Chapter 6: C-UAS Evolving Methods of Interdiction
C. Carter
Student Learning Objectives
There are several goals for student learning in this chapter:
- To understand the need for Interdiction in C-UAS,
- To see the need to increase security UAS Supply chain management potentially using Blockchain,
- To dig into the Blockchain process and understand its strengths and vulnerabilities and its relationship to aircraft communications,
- To recognize the hurdles that Blockchain may face like 5G and public acceptance.
Why is Interdiction Needed?[1]
Unmanned aircraft receives external communication through radar. There are four different types of radar: active (using the drone’s transmitter or illuminator), passive (using another drone’s transmitter), basic (from one location) and multistatic (when the radar transmitter and receiver are at different locations) (Chantz, 2016). In addition, radar is used with a measure of signals and patterns to direct the drone out of harm’s way. This communication process is based on a network of trust. GNSS/GPS jamming, and spoofing are methods that compromise the blind aviation trust of the external communications the unmanned aircraft receives. Other methods of electronic compromise have created a challenge when addressing C-UAS.
Methods of interdiction should be one step ahead of the unmanned aircraft industry to become an effective offensive security measure.
What is a Blockchain?
Most people associate blockchain with cryptocurrency, not all blockchains are created with the same product in mind. At the most basic level, every blockchain is a digital ledger of transactions that take place on a peer-to-peer network with the ability to control visibility — who has permission to see which data (Marx, Sealy, & Thompson, 2019). Each step the transaction makes through the supply chain it is assigned an encrypted block. Each block contains information about a certain number of transactions, a reference to the preceding block in the blockchain, and an answer to a complex mathematical challenge known as the “proof of work”. The concept of proof of work is used to validate the data associated with that particular block as well as to make the creation of blocks computationally “hard”, thereby preventing attackers from altering the blockchain in their favor (Ferrer, 2017)
The blockchain network has four main components viz, asymmetric cryptography and node applications, transactions and blocks, the distributed ledger, and the consensus mechanism
Blockchain is can be considered trustless, since the transaction participates do not require trust. Inversely to digital certificates, which a client trusts the certificate presented by a certificate authority on behalf of a website, to conduct secure transactions.
Figure 6-1: Blockchain in Supply Chain Management
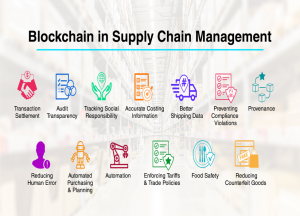
Source: (3i Infotech, 2019)
The Process of Blockchain Synchronization
The advantage of decentralization and the distribution of information in the blockchain is also a vulnerability. Depending on the implemented framework of blockchain, the scalability and consensus becomes more challenging to guarantee performance of the blockchain process. Below is a list of parameters that determine synchronization mechanism between nodes in a distributed system (consensus mechanism) (Bogdanov, et al., 2018):
- Decentralized governance: a single central authority cannot ensure the completion of a transaction.
- Quorum structure: Nodes exchange messages in predestination (paths that may include steps or levels).
- Authentication: this process provides the means to verify the identity of participants.
- Integrity: it provides verification of the integrity of a transaction (for example, mathematically by means of cryptography).
- Non-repudiation: provides a means to verify that the intended sender actually sent the message.
- Privacy: this helps ensure that only the intended recipient can read the message.
- Fault tolerance: The network works efficiently and quickly, even if some nodes or servers do not work or are slow.
- Performance: considers bandwidth, survivability, scalability and latency.
The blockchain is not full proof from attacks. Established chains of reliable users can be used to carry out a third-party attack (Bogdanov, et al., 2018). Also, there is the possibility of including third parties as an additional node of the Blockchain system with the participation of an unscrupulous partner of a streamlined chain (Bogdanov, et al., 2018).
