Chapter 5: Surveillance and Reconnaissance
H.C. Mumm
Student Learning Objectives – The student will gain knowledge of the concepts and framework as it relates to the surveillance and reconnaissance aspects of C-UAS (Counter-unmanned aerial systems). The student will be able to:
- Describe the importance of surveillance to C-UAS activities, differentiating it from reconnaissance
- Describe the importance of reconnaissance to C-UAS activities, differentiating it from surveillance
- Develop a surveillance plan for a notional C-UAS scenario, identifying processes, systems, and technologies needed, as well as mission goals and metrics
- Explain how detection of UAS is different from detection and interpretation of adversarial intent
- Explain the need for operational secrecy for C-UAS surveillance and reconnaissance activities
History-What is it, and Why Does it Matter?
This chapter explores the differences and similarities of how technology is used to find manned and unmanned aircraft in the sky. The history of surveillance and reconnaissance has its roots in military uses with only a small operation with its civilian counterparts. “The tactics and techniques that are applied to today’s technology stem from the field of remote sensing. Remote sensing has a long history as it began with humans attempting to see and sense phenomena from a distance and (we have now) taken a long journey from using pigeons to balloons to aircraft, then to satellites, to UAS [unmanned aerial systems]” (Nichols & Mumm, 2018)
The use of UAS or unmanned aerial vehicles (UAVs) for intelligence, surveillance, and reconnaissance is one of the most well-known applications of the technology. “The vast majority of UAVs are used purely for intelligence, surveillance, and reconnaissance (ISR) missions. In current military usage, they range from the Global Hawk, with a wingspan greater than a Boeing 737 airliner, to nano-helicopters that weigh a few grams, and all points in between” (Lambeth, 2006). This field of study has allowed advances in military movement, attack, and defend, as well as civilian surveying and developing, freedom of movement throughout our world. (Nichols & Mumm, 2018)
However, the tactics this chapter will discuss are almost 180 degrees from the normal thought process in surveillance and reconnaissance, as the “target” is up in the expansive sky and is not always bound by the rules of conventional manned aircraft, and sometimes UAS technologies evolve so quickly that counter-UAS (C-UAS) systems just cannot adapt quickly enough. “The proliferation of C-UAS technology might even accelerate the development of technologies that will render C-UAS systems ineffective, particularly in military environments” (“The new world of counter-drone technology,” 2018). C-UAS technology has two primary functions “the first is to identify or detect drone activity. The second function is to intercept the airspace threat or defeat the drone” (Friedberg, 2019)
Figure 5-1: Drone Capability Diversity
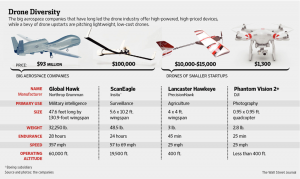
Source: (Snow, 2014)
According to Merriam-Webster, the definition of reconnaissance is “a preliminary survey to gain information; especially an exploratory military survey of enemy territory. (Dictionary, 2019) In historical terms, it is French and means “recognition” or from Old French reconoistre or to “recognize” (Surveillance, 2019). This idea of a quick look or survey is in contrast with the meaning of surveillance which is “continuous observation of a place, person, group, or ongoing activity in order to gather information: attentive observation, as to oversee and direct someone or something” (Surveillance, 2019). This continuous observation does not always need to be carried out with the knowledge or consent of the surveilled as we can use electronic surveillance methods which allow for “surveillance or the gathering of information by surreptitious use of electronic devices, as in crime detection or espionage” (Surveillance, 2019)
.Furthering this idea in the C-UAS arena, one must look at not only finding an object in the vastness of the open sky but the ability to detect, classify, identify and dispatch countermeasures for not only the flying vehicle but also for the operator or base station on the ground. Detection means the technology can discover UAS in a given area. Classification of UAS will usually be able to separate UAS (drones) from other types of objects – such as manned aircraft.
“One step further is identification. Some equipment can identify a particular model of drone or even identify the drone’s or controller’s digital fingerprint, like a MAC address for example. This level of identification can be handy for (tracking and) prosecution purposes. Being alerted that a drone is present…is already useful. But your situational awareness, and ability to deploy countermeasures is greatly enhanced if you know the drone’s (and/or the controller’s) exact location. Some equipment will even allow you to track the drone location in real-time” (9 Counter-Drone Technologies To Detect And Stop Drones Today, 2019).
