Chapter 10: When the Other Side Fights Back – Cyberwarfare, Directed Energy Weapons, Acoustics,Integrating C-UAS into Planning
R. K. Nichols
Student Objectives
All the C-UAS systems described in this chapter are known by USA and friendly forces and, in general, by other countries (China, Russia, terror states under CNKI, etc.) So, the object of this chapter is to understand the lethal use of the EMS by:
- Study four classic direct energy weapons (DEW, Laser, Microwave, Particle Beams) technologies
- Learn about acoustic countermeasures and their effects on MEMS
- Sample real-world advanced UAS systems deployed in the field. These UAS are able to fight back via EW and have both kinetic and non-kinetic countermeasures against friendly C-UAS systems.
What Happens When the Enemy Decides to Fight Back?
There needs to be plans /policies in place. The UK Government has developed one and presented it to Parliament in October 2019. In the UK Counter-Unmanned Aircraft Strategy we read the following objectives: (Norbiton, Oct 2019)
1 The objective of the strategy is to reduce risk posed by the highest-harm illegal use of drones,
2 The government’s strategy is to mitigate the malicious, criminal use of drones, including threats to the UK’s national security and critical infrastructure,
3 To develop a comprehensive understanding of the evolving risks posed by the malicious and illegal use of drones,
4 To take a full spectrum approach to deter, detect and disrupt the misuse of drones
5 To build strong relationships with industry to ensure products meet the highest security standards
6 To empower police and other operational responders through access to counter-drone capabilities and effective legislation, training and guidance.[1]
(Norbiton, Oct 2019) document considers highest-harm risks resulting from malicious use of drones:
- Facilitating terrorist attacks
- Facilitating crime, especially in the UK prisons
- Disrupting Critical National Infrastructure (CNI)
- Potential use by hostile state actors
The two departments that are responsible for strategy and policy associated with the illegal use of drones are Department of Transport(DT) (responsible for the safe and lawful use of drones within UK airspace) and the Home Office (HO) which has overall responsibility for domestic counter-drone activity as part of its wider security remit. (Norbiton, Oct 2019)
First Actions
Following the Gatwick drone sightings in December 2018, the DT and the Center for Protection of National Infrastructure (CPNI) put in place policies to reduce the vulnerability of sensitive sites to drone incursions:
- Guidance for CNI operators, including airports on how to assess drone risks and vulnerabilities, and training on available counter -drone technologies.
- Standardized signage to clearly designate areas where drone flights are prohibited, and providing information to the public on how to report drone sightings,
- Setting security requirements for manufacturers and end-users of counter-drone equipment to safely test and refine their equipment,
- Put in place significant additional classified steps to ensure that UK airports are prepared to detect, deter, and disrupt drone incursions.(Norbiton, Oct 2019)
Regulations
The Air Navigation Order (ANO) of 2016 established a number of offenses regarding the irresponsible use of drones. (National Archives, 2019) This is an extensive order much like the FAA multiple instructions / regulations / drafts for flight certifications, suitability, guidance and penalties for illegal use. APO 2016 was updated to include more offenses after the Gatwick 2018 incidents. On 30 November 2019, all sUAS drones must be registered and owners / pilots must undertake competency testing.
The DT, in its 2018 consultation, Taking Flight: The Future of Drones in the UK, (Transport, 2019) announced its intention to give police new powers to enforce drone offenses under ANO 2016 by:
- Giving police the power to require a drone to be grounded,
- Giving police the power to require operators to produce evidence of registration and competency and provide the identity of the operator
- Improving police powers to investigate where an offense has been committed,
- Making an expansion to “no-fly zones” around airports from 1km to 5 km, effective March 2019,
- Improved Stop and Search power for offenses relating to flying a drone in a restricted zone of an aerodrome.[2]
Compare this approach to the ineffectual California police handling a drone operator misusing his drone during a huge and dangerous wildfire. The drone forced rescue helicopters to avoid critical areas and to be grounded. (Norman, 2019)
Practical Aviation Security in USA
An Airport Cooperative Research Project (ACRP), Unmanned Aircraft Systems at Airports: A Primer researched the potential use and impact of ATC systems, airport facility standards, environmental impact, safety management systems and community outreach. (K. Neubauer, 2015) Unfortunately, the report failed to envision the security threats posed by UAV operations away from an airport.
Security Implications of UAV Operations (5 major threats)
The security threats from current enemy drone operations are multiple:
- A UAV can be used to conduct surveillance on airports or other high-value targets (HVT)
- A UAV can be purposely flown into a passenger aircraft.(Example Figure 3-1 in (Nichols, et al., Unmanned Aircraft Systems in the Cyber Domain, 2019)
- A UAV can be weaponized with a gun, DEW, Sonic systems, lasers, IEDs, to attack a high-value targets, passing quietly over the heads of security personnel and any security fencing or barriers
- A UAV could combine weapons and surveillance and flown into a number of specific targets
- A UAV can be equipped with CBR element and dispense the agent over an open-air assembly, stadium, ball park, mall or concert. (Forrest, 2016)
Most of the authors’ 2nd edition was devoted to expanding the threat landscape and countering the risks so determined. (Nichols, et al., Unmanned Aircraft Systems in the Cyber Domain, 2019) In this text, the authors assume the enemy fights back. All the risks remain and must be considered viable scenarios at some level of exposure and mitigation. Several Russian and Chinese competitive systems are discussed later in this chapter.
Important Changes in Electronic Warfare
The authors agree with Commander Malte von Spreckelsen, DEU N, NATO Joint Electronic Warfare Core Staff that modern conflicts will be fought in all dimensions possible and that Electronic Warfare (EW) will be the key for modern conflict. (Commander Malte von Spreckelsen, 2018)[3]
The modern “father” of Electronic Warfare technology is David L. Adamy. In his textbook (Adamy D. L., 2015) he points out important changes in EW (especially after the Iraq wars and the expansion of UAS in the battlefield):
- The recognition of the electronic environment as a distinct battlespace;
- New and extremely dangerous electronically guided weapons;
- New technologies that impact both the accuracy and lethality of weapons.
Adamy defines radio emissions associated with threats as “threats.” This is not technically correct because things that explode or can cause great damage are also threats. Adamy refers to signals as threats, especially radar and radar-controlled weapons:
- Search and acquisition radars;
- Tracking radars;
- Radio links between radar processors and missiles
The other significant area defined by Adamy is communication threats which include:
- Command and control communications;
- Data links between components of integrated air defense systems;
- Command and data links connecting UAVs with their control stations;
- Cell phone links when used for military purposes.(Adamy D. L., 2015)
Adamy essentially focuses on ADS. Cmd. von Spreckelsen considers integration of the EMS the entire battlespace to insure effectiveness of IADS suppression. (Stathopoulos, 2018) See Figure 10-1.[4]
NATO has a pretty decent view on the threats it may encounter on land, on and below sea, in the air, and in space. Furthermore, cyberspace is increasingly considered by NATO as critical risk – determinative. (Commander Malte von Spreckelsen, 2018)
“In its EW policy[5], NATO defines Electronic Warfare as ‘a military action that exploits electromagnetic energy, both actively and passively, to provide situational awareness and create offensive and defensive effects’. It is warfare within the Electromagnetic Spectrum (EMS) and (shown in Figure 10-2) involves the military use of electromagnetic energy to prevent or reduce an enemy’s effective use of the EMS while protecting its use for friendly forces.”
Figure 10-1 Integration of the Electromagnetic Spectrum (EMS) into Every Operating Domain
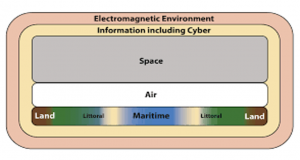
Source: (Stathopoulos, 2018)
Figure 10-2 Electronic Warfare in today’s military environment
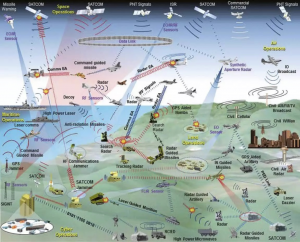
Source: (Commander Malte von Spreckelsen, 2018)
Figure 10-2 is a complex reality. Study this in detail. Recognized the importance of communications, cybersecurity, and EW components. EW can have significant mission impact – even in the simplest possible scenario. “For example, having an adversary monitor one’s communications or eliminate one’s ability to communicate or navigate can be catastrophic. Likewise, having an adversary know the location of friendly forces based on their electronic transmissions is highly undesirable and can put those forces at a substantial disadvantage.” (Commander Malte von Spreckelsen, 2018)
Recall from (Nichols, et al., Unmanned Aircraft Systems in the Cyber Domain, 2019) the EMS purview in Figure 10-3:
Figure 10-3 EMS Purview
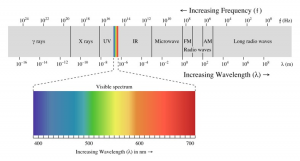
Source: (TRS, 2018)
Now integrate the EMS information with the Battlespace Dimensions in Table 9-3 from previous chapter (Nichols, et al., Unmanned Aircraft Systems in the Cyber Domain, 2019):
The point is that the security environment has changed necessitating a refocus on EW, especially integrated with Cyber capabilities. Russia and China have significantly upgraded their capabilities to operate in the EMS. (Commander Malte von Spreckelsen, 2018) These are not threats to be ignored.
Revisit Figure 9-21 showing the intersection of Cyber, EW, and Spectrum Warfare designated as Cyber Electromagnetic Activities (CEA).[6]
Cyberwarfare Purview
When our authors think Cyberwarfare, the consensus is that cyber refers to information moved from computer to computer over the Internet, within the network of computers comprising the Internet. In Chapter 4 of the 2nd edition textbook (Nichols, et al., Unmanned Aircraft Systems in the Cyber Domain, 2019) the authors expanded this definition to measures on the information superhighway to gain military advantage by gathering military significant information from the enemy or interfering with the enemy’s ability to move its own information over the Internet or other networks or to process information within a computer or finally to be able to make command decisions faster than the enemy in all the domains. In Chapter 1 of this textbook, the authors consider the role of information technologies (automated decisions, artificial intelligence (weak and strong), communications, networking, remote sensing) and later in Chapter 4 the authors consider issue of resiliency, i.e. planning for resiliency and robustness expecting pushback, when secrecy is needed, how to shield operations. In Chapter 9, the authors introduced SCADA attacks and vulnerabilities and how important they were in terms of UAS operations.
The uninitiated would see cyber warfare as conducted by the use of malware. This is first level software whose purpose is destruction. The tools in this view are simply viruses, worms, Trojan Horses, spyware, rootkits, attacks on service, protocols storage or data in transit. All these are useful. But the real meat especially for UAS, satellite, ground stations and mobile deployment units is SCADA and its vulnerabilities.[7] This would be like calling Stuxnet just a virus! Stuxnet was an exquisitely designed cyberweapon with vectoring in on multiple zero-day vulnerabilities, specific manufacturer OS / maintenance SCADA attacks, multiple coordinating vectors of attack, secret target acquisition in Iran. It had the huge effect of delaying Iran’s nuclear buildup by destroying their centrifuge processes from within by inducing cavitation and turning off operator controls / alarms without detection. (Zetter, 2014) The only property that Stuxnet didn’t have was self-destruction upon discover or self-encryption for protection against countermeasures. Stuxnet was not discovered by Iran but information was released publicly by commercial interests for unknown reasons.
