharia, M. D. (2012). Discretized Streams: An Efficient and Fault-Tolerant Model for. Retrieved from UNIX Org: https://www.usenix.org/system/files/conference/hotcloud12/hotcloud12-final28.pdf
Zwijnwenburg, W. (2014, October 8). ZwijnwenbDrone-tocracy? Mapping the Proliferation of Unmanned Systems. Retrieved from Sustainable Security.org.
Appendix 9-1 Tri-band Anti Drone Rifle KWT-FZQ/DG10-A[37]
Source: (LRAD Corporation, 2019)
Manufacturer: Globaldroneuav.com https://globaldroneuav.com/Product/Police-drone-jammer-effective-drone-controller.html
Functions and features
- Full range cover within three frequency section and high-power transmission helps to achieve the ideal effects.
- Fast trigger, easy use and daughter switch design make control more ease and comfort.
- Dual lithium batteries for power supply last work time longer.
- The strong internal line connector and external fuses port make the whole vehicle and component parts fastened securely.
- All aluminum alloy case body design and glass fiber material for antenna cover make its appearance lighter and faster.
ce dimension :(mm)L×W×H;1323mm×403mm×341 mm
Weight(Kg):4.7kg±0.2kg(mainframe + battery)
0.6kg±0.1kg(sighting telescope)
Source: Tri-band Anti Drone Rifle KWT-FZQ/DG10-A
Manufacturer: Globaldroneuav.com https://globaldroneuav.com/Product/Police-drone-jammer-effective-drone-controller.html
Appearance dimension :(mm)L×W×H;1323mm×403mm×341 mm
Weight(Kg):4.7kg±0.2kg(mainframe + battery)
0.6kg±0.1kg(sighting telescope)
Source: Tri-band Anti Drone Rifle KWT-FZQ/DG10-A
Manufacturer: Globaldroneuav.com https://globaldroneuav.com/Product/Police-drone-jammer-effective-drone-controller.html
Technical parameters
| SN | Parameter name: | Parameter index record: | |
| 1 | Power supply- | Work voltage V | DC13V~16.8V |
| 2 | Work current A | ≤9A@DC14.8V | |
| 3 | Work time | ≥1.5h | |
| 4 | Radio Frequency | Work frequency range MHz | (1550±5) MHz~(1620±5)MHz
(2400±5) MHz~(2483±5)MHz (5725±5) MHz~(5852±5)MHz |
| 5 | Output power dBm | 40dBm@1550~1620MHz(±1dB) | |
| 6 | 37dBm@2400~2483MHz(±1dB) | ||
| 7 | 37dBm@5725~5852MHz(±1dB) | ||
| 8 | Out of band rejection | <-36dBm@30~1000MHz
<-30dBm@≥1GHz |
|
| 9 | Specification
&environment |
Weight | 4.8kg±0.2kg(Mainframe +battery)
0.6kg±0.1kg(sighting telescope) |
| 10 | Dimension | 1323mm×403mm×341 mm, with battery and antenna | |
| 11 | Work environment humidity | ≥95% | |
| 12 | Work temperature | -25℃~55℃ | |
| 13 | Storage temperature | -40℃~70℃ |
Appearance dimension :(mm)L×W×H;1323mm×403mm×341 mm
Weight(Kg):4.7kg±0.2kg(mainframe + battery)
0.6kg±0.1kg(sighting telescope)
Source: Tri-band Anti Drone Rifle KWT-FZQ/DG10-A
Manufacturer: Globaldroneuav.com https://globaldroneuav.com/Product/Police-drone-jammer-effective-drone-controller.html
Appendix 9-2 MQ-4C Triton design features
The MQ-4C Triton is based on the RQ-4N, a maritime variant of the RQ-4B Global Hawk. The main aluminum fuselage is of semi-monocoque construction, while the V-tail, engine nacelle and aft fuselage are made of composite materials. The forward fuselage is strengthened for housing sensors and the radomes are provided with lightning protection, and hail and bird-strike resistance.
The UAS has a length of 14.5m, height of 4.7m and a wingspan of 39.9m. It can hold a maximum internal payload of 1,452kg and external payload of 1,089kg.