Table 5‑2: Threat Detection Tools
| Technology | Method |
| Radar | Detects the presence of small unmanned aircraft by their radar signature, which is generated when the aircraft encounters RF pulses emitted by the detection element. These systems often employ algorithms to distinguish between drones and other small, low-flying objects, such as birds. |
| Radio Frequency (RF) | Identifies the presence of drones by scanning for the frequencies on which most drones are known to operate. Algorithms pick out and geo-locate RF-emitting devices in the area that are likely to be drones. |
| Electro-Optical (EO) | Detects drones based on their visual signature. |
| Infrared (IR) | Detects drones based on their heat signature. |
| Acoustic | Detects drones by recognizing the unique sounds produced by their motors. Acoustic systems rely on a library of sounds produced by known drones, which are then matched to sounds detected in the operating environment. |
| Combined Sensors | Many systems integrate a variety of different sensor types in order to provide a more robust detection capability. For example, a system might include an acoustic sensor that cues an optical camera when it detects a potential drone in the vicinity. The use of multiple detection elements may also be intended to increase the probability of successful detection, given that no individual detection method is entirely failproof. |
Source: (Michel, 2018)
Threat Identification-How and Why
The traditional ways of looking for human-made objects in the sky are radar signatures, heat signatures, visually seeing the object with the human eye, or through an optical assist mechanism. There are also acoustic signatures as well as an array of electronic signals sweeping technologies used for detection as “C-UAS systems can be ground- or air-based or even handheld. Most systems on the market today are designed only for detection or for interdiction, and the clear majority are ground-based, although a few comprise air and ground components” (Wilson, 2018). Table 5 -1 lists the main techniques for the detection and tracking of UAS.
The ability to find an object in the sky is a combination of the mechanism chosen as well as the size, speed, trajectory, weather conditions and possible stealth capabilities the object may employ to avoid detection. Surveillance and reconnaissance in the C-UAS arena
includes radar, radio frequency (RF), electro-optical (EO), infrared (IR), acoustic, and combined sensors. There are no perfect detection methods. Many affordable electro-optical sensors are limited to daylight operations and a direct line-of-sight to the target (also true for IR and many RF systems). RF and acoustic sensors use a library of known sounds and frequencies to detect UAVs, but the rapid development of new platforms makes it impossible for those to be fully up to date. Sensor sensitivity also is an issue; too sensitive generates many false positives, while reduced sensitivity leads to false negatives (Wilson, 2018).
Adding to this equation is the atmospheric effects of temperature, weather conditions, and location of the object be it over an open desert, the vastness of the ocean, or mixed within the many buildings and signals within a city or urban terrain. Tracking an object in the sky is more difficult than tracking an object on land as the vastness of the sky creates the difficulty of a three dimensional environment where the object could move up, down, laterally side to side or a combination of all three dimensions as individuals and sensors attempt to find and track the object. The most common way to find and track an aircraft is through the use of radar. RADAR is an acronym for Radio Detection and Ranging. A simple explanation how radar works is:
A beam of energy, called radio waves, is emitted from an antenna. As they strike objects in the atmosphere, the energy is scattered in all directions, with some of the energy reflected directly back to the radar. The larger the object, the greater the amount of energy that is returned to the radar. In addition, the time it takes for the beam of energy to be transmitted and returned to the radar also provides is with the distance to that object. (How Radar Works., 2019)
Figure 5-2: Example of RADAR Signal
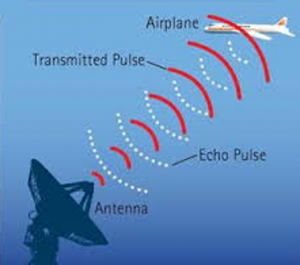
Source: (Goyal, 2019)
A radar signal has a pulse width (pulse duration), which can be increased or decreased to “see” further out or to get a better image of the object in question. The “Pulse width determines the spatial resolution of the radar… decreasing the pulse width increases signal bandwidth. A wider system bandwidth results in higher receiver noise for a given amount of power, which reduces sensitivity” (Encyclopedia Britannica, 2019). As we are working with the position of time and space of an aircraft a “Doppler radar systems can provide information regarding the movement of targets as well as their position by measuring the shift (or change) in phase between a transmitted pulse and a received echo, the target’s movement directly toward or away from the radar is calculated” (How Radar Works., 2019).