Cyber vs EW Battlespace (Parallels)
EW in legacy terms has three major subfields and another closely related field:
- Electronic warfare (EW) support (ES), which involves hostile intercept of enemy transmissions
- Electronic Attack (EA) in which enemy electronic sensors (radars and communications; receivers) are degraded either temporarily or permanently by transmission of signals designed for that purpose;
- Electronic protection (EP), which is a set of measures designed to protect friendly sensors from enemy EA actions;
- Decoys, which act as bait to cause enemy missile and gun systems to acquire and track invalid targets.(Adamy D. -0., 2015)
Cyber warfare (CW) involves attacks on military assets through networks, including the internet. Electronic Warfare involves attacks on military assets through electromagnetic propagation. Table 10-1 continues the legacy definitions comparison of CW and EW functions.
Table 10-1 Comparison of EW and CW Functions in legacy terms
| Operational Function | EW | CW |
| Collect information from enemy | EW support, listens to enemy signals to determine enemy capabilities and operating mode | Spyware, causes information to be exported to a hostile location (or friendly depending on the side employed) |
| Electronically interfere with enemy’s operational capability | EA, either covers received information or causes processing to give inaccurate outputs | Viruses, reduce available operating memory or modify programs to prevent proper processing outputs |
| Protect friendly capabilities from enemy’s electronic interference | EP, prevents enemy jamming from impacting operational capabilities | Passwords, firewalls, VPNs, hardware modifications, cryptography,[8] steganography [9],2-factor authentication, digital signatures, prevent malware from penetrating a computer and breaching information security protocols |
| Cause enemy systems to initiate undesired actions | Decoys, look and act like valid targets, when acquired by missile or gun systems point away from the real target | Trojan Horses, rootkits, are hostile software accepted by the enemy computers because they appear valid and have acceptable credentials (Adamy D. -0., 2015) |
| Direct damage or destruction | DEW, Acoustic grenades, lasers, anti-satellite weapons all hit the UAS target from outside and destroy it by delivering focused energy in real time on a small slice of the target | Advanced Cyberweapons attack SCADA and internal subsystems causing them to act in unplanned actions (fatal) to either over or under perform a critical function or subfunction, lose energy, destabilize, or prevent operator action on a critical fault (Nichols, et al., Unmanned Aircraft Systems in the Cyber Domain, 2019) |
EMS Environment
It can be deduced from Table 10-1 that the difference between cyber warfare and EW has to do with how the hostile function is introduced into the enemy’s systems. Historically, EW dealt with the electromagnetic spectrum (EMS) as it was related to kinetic threats. Radars that locate targets guide missiles to those targets and detonate warheads. EW was purposed to make missiles unable to hit those targets. This meant disrupting a receipt of a return signal or preventing the missile uplink from delivering guidance information. Enemy communications relate to command and control (CC). Historically, this referred to kinetic attack protocols. The purpose of EW was to prevent CC by the enemy. (Adamy D. -0., 2015)
Computers and software are an integral part of almost every aspect of modern warfare, and cyber warfare attacks on those computers directly impacts kinetic attacks and the defenses against those attacks. The new reality is that the EMS itself has become a target of enemy actions. By denying USA use of the EMS, the enemy can inflict significant economic damage upon society, put our military forces at a disadvantage without firing a single shot or dropping a single bomb.
The EMS environment is becoming more complex, congested, and contested, making it imperative for Defense agency and organizations to continually improve EW capabilities to enable reliable use of the EMS.
NATO – EME, EMO
NATO, like DoD, is evolving how it conducts operations and support of emerging technologies. The focus has shifted away from isolated EW operations to joint Electromagnetic Operations (EMO) in the electromagnetic environment (EME). (Commander Malte von Spreckelsen, 2018).
The EMS is defined as the entire distribution of electromagnetic radiation according to frequency or wavelength (Figure 10-3).[10] Electromagnetic waves (EMW) travel at speed of light in a vacuum, they do so across a wide range of wavelengths and corresponding frequencies. EMS comprises the span of all electromagnetic radiation (ER) and consists of many subranges called spectral bands such as visible light or ultraviolet radiation. EME is the geophysical environment influenced by terrain, weather and atmospheric conditions, which supports the radiation, propagation and reception of ER across the entire EMS. (Commander Malte von Spreckelsen, 2018)
Within NATO, EMO is the deliberate transmission and reception of EM energy in EME for military operations. This includes communications, navigation, attack, battlespace awareness, and targeting. Figure 10-4 demonstrates that EMO not only enables operations in each domain but also provides the thread which links and integrates military forces across domain, and in cyberspace and information environments. EMO is conducted by both friendly and enemy forces. EMO often leads to contested, overlapping, congested or interference with neutral actors in the EME. (Commander Malte von Spreckelsen, 2018)
DE Weapons
In Chapter 9, the authors looked at the basic principles of DE weapons. UAS in flight (SWARMS or other configuration) are subject to destruction by deployment of DE weapons. DE weapons are in a class by themselves and represent huge portion research budgets in USA, China and Russia. All military and large commercial UAS are potential targets for DEW deployment. There are four types of DE weapons, kinetic energy, lasers, microwave and particle beams. (Nielsen, 2012) The approach taken is to discuss fundamental concepts, then propagation (travel) towards the target, and lastly, interaction with the target and the mechanisms by which the target is destroyed.
Kinetic Energy Weapons (KEW)
Kinetic energy (KE) weapons fir the definition of DEW because their energy is aimed or directed at a target and intercepts a small fraction of the target’s surface area. 10,000 Joules is a magic number because it is close to the energy delivered by a wide range of DEWs. 10,000 Joules is sufficient energy to vaporize about one cubic centimeter of anything! (Nielsen, 2012)
Figure 10-4 EMO in EME

Source: (Commander Malte von Spreckelsen, 2018)
We need some understanding of the parameters and units affecting target response and damage. Table 10-2 shows key parameters, units, definitions, and comments
KEW damage targets with their energy of motion. This energy is proportional to a projectile’s mass and the square of its velocity. In space, projectile motion is determined by the gravitational force of earth, along with the forces from the projectile’s launcher or on-board engine. Gravitational forces dominate a projectile’s trajectory, and KE far exceed damage criteria. Stress in the target exceed its internal strength, and it responds like a dense gas. Details of projectile and target construction are of minor importance. In the atmosphere, ranges are shorter and energies less due to atmospheric drag. At lower energies forces internal to a target are important. The target’s response depends on its construction and end engagement scenario. Projectile design for efficient propagation and interaction is a priority and may be a compromise with optimization for target interaction. (Nielsen, 2012)
Table 10-2 Parameters , Units affecting Target Response and Damage
| Parameter | Symbol | Units | Definition | Comments |
| Kinetic Energy | K | Joules (J) | K= Mv2 / 2 | M,v = Projectile mass, velocity |
| Momentum | ρ | Kg m/sec | Mv | K and ρ are conserved when particles collide |
| Force | F | Newtons (Nt) | M dv/dt | Also, F= dp/dt |
| Pressure | P | Nt/m 2 | Force / Area | Force/ Area = Energy / Volume |
| Impulse | I | Nt sec | Force x time | |
| Fluence[11]
Or Intensity |
F or
I |
Joules / cm 2
Watts / cm 2 |
KE /area | Concentrated KE density necessary to damage a target measured as an output of a radiation field or laser beam |
Source: (Nielsen, 2012)
The finite speed of KEW (10 km/sec or less) means that the time to engage goes up with increasing distance and moving targets can be engaged only if they are “led”[12] with computer calculations made in advance on how to bring the weapon and target together. There are three truths that hold for all types of DEW.
- “Propagation in a vacuum follows well defined physical laws. These account for adequate energy placement on the target by the weapon. Long ranges associated with engagements in space place severe constraints on the energy that the weapon launcher requires to ensure lethal energies are brought to bear on the target. Orbital motion counts for much of the energy in space. This energy is not free and comes from the energy in the rocket engines which placed the weapons in orbit.(Nielsen, 2012)
- In the atmosphere, ranges are much less than in space and interactions results in greater energy losses. Therefore, weapon characteristics / parameters (bullet shape, laser pulse width, etc.) must be tailored to minimize these energy losses. (Nielsen, 2012)
- When a weapon encounters a target, energy must be efficiently absorbed for damage to occur. This places constraints on weapon parameters which may be conflict with those necessary for efficient propagation. (Nielsen, 2012)
Lasers
A Laser is fundamentally nothing more than a device that can produce an intense, or highly energetic, beam of light.[13] Light is an EM band in the EMS and is subject to Maxwell’s wave equations. (David H. Staelin, 1998) Here are the basic ideas about lasers as weapons from (Nielsen, 2012):
- Lasers are intense sources of ER with wavelengths from 10 to 0.4 μm and frequencies from about 3 x 10 13 to 8 x 10 14 Hz.
- The materials with which lasers might interact are characterized by an index of refraction, n, and the attenuation coefficient, K. When light passes regions of different n, it is bent according to the Law of Refraction. When light propagates a distance, z, through a region whose attenuation coefficient is K, its intensity is decreased by a factor of e (-Kz).
- A laser with a wavelength, λ, emerging from an aperture of diameter, D, can propagate a distance on the order of D2 / λ, as a collimated beam.[14] Beyond this distance, it will diverge at an angle of θ ≈ λ / D. Figure 10-5 shows Collimated light for Laser.
- Decreases in intensity result from both diffraction and attenuation. This results in a fraction of the beam’s energy being reduced and reduces the amount of energy that can be brought to bear on the target. Compensating parameters to reduce this effect are energy level, pulse width, wavelength, and diameter of the beam.
- In the atmosphere, K, is highly dependent, made up of contributions from absorption and scattering from both molecules and particles.[15] If a beam becomes too intense, free electrons in the atmosphere will multiply and breakdown, forming an ionized plasma which will absorb the beam. Following the breakdown, plasmas propagate toward the source of laser light as combustion or detonation waves.[16]
Figure 10-5 Collimated light for Laser
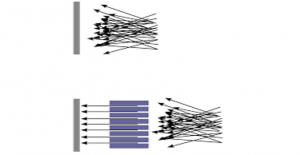
Source: (Jackson, 2017)
- In the atmosphere, n, the index of refraction, can vary through turbulence or through expansion induced by absorption of laser light. The second effect results in beam expansion (thermal blooming) or bending. These effects must be compensated for in real time through adaptive optics.