Blockchain Aircraft Communication
Announced in 2018, as of January 1, 2020, the FAA will now enforce the mandatory installation of Version 2 ADS-B Out system to fly in most controlled U.S. airspace. The ADS-B system uses GPS satellites verses the traditional ground-based radar. The advantage of GPS based system, FAA will be able to see information such as registration number, precise location, aircraft dimensions, etc. However, the rules were published May 27, 2010 and the DOD submitted comments to the FAA of ADS-B compromising the safety of special flights and missions. This lag in time is significant in understanding the threat that emerged over the past ten years, before implementation the ADS-B out system can be considered already out of date.
On January 12, 2020, Ronald J. Reisman (NASA Ames Research Center) published research entitled,” Air Traffic Management Blockchain Infrastructure for Security, Authentication, and Privacy “. Mr. Reisman outlines the vulnerabilities of ADS-B for civil and military aviation and provides the solution of blockchain. “The design innovation is the use of an open source permissioned blockchain framework to enable aircraft privacy and anonymity while providing a secure and efficient method for communication with air traffic services, operations support, or other authorized entities,” Notes Mr. Reisman (Global Business Outlook, 2020). Mr. Reisman’s scalable framework will include certificate authority, smart contract support, and higher-bandwidth communication channels for private information that may be used for secure communication between any specific aircraft and any particular authorized member (Global Business Outlook, 2020) The blockchain would essential provide a method to encrypting the ADS-B transmissions. Aviation Blockchain Infrastructure (ABI) design that enables aircraft to communicate effectively, securely, and privately with air traffic management and other properly authorized entities (Reisman, 2019). In the case of unmanned aircrafts, blockchain brings security to Radio Frequency by keeping a high-speed, assured ledger of airspace activity and information regarding the drone and its operator, and distributing it to all appropriate parties (Chantz, 2016).
Figure 6-2: Notional Design of Blockchain-Mitigated Channels of Communication
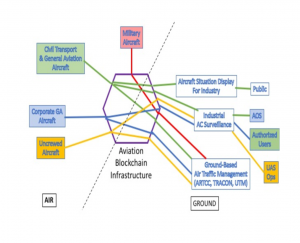
Source: (Reisman, 2019)
Figure 6-2 shows the Notional design of blockchain-mitigated channels of communication. Chain code (aka ‘Smart Contracts’) routes the information appropriately between aircraft and the ground-based ATM and other support services (Reisman, 2019).
ABI proposed by Mr. Reisman is based on Hyperledger Fabric, a Linux based opensource tools and blockchains with contributions from Intel, IBM, and SAP. Hyperledger Fabric allows for the creation of a private and permissioned blockchain. Through services called “private channels” as a means to communicate private information at a comparatively high bandwidth. These private channels may be used to pass a private key (or time-key data structure) suitable for encrypting ADS-B Out transmissions between any specific aircraft and any particular authorized member in accordance with the terms of the smart contracts associated with the particular private channel (and subnet). The use of ciphertext enables ADS-B users to maintain privacy and anonymity from general public while also providing a secure and efficient method for communication with authorized entities, such as Air Traffic Services or Airline Operations Services (Reisman, 2019).
Blockchain to encrypt ADS-B transmissions is in the testing phases. While this is a solution for right now, we need to look ahead to understand how blockchain, as ADS-B could become present new risks verses a solution in particular verticals of aviation.
Blockchain Vulnerabilities
First document blockchain successful hack occurred in 2011. A simple case of compromised credentials. Victorious hacks of blockchains have continued along with the sophistication of attacks. Manipulation of signatures, overwriting transactions, etc. Prominently the attacks on blockchains come back to one of the basic security issues that no vertical has solved, compromise of the company employees and systems. It is amazing to see social engineering techniques that can date back to the days of Frank Abagnale Jr. are still just as effective as they were in 1960’s. A simple act of piggybacking through a secure door, picking up items that were left on the printer, and photographic diagrams with IP addresses can lead to a system’s compromise. Below are additional blockchain attacks that could lead to breaking the blockchain:
Blockchain Attack Scenarios (Anwar, 2019)
- A 51% Attack
The majority of Blockchains use the prove of work to communicate the verified transactions in the block. The mining for the prove of work entails the nodes spend large amounts of computing power to prove themselves trustworthy enough to add information about new transactions to the database (Orcutt, February)
- Blockchain Protocol Code Bugs
Bad actors exploit those loopholes
- Routing Attacks
Bad Actors can intercept communication channels with a compromise of ISP
- Smart Contract Bugs/Compromise
If a smart contract is changed it the blockchain is gravely impacted. Since transactions cannot be undone, a “fork” in the blockchain (a new branch of the blockchain) will need to occur to bring the process back up.