Several factors affect the performance of a given radar system, these factors include
- (1) the maximum range at which it can see a target of a specified size, (2) the accuracy of its measurement of target location in range and angle, (3) its ability to distinguish one target from another, (4) its ability to detect the desired target echo when masked by large clutter echoes, unintentional interfering signals from other “friendly” transmitters, or intentional radiation from hostile jamming (if a military radar), (5) its ability to recognize the type of target, and (6) its availability (ability to operate when needed), reliability, and maintainability (Encyclopedia Britannica, 2019).
These and many other factors create issues when attempting to use radar to find and track UAS as “Echoes from land, sea, rain, snow, hail, birds, …but they are a nuisance to those who want to detect aircraft, ships, missiles, or other similar targets. Clutter echoes can seriously limit the capability of a radar system… (we must) minimizing the effects of clutter without reducing the echoes from desired targets” (Encyclopedia Britannica, 2019)
UAS tend to be small in size and have a low electromagnetic signature, which can be missed by most traditional detection measures such as an airport radar system; however, a micro–doppler radar “is able to detect movement – specifically, speed differences – within moving objects. And drones tend to have propellers that create a large spectrum of speed differences. Part of the propeller is moving towards you, and part is moving away (9 Counter-Drone Technologies To Detect And Stop Drones Today, 2019). This micro-doppler technique can identify drones and even distinguish drones from birds. UAS can also be detected by using the millimeter-wave range as this range is “ideal for surveillance tasks in the immediate environment, particularly when visibility is poor. In comparison to the optical and IR spectrum, millimeter waves have good penetration characteristics in the presence of fog, smoke, or dust.” (Caris, 2019)
Radio Frequency (RF)
Radio Frequency (RF) sensors can detect the UAS and the operator or ground station location from which the control signal or payload exploitation signal is being sent and received. Commercial drones are usually operated via a radio control signal and often have onboard data link transmitters for real-time sensor download (typically in the 2.4 GHz ISM band). These upload and download frequency signals can be detected and geolocated (Drone Detection , 2019). RF sensors are passive and do not require legal authorization for use, so they will not emit signals that can cause issues with other signal emitters in a given area. RF sensors are one of the first lines of defense in C-UAS as they can “detect commercial, consumer, and DIY or prototype drones, flight paths, and the location of drones. RF sensors are capable of identifying a drone’s type and model based on the protocol or frequency the drone is operating” (Friedberg, 2019).
Electro-Optical (EO) Sensors-Full Motion Video Cameras
Full motion video or digitally enhanced cameras can “provide vital visual confirmation of a drone, help identify payloads, and record forensic evidence of drone intrusions. This sensor is important for times when human verification is necessary, or when security teams need visual evidence of an intrusion” (Friedberg, 2019).
Video and camera sensors are limited in their ability to find a UAS and generally need to be cued to a UAS through other sensors. Cameras are limited in a C-UAS system due to limitations of weather conditions, low visibility environments, line of sight, range, smoke environments, and nighttime operations. EO sensors are normally combined with an infrared sensor (IR) device and sold as one unit, as an EO/IR sensor.
Infrared Sensors (IR)
Infrared sensors are based on the science that “all objects emit infrared energy, known as a heat signature. An infrared camera (thermal imager) detects and measures the infrared energy of objects. The camera converts that infrared data into an electronic image that shows the apparent surface temperature of the object being measured” (Thermography Fundamentals, 2016).
Figure 5-3: Infrared Heat Signature
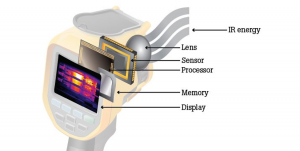
Source: (Thermography Fundamentals, 2016)
This temperature difference offers the ability for the sensors to surveil the aircraft in the sky as the “camera processor takes the signal from each pixel and applies a mathematical calculation to it to create a color map of the apparent temperature of the object (Thermography Fundamentals, 2016).
Acoustic Sensors for C-UAS
The concept behind acoustic sensors is based on the idea that the distinct sounds created by different aircraft can be identified and distinguished from all other sounds in a given area as “acoustic sensors use a library of known sounds and frequencies to detect UAVs, but the rapid development of new platforms makes it impossible for those to be fully up-to-date. Sensor sensitivity also is an issue; too sensitive generates many false positives” (The new world of counter-drone technology).