- When laser light encounters a target , a fraction of the light is absorbed in the target surface, and manifests as heat. Thresholds for melting and vaporization are established by the criterion that energy is deposited so rapidly that it cannot be carried away within the pulse width of the laser. Targets can be damaged by erosion (thermal melting) or through momentum transferred to the target surface by the evolving vapor jet (mechanical damage).[17]” (Nielsen, 2012)
Actually, the torch cutting process is a good example of laser optimization of intensity versus pulse width concept. Such optimum considers propagation and interaction effects as they work together to constrain the available operating parameters. Figure 10-6 Laser technology processing activities used in manufacturing.[18]
Figure 10-6 laser processing activities as a function of the laser pulse width
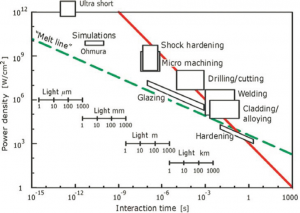
Source: (National Academies of Sciences, 2018)
It may be concluded (extending the torch thinking) that there is very little opportunity to damage targets in the atmosphere without operating at intensities where potentially deleterious propagation effects must be handled. Even melting through targets in times less than seconds will be influenced by thermal blooming. If mechanical damage is needed, the full range of propagation effects could constrain the interaction between laser and target. [19]
Microwaves
Like lasers, microwaves travel through space, carrying energy and are characterized by specific frequencies. Microwaves are another form of ER, having a much longer wavelength and much lower frequency than light. Microwaves have wavelengths of about 1 cm, and frequencies on the order of 1010 Hertz, or 10 GHz. (See Figure 10-7) Microwaves have a long history of use in commercial devices.
Figure 10-7 Microwave portion of the EMS
Source: (Micro Denshi Co.,Ltd., 2019)
Microwaves travel at the speed of light, c, (=3 x 108 m/sec) in a vacuum. They have frequency, v, and wavelength, λ, related by the expression v = c / λ. Microwave frequencies lie in the range of 0.1 – 100 GHz, and the associated wavelengths lie in the range 100 – 0.1 cm. Microwaves are unique in that their wavelengths are similar in size to the physical objects they interact with. (Micro Denshi Co.,Ltd., 2019)
Microwave Target Interaction
Microwaves are likely to damage targets through the soft kill mechanisms (similar to cyber-attacks on SCADA systems) – those that exploit inherent target vulnerabilities. There are two types of soft-kill: in-band and out-of-band. (Nielsen, 2012)
- With in-band damage, microwaves enter target through its antenna.(Adamy D. , 2009) This requires that the attacking microwaves be of the same frequency as those the target is tuned to receive. Damage occurs when the target’s circuits are loaded beyond their design capacity. (Nielsen, 2012) The best-known example of in-bound microwave attack is EW jamming, a staple of CEA. (Adamy D. , 2009) Although there are shielding methods in military UASs to reduce this microwave jamming vulnerability, damage may still occur.
- In out-of-bounds damage, microwaves enter the target through the back door – apertures (again similar to some cyber-attacks) which were not designed for entry. Damage occurs as the microwaves are absorbed in thin, sensitive electronic components, heating them to the point of exhaustion and damage. (Nielsen, 2012)
Particle Beams
The fourth (DEW, Lasers, Microwaves and Particle Beams (aka PB)) type of DEW that may be used against UASs are Particle Beams. Particle beams are large numbers of atomic or sub-atomic particles moving at relativistic velocities. [20] There are a large number of particles in these beams. Their interactions among themselves is as important as their interactions with the atmosphere and with targets. Below are the main concepts as we delve into the propagation and interaction forest of charged and neutral particle beams. (Nielsen, 2012)
- There are two types of PB: charged and neutral. Charged PB consist of particles such as electrons and photons which have an electrical charge. Charged PB tend to spread because of mutual repulsion of their particles. Neutral PB consist of electrically neutral particles such as hydrogen atoms.(Nielsen, 2012)
- A PB is characterized by the current it carries, the energy of its particles, and its radius. These quantities are related to more weapon related parameters such as intensity, through relationships shown in Table 10-3. (Nielsen, 2012)
Table 10-3 Quantities Used to Characterize Particle Beams (PB)
| Fundamental Physics | Beam Engineering | Weaponeering |
| Particle charge, q | Current, I | Beam intensity, S |
| I = nqvπw2 | S= nKv | |
| Beam radius, w | ||
| Particle density, n | Kinetic Energy, K | Beam Fluence, F |
| ϓ =1/(1-v2 /c2) 1/2 | F= Stp | |
| Particle velocity, v | K= (ϓ-1)mc2 | |
| Pulse width, tp | Pulse width, tp |
Source: (Nielsen, 2012)
- Real PB deviate from perfection, in which all the particles propagate in the same direction with the same velocity. Lack of perfection is expressed in PB brightness (current/area/per solid angle); divergence (angle which the PB envelope makes as it expands); or temperature (small random fluctuations in energy about the average value). (Nielsen, 2012)
- Neutral PB can propagate only in a vacuum at altitudes greater than about 100 km. Charged PB can propagate only in the atmosphere at altitudes less than about 200 km.(Nielsen, 2012)
- In propagating through the atmosphere, particles in the PM lose energy by ionization of the background gas and radiation. Further, if the PB contains heavy particles (photons or atomic nuclei), it loses current from collisions. These negative effects are reduced in magnitude as the atmospheric density is reduced. PB can also become unstable and cease to propagate when internal perturbations occur and grow. (Nielsen, 2012)
- PB interact with targets just as they do with the atmosphere – through ionization, bremsstrahlung,[21] and nuclear interactions. The energy deposited into the target is a function of its density. Energy losses from a PB propagating through the atmosphere to a target are less than those within the target itself.(Nielsen, 2012)
- For PB in the atmosphere, the total time it takes to destroy a target may be greater than the time required for a constant beam to deposit sufficient energy on it, because of “hole-boring” and suppression of instabilities.
PB Target Implications (especially large UAS)
In principle, PB should be ideal as DEW. Unlike lasers or microwaves, their propagation is unaffected by weather, clouds, rain, which add very little to the mass a PB might encounter on the way to the target. PB are an all-weather weapon. Once the PB encounters the target, the long penetration range of relativistic particles ensures that critical components on the interior of the target will be rapidly engaged. Time is not wasted on eroding protective layers of matter on the target surface. Shielding targets against PB as a defensive countermeasure (CM) is not practical.
In practice, PB are not technologically “there” yet. Difficulties in achieving stable propagation in the atmosphere has caused the research funds to focus on space based neutral PB, where physical problems of atmospheric propagation are replaced by engineering problems of deployment into space and maintaining large constellations of particle accelerators. (Nielsen, 2012)
So, of four DEW, it appears that only Lasers, Microwaves are viable and cost-effective approaches. However, a new EMS team player has joined the C-UAS fray. Sound. Sound has some very nice properties and is useful as both a countermeasure and an identifier in IFF systems. Sound as a CM was introduced in Chapter 19: Audiology, Acoustic Countermeasures against Swarms and Building IFF Libraries of (Nichols, et al., Unmanned Aircraft Systems in the Cyber Domain, 2nd Edition, 2019) [22] A summary of findings of this previous work follows.[23]
Acoustic Countermeasures and Building Identify Friend or Foe (IFF) Acoustic Libraries –Revisiting the C-UAS Problem
The Risk of success of Terrorist Attacks on US Air Defense Systems (ADS) via sUAS / UAS is higher and improving because of commercial capabilities and accessibility. Advanced small drones capable of carrying sophisticated imaging equipment, significant (potentially lethal) payloads and performing extensive Intelligence, Surveillance, and Reconnaissance (ISR) missions are readily available to civilian market. They pose a significant threat to civilian and military UAS operations and safety in the NAS. The highest threats to ADS are presented by hostile UAS SWARMS.
Problem Solution
The author’s research suggests that UAS SWARMS can be both identified (IFF) and destabilized / mitigated /eliminated / countered in the air by applying harsh acoustic countermeasures at resonance frequencies. UAS (in any formation – especially SWARMS) present detectable acoustic signatures that can be collected in an IFF sound libraries and like fingerprints or DNA they are unique to the make, model and origin manufacturer. Once identified as hostile, UAS (SWARM units) may be destabilized by harsh – explosive amplitude acoustic countermeasures to the MEMS or rotor base of the UAS’s causing destabilization of the UAS and grounding. Emergency and waypoint recovery functions do not work under this approach.
Sound as a Weapon and Countermeasure
Next, we add sound to the group of DEWs. The approach taken is to discuss fundamental concepts, then propagation (travel) towards the target, and lastly, interaction with the target and the mechanisms by which the target is destroyed.
Essentials of Audiology
The question is why would hitting a UAS going at 100+ mph or more be susceptible to a loud noise hitting the MEMS under the rotors or the rotors themselves? Why would this same noise or variation thereof be capable of characterization of the UAS’s of a hostile or friendly power? It is not something we can just take for granted without understanding the essentials of audiology underlying the process.