- Sybil Attack
The attacker is running multiple fake nodes on a blockchain network that can block receiving and transmission of blocks.
- Direct Denial of Service (DDoS)
Flooding the network with requests to stop all functions. There are critics that claim the decentralization of the blockchain reduces the risk of DDoS. However, several successful attacks DD0S on blockchains have taken place.
Blockchain Unmanned Aircrafts
Blockchain brings new functionality to the unmanned aircraft industry. The UAS vertical has struggled with air traffic control, identity management, insurance, and security. In march 2017, IBM patent filing outlines using distributed ledger technology (blockchain) can provide effective techniques for managing data related to commercial and recreational drones, particularly when a security risk level is considered to be relatively high (Cant, 2019). IBM was not alone, Intel, Accenture, and numerous individuals applied for unmanned aircraft technology patents. Walmart out applied all organizations with their unmanned aircraft technology patents. From pizza cooking delivery to compromise of communication while delivery is in progress.
U.S. Unmanned Aircraft Patents
The patents filed over the past seven years referencing unmanned aircrafts and blockchain give an indication of the direction of the technology. China globally leads the way with 62% of the blockchain patents applications (IAM, 2019). The United States is at a mere 22% globally with blockchain patents applications (IAM, 2019). However, Korea grants 54 % of the blockchain patents filed (IAM, 2019). These numbers are concerning for the United States, blockchain security and process will be the future of all verticals not just in the drone industry. Highlighted below are a few of the newsworthy United States patents.
IBM patent application for Unmanned Aerial Vehicle Date Management highlights the use of blockchain securing the unmanned aerial data. “The chain can be considered a chronicle of a UAV’s path through time. When a transaction is conducted, the corresponding UAV parameters are sent to one or more of the computing nodes in the system for validation. The one or more computing nodes establish a validity of the transaction and generate a new block. Once the new block has been calculated, it can be appended to the stakeholder’s UAV blockchain. Among many other advantages, the use of a blockchain infrastructure helps in identifying misbehaving UAVs by multiple parties and such activities are recorded in an immutable ledger.” (United States of America Patent No. US2018/027024A, 2019)
One of Walmart’s patents outlines security for electronic communications in connection with a package delivery. “Authentication can be performed at the delivery communication and control system and/or other security systems by visual recognition such as facial recognition, biometric fingerprint analysis, and so on, audio recognition such as voice signatures, biometric recognition via a fingerprint or retinal scanning device (not shown) at the unmanned vehicle, blockchain recognition for scanning a blockchain signature or key for authentication, and so on.” (United States of America Patent No. US2018/0205682A, 2018). In 2019, Walmart filed a patent application for Cloning Drones Using Blockchain. This Walmart patent application focuses on data integrity, “A blockchain ledger may store any kind of information that may be stored in any other format or medium, for example, a large list of instructions of different types, navigational information, and maps. In such a way, a same software profile may be deployed across the cloned drone” (Foxley, 2019)
Countering a Blockchain Unmanned Aircraft Attack
Published research of countering a blockchain unmanned aircraft attack is a sparse. However, a counter technique can be developed by applying known flaws of blockchain technology. A successful attack involves multiply vectors. Using the following vectors an affective counterattack can be formulated:
- If blockchain is used for synchronized unmanned aircraft attack by a bad actor, it can be determined the decentralized algorithm requires will require significantly lower communications bandwidth. Therefore, sharing intel on obstacle-free regions in their immediate vicinity (Ferrer, 2017).