It’s a Big Sky-How Can We Discern the Clutter from the UAS?
Another issue of tracking airborne objects is one or more of the objects in the sky making contact or colliding into each other; however, this is rare and is known as the Big Sky Theory. The Big Sky theory states “that two randomly flying bodies are very unlikely to collide, as the three-dimensional space is so large relative to the bodies. Some aviation safety rules involving altimetry and navigation standards are based on this concept” (Big Sky Theory, 2019).
With the “advent of radar, two aircraft could be “seen” and maneuvered clear of each other’s flight paths. The advent of Traffic Collision Avoidance System (TCAS) equipment allowed equipped aircraft to resolve conflicts. Now we have technology that allows space-based positioning of two aircraft” (Big Sky Theory, 2019).
One of the techniques to control the Big Sky Theory is assigning different types of airspace rules to control certain areas of time and space. This use of airspace allows different rules to be assigned to different environments. As an example, if an aircraft, manned or unmanned is not following the agreed-upon rules it is considered to be hazardous. Predetermined responses are employed depending on which airspace the vehicle is operating in and to what degree the vehicle is not following the agreed-upon rules.
Figure 5-4 depicts the different types of airspace and control within each of these airspace corridors. Depending upon which airspace corridor a vehicle is operating in, a series of positive controls are in place including radar tracking, mode “C” altitude encoders (allows for a unique code to be assigned to each aircraft in an area), self-reporting by operators, visual indicators and radio call signs. This concept has worked well in the manned aircraft arena as all aircraft in controlled airspace must have an altitude encoder, and “up until now means planes moving between Europe and North America have had to use regimented tracks in the sky. The rigid structure maintains large areas of clear space around planes to remove the possibility of a collision” (Amos, 2019). This concept must now become more flexible as unmanned and optionally manned technology proliferates around the world. The system is slowly evolving with the invention of Automatic Dependent Surveillance-Broadcast (ADS-B) transponders. These transponders push out information from a particular aircraft – including its identity, GPS-determined altitude, and ground speed. ADS-B was introduced to enhance surveillance and safety over land, but the messages can also be picked up by satellites (Amos, 2019).
Figure 5-4: Air Space Classification
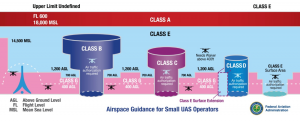
Source: (FAA, 2019).
Table 5-3: Airspace and Altitude Definitions
| Airspace | Altitude Definition |
| Class A | Generally, airspace from 18,000 feet mean sea level (MSL) up to and including FL600.
Includes airspace overlying the waters within 12 nautical miles (NM) off the coast of the 48 contiguous United States and Alaska. |
| Class B | Generally, from the surface to 10,000 feet MSL including the airspace from portions of Class Bravo that extends beyond the Mode C Veil up to 10,000 feet MSL (e.g. SEA, CLE, PHX). |
| Class C | Generally, from the surface up to 4,000 feet MSL including the airspace above the horizontal boundary up to 10,000 feet MSL. |
| Class D | Generally, airspace from the surface up to 2,500 feet above the airport elevation. The configuration of each Class D airspace is individually tailored. |
| Class E | Above 14,500 feet MSL over the 48 United States and Alaska, excluding airspace at and below 2,500 feet AGL and excludes airspace 18,000 MSL or above.
Includes airspace overlying the waters within 12 nautical miles (NM) off the coast of the 48 contiguous United States and Alaska. |
| Class G | Uncontrolled airspace – not designated as Class A, B, C, D, or E. |
Source: (-Handbooks, 2019) [1]
Automatic Dependent Surveillance-Broadcast (ADS-B)-Helping to Eliminate the “Good Guy” from C-UAS Surveillance and Reconnaissance Challenge
The introduction of the Automatic Dependent Surveillance-Broadcast (ADS-B) will help transform surveillance and reconnaissance of manned aircraft, yet how this new technology can fit into the unmanned arena and possibly assist C-UAS is still being determined. The U.S. firm, Aireon, says “its new satellite surveillance network is now fully live and being trialed over the North Atlantic. The system employs a constellation of 66 spacecraft, which monitors the situational messages pumped out by aircraft transponders. These report a plane’s position, altitude, direction and speed every eight seconds. The more detailed information they now have about the behavior of airplanes means more efficient routing can be introduced” (Amos, 2019).