Detection Signatures
(Nichols, et al., Unmanned Aircraft Systems in the Cyber Domain, 2nd Edition, 2019) found that UAS / UAVs are detected by their signatures: noise (acoustic), optical (visible), infrared (thermal) and radar (radio). “These acoustic or electromagnetic emissions occur at the following wavelengths: (Austin, 2010)
- A) Noise (acoustic) [16 m-2 cm, or 20 – 16000 Hz]
- B) Optical (visible) [0.4 – 0.7 um]
- C) Infrared (thermal) [0.75 um – 1 mm]
- D) RADAR (radio) [3 mm – 3 cm]” (Austin, 2010)
“If the designer is to reduce the vehicle detectability to an acceptable risk level, it is necessary to reduce the received emissions or reflection of the above wavelengths (expressed as frequencies) below the threshold signature value. A good portion of the UAS signatures are a function of the operating height of air vehicle.” (Austin, 2010) The concept of frequency as a fifth realm can be elucidated in terms of targets, battlespace, and wavelengths. (Nichols, et al., Unmanned Aircraft Systems in the Cyber Domain, 2nd Edition, 2019) One of the parameters, range was a serious limitation on performance. Range has a significant impact on radio transmission. Depending on the environment, the strength of a received signal, T, is a function of the square or fourth power of a distance, d, from the transmitter. (Adamy D. -0., 2015)
In Chapters 8 and 14 of (Nichols, et al., Unmanned Aircraft Systems in the Cyber Domain, 2nd Edition, 2019), EMS was presented with emphasis on sound frequencies, many out of human hearing range. The author’s experiments were performed using DJI Phantom 4 at 400 ft. This is not a tactical distance for a C-UAS countermeasure. However, the LRAD 1000X made by LRAD Corporation is effective to a 1.864 miles. See Figure 10-8. Appendix 10-2 gives the LRAD 1000X specifications. (LRAD Corporation, 2019) Longer-range models are in pipeline. The upper end of noise – Stealth acceptability is 17,150 Hz. The Stealth range is 20 Hz – 17,150 Hz. (Austin, 2010)
Figure 10-8 LRAD 1000x C-UAS

Source: (LRAD Corporation, 2019) [24]
Designing a UAS for Stealth
Stealth means “to resist detection.” Stealth applies to the air vehicle and materials visible to the enemy plus the internal SAA systems that control / create noise, heat, electromagnetic emanations, and changes in light. For ISR platforms and missions, it is essential the UAS systems be undetected in operation. “It is desirable not to alert the enemy (military) or criminals (police) to the ISR operation.” It can be assumed that the enemy is using counter-UAV operations and weapons. Stealth design protects the air vehicle from these counter – UAV measures. Stealth in civilian operations results in minimal environmental disturbances. (Austin, 2010)
From a personal privacy standpoint or in civil airspace it is desirable to have the UAV stealth features turned off. [It should be as if we had flicked a switch.] (Austin, 2010) Thinking again about a team or swarm of UAS, the low-hanging fruit target is US communications. We depend on connectivity in everything we do: daily lives, social interactions, business, manufacturing, government, transportation, computers and warfare to name just a few in the extensive list. Connectivity is any technique for the movement of information from one location or player to another. Consider the economic impact of having our critical infrastructure (banking, air transportation, etc.) shut down. Damaging the connectivity of system is real damage. We measure connectivity in terms of information flow. In warfare, this is called Information Operations (IO). Fundamental to IO is the frequency at which the information is transmitted or received. Returning to stealth with respect to UAS design, we note that the intelligence, surveillance, reconnaissance and weapons payload-delivery functions of UAS. These are all IO operations and frequency is at the heart of their success against or denial by the enemy. (Adamy D. -0., 2015)
Acoustic Signature Reductions
“Aircraft noise may be the first warning of its presence; however, it may not immediately be directionally/locatable for detection.” “UAS noise emanates predominantly from vortices, tips of wings, rotors, or propellers. Lowering wingspan or blade span enhances acoustical stealth.” Conventional propulsion systems are a concern because of the noise of combustion. Electric motors develop virtually no noise. “Reducing mass and aerodynamic drag of the UAS reduces noise generation.” (Austin, 2010) The human ear is a problem for the designer. “It is most sensitive to frequencies around 3500 Hz and can hear sound down to a practical threshold of 10 dB. For a given sound pressure level, attenuation of sound with distance in air and insulating material varies as the square of the sound frequency. Low frequency sound presents a greater problem for UAS stealth design.” (Austin, 2010)
Audiology Fundamentals
- The science of sound is called acoustics, which a branch of physics. Appendix 10-1 displays the principal physical quantities in MKS, cgs, and English units. It is the starting point of a trip uphill to resonance frequencies. Sound is small portion of the EMS.
Figure 10-9 shows the conversion for sound and acoustic wave period to frequency and back. (Adamy D. -0., 2015) Figure 10-10 shows the Sound EMS regions (Adamy D. -0., 2015)
Figure 10-9 Conversion for sound and acoustic wave period to frequency and back
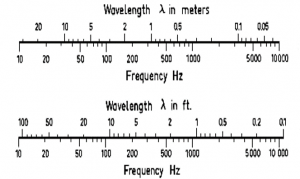
Source: (TRS S. , 2018)
Figure 10-10 Sound EMS Regions
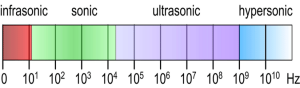
Source: (TRS S. , 2018)
Acoustic waves and Sound Waves in Air
- Sound waves are EMS waves which propagate vibrations in air molecules. The 1986 standard speed of sound, c, is 331.3 m/s or 1125.33 ft/s at a temperature, T = 0 degrees Celsius.”(TRS S. , 2018) “The formulas and equations for sound are
c = L x f; L = c /f = c x T; f=c /L Equation 10-1
Where:
T = time- period or cycle duration and T = 1/ f and f = 1 / T.
The unit for frequency is Hertz = Hz =1/s. The unit for wavelength, L is meters, m. The time-period or cycle duration, T is sec, s. The wave speed or speed of sound, c, is meters/sec, m/s.” (TRS S. , 2018)
(Austin, 2010) states that the design limit for UAS Stealth for acoustic (noise) or sound waves is “[16 m-2 cm, or 20 – 16000 Hz].” The Stealth range is 20 Hz – 17,150 Hz. [25]
- Hearing range describes the range of frequencies that can be heard by humans, (aka range of levels). The human range is commonly given as 20 to 20,000 Hz, there is considerable variation between individuals, especially at high frequencies, and a gradual loss of sensitivity to higher frequencies with age is considered normal. Sensitivity also varies with frequency, as shown by equal loudness contours. (Rosen, 2011) See Figure 10-11.[26]
Figure 10-11 Equal Loudness Contours
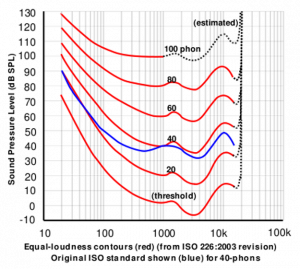
Source: Equal -Loudness Contours (Fletcher, 1933) (Rosen, 2011)
Intensity and Inverse Square Law
- “Sound radiates outward in every direction from its source. This constitutes a sphere that gets larger and larger with increasing distance from the source.”(Entokey, 2019) Figure 10-12 shows the relationship between Intensity and the Inverse Square Law.(Uni-wuppertal, 2019) Intensity (I) (power divided by area) decreases with distance from the original source because of finite amount of power is spread over increasing surface area. (Entokey, 2019) Proportionately less power falls on the same unit of area with increasing distance from the source. (Gelfand, 2004) [27] [28]
Figure 10-12: Inverse Square Law, Sound Intensity
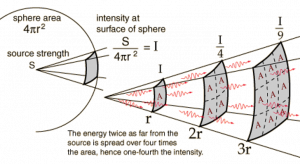
Source: (Uni-wuppertal, 2019)
- Figure 10-13 shows common decibel and Intensity levels within the hearing range. This does not consider environment, frequency differences or noise (discussed presently). It does show the ease of which decibels may be used to rank the sound intensity levels which vary greatly in magnitude. Hearing aids are effective from about 6 –90 decibels. Above 90 dB, they can dampen but not eliminate the very loud sounds unless there is complete loss of hearing.
The Nature of Sound
- Sound is defined as a form of vibration that propagates through the air in the form of a wave. Vibration is the to-and-fro motion (aka oscillation) of an object. Some examples are playground swing, tuning fork prong, air molecules and UAS rotor blades [circular motion]. The vibration is called sound when it is transferred from air molecule to air molecule. This transfer may be simple like a tuning fork or a very complex pattern like the din in a school cafeteria. Naturally occurring sounds are very complex. (Entokey, 2019) UAS sounds are not natural and supported by machinery, hardware and software. Three weaknesses of the UAS are the MEMS, gimbal assembly and rotors. Although stealth mechanisms may be employed to reduce noise emissions, the former parts are exposed. They do produce discernable signatures.
- A tuning fork illustrates the oscillations of sound. After being struck, the tuning fork vibrates with a simple pattern that repeats itself over time. (Entokey, 2019) Figure 10-14 shows that the tuning fork when struck exerts a force on the air molecules which alternatively exerts a high pressure (compression) and a low pressure (rarefaction) zones. The zones exhibit wave amplitude and wavelength as a function of air pressure and distance. The sound wave is distributed in 360 degrees through the air.
Figure 10-13 Shows common decibel and Intensity levels within the hearing range.
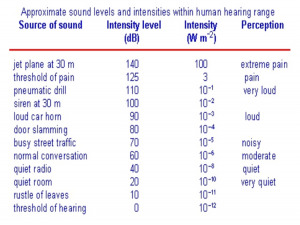
Source: (Carter, 2012)
Figure 10-14 diagrams tuning fork oscillations over time. Sounds that are associated with simple harmonic motion are called pure tones. Vertical displacement amount of the tuning fork prong displacement around its resting position. Distance from left to right represents progression of time. One complete round-trip or replication of an oscillating motion is called a cycle. The number of cycles occurring in one second is the frequency. The duration of one cycle is called its period. This form of motion occurs when a force is applied to an object having properties of elasticity and inertia. Simple harmonic motion (SHM) shows the same course of oscillations as in Figure 10-15 because they repeat themselves at the same rate until friction causes dampening of the waveform. (Entokey, 2019) and (Gelfand S. A., 2009)
Figure 10-14: Tuning for Oscillations
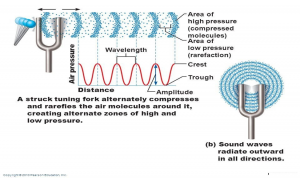
Source: (Pierson, 2019)
Figure 10-15: Tuning fork oscillations over time
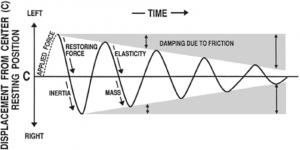
Source: (Entokey, 2019)
Other Parameters of Sound waves
- Probably the most useful SHM waveform is the sinusoidal wave or sine wave.[29]
The number of times a waveform repeats itself in one second is known as the frequency or cycles per second (CPS). (Gelfand S. A., 2009)Two useful relationships are: f = 1/ t or t = 1/f; where f is the frequency in cps and t is the period in seconds. Amplitude denote the magnitude of the wave. The peak- to – peak amplitude is the total vertical distance between negative and positive peaks. The peak amplitude is the distance from the baseline to one peak. The magnitude of sound at any instant is the instantaneous amplitude. Wavelength (λ) is the distance traveled between one peak and the next. (Gelfand, 2004) Wavelength formula is: λ = c / f, where c is the speed of sound in air (344 m/s. f is the frequency of sound in Hz. Similarly, frequency is inversely proportional to wavelength or f = c / λ. (Gelfand S. A., 2009) Another interesting sound parameter is Pitch. Pitch is the quality of sound and especially a musical tone governed by the rate of vibrations producing it. It is the degree of highness or lowness of sound. (Merriam-Webster, 2019)
Complex waves
- When two or more pure-tone waves are combined, the result is a complex wave. (Gelfand, 2004) They may contain any number of frequencies. Complex periodic waves have waveforms that repeat themselves. If they don’t, they are aperiodic. Combining waves may reinforce themselves or cancel themselves whether they are in phase or out. The lowest frequency component of a complex periodic wave (like a combination of sign waves) is called its fundamental frequency. (Gelfand, 2004)
- Harmonics are whole number or integral multiples of the fundamental frequency. Waveforms show how amplitude changes with time. (Gelfand, 2004) Fourier’s Theorem shows that complex sound waves can be mathematically dissected into its pure tones. Of more interest to UAS designers are aperiodic sounds which are made up of components that are not harmonically related and do not repeat themselves over time. The extreme cases of aperiodic sounds are transients and random noise. A transient is an abrupt sound that is very brief in duration. Random noise has a completely random waveform, so it contains all possible frequencies in the same average amplitude over the long run. Random noise is also called white noise like white light because all possible frequencies are represented.