- As referenced in the beginning of the chapter, SSL certificates are used encrypt the blockchain. When a flaw in the encryption algorithm arises, or as computing power continues to become stronger, the encrypted data may then be decrypted to reveal private details (Fitzpatrick, 2019). In 2017, industry drone manufacture DJI had an incident of SSL certificate leak. Leading cloud security systems, for example Imperva’s Incapsula, compromised undisclosed amount of customer SSL certificates. Imperva has seven out of 10 global telecom providers, half of the top ten United States commercial banks, along with other prominent industries (Imperva, 2018).
- The UAV sensor system consists of the sensory equipment of the UAV together with integrated pre-processing functionalities. For common military UAVs these sensors are often cameras with different capabilities. UAVs may be equipped with further sensors, such as INS, GPS and radar (Hartmann & Steup, 2018). Sensors with external references are more susceptible to jamming and spoofing than sensors with internal references. External references generally impose a risk to the integrity of the system (Hartmann & Steup, 2018).
Taking these vulnerabilities into consideration the following steps can be used to counter a blockchain unmanned aircraft attack. The methods below are homegrown hacking methods and purchased commercial solutions.
- Skyjack Drone Hack, developed by hacker and researcher Samy Kamkar. Drone that flies around seeking Seeks wireless signal of any other drone in area. Forcefully disconnects wireless connection of true owner of target drone. Authenticates with target drone pretending to be its owner (O’Malley, 2019)
- SSL interception proxy using Burp Suite, using the steps below (Vanunu, Barda, & Zaikin, 2018):
- Open our Burp Suit Certificate and cast it to X509Certificate.
- Load a KeyStore and put the certificate inside.
- Create TrustManagerFactory and initialize it with the KeyStore we just created that contains our Burp Suit certificate.
- Overload the SSLContext and hook the TrustManager with our TrustManager.
- Sensor Jamming: disruption to inter–drone communications by manipulating UAS onboard sensors can be archived by Sensor Jamming. Jamming sensors can impact GPS signals by giving false GPS information (camera/gimbal dislocation, heading sensor demagnetization, etc.). “High intensity light directed at an optical sensor can blind it. GPS receivers can be cyber-spoofed, which consists of transmitting a stronger, but false, GPS signal to a receiver, resulting in inaccurate navigation. Influencing the local magnetic field can have adverse effects on both onboard hard drives and sensors that require magnetic orientation to operate correctly.” (Boutros, 2015)(Humphreys, 2012)
Using proven techniques of signal jamming, SSL interception proxy, and sensor jamming potentially counter a blockchain unmanned aircraft attack. Evolving technology will continue to change the characteristics of blockchain but the basic concept gives the layout of the process.
Next Counter-UAS Hurdle – 5G Communication, Blockchain, Unmanned Aircrafts
What will the combination of 5G Communication and Blockchain bring to UAS? Counter-UAS? 5G is the fifth-generation mobile network (Qualcomm, 2020). 5G is a unified platform that will support a larger range of bands (1GHz to millimeter-wave) and 100% more traffic with latency of 1ms, along with other improvements.