Mission capabilities of MQ-4C Triton BAMS UAS
The MQ-4C is a high-altitude, long-endurance UAS, suitable for conducting continuous sustained operations over an area of interest at long ranges. It relays maritime intelligence, surveillance and reconnaissance (ISR) information directly to the maritime commander.
The UAS can be deployed in a range of missions such as maritime surveillance, battle damage assessment, port surveillance and communication relay. It will also support other units of naval aviation to conduct maritime interdiction, anti-surface warfare (ASuW), battle-space management and targeting missions.
The MQ-4C is capable of providing persistent maritime surveillance and reconnaissance coverage of wide oceanographic and littoral zones at a mission radius of 2,000 nautical miles. The UAS can fly 24 hours a day, seven days a week with 80% effective time on station (ETOS).
Payloads of Northrop’s unmanned system
The payload is composed 360° field of regard (FOR) sensors including multifunction active sensor (MFAS) electronically steered array radar, electro-optical / infrared (EO/IR) sensor, automatic identification system (AIS) receiver and electronic support measures (ESM). The payload also includes communications relay equipment and Link-16.
The MTS-B multispectral targeting system performs auto-target tracking and produces high-resolution imagery at multiple field-of-views and full motion video. The AN/ZLQ-1 ESM uses specific emitter identification (SEI) to track and detect emitters of interest.
Engine and performance of the US’s UAS.
MQ-4C Triton is powered by a Rolls-Royce AE3007H turbofan engine. It is an advance variant of the AE3007 engine in service with the Citation X and the Embraer Regional Jet. The engine generates a thrust of 8,500lb.
The UAS can fly at a maximum altitude of 60,000ft. It has a gross take-off weight of 14,628kg. Its maximum unrefueled range is 9,950 nautical miles and endurance is 30 hours. The maximum speed is 357mph.
Ground control station
The UAS is operated from ground stations manned by a four-man crew, including an air vehicle operator, a mission commander and two sensor operators. The UAS can fly 24 hours a day, seven days a week with 80% effective time on station (ETOS).
The ground station includes launch and recovery element (LRE) and a mission control element (MCE). The MCE performs mission planning, launch and recovery, image processing and communications monitoring. The LRE controls related ground support equipment as well as landing and take-off operations. (Naval Technology Team, 2019)
Appendix 9-3: J/S Calculation Example
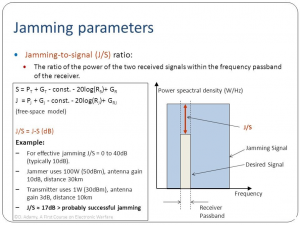
Source: Cagalj, M. (2014) & Adamy, D, (2001) EW 101
Quote from manufacturer Globaldroneuav.com: (Adamy D. , 2009)
Endnotes
[1]FIRES definition (US DoD – JP 3-0) the use of weapon systems to create a specific lethal or nonlethal effect on a target.
[2] Danger Close Definition www.benning.army.mil/infantry/magazine/issues/2013/May-June/Myer.html Nov 14, 2013 – 1) danger close is included in the “method-of-engagement” line of a call-for-fire request to indicate that friendly forces are close to the target. … Danger close is a term that is exclusive from risk estimate distance (RED) although the RED for 0.1 percent PI is used to define danger close for aircraft delivery. Pi = Probability of incapacitation. 2) Definition of “danger close” (US DoD) In close air support, artillery, mortar, and naval gunfire support fires, it is the term included in the method of engagement segment of a call for fire which indicates that friendly forces are within close proximity of the target.
[3] See Team or SWARM formats, Tables 3-1 and 3-2 in (Nichols, et al., 2019)
[4] (Moir I. &., 2006) provides data on all the listed military avionics systems, including role description, key performance characteristics, profile, crew component, systems architecture, major components (avionics, communications, mission systems and weapons), and pictures of aircraft types in the role. The purpose of this section is to detail one role, the Military Maritime Role (MPA) to show that UASs can perform the role in support of the author’s opening contention that manned (piloted) aircraft systems can be replaced by unmanned (no crew) aircraft systems for a variety of the key performance characteristics for less investment and reduced liability to US forces. Every role listed reasonable fits within the author’s contention, again presented without any intended disrespect to our US military forces.
[5] Authors conclusions.