Standing Waves and Resonance
- We have arrived at the crux of the acoustic CM discussion, the natural or resonating frequency. “The frequency(ies) at which a body or medium vibrates most readily is called its natural or resonant frequency(ies).”(Gelfand S. A., 2009) Differences in resonance frequency ranges enable different devices to act as filters by transmitting energy more readily for certain high, low, or band-pass frequencies. UAS with multiple rotors circulate the rotors to gain lift and / or hold steady / or descend in altitude. Four, six, eight – rotor UAS maintain control via internal SCADA systems and send critical information through a MEMS component located at the bottom of rotors. Rotor frequencies are coordinated, monitored, and position -controlled through the MEMS and in-board computers. Even though the rotor(s) motions are spinning in circular fashion, the sound wave generation is not curvilinear, or aperiodic but transferred up through the Y axis and back again to its base as it ascends in altitude. There is a tendency to maintain equilibrium in terms of position of the UAS.
- The author contends that the UAS rotor systems act like vibrating strings and resonance frequency information can be approximated by this approach. An example of a vibrating spring is when you “pluck” a guitar. The waves initiated move outward toward the two tied ends of the string. The waves are then reflected back, and they propagate in the opposite directions. The result is a set of waves that are moving toward each other, resulting in a perturbation sustained by continuing reflections from the two ends. The superimposed waves interact and propagate and appears as a pattern that is standing still. Peaks (maximum displacement) and no displacement (baseline crossings occur at fixed points along the string.[30] Places along the spring where zero displacement in the standing wave pattern are called nodes. (Gelfand, 2004) Locations where the maximum displacement occurs are called antinodes. See Figure 10-16.
Figure 10-16: Standing Wave
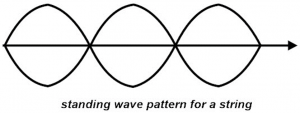
(Administrator, 2015)
- “The fundamental frequency is defined as the lowest frequency of a periodic waveform. It is generally denoted as ‘f’. The lowest resonating frequency of a vibrating object is called as fundamental frequency.”(Administrator, 2015)
- “Harmonic is a frequency, which is an integer multiple of the fundamental frequency. The forced resonance vibrations of an object are caused to produce standing waves. At the natural frequency it forms a standing wave pattern. These patterns are created at specific frequencies, they are called Harmonic Frequencies or Harmonics.”(Administrator, 2015)
- “The sound produced by a wave form at its harmonic frequency is very clear, and at other frequencies we get noise, and cannot hear the clear sound of waves. Harmonics may occur in any shaped wave forms, but mostly they occur in sine waves only. Non – sinusoidal wave forms, like triangular and saw tooth wave forms are constructed by adding together the harmonic frequencies. The word harmonic is generally used to describe the distortions caused by different un- desirable frequencies called noise, of a sine wave.”(Administrator, 2015)
- “Node and antinodes occur in a wave form. So, the waves have harmonic frequency in them. The fundamental frequency is the smallest frequency in a harmonic. Hence there is only a single anti-node occurs between them. This Antinode is middle of the two nodes. So, from this we can say that the guitar string produces longest wavelength and the lowest frequency.”(Administrator, 2015)
- “The lowest frequency produced by any instrument is called the fundamental frequency. This is also known as first harmonic of the wave. In words of fundamental frequency, harmonics are the integer multiples of the fundamental frequency.” (Ex: f,2f,3f,4f, etc.… are harmonics.) (Administrator, 2015)
- “Because of multiple integers of fundamental frequency, we will have n number of harmonics like 1st harmonic, 2nd harmonic,3rd harmonic, and so forth.”(Administrator, 2015) “The fundamental frequency is also called as First harmonic. In the first harmonic, we have two nodes and one antinode. he numbers of antinodes are equal to the integer multiples of specific harmonics. i.e., for 1st harmonic we have 1 antinode, for 2nd harmonic we have 2 antinodes etc.”(Administrator, 2015)
MEMS
- What is a MEMS and how does it relate to the UAS gyroscope? As shown in Figure 10-17 MEMS Gyroscope, MEMS (Micro-Electro-Mechanical-Systems) gyroscopes are located in the rotor systems of most drones. Visualization of a MEMS gyroscope is a single proof mass suspended above a substrate The proof mass is free to oscillate in two perpendicular directions, the drive and sense direction.(Said Emre Alper, December 2008)
Resonance Effects on MEMS
- Achieving resonance frequencies can have a significant effect for countering hostile UAS:
- MEMS Gyroscope can be degraded using harsh acoustic noise
- MEMS Gyroscope has a resonant frequency that is related to the physical characteristics of its structure (Usenix.org, 2019)
- MEMS Gyroscopes have resonant frequencies much higher than can be heard (audible and ultrasonic ranges)
- Unexpected resonance output caused from an attack will cause the rotor system to malfunction
- Rotors will spin at differing speeds causing the drone to become unstable and crash
Figure 10-17: MEMS Gyroscope
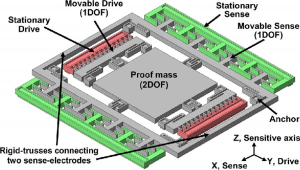
Source: (Said Emre Alper, December 2008)
Resonance Tuning
- In the operation of MEMS gyroscopes, the bending changes the capacitance between the sensing mass and the sensing electrode, and this capacitance change is sensed as the output of the gyroscope By using an additional feedback capacitor connected to the sensing electrode, the resonant frequency and the magnitude of the resonance effect can be tuned Resonance can be induced by a malicious attacker, if resonant frequencies exist in gyroscopes.(Nichols R. K., Hardening US Unmanned Systems Against Enemy Counter Measures, 2019)
What is the “so what” for Acoustics?
- “Passive detection is much cheaper and cost effective to operate vs a complex radar system for a single installation (limited by detection range ~350ft).MEMS gyroscopes contained in rotor systems are very susceptible to malfunction when struck with rough noise that resonates inside the MEMS. Offensive acoustic systems are currently mounted, could become man portable. Offensive systems are not detected by National ELINT assets not looking for acoustic energy signatures, enemy can remain hidden from detection when using acoustics.”(Nichols R. K., Hardening US Unmanned Systems Against Enemy Counter Measures, 2019)
- What is an Acoustical attack on the UAS Gyroscope?
There are two possibilities: compromising the sound source or drone on drone attack:
Compromising the Sound Source
- UAM with speakers (consider police and military operations or search-and-rescue operations)(Usenix.org, 2019)
- Counter the source of the sound from the speaker with different frequency sound
- Jamming attack aims to generate ultrasonic noises and cause continuing vibration of the membrane on the sensor, which make the measurements impossible
- Level of noise causes performance degradation
Drone on Drone Attack
- Taking a picture of a moving object from UAM
- An adversary drone equipped with a speaker could steer itself toward a victim drone and generate a sound with the resonant frequency of the victim’s gyroscope to drag it down(Usenix.org, 2019)
What are Countermeasures for Acoustic attack on Gyroscope
- Countermeasures for attacks on gyroscope include: Physical Isolation – provide physical isolation from the sound noise; Surrounding the gyroscope with foam would also be a simple and inexpensive countermeasure; using a differential comparator; using an additional gyroscope with a special structure that responds only to the resonant frequency so the application systems can cancel out the resonant output from the main gyroscope and improving detect and cancel out analog sensor input spoofing against CIEDs.(Nichols R. K., Hardening US Unmanned Systems Against Enemy Counter Measures, 2019)
In terms of UAS Countermeasures, why are Acoustics so important? (Nichols R. K., Hardening US Unmanned Systems Against Enemy Counter Measures, 2019)
- They are important because:
- Offensive systems use ultrasonic frequency resonance
- Cannot be heard by humans when used to intercept a drone
- Passive systems are difficult, if not impossible, to detect
- Able to identify and track drone based on acoustic and/or visual signature
- Acoustic detection systems are limited in range ~ 350 ft to 500 ft due to environmental variables BUT commercial companies like LRAD, Corporation have developed long range acoustic devices which can detect a UAS up to a mile away at altitude.
- Can be a cost-effective way to defend a small area –especially against SWARM Attack
What are the Acoustic Detection Issues?
- Detection relies on uniqueness of the UAS and hearing capabilities at low frequencies:
- Detects drones by recognizing the unique sounds produced by their motors
- Rely on a library of sounds produced by known drones, which are then matched to sounds detected in the operating environment, however,
- The human ear is a problem for the designer
- It is most sensitive to frequencies around 3500 Hz and can hear sound down to a practical threshold of 10 dB
- For a given sound pressure level, attenuation of sound with distance in air and insulating material varies as the square of the sound frequency
- Low frequency sound presents a greater problem for UAS stealth design
- The greater noise problem is posed by smaller UAS using piston engines
- Sound comes from their internal combustion and exhaust systems
- Sound emission can be reduced with sound-absorptive materials, silencers and mufflers and by directing the intake and exhaust manifolds upward
- Level of sound detected depends on the level of background noise for sound contrast
- Limited range to 500 feet (experimental and research – not commercial or military)
- Noisy backgrounds (airports, city downtown) limit detection & interdiction
- Drone tuning (changing the stock propellers) limits detection / Interdiction
Is Acoustic Quieting possible?
- “Yes, under certain conditions:
- Disguise sounds from sensors to eliminate its noise and passive echoes
- “Acoustic superiority” used by the Navy to mask detection of U.S. submarines
- Acoustic technology is “passive,” meaning it is engineered to receive pings and “listen” without sending out a signal which might reveal their location to an enemy
- Increased use of lower frequency active sonar and non-acoustic methods of detecting.”(Nichols R. K., Hardening US Unmanned Systems Against Enemy Counter Measures, 2019)
- How has the Long-Range Acoustic Device (LRAD) used as a sonic weapon?(LRAD, 2019)
It has been used primarily for denying GPS navigation:
GPS Denied Navigation
- GPS navigation relies on measuring the distance or delay, to several known transmitters in order to triangulate the mobile receiver’s position
- GPS-denied environment presents navigation challenges for UAV and UAM
- These areas include urban canyons, forest canopy, etc.
- Strike Resonance frequency – which disrupts balance (vehicles tilt, orientation & rotation)
UAS Collaboration – SWARM
A UAS SWARM as a uniform mass of undifferentiated individual’s w/o Chief at automation level 4 or 5. SWARMs exhibit the following advantages:
- Efficient based on numbers, emergent large group behaviors, and reactions
- Not controllable or automated, decentralized intelligence
- Think shoal of fish w/ evolving local rules; highly resistant form
- Not changing based on survivability of members, no hierarchy
SWARM Countermeasures include disruption, i.e. changing the Strategic Global View of SWARM (its only real vulnerability), complete Defender collaboration with multiple kinetic and non-kinetic countermeasures, and use of Acoustic Countermeasures for identification as friend or foe (IFF) based on a library of manufacture detection signatures and complete , abrupt rotor disablement by attacking the SWARM units with resonant, loud ( 100-140 dB) sound noise aimed directly at the MEMS gyroscopes or close by on the unit. [Think of glass breaking at resonance frequency or a submarine under depth charge attack. The former breaks by super- excited molecules in the glass and literally shakes apart. The latter is destroyed by violent shaking of the submarine so that its parts break and flooding ensue. It is not necessary to hit the submarine directly because explosions in water, hence sound waves and explosive forces, carry very far and effectively to the target.]