The combination of 5G and blockchain will enable traffic management to geofence unmanned aircrafts. “…envision the use of the emerging 5G networking technology for that. 5G networking technology is the next generation of cellular networks. It is designed to provide much higher speed—larger bandwidth and smaller latency—higher reliability and the ability to serve a larger number of users, in comparison to 4G. To do that, the radio spectrum is partitioned into bands, with different frequencies—from low to extremely high.” (Tasevski, 2018). Blockchain will be used to reach the consensus in the environment. 5G integrated at all levels of UAS (physical, network, and joint communication) and blockchain will bring greater control to air traffic management. China based studies have researched the creation of UAS-based antenna array system with high data rate and low service time can be created using 5G. The UAS-based antenna data will be protected by blockchain (Bin Li & Zhang, 2019). In the publication of Unmanned Aircrafts in the Cyber Domain, (by the authors of this publication) gives the use case of a cyber weapon deployed from a small UAS. The research points to the use of this UAS cyber weapon to cause the 2017 collusions of U.S. Navy Warships with commercial vessels. When reviewing the research of that incident combined with the creation of UAS-based antenna with 5G and blockchain, the threat level of advanced attack of vessels increases. Just this incident alone justifies the need for offensive security to be a priority for UAS commercial, military, and hobbyist.
Figure 6-3: 5g Communications/ Blockchain Geofence for the Financial District of Manhattan NYC
Source: (Tasevski, 2018)
Challenges Facing Interdiction Methods for C-UAS
Unmanned aircrafts hobby, military and commercial have their own unique attack methods, impacts, and risks. Geographic location, event, and intention can determine the method of prohibiting a drone attack. From a nation-state conflict to an outdoor concert, reviewing the scenarios and using a risk model can highlight the efficacy between C-UAS methods. With the addition of blockchain, 5G communication, and the evolution of UAS technology the risks/threats increase. Per contra, blockchain and 5G communication presents a substantial threat for the creation of an effective C-UAS.
Conclusions
Blockchain represents a disruptive security technology that may significantly improve the C-UAS supply chain management. It also faces some stiff challenges because of inherent vulnerabilities. Blockchain and 5 G communications are a mixed blessing and with increased UAS technology, comes increased threats.
References
3i Infotech. (2019, March 26). Why you must Modernize your Supply Chain Management with Blockchain. Retrieved from 3i Infotech Limitless Excellence: https://www.3i-infotech.com/must-modernize-supply-chain-management-blockchain/
Anwar, H. (2019, November 17). 101 Blockchains Reviews. Retrieved from 101 Blockchains: https://101blockchains.com/blockchain-hacked/
Bin Li, Z. F., & Zhang, Y. (2019, January 20). UAV Communications for 5G and Beyond: Recent Advances and Future Trends. Retrieved from ARXIV: https://arxiv.org/pdf/1901.06637.pdf
Bogdanov, A., Degtyarev, A., Korkhov, V., Kamande, M., Iakushkin, O., & Khvatov, V. (2018). ABOUT SOME OF THE BLOCKCHAIN PROBLEMS. Saint Petersburg: Saint Petersburg State University.
Boutros, D. (2015, May 15). Operational Protection from Unmanned Aerial Systems. Retrieved from http://www.dtic.mil/dtic/tr/fulltext/u2/a621067.pdf
Cant, J. (2019, November 29). Cointelegraph News. Retrieved from Cointelegraph: https://cointelegraph.com/news/ibm-files-a-blockchain-patent-for-fighting-package-theft-by-drone
Chantz, H. (2016, August 25). Security Inteligence Manframe. Retrieved from Security Inteligence : https://securityintelligence.com/using-blockchain-to-address-drone-cybersecurity/
De Wilde, W., Cuypers, G., Sleewaegen, J.-M., Deurloo, R., & Bougard, B. (2016). GNSS Interference in Unmanned Aerial Systems. Belgium: Septentrio Satellite Navigation.
Ferrer, E. C. (2017). The blockchain: a new framework for robotic swarm systems. Cambridge: MIT Media Lab.