[6] These are legacy definitions from (Moir I. &., 2006) and are included for functional purposes. Chapter 14 of (Nichols, et al., 2019) update these definitions to USA and NATO categories. ES = Electronic Warfare support ( old ESM); EA = Electronic attack – which is the old ECM but also includes ASW and Directed Energy (DE) weapons; and EP = Electronic Protection is the old ECCM.
[7] Again, the chosen material for Table 9-2 has legacy implications by design. Many of the included systems have been significantly upgraded and, in some cases, classified as to performance. All the system names are found in the Abbreviations List. MPA represents a huge category in tasks and is a primary user of acoustic data.
[8] The EW, CW and Acoustic Countermeasures discussions are updated from Chapter 3: Understanding Hostile Use and Cyber- Vulnerabilities of UAS: Components, Autonomy v Automation, Sensors, SAA, SCADA and Cyber Attack Taxonomy;” Chapter 8:” Designing UAS Systems for Stealth;” Chapter 14: Exposing UAS Vulnerabilities via EW and Countering with LPI Signals;” and Chapter 19: Audiology, Acoustic Countermeasures against SWARMS and Building IFF Libraries.” (Nichols, et al., 2019)
[9] The EW, CW and Acoustical sections are updated / illustrated from our previous textbook (Nichols, et al., 2019)
[10] In (Nichols, et al., 2019), we studied the EMS, datalinks and cyber-vulnerabilities of UAS. Here we consider electronic warfare as a method of overwhelming, destroying, or controlling the information, transmitted by communication datalinks, to alter the mission of the UAS deployment. Chapter 14: Exposing UAS Vulnerabilities via EW and Countering with LPI Signals;” in (Nichols, et al., 2019) and (Moir I. &., 2006) in their Chapter 6 Electronic Warfare give reasonable discussions of the fundamentals, technologies, missions and key players for EW. They by no means cover the field however, they serve as a starting point on the long road of EW discoveries.
[11] Nuclear weapons may be characterized in terms of megatons, bullets in terms of muzzle velocity, and particle beams in terms of amperes of current. The commonality is amount of energy absorbed by the target which leads to similar levels of damage achieved at similar levels of energy deposited. (Nielsen, 2012)
[12] Joules is the preferred unit for DE. A joule is approximately the energy required to lift a gallon of milk a distance of three feet or 1/50,000 of the energy needed to brew a cup of 6 oz coffee. For us old-time engineers for reference points: 1 BTU = 1055 J; 1 Calorie = 4.19 J; 1kw hr = 3.6 x 106 J; 1eV = 1.6 x 10-19 J and 1 erg = 10-7 J.
[13] For this example, C= 4.2 (J/gm x o C) and ice cube = 50 gm, Ti= -10 (o C), Tm= 0 (o C). (Lm) for water = 334 Joules / gm. So, 16,700 additional Joules are necessary to melt the ice cube of 50gm. Tv = vaporization temperature, (100 o C),
[14] Aka called “Fluence” Units of fluence are 1 J/cm2 =104 J/m2 and 1 W /cm2 = 104 W/ m2
[15] The effect of area can be better understood by looking at the energy delivery from the two atom bombs delivered against Hiroshima and Nagasaki. (Glasstone, 1977) Both weapons had yields of about 20kT, they released about 8 x 1013 Joules of energy. At a range of z of 0.1 mile (= 1.6 x 104 cm), the energy density would be approximately 8 x 1013 Joules / 4πz2 = 2.5 x 104 J /cm2 or fluence. So, when spreading of the blast energy is accounted for, the result is consistent with other weapon types. Our damage energy density sufficiency is 10,000 J / cm2 or fluence.
[16] Thermal conductivity varies for materials. Copper (good conductor) = 4.2 J/cm sec deg whereas Air (thermal insulator) has a value of 0.00042 J /cm sec deg. (Nielsen, 2012) Thermal conductivity is not just a simple single order equation. Other effects are observed changes in regional temperatures, effects of thermal conductivity, thermal diffusion, / diffusivity, temperature propagation v time.
[17] Black Body radiation is a mathematical ideal surface that absorbs all radiation incident upon it. In equilibrium it would radiate more energy than any other object. (Nielsen, 2012)
[19] Definitions
Electronic warfare (EW) is defined as the art and science of preserving the use of the electromagnetic spectrum (EMS) for friendly use while denying its use by the enemy. (Adamy D. , 2001) The EMS is from DC to light and beyond. EW covers the full radio frequency spectrum, the infrared spectrum, and the ultraviolet spectrum.