South Korean experiment
A paper by Yunmonk son, et. Al. From the Korean advanced institute of science and technology (KAIST), in the authors judgement, is the seminal paper on taken down drones using sound noise on gyroscope sensors! (Yunmonk Son, 2015) It is required reading for my students.
(Yunmonk Son, 2015) describes the relationship between Sound Pressure Level (SPL) and Sound Amplitude and derives the attack distance, d as (in dB):
SPL = SPLref + 20 log (A / Aref ) Equation. 10-2
Where SPL = sound pressure level, SPLref is the reference, A and Aref are the amplitudes of the source and reference point. Using real-world experiments (Yunmonk Son, 2015) found that:
SPL = SPLref – 20 log (d / dref ) Equation. 10-3
Where d, dref are the attack scenario distances.
KAIST under (Yunmonk Son, 2015) primary conclusions are:
- “Many sensing and actuation systems trust their measurements and actuate according to them. Unfortunately, this can lead to security vulnerabilities that cause critically unintended actuations.
- The sound channel can be used as a side channel for MEMS gyroscopes from a security point of view.
- 15 kinds of MEMS gyroscopes were tested, and seven of them were found vulnerable to disruption using intentional noise.
- The output of the vulnerable MEMS gyroscopes was found using a consumer-grade speaker to fluctuate up to dozens of times as a result of the sound noise.
- Authors found that an attacker with only 30% of the amplitude of the maximum sound noise could achieve the same result (disruption) at the same distance.
- At 140 decibels, it would be possible to affect a vulnerable drone up from around 40 meters away,
- Some drone gyroscopes have resonant frequencies in both the audible and ultrasonic frequency ranges, making them vulnerable to interference from intentional sound noise.
- Authors found that accelerometers integrated with MEMS gyroscopes were also affected by high-power sound noise at certain frequencies.”(Yunmonk Son, 2015)[31]
Noise
Loud and abrupt sound as a countermeasure also brings the problem of exposure and loss. Chapter 17 of (Gelfand S. A., 2009) discusses the effects of noise and hearing conservation. Chapter 20 of (Gelfand S. A., 2009) discusses occupational standards. Safety is an important topic but outside the scope of this writing.
Real World C-UAS
Time to move from the theoretical into the practical. The balance of this chapter will be devoted to a sample of deployed ADVANCED UAS / C-UAS multi-mission systems globally. They can fight back!
Chinese CH7
At the air show China 2018 in Zhuhai, South China, The UAV – CH7 was unveiled. The CH7 is China’s new generation stealth combat unmanned aerial vehicle. The CH7 makes China the second country, followed by the US, to produce HALE combat vehicles with advanced penetration capabilities. The CH7 has internal weapons bays, making it capable of launching anti-radiation missiles, air-to-ground (ATG) or anti-ship missiles and long -distance precision guided bombs. Its missions favor high altitude, stealth capacity and endurance under dangerous conditions such as C4ISR or launching missiles at HVTs. The CH7 is 10m long and has a wingspan of 22 m. It weighs 13,000 kg, cruises at 0.5-0.6 Mach and can fly for 15 hours. The CH7 can intercept radar electronic signals and simultaneously detect, verify and monitor HVTs such as US command stations, missile launch sites and navy vessels. (Defense Editor, 2018) See Figure 10-18.
Russian Okhotnik aka “Hunter Drone”
Just as General Michael Hayden and Roger N. McDermott predicted in their report, Russia’s Electronic Warfare Capabilities to 2025: Challenging NATO in the Electromagnetic Spectrum (McDermott, September 2017), along comes the Russian Okhotnik drone. Flying with the fifth generation Su-57, the Okhotnik, or “Hunter,” drone which is able “to broaden the fighter’s radar coverage and to provide target acquisition for employing air-launched weapons.” (Pickrell, 2019)
Figure 10-19 shows the Okhotnik drone flying next to the SU-57, Russia’s most advanced stealth fighter. The latest flight appears to confirm suspicions that the drone was designed to fight alongside and provide critical battlespace information to Russia’s newest fighters. (Pickrell, 2019)
Figure 10-18 Chinese CH7 – UAV

Source: (Defense Editor, 2018)
Figure 10-19 Okhotnik drone flying next to the SU-57, Russia’s most advanced stealth fighter

Source: (Pickrell, 2019)
The Iranian Shahed 129
The Shahed 129 (Persian for Eyewitness) is an Iranian single-engine MALE (UCAV) designed by Shahed Aviation Industries for the (IRGC). The Shahed 129 is capable of combat and reconnaissance missions and has an endurance of 24 hours; it is similar in size, shape and role to the American MQ-1 Predator and is widely considered the most capable drone in Iranian service. (Taghvaee, 2017) See Figure 10-20.
General characteristics from (Taghvaee, 2017)
- Crew: none
- Capacity: 400 kg payload
- Length: 8 m (26 ft 3 in)
- Wingspan: 16 m (52 ft 6 in)
- Height: 3.1 m (10 ft 2 in)
- Powerplant: 1 × Rotax 914 four-cylinder, four stroke Ac engine
- Propellers: 3-bladed
Performance
- Cruise speed: 150 km/h (93 mph, 81 kn)
- Combat range: 1,700 km (1,100 mi, 920 nm)
- Ferry range: 3,400 km (2,100 mi, 1,800 nm)
- Endurance: 24h
- Service ceiling: 7,300 m (24,000 ft)
Armament
- Bombs: 4 × Sadid-345 PGM
Avionics
Oghab-6 electro-optical/infrared sensor
Laser range finder
Figure 10-20 The Iranian The Shahed 129

Source: (Taghvaee, 2017)
In June, U.S. Air Force F-15Es shot down two Iranian UAVs in Syria—both Shahed 129s operated by Iran’s Islamic Revolutionary Guard Corps. These were rare incursions between U.S. and Iranian aircraft in the Middle Eastern country, which Iran has used as a testing ground for the Shahed, one of the most advanced armed UAVs in the Iranian Revolutionary Guard’s Air & Space Force (IRGC-ASF) drone unit. It will continue to be a mainstay of the Iranian fleet for the foreseeable future. (Taghvaee, 2017)
The Israeli Tactical Heron
The Tactical Heron, joins drones that have “hundreds of thousands of operation flight hours.” Designed for missions on the battlefield, the tactical Heron is used by ground troops or coast guards. The new Heron can fly up to 7.3 km. with payloads of 180 kg. (Frantzman, 2019) The Heron is used for ISTAR missions. Figure 10-21 shows the Tactical Heron.
Figure 10-21 Israeli Tactical Heron

Source: (IAI, 2019)
“According to IAI, T-Heron is the best of the best of Heron line, with all its sensors, cameras, intelligence and attack capabilities, but for the “local” tactical level. Only UAV in the world with the abilities of super drones but for tactical levels (according to the ISI). It has a versatile design and is all-weather day and night. It is 30% smaller than the standard Heron, and most importantly, cheaper. It’s for the Brigade tactical level, specifically ground and mechanized forces, and can even be operated by them (without having to bring specialized drone operators). It can be brought to its required location with two trucks and can lift off and land back on very short paved low-level runways. Because it’s mobile and tactical, it can travel with front-line forces with no logistical long tail headaches. It can carry multiple payloads, up to 180 KG, and its gross weight up to 600 KG. It has a flight time of 24 hours, 300 KM range, 23000 ft altitude and has a 10-meter wingspan.” (IAI, 2019)
According to Moshe levy, VP of Aircraft division at IAI, “We are proud to introduce the most recent UAS developed by IAI. Our T-Heron tactical UAS rounds up the range of operational UAS solutions IAI offers to all forces on the battlefield: marine, air, ground, and intelligence. IAI preserves its leadership position in UAS’s with a continuous stream of solutions for the challenges posed by the field.” (IAI, 2019)
IAI doesn’t foresee much maturity problems as it has the same materials and components as the other Heron’s, only in smaller amounts. (IAI, 2019)
USA Predator C Avenger
The General Atomics Avenger (formerly Predator C) is a developmental UCAV built by General Atomics Aeronautical Systems for the US military. Its first flight occurred on 4 April 2009. Unlike the previous MQ-1 Predator and MQ-9 Reaper (Predator B) drones, the Avenger is powered by a turbofan engine, and its design includes stealth features such as internal weapons storage, and an S-shaped exhaust for reduced infrared and radar signatures. The Avenger will support the same weapons as the MQ-9 and carry the Lynx SAR and a version of the F-35 Lightning II’s electro-optical targeting system (EOTS), called the Advanced Low-observable Embedded Reconnaissance Targeting (ALERT) system. The Avenger will use the same ground support infrastructure as the MQ-1 and MQ-9, including the GCS and existing communications networks. (Staff, General Atomics Avenger, 2019)
Predator C Avenger can carry Hellfire missiles and guided bombs and ammunition. The Predator C Avenger is a remotely piloted aircraft developed by GA‑ASI. The first flight of the aircraft was conducted in April 2009. The combat drone has a maximum take-off weight of 8,255kg.It is capable of carrying multiple sensor payloads attached to its wing hard-point mountings while its internal weapons bay can carry precision mutations and large sensors up to 1,588kg. The total payload capacity of the aircraft is 2948kg. Its weapon payload includes Hellfire missiles, guided bomb unit (GBU)-12/49 laser-guided bombs, GBU-31 GBU-32, GBU-38 38 joint direct attack munitions (JDMA) and GBU-39 and GBU-16/48 bombs. The Predator C Avenger offers greater operational and transit speeds than Predator B aircraft. Powered by Pratt and Whitney PW545B turbofan engine, the combat drone is capable of reaching altitudes up to 50,000ft. It has a maximum speed of 400k and endurance of 20 hours. (Army, The world’s top combat drones, 2019) See Figure 10-22.
Conclusions
There are five DE systems (DEW, Laser, Microwave, Particle Beams, Acoustic) which use the EMS to attack and defend against hostile UAS. Acoustic systems have the secondary advantage that their resonance frequencies may be used not only to knock out UASs but also characterize and identify friend or foe (IFF) UASs. All these EMO technologies have varying success rates against SWARMS.
Acoustical defenses show promise in they represent a two-for. Not only can they disrupt the MEMS with explosive sound at resonance frequencies, but every UAS has a unique acoustical signature. These acoustic signatures can be cataloged and used for challenge – response in an Identify Friend or Foe (IFF) algorithm.