ADS-B is a system of systems and rides “piggyback on all 66 spacecraft of the Iridium sat-phone service provider. These sensors make it possible now to track planes even out over the ocean, beyond the visibility of radar – and ocean waters cover 70% of the globe” (Amos, 2019). If we know where the manned “friendly” aircraft are in time and space, this may assist in the surveillance and reconnaissance of potentially harmful UAS and allow for the tracking and neutralizing of this threat. Figure 5-5 illustrates how ADS-B will operate in the next few months as the FAA (Federal Aviation Administration) has mandated that all aircraft are required to comply by January 1, 2020. This includes any aircraft operating in Class A, B, or C airspaces. Additionally, any aircraft operating in Class E airspace (above FL100 MSL but not below 2,500 ft AGL) must also comply (“The “No-BS” PDQ ABC’s of ADS-B,” 2019).
Figure 5-5: ADS-B Signal Broadcast
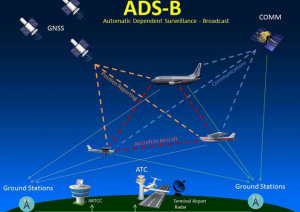
Source: (The “No-BS” PDQ ABC’s of ADS-B, 2019)
With ADS-B technology offering near-real-time surveillance from satellites, the ability to “introduce greater flexibility into the management of the airspace (become[s] possible). For example, in the North Atlantic, traditional in-line safe separation distances will eventually be reduced from 40 nautical miles (80km) down to as little as 14 nautical miles (25km)” (Amos, 2019). This flexibility offers great promise for the airline industry; however, it also complicates C-UAS, as aircraft are no longer on a known, predictable flight path. Attempting to mandate that all UAS incorporate ADS-B transponders may prove to be difficult as the technology can cost thousands of dollars, and integration into current UAS designs may not be completely successful.
The Difficulty of Differentiating Harmless Aircraft from Threat Aircraft in the C-UAS Space
How do you determine what is flying in the area-is it a bird, small plane, UAS, and is it a threat? The standard airport radar does not work well for finding and tracking most UAS. There are several reasons for this, including the size of the aircraft, the material it is made from, and the general lack of a heat signature in most of the Group 1 and Group 2 weight classes. (See also Figures 5-6, and 5-7)
Table 5-4: UAVs Classification According to U.S. DoD
| UAVs Classification According to the U.S. Department of Defense (DoD) | ||||
| Category | Size | Maximum Gross Takeoff Weight (MGTW) (lbs) | Normal Operating Altitude (ft) | Airspeed (knots) |
| Group 1 | Small | 0-20 | <1,200 AGL* | <100 |
| Group 2 | Medium | 21-55 | <3,500 | <250 |
| Group 3 | Large | <1320 | <18,000 MSL** | <250 |
| Group 4 | Larger | >1320 | <18,000 MSL | Any airspeed |
| Group 5 | Largest | >1320 | >18,000 | Any airspeed |
| *AGL = Above Ground Level **MSL = Mean Sea Level Note: If the UAS has even one characteristic of the next level, it is classified at that level. |
Sources: (U.S. Army Unmanned Aircraft Systems Roadmap 2010-2035, 2010)
Complicating the matter of discerning manned from unmanned systems is a multitude of ontologies and taxonomies used to discuss different sizes, weight, and mission classes of aircraft as illustrated in Tables 5-3 and 5-4. The fact that most UAS blur the line between civilian and military use (dual-use technology) compound these issues. Cohesive agreed to classifications for UAS, and manned aircraft is a worldwide issue. There is a real challenge in verifying if an aircraft is manned, definitely unmanned, or maybe optionally manned when a human must make a judgment call of life or death when determining if a UAS has nefarious intent or is simply an innocent aircraft flying in a given airspace.