Nichols (2000) defines Cybersecurity in terms of cyber-conflict. (Nichols R. K., 2008) Alford (2000) authored effective definitions for the DoD. These will illustrate the bigger picture of Information Operations (IO) and the subset known as Electronic Warfare (EW).
Cybersecurity (in the context of Cyber conflict) is defined as, “the broad tree of investigation and practice devoted to cybercrimes, Computer Forensics (CF), Information Assurance (IA), Information Security (INFOSEC), Communications Security (COMSEC), and especially Cyber Counterintelligence (CCI).” (Nichols R. K., 2008)
“Cyber Warfare (CW / CyW). Any act intended to compel an opponent to fulfill our national will, executed against the software controlling processes within an opponent’s system. CyW
includes the following modes of cyber-attack; cyber infiltration, cyber manipulation,
Cyber assault, and cyber raid.” (DAU, 2018) (DAU, 2018)
“Cyber Infiltration (CI / CyI). Penetration of the defenses of a software-controlled system such
that the system can be compromised, disabled, manipulated, assaulted, or raided.” (DAU, 2018) (DoD, 2018)
“Cyber Manipulation (CM / CyM). Following infiltration, the control of a system via its software which leaves the system intact, then uses the capabilities of the system to do damage.
For example, using an electric utility’s software to turn off power.” (DAU, 2018) (DoD, 2018)
“Cyber Assault (CA / CyA). Following infiltration, the destruction of software and data in the system, or attack that compromises system capabilities.” (Alford, 2000) Includes viruses and system overloads via e-mail (e-mail overflow).” (DoD, 2018; DoD, 2018)
“Cyber Raid (CR / CyR). Following infiltration, the manipulation or acquisition of data within the system, which leaves the system intact, results in transfer, destruction, or alteration of
data. For example, stealing e-mail or taking password lists from a mail server.” (DAU, 2018) (DoD, 2018)
Cyber-Attack. See CyI, CyM, CyA, or CyR.
Cybercrime (CC / CyC). Cyber-attacks without the intent to affect national security or to further operations against national security.” (Alford, 2000)
“C4ISR. The concept of Command, Control, Communications, Computers, Intelligence, Surveillance and Reconnaissance.” (DoD, 2018) (Kaye, 2001) See Figure 9-15 (C4ISystems, 2013)
Electronic Warfare (EW) is defined as the art and science of preserving the use of the Electromagnetic Spectrum (EMS) for friendly use, while denying its use by the enemy. (Adamy D. , 2001)
“Information Assurance (IA). Measures that protect and defend information and information systems by ensuring their availability, integrity, authentication, confidentiality, and non-repudiation. These measures include providing for restoration of information systems by incorporating protection, detection, and reaction capabilities.” (Barker, 2003) (Kaye, 2001)
“Information Operations (IO). The integrated employment of the core capabilities of electronic warfare, computer network operations, psychological operations, military deception, and operations security, in concert with specified supporting and related capabilities, to influence, disrupt, corrupt, or usurp adversarial human and automated decision-making process, information, and information systems while protecting our own.” (Barker, 2003) (Kaye, 2001)
“Information Superiority (IS). The capability to collect, process, and disseminate an uninterrupted flow of information while exploiting or denying an adversary’s ability to do the same. A newer form of this is that: degree of dominance in the information domain which permits the conduct of operations without effective opposition.” (Alford, 2000) (Kaye, 2001)
“Information Warfare (IW). Information operations conducted during time of crisis or conflict to achieve or promote specific objectives over a specific adversary. IW is any action to Deny, Exploit, Corrupt or Destroy the enemy’s information and its functions, protecting those actions and exploiting our own military information functions.” (Alford, 2000) (Kaye, 2001)
“Intentional Cyber Warfare Attack (ICWA). any attack through cyber-means to intentionally affect national security (cyber warfare) or to further operations against national security.
Includes cyber-attacks by unintentional actors prompted by intentional actors. (Also
see “unintentional cyber warfare attack.”) IA can be equated to warfare; it is national policy at the level of warfare. Unintentional Attack(UA) is basically crime. UA may be committed by a bungling hacker or a professional cybercriminal, but the intent is self-serving and not to further a national objective. This does not mean unintentional attacks cannot affect policy or have devastating effects.