The sampling of advanced attack capability UAV from around the world, at the end of this chapter are targets that have the ability to fight back – either with ISTAR, missiles, precision guided bombs (PGB) / (PGM) / missiles or EW countermeasures. They are able to identify the defender’s transmitters. They can put a world of hurt on opposing forces.
Figure 10-22 Predator C Avenger

Source: (Staff, General Atomics Avenger, 2019)
Discussion Questions
- This chapter explores the use of acoustic countermeasures against UAS. The authors contend that every manufactured UAS has unique sound detection signatures. Further these can be libraried and used in a search algorithm to IFF the UAS group or SWARM. At the DoD 7th Annual Summit, (Nichols R. K., Hardening US Unmanned Systems Against Enemy Counter Measures, 2019) the author found that several contractors are actually doing this and building databases. BUT they refuse to share their data because it is proprietary. Assuming this situation cannot be changed, suggest two ways to get around this problem not involving legal actions. What type of research project would you propose to meet an 85% detection criteria that would suffice as an initial IFF database for evaluation?
- Along with attacking the MEMS gyroscopes to disable the UAS rotor, propose an experiment to use acoustic countermeasures on the UAS internals, such as SCADA, payload, navigation, internal clocks, internal computer, battery, etc. Perhaps loud noise can disrupt additional UAS features?
- This chapter has discussed sound in the in the extended hearing ranges from 10 Hz to 20,000 Hz. Many UAS are designed for higher frequencies, i.e. ultrasonic and hypersonic. Propose an experiment to test sound disruption effects at the higher frequencies. (Drones, 2017) Quad Star Drones has some interesting “takes” on hypersonic flight and Mach 0.8 speeds.
- There was a fascinating story in the 4 November 2019 web-issue of Popular Mechanics about drones being launched from submarines. (Mizokami, 2019) See: https://hmg.h-cdn.co/videos/missle-rc-illustration-1572620289.mp4 The article is critical of carrier warfare and suggests that submarine launched drones would change the way carriers are deployed.
Assignment: read the article. Then you be the designer to tie it all together. How would you do it?
Much of the tech needed to develop drone-launching submarines—such as creating a large submersible or controlling drones at sea—has already been mastered. When someone ties it all together, we could see (or rather, not see) a naval event where carriers from both sides are totally underwater.
Now that you have it tied together and plan to bring this new form of warfare, now defend against it. What technologies would you use from this chapter?
REFERENCES
Adamy, D. -0. (2015). EW 104 EW against a New Generation of Threats. Boston: Artech House.
Adamy, D. (2001). EW 101 A First Course in Electronic Warfare. Boston, MA: Artech House.
Adamy, D. L. (2004). EW 102 A Second Course in Electronic Warfare. Boston: Artech House.
Adamy, D. L. (2015). EW 104 EW Against a New Generation of Threats. Boston: Artech House.
Alford, L. (2000). Cyber Warfare: Protecting Military Systems. Acquisition Review Quarterly.
Angelov, P. (2012). Sense and avoid in UAS research and applications. Hoboken: NJ.
Army, U. (1992, November 23). US Army Field Manual FM 34-40-7. Communications Jamming Handbook.
Barnhart, R. K. (2012). Introduction to Unmanned Aircraft Systems. New York: CRC Press.
Beaudoin, L. e. (2011). Potential Threats of UAS Swarms and the Countermeasures Need. ECIW.
Burch, D. (2015). RADAR for Mariners. New York: McGraw-Hill.
Clothier, R. R. (2011). The Smart Skies project. IEEE Aerospace and Electronic Systems Magazine.
David H. Staelin, A. W. (1998). Electromagnetic Waves. Upper Saddle River, NJ: Prentice Hall.
Fitts, R. (1980). The Strategy of Electromagnetic Conflict. Los Altos, CA: Peninsula Publishing.
Foley, W. S. (March, 1979). Ancient Catapults. Scientific American, 240, 150.
Gelfand, S. A. (2009). Essentials of Audiology, 3rd Edition. Stuttgart, DE: Thieme.
Halsam, C. M.-S. (1982). Small Arms and Cannons. Oxford: Brassey’s Publishers.
Hubbard, R. K. (1998). Boater’s Bowditch. Camden, MA: International Marine.
Marshall, D. M. (2016). Introduction to Unmanned Aircraft Systems, 2nd Edition. New York: CRC Press.
Merriam-Webster. (2019, May 17). Merriam-Webster Online Dictionary.
Merrick, K. (2016). Future Internet. 10.3390/fi8030034 Review, 8(3), p. 34.
Moir, I. &. (2006). Military Avionics Systems. New York City, NY: Wiley.
Moir, I. a. (2006). Military Avionics Systems. New York: Wiley Aerospace Series.
Nichols, R. K. (1996). Classical Cryptography Course, Volume I. Laguna Hills, CA: Aegean Park Press.
Nichols, R. K. (1999). The ICSA Guide to Cryptography. New York, NY: McGraw Hill.
Schneiner, B. (1996). Cryptography. New York, NY: John Wiley.
Singer, P. W. (2010, February 25). Will Foreign Drones One Day attack the US? . Newsweek.
Studios, D. D. (2017). Boaters Ref. USA.
Usenix.org. (2019, 6 9). MEMS, Drones, & Sound Sourcing. Retrieved from Usenix.org: www.usenix.org
Vernard Foley, G. P. (January, 1985). The Crossbow. Scientific American, 252, 104.
Appendix 10-1: Standard Acoustic Principal Physical Properties
| Quantity | Formula | MKS (SI)Units | Cgs Units | Comments | English Units |
| Mass (M) | M | kilogram (kg) | gram (g) | 1kg = 103 g
1kg = 2.2046 lbs |
pounds (lbs) |
| Time (t) | t | seconds, (s) | s | s | |
| Area (A) | A | m2 | cm2 | 1 m2 = 104 cm2 | ft2 |
| Displacement (d) | d | meter (m) | centimeter (cm) | 1m = 102 cm | ft |
| Velocity (v) | v = d/t | m/s | cm/s | 1 m/s = 102 cm/s | ft/s |
| Acceleration (a) | A = v/t | m/s2 | cm/s2 | 1 m/s2 = 102 cm/s2 | ft/s2 |
| Force (F) | F = MA = Mv/t
Mv = Momentum |
kg x m/s2
newton (N) |
g x cm2
dyne
|
1N = 105 dynes | 1lbf = 1 lb x 32.174049 ft -lbs /s2 = 9.80665 m/s2 |
| Pressure (p) | p = F/ A | N /m2
Pascal (Pa) |
dynes /cm2
microbar (µbar) |
20 µPa = 2 x 10-5 N/m2
reference value |
Psi = lbf /in2
1 N/m2 = 0.000145 psi
|
| Work (W)
|
W =Fd | N x m
Joule
|
dyne x cm
erg |
1 j = 107 erg/s
Energy -capability to do Work. Potential energy for a body at rest and kinetic energy for a body in motion. |
BTU
[British Thermal Unit] 1 BTU = 1055.056 joules |
| Power (P) | P = W/t =
Fd/t =Fv |
Joules/s
watt (w) |
erg/s
watt (w) |
1 w = 1 J/s = 107 erg/s | 1 watt = 3.412 BTU/hr |
| Intensity (I) | I = P/A
I = P / 4ℼr2 Based on sphere radius
|
w/m2 | w/cm2 | 10-12 w/m2
reference value |
Sources: (Entokey, 2019) & (Studios, 2017) & (Nielsen, 2012)
Appendix 10-2 LRAD 1000X, Source: (LRAD Corporation, 2019)
Communicate Even Further with Longer Range AHD
The LRAD 1000Xi is a power efficient, long distance communication system designed for applications ranging from critical infrastructure protection to territorial water, border and port security, and large vessel and vehicle installations.
Featuring a rugged carbon fiber emitter head integrated with electronics and amplification, the LRAD 1000Xi comes standard with an MP3 Control Module for playing recorded messages and an all-weather microphone for live broadcasts. The MP3 Control module also enables remote operation of the device from safe locations.
Superior voice intelligibility and an extended frequency range ensure broadcasts are clearly heard and understood over wind, engine and background noise. The LRAD 1000Xi provides a long-range communications capability to issue authoritative voice commands and attention-commanding deterrent tones to determine intent, safely enhance response capabilities, modify behavior, and scale the use of force if necessary.
Features
- Rugged, military tested construction
- Low power requirements
- All-weather use
- Easy to use
- Increased coverage with single operator
- Safer alternative to non-lethal deterrent measures
- HD Camera (optional)
Directionality, Power Efficiency & Range
- Highly intelligible communication up to 3,000 meters (1.864 miles)
- Safely communicates beyond standoff distances to determine intent
- Variable beam width for extended coverage
- Clear, long range, directional communication
- Establishes instant acoustic standoff perimeter
LRAD 1000Xi Specifications
Acoustic Performance
- Maximum Continuous Output: 153 dB SPL @ 1 meter, A-weighted
- Sound Projection +/- 15° at 1 kHz
- Communications Range: Highly intelligible voice messages over distances up to 3,000 meters; max range of 1,250 meters over 88 dB of background noise.
6+ dB above background noise is based on field trials conducted by independent sources.
Environmental Performance
- Hot Operating Temperature: MIL-STD-810G, Method 501.5, Procedure II, Design type Hot, 60°C
- Cold Operating Temperature: MIL-STD-810G, Method 502.5, Procedure II, Design type Basic Cold, -33°C
- Hot Storage Temperature: MIL-STD-810G, Method 501.5, Procedure I, 70°C
- Cold Storage Temperature: MIL-STD-810G, Method 502.5, Procedure I, -40°C
- Operating Humidity: MIL-STD 810G, Method 507.5, Procedure II – Aggravated Cycle
- Rain: MIL-STD-810G, Method 506.5, Procedure I, Blowing rain
- Salt Fog: MIL-STD-810G, Method 509.5
- Shipboard Vibration: MIL-STD-167-1A
- Shipboard Shock: MIL-S-901D, Class I, Shock grade B
- Random Vibration: MIL-STD-810G, Method 514.6, Wheeled vehicles
- SRS Shock: MIL-STD-810G, Method 516.6, Procedure I, (Functional shock)
Tested by National Technical Systems (NTS) following MIL-STD-810G, MIL-STD-167-1A & MIL-S-901D
Mechanical
- Dimensions: 36” ACOUSTIC PERFORMANCE x 40“ ACOUSTIC PERFORMANCE x 13” D (91cm x 102cm x 33cm)
- Weight: 87 lbs. without accessories (39.4kg)
- Construction: Molded low smoke composite, 6061 Aluminum, 316 Stainless hardware
Electrical Requirements
- Typical Power Consumption: 720 Watts (With tone)
- Normal Power Consumption: 190 Watts (With voice content)
- Power Input: 90-260VAC 50/60Hz Typical Power with warning tone. Normal Power Consumption: with voice content, sound projection is wide and voice boost is off.