Table 5-5: NATO UAS Classification
| NATO UAS Classification | ||||||
| Class | Category | Normal Employment | Normal Operating Altitude | Normal Mission Radius | Primary Supported Commander | Example Platform |
| Class III (> 600 kg) | Strike/ Combat* | Strategic/ National | Up to 65,000 ft | Unlimited (BLOS) | Theatre | Reaper |
| HALE | Strategic/ National | Up to 65,000 ft | Unlimited (BLOS) | Theatre | Global Hawk | |
| MALE | Operational/ Theatre | Up to 45,000 ft MSL | Unlimited (BLOS) | JTF | Heron | |
| Class II | Tactical | Tactical Formation | Up to 18,000 ft AGL | 200 km (LOS) | Brigade | Hermes 450 |
| Class I | Small (>15 kg) | Tactical Unit | Up to 5,000 ft AGL | 50 km (LOS) | Battalion, Regiment | Scan Eagle |
| Mini (<15 kg) | Tactical Subunit (Manual or hand launch) | Up to 3,000 ft AGL | Up to 25 km (LOS) | Company, Platoon, Squad | Skylark | |
| Micro**
(<66 J) |
Tactical Subunit (manual or hand launch) | Up to 200 ft AGL | Up to 5 km (LOS) | Platoon, Squad | Black Widow |
Source: (Szabolcsi, 2016)
An airport radar normally detects aircraft as small as helicopters and single-engine land aircraft, and as large as jumbo jets, however, these all of these aircraft are generally made out of metal, have a recognizable heat signature, and a pilot that can communicate location and intent. UAS tend to have none of these attributes. Additionally, most UAS are made from plastics, balsa wood, composite materials, or combinations of all of these materials, with metal tending to be used less than any other material. Group 1 and 2 UAS tend to be battery-powered and therefore offer no discernable or trackable heat source. UAS that uses a combustible fuel engine will still not have enough of a heat signature or radar return signature to make surveillance and reconnaissance an easy task.
Figure 5-6: Size Comparison Drone to Commercial Aircraft -A
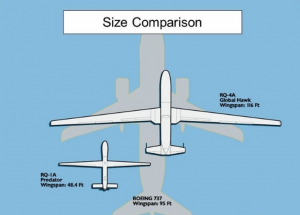
Figure 5-7: Size Comparison Drone to Commercial Aircraft -B
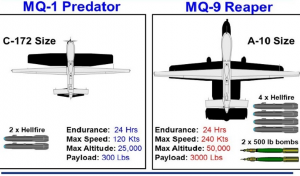
Sources: (Aviation-Design of UAV Systems, 2014) (Eggers)
These composite built UASs do not reflect radar energy the way denser materials such as metal does. UAVs can further reduce any energy by using composites made with radar absorbing materials (RAM) or be constructed to include a radar-absorbing structure (RAS) into the superstructure using reinforced plastics or other unique non-traditional materials. Most UAS are small enough that finding a radar signature is sufficiently difficult; however there is now “a plethora of foams and coatings that can reduce radar signature now make up a highly active sector of the microwave materials market” (Marsh, 2010).
The use of composites is not unusual in UAS as reinforced plastic materials are known for their unique combination of low weight with high strength, stiffness and fatigue resistance, but their electromagnetic (EM) characteristics are important too; witness, for example, glass fiber reinforced plastic (GRP)-based printed circuit boards and carbon composite electromagnetic interference (EMI) shielding enclosures for sensitive electronic equipment. Low-weight RAS can be made from glass and carbon fiber composite lattices in which the voids are occupied by microwave absorbent foams. Absorption effectiveness would be related to the volume fraction of the grid cell structure and the distance between elements (Marsh, 2010).
New Challenges Require New Thinking-Combined Sensors
The most successful C-UAS initiatives incorporate a multi-sensor approach to ensure the accurate identification of a UAS as
relying on just one detection method; it can be possible for a drone to be missed. For example, when using conventional radar, it can be difficult to detect low-flying drones or distinguish drones from birds. Or if the drone is obscured by buildings or trees, an optical sensor will struggle to pick it up. By augmenting the radar and optical sensors with spectrum monitoring, the security team (will) have a much clearer picture of any potential drone activity (Drone Detection , 2019).
The discussion presented here is a sampling of the technical challenges of finding and tracking UAS. The tasks of identifying the specific UAS type, aircraft owner, what the UAS is generally used for (normal payloads) and the aircraft operator become an even greater challenge as “C-UAS systems, employing combined data from several sensors, also must be able to differentiate between legitimate and hostile, allied, and enemy UASs — something no known system can do. This is where a human operator must intervene to make what often is a split-second assessment” (Wilson, 2018).