Intentional Cyber Actors (I-actors). Individuals intentionally prosecuting cyber warfare (cyber
operators, cyber troops, cyber warriors, cyber forces).” (Alford, 2000)
“Network Centric Operations (NCO). NCO involves the development and employment of mission critical packages that are the embodiment of the tenets of Network Centric Warfare (NCW) in operations across the full mission spectrum. These tenets state that a robustly networked force improves information sharing and collaboration, which enhances the quality of information, the quality of awareness, and improves shared situational awareness. This results in enhanced collaboration and enables self-synchronization improving sustainability and increasing speed of command, which ultimately result in dramatically increased mission effectiveness. (Kaye, 2001)” (MORS, 2018) (Kaye, 2001)
OPSEC. (Operations Security) (DoD-01, 2018) “Determining what information is publicly available in the normal course of operations that can be used by a competitor or enemy to its advantage. OPSEC is a common military practice that is also applied to civilian projects such as the development of new products and technologies.
OPSEC – The Official Definition
(From JP 1-02, Department of Defense Dictionary of Military and Associated Terms, www.dtic.mil/doctrine/new_pubs/jp1_02.pdf.) Operations Security (OPSEC) is a process of identifying critical information and subsequently analyzing friendly actions attendant to military operations and other activities to:
1. Identify those operations that can be observed by adversary intelligence systems,
2. Determine what indicators adversary intelligence systems might obtain that could be interpreted or pieced together to derive critical information in time to be useful to adversaries, and
3. Select and execute measures that eliminate or reduce to an acceptable level the vulnerabilities of friendly actions to adversary exploitation.” (DoD-01, 2018)
“Psychological Operations (PO) Planned operations to convey selected information and indicators to foreign audiences to influence their emotions, motives, objective reasoning, and ultimately the behavior of foreign entities.” (Alford, 2000) (Kaye, 2001)
“Psychological Warfare (PW / PSYWAR) The planned use of propaganda and other psychological actions to influence the opinions, emotions, attitudes and behavior of hostile foreign groups.” (Kaye, 2001)
“Unintentional Cyber Actors (U-actors). Individuals who unintentionally attack, but affect
national security and are largely unaware of the international ramifications of their actions.
Unintentional actors may be influenced by I-actors, but are unaware they are being
manipulated to participate in cyber operations. U-actors include anyone who commits
CyI, CyM, CyA, and CyR without the intent to affect national security, or to further
operations against national security. This group also includes individuals involved in
CyC, journalists, and industrial spies. The threat of journalists and industrial spies
against systems including unintentional attacks caused by their CyI efforts should be
considered high.
Unintentional Cyber Warfare Attack (UCWA/ UA). Any attack through cyber-means, without the intent to affect national security (cybercrime).” (Alford, 2000)
[21] Skyjack Drone hack. Drone that flies around seeking Seeks wireless signal of any other drone in area. Forcefully disconnects wireless connection of true owner of target drone. Authenticates with target drone pretending to be its owner. Feeds commands to it and all other zombie drones SkyJack primarily a Perl application which runs off a Linux. Detect drones by seeking out wireless connections from MAC addresses.
[22] Aircrack-ng© To put wireless device into monitor mode to find drones and drone owners. De-authenticate true owner of drone. Once de-authenticated, connect as drone waiting for owner to reconnect.
[23] Snoopy is Software that can hack into Wi-Fi and steal data – attached to drones. Comprised of various existing technologies. Uses Distributed tracking and profiling framework. Runs client-side code on any device that has support for wireless monitor mode. Collects probe-request and uploads to a central server. Exploits handsets looking for wireless signal. Most leave their device Wi-Fi setting on Spoof network available to Wi-Fi searchers to use. Once connected to rogue network, data is stolen. Differs from other rogue access points in way data is routed. Traffic is routed via an OpenVPN connection to a central server. Able to observe traffic from all drones in field at one point. Traffic manipulation only done on server. Allows basic data exploration and mapping.