Safety
MIL-STD-1474D
MIL-STD-1474D standard establishes acoustical noise limits and prescribes testing requirements and measurement techniques for determining conformance to the noise limits specified therein.
Electromagnetic Compatibility (EMC)
FCC Part 15 class A radiated emissions, CE
Requirements for the control of electromagnetic interference characteristics of subsystems and equipment.
Endnotes
[1] “Drone” in this document refers to small unmanned aircraft, remotely piloted or autonomous, fixed-wing or rotary blade, controlled remotely or use satellite navigation systems, or RTF or tethered or RC models.
[2] In 2018, the Home Office ran a public consultation, Stop and search: extending police powers to cover offences relating to unmanned aircraft (drones), laser pointers, and corrosive substances. The result was published in 2019
[3] A fascinating study by NATO on Transforming Joint Air and Space Power via The Journal of the Joint Air Power Competence Center (JAPCC) available for download at: https://www.japcc.org/wp-content/uploads/JAPCC_J27_screen.pdf
[4] In Chapter 14: Exposing UAS Vulnerabilities via Electronic Warfare (EW) and Countering with Low Probability Intercept Signals (LPI), EW, CYBER and LPI in modern communications systems is covered in detail. (Nichols, et al., Unmanned Aircraft Systems in the Cyber Domain, 2019)
[5] MC 64/11, 4 Jul. 2018
[6] Student assignment end of Chapter 9.
[7] SCADA systems, functions, configurations, and their vulnerabilities are covered in detail in (Nichols, et al., Unmanned Aircraft Systems in the Cyber Domain, 2019) Chapter 3: Understanding Hostile Use and Cyber-Vulnerabilities of UAS: Components, Autonomy v Automation, Sensors, SAA, SCADA and Cyber Attack Taxonomy. The purpose of this textbook is to move forward not rehash materials previously presented. Some Tables in Chapter 3 have been republished here for convenience. The reader is reminded that UNMANNED AIRCRAFT SYSTEMS IN THE CYBER DOMAIN: PROTECTING USA’S ADVANCED AIR ASSETS, 2nd Edition by Nichols, R. K., Ryan, J., J.C.H., Mumm, H.C., Lonstein, W.D., Carter, C., Hood, J.P. is available for FREE at www.newprairiepress.org/ebooks/27
[8] In the authors’ ancient textbook (Nichols R. K., The ICSA Guide to Cryptography, 1999) Cryptology is the study of creating codes and ciphers (cryptography) and decoding or deciphering codes and ciphers (cryptanalysis) when the system is not known. There are far better books available. Consider the classic by guru and one-time competitor, Bruce Schneier, simply entitled Cryptography. (Schneiner, 1996)
[9] The general term for the art and science of concealment ciphers is steganography. This includes null, ciphers and image / pixel deceptions (hiding in plain sight or in a massive amount of storage) (Randall K. Nichols D. J., 2000).
[10] If the reader is really interested in pain and all things Maxwell (James Clerk), consider the textbook Electromagnetic Waves by Staelin, et.al. (David H. Staelin, 1998). Prepare for hours of math and difficult reading.
[11]Fluence – particle density or energy density, used to describe the output of a radiation field or of a laser beam (Collins-Dictionary, 2019)
[12] Think skeet shooting.
[13] Laser stands for Light amplification through simulated emission of radiation.
[14] A collimated beam of light or other electromagnetic radiation has parallel rays, and therefore will spread minimally as it propagates. A perfectly collimated light beam, with no divergence, would not disperse with distance. … Perfectly collimated light is sometimes said to be focused at infinity. (Wikipedia, Collimated Definition, 2019)
[15] This effect is referred to as aerosols.
[16] Plasma weapons are very cool and are more sci-fi than reality, certainly against UAS systems. A plasma weapon is a type of” ray gun” that fires a stream, bolt(s), pulse or toroid of plasma (i.e. very hot, very energetic excited matter). The primary damage mechanism of these fictional weapons is usually thermal transfer; it typically causes serious burns, and often immediate death of living creatures, and melts or evaporates other materials. Fictional plasma weapons are often visually analogous to real-life plasma torches that cut into materials for industrial use purposes; however, said torches currently only produce a plasma jet of several inches at most. (Wikipedia, Plasma Weapons, 2019) Amazon sells a Star Wars Nerf Captain Plasma Blaster for a mere $34.57 +tax and shipping. Six-year old’s can now melt down a droid.
[17] Aside from author’s comments in note 19, the ignition of plasmas at a target surface, and their subsequent propagation as detonation or combustion waves, can greatly enhance the thermal and mechanical coupling of a laser to a target, either in a vacuum or air.
[18] Laser material processing is now a major component of the manufacturing process. Lasers accomplish tasks ranging from heating for hardening, melting for welding and cladding, and the removal of material for drilling and cutting. Typical intensities required for such tasks include heat treating at 103 – 104 W/cm2, welding and cladding at 105 – 106 W/cm2, and material removal 107 – 109 W/cm2 for drilling, cutting, and milling. (National Academies of Sciences, 2018)
[19] These conclusions may be big jump from real earth to atmosphere. A better picture of the thermal, mechanical damage, stimulated Rama scattering (SRS), vaporization, melting as a function of intensity and pulse width is provided by (Nielsen, 2012) in Chapter 3, p 191, Figure 3-76. No matter how we dissect the laser weapon use concepts, UASs are not cost-effective targets for this cool technology.
[20] Relativistic velocities – Velocities approaching speed of light.
[21] Bremsstrahlung -radiation loss of energy induced by the acceleration of particles they suffer in collisions in the PB. (Nielsen, 2012)
[22] Another related chapter was Chapter 8: Designing UAS Systems for Stealth. (Nichols, et al., Unmanned Aircraft Systems in the Cyber Domain, 2nd Edition, 2019)
[23] Refer to Appendix 10-1 for standard acoustical properties and units.
[25] Use the bottom of the page converter. Basis: Speed of sound c = λ × f = 343 m/s at 20°C} for 16 m L = 21.4375Hz. This compares to the Austin value of 20 Hz. For the 2 cm = 0.02 m, the resulting valued for f = 17650 Hz. This is above the 16,000 Hz limit from Austin. This might be due to the 20-degree Celsius basis difference. This tells the UAS designer that the upper end of noise – Stealth acceptability 17,150 Hz.
[26] “An equal-loudness contour is a measure of sound pressure (Db SPL) over the EMS spectrum, for which a listener perceives a constant loudness when presented with pure steady tones. The unit of measurement for loudness levels is the phon and is arrived at by reference to equal-loudness contours. Two sine waves of differing frequencies are said to have equal-loudness level measured in phons if they are perceived as equally loud by the average young person without significant hearing impairment.” (Staff, Equal Loudness Contours, 2016)
[27] “Four important relationships to note are that power is equal to pressure squared, P = p2, pressure is equal to the square root of power, p = √ P, intensity is proportional to pressured squared,
I ≈ p2 and pressure is proportional to intensity, p ≈ √I. This makes it easy to convert between sound intensity and sound pressure.” (Entokey, 2019) These relations yield a few more to relate sound pressure, sound intensity and distance r. Given to pressures p1 and p2 at distance r1 and r2, they are proportional: p2 / p1 = r1 / r2; and factoring in intensities at I1 and I2, gives I2 / I1 = (r1 /r2)2. Finally, r2 / r1 = p2 / p1 = √I1 / I2. (TRS S. , 2018)
[28] Decibels (Adamy D. , 2001) (Gelfand S. A., 2009) Sound magnitudes, intensities, and pressures vary over an enormous range. We use decibels (dB) to express sound values. Decibels takes advantages of ratios and logarithms. Ratios are used so that physical magnitudes can be stated in relation to a reference value that has meaning to us. The reference point chosen is the softest sound that can be heard by normal people. The reference value has an intensity of 10-12 w/m2 (10-16 w/cm2). In terms of sound pressure, the reference value is: 2 x 10-5 N/m2 or 20 µPa (2 x 10-4 dynes/cm2). An interesting Geek bar bet is what is the logarithm of all 2:1 ratios, 8:4, 20, 20:10, 100:50, etc.? Even though the distance between absolute numbers gets wider, 1,4,10, 50…, the logarithms of the 2:1 ratios are the same at 0.3. Another interesting factoid about ratios is the units generally cancel out.
The general decibel formula in terms of power level (PL) is as follows (Gelfand, 2004):
PL = 10 log P / Po Equation 10-4
Where P = power of the sound measured, and Po is the reference power to be compared.
The general decibel formula in terms of power level (IL) is as follows (Gelfand, 2004):
IL = 10 log I / Io Equation 10-5
Where I = intensity of the sound measured, and Io is the reference intensity to be compared. Io is given as 10-12 w/m2 .
The general decibel formula for sound pressure level (SPL) is obtained by replacing all of the intensity values with the corresponding values of pressure squared because (I ≈ p2).
SPL = 10 log p2 / po2 Equation 10-6
Where p is the measured sound pressure (in N/m2) and po is the reference sound pressure of
2 x 10-5 N/m2 . A more convenient form of this equation recognizes that log x2 = 2 log x. (Gelfand, 2004)
SPL = 20 log p / po. Equation 10-7
Equation 10-7 is the common formula for SPL. A couple of observations a positive decibel value means that the sound pressure level is greater than the reference. The decibel value of the reference is 0 because reference value / reference value = 1 and 10 log 1 = 0. This does not mean no sound; it just means the sound measured is equal to the reference point. A negative value of decibels means that the sound magnitude is lower than the reference. (Gelfand S. A., 2009)
[29] It is left to the reader to obtain any standard trigonometry text to see all the parameters of the well-known sine wave.
[30] The formula for the string’s resonant frequency Fo is:
Fo = 1 / 2L x √T /M Equation 10-8
Where Fo is resonance frequency in Hz, T is Tension, M is Mass, L = λ /2 and f = c / λ and c = speed of sound. L = length of the string. (Gelfand, 2004) The strings lowest resonant frequency is f = c / 2 L but Eq 10-8 considers that the speed of sound is different for a vibrating string than it is for air.
[31] Author’s note although not specified in (Yunmonk Son, 2015), according to chapter author research and experimentation, the frequencies turn out to be the resonance frequencies. So agrees Dr. Kim at KAIST. “You would think that the gyroscopes used in unmanned aircraft systems (UAS) would have been designed to have resonant frequencies above the audible spectrum – i.e., above 20 kHz – but Kim and his team found that some have not.” (Yunmonk Son, 2015) In the case of a gyroscope, “you can get it to spit out very strange outputs, as researcher Yongdae Kim, a professor in the electrical engineering department of the Korea Advanced Institute of Science and Technology (KAIST), told ComputerWorld” (Kirk, 2015) An example of resonance frequency and breaking glass can be found on youtu.be at https://youtu.be/BE827gwnnk4