Fitzpatrick, L. (2019, February 4). Forbes A Haackers Take on Blockchain Security. Retrieved from Forbes: https://www.forbes.com/sites/lukefitzpatrick/2019/02/04/a-hackers-take-on-blockchain-security/#2c788dbd4334
Foxley, W. (2019, August 14). Coindesk Markets. Retrieved from Coindesk: https://www.coindesk.com/walmart-files-patent-application-for-blockchain-backed-drone-communication
Global Business Outlook. (2020, January 20). Global Business Outlook Technology Top Stories. Retrieved from Global Business Outlook: https://www.globalbusinessoutlook.com/nasa-to-use-blockchain-technology-for-air-traffic-management/
Hartmann, K., & Steup, C. (2018, October 26). NATO CCD COE. Retrieved from The Vulnerability of UAVs to Cyber Attacks – An Approach to the Risk Assessment: https://ccdcoe.org/uploads/2018/10/26_d3r2s2_hartmann.pdf
Heue, R. (2018, June 2). GNSS Jamming and Spoofing: Hazard or Hype? Retrieved from Space of Innovation: https://www.space-of-innovation.com/gnss-jamming-and-spoofing-hazard-or-hype/
Humphreys, T. (2012). STATEMENT ON THE VULNERABILITY OF CIVIL UNMANNED AERIAL VEHICLES AND OTHER SYSTEMS TO CIVIL GPS SPOOFING. Austin: The University of Texas .
IAM. (2019, July 23). IAM Patents. Retrieved from IAM: https://www.iam-media.com/patents/revealed-countries-leading-race-blockchain-patents
Imperva. (2018, July 9). Imperva Company Overview. Retrieved from Imperva: https://www.imperva.com/resources/datasheets/Imperva_Company_Overview.pdf.pdf
Kumar, A., Kundu, A., Pickover, C., & Weldemariam, K. (2019). United States of America Patent No. US2018/027024A.
Ledger Insights. (2019, December 20). Retrieved from Ledger Insights Enterprise Blockchain News: https://www.ledgerinsights.com/us-air-force-blockchain-cybersecurity-xage/
Lufthansa Group. (2018, September 25). Newsroom Lufthansa Group. Retrieved from Lufthansa Group: https://newsroom.lufthansagroup.com/english/newsroom/news-releases/all/lufthansa-and-sap-select-the-nine-finalists-for-the-world-s-first-aviation-blockchain-challenge/s/b2a97099-b65b-46f6-94a3-1e6bacf5e62f
Marx, C., Sealy, R. P., & Thompson, S. (2019, July 7). How blockchain can improve the aviation industry. Retrieved from Strategy-Business: https://www.strategy-business.com/article/How-blockchain-can-improve-the-aviation-industry?gko=9e976
McCarthy, S., Zheng, W., & Tsang, D. (2018, October 29). Hong Kong Society. Retrieved from South China Morning Post: https://www.scmp.com/news/hong-kong/law-and-crime/article/2170669/hk13-million-damage-caused-gps-jamming-caused-46-drones
O’Brien, J., & High, D. (2018). United States of America Patent No. US2018/0205682A.
O’Malley, J. (2019, February 18). E&T Engineering and Technology. Retrieved from Take me out: creating ‘No-Drone Zones’ around airports: https://eandt.theiet.org/content/articles/2019/02/take-me-out-creating-no-drone-zones-around-airports/
Orcutt, M. (Feburary, 19 2019). MIT Technology Review. Retrieved from MS. Tech MIT Technology Review: https://www.technologyreview.com/s/612974/once-hailed-as-unhackable-blockchains-are-now-getting-hacked/
Qualcomm. (2020). Everything You Need to Know About 5G. Retrieved from Qualcomm: https://www.qualcomm.com/invention/5g/what-is-5g
Reisman, R. J. (2019). Page 1 1Air Traffic Management Blockchain Infrastructure forSecurity, Authentication, and Privacy. Mountian View: NASA Ames Research Center.
Tasevski, S. (2018, December 3). Herding Drones with Blockchains and 5G. Retrieved from Drone Below: https://dronebelow.com/2018/12/03/herding-drones-with-blockchains-and-5g/
Vanunu, O., Barda, D., & Zaikin, R. (2018, November 8). Check Point Research. Retrieved from Check Point: https://research.checkpoint.com/2018/dji-drone-vulnerability/
Endnotes