[24] Special thanks and credit to my co-author Dr. Julie J.C.H. Ryan and Dan J. Ryan, Esq who were pioneers in the field information security and its associated risks. (Randall K. Nichols, 2000)
[25] Adamy sets the standards for EW instruction. Moir summarizes the topic with respect to military operations, UAS, and military avionics systems. (Moir I. a., 2006) (Toomay, 1982) and (Burch, 2015) bring Radar to the non-specialist reader. A Google search on the key = RADAR yields 296,000,000 results (0.49 seconds). There is substantial material on the subject. The challenge is determining the UAS applicability.
[26] Legacy EW definitions- EW was classically divided into: (Adamy D. , 2001)
ESM – Electromagnetic Support Measures – the receiving part of EW;
ECM – Electromagnetic Countermeasures – jamming, chaff, flares used to interfere with operations of radars, military communications and heat-seeking weapons;
ECCM -Electronic Counter-Counter Measures – measures taken in design or operation of radars or communications systems to counter the effects of ECM.
Not included in the EW definitions were Anti-radiation Weapons (ARW) and Directed Energy Weapons (DEW).
USA and NATO have updated these categories:
ES – Electronic warfare Support (old ESM)
EA – Electronic Attack – which is the old ECM but also includes ASW and DE weapons;
EP – Electronic Protection – (old ECCM) (Adamy D. , 2001)
ES is different from Signal Intelligence (SIGINT). SIGINT is made up of Communications Intelligence (COMINT) and Electronic Intelligence (ELINT). All these fields involve the receiving of enemy transmissions. (Adamy D. , 2001)
COMINT receives enemy communications signals to extract intelligence.
ELINT uses enemy non-communications signals for determining the enemy’s EMS signature so that countermeasures can be developed. ELINT systems collect substantial data over large periods to support detailed analysis.
ES/ESM collects enemy signals, either communication or non-communication, with the object to do something immediately about those signals or the weapons associated with those signals. The received signals might be jammed, or the information sent to a lethal responder. Received signals can be used to type and locate the enemy’s transmitter, locate enemy forces, weapons, distribution, and electronic capability. (Adamy D. , 2001)
[27] This a main theme of this book. In addition, this section started off with the answer – Low Probability of Intercept (LPI) as a countermeasure to reduce risk of EA to the UAS missions. (Adamy D. , 2009)
[28] Any number expressed in dB is logarithmic base 10. dB mathematical concepts with examples may be found in Chapter 2 of Adamy, D., (2001) EW 101. A value expressed in dB is a ratio converted to logarithmic form. A linear number is converted to dB form by the formula: N(dB) = 10 log (base 10) [N]. dB values are converted back to linear format by the formula N = 10 **N (dB/10). dB numbers are usually reference to some standard with constant value. A common example is signal strength expressed in dBm = dB value of Power / 1 milliwatt, used to describe signal strength. For example, 4 watts power level = 4000 mw. Divide by 1 mw standard then convert 4000 to dB = 10 log (4000) = 36.02 dBm. dB forms are used because of the wide range of numbers and orders of magnitude for the EMS.
[29] dBi = dB value of antenna gain relative to the gain of an isotropic antenna ( perfect antenna). 0 dBi is the gain of an omnidirectional (isotropic) antenna.
[30] Video Report, Quote by Amy Hu. Data Expert Technology LTD, https://www.youtube.com/watch?v=o057LmNGsJA DLA 07312018
[31] Source: Tri-band Anti Drone Rifle KWT-FZQ/DG10-A
Manufacturer: Globaldroneuav.com https://globaldroneuav.com/Product/Police-drone-jammer-effective-drone-controller.html
[32] DE weapons are technically kinetic weapons with non-kinetic interfaces. The author has included them because they are very cool and represent a huge amount of classified advanced research for C-UAS purposes.
[33] FM 3-38 (2014)
[34] Askin, O., Irmak, R, and Avseyer, M. (14 May 2015)
[35] CEA aka Cyber electronic warfare
[36] Student will research CEA and its parallels to EW (start with FM 3 – 38 Cyber Electromagnetic Activities in CANVAS or use Google to find the free PDF) How do these intersections support both friendly and hostile actions on UAS systems in all classes? Develop a PowerPoint presentation with your answers for class submission. Look for tools like cyber offensive weapons against key UAS systems and cyber defensive weapons/countermeasures that can be used to thwart the cyber weapons that you have found in Open Source literature (Non- CLASSIFIED). Try to develop a taxonomy around your findings.