Since the early years of the FAA, the agency has mandated that manned aircraft must be registered and assigned a tail number, which must be displayed permanently on the aircraft. Information on manned aircraft is easily found in databases around the world. As a newer technology that is evolving faster than policies, laws, and governance can keep pace with, there is no comprehensive database that offers an easy UAS identification look up and even if there were such databases, the varying laws for registering the UAS (along with limited compliance) would render most of the information incomplete and unusable. New UAS are evolving at a rapid pace, and their missions are far beyond the once normal camera sensor work as UAS are taking over many traditional manned aircraft missions. This is illustrated with Boeing’s aircraft refueling drone which is an “advanced unmanned aircraft designed to refuel the US Navy’s fighter jets in mid-air has taken to the skies operating under the name T1, the prototype MQ-25 performed an autonomous flight over the course of two hours at MidAmerica St. Louis Airport” (Lavars, 2019). The FAA is continuing to struggle with these issues. In July 2019, many US lawmakers sent a letter to the Secretary of Transportation stating that
“We write to register our ongoing concerns regarding the continuing delay in the issuing of the Federal Aviation Administration’s (FAA) rule requiring remote identification for unmanned aircraft systems (UAS) and urge you to dedicate the necessary staff and resources for the rapid publication of a notice of proposed rulemaking (NPRM) on this subject…the failure to complete Remote ID poses “serious risks” to the airspace and also “stifle innovation” in the drone industry. There are many reasons for this – the technology isn’t simple, there are multiple methods and discussions over which is best, and many stakeholders in the mix” (McNabb, 2019).
This section of the chapter offers a glimpse of new technologies, tactics, techniques, and policies that are being explored to assist the difficulties in the C-UAS surveillance and reconnaissance mission areas. Technologies that were originally designed to protect military installation are being modified for C-UAS missions. The Scanning Surveillance Radar System (SSRS) is an example and is “ideally suitable for the detection and precise location of several drones of both classes (micro and mini UAS) at close range. In addition, the SSRS system offers live tracking for up to four UAS in a measurement range of 50 to 150 meters”(Caris, 2019). This technology is effective for smaller UAS; additional combined sensor technology must be used to create a full C-UAS spectrum of protection.
Many C-UAS directories exist; however, a good amount of the information is not vetted correctly or is more in an advertising format than an informative format. The Counter UAS Directory from www.unmannedairspace.info is one of the more comprehensive lists. The latest edition had 83 technologies discussed within a 54-page document. The directory is free to the public and tends to be vetted with only verifiable information listing “available counter-UAS systems, networks, and components and is supplied free of charge…Information is supplied directly by suppliers, with data edited to remove unverifiable claims” (FAA, 2019).
One of the issues that have proven to be difficult in the C-UAS arena is attempting to not only find and track a vehicle; it is attempting to find where the vehicle is being controlled from and who is controlling the vehicle. New technology is being developed to cope with this issue as “CACI’s SkyTracker® Technology Suite is a counter-small unmanned aircraft system (C-sUAS) capability comprised of different form factors designed to exploit the radio communication between small unmanned aircraft systems (sUAS) and their controller” (CACI, 2019).
The SkyTracker® has three different form factors depending on C-UAS requirements; they include the:
CORIAN system provides fixed facility protection against unmanned aircraft systems (UAS) threats to warfighters and critical infrastructure. CORIAN detects, identifies, tracks, and mitigates sUAS threats using precision neutralization techniques to ensure little to no collateral damage to the surrounding radio frequency (RF) spectrum and existing communications.
AWAIR® system provides on-the-move force or facility protection against hostile sUAS. The ruggedized mobile platform leverages the CORIAN software baseline to precisely detect, identify, and mitigate sUAS threats. The system can be easily deployed on a vehicle or marine vessel, providing both ground and maritime convoy protection.
CACI’s man-packable advanced attack system can defeat small, complex UAS. The system surveys the environment to enable deployed units to counter sUAS and analog video signals. The system can operate autonomously to deliver precision distributed attacks and provide rapid, responsive force protection capability in hostile environments (CACI, 2019).
A U.S. applied research not-for-profit company known as SRC “is applying its extensive background in electronic warfare, air surveillance, and target detection, tracking and classification algorithms to help detect, track and defend against low, slow and small unmanned aircraft system (UAS) threats” (Counter-UAS Systems, 2016).
SRC has taken this knowledge and create C-UAS technology for both the military and civilian market places.
Silent Archer® counter-UAS technology detects, tracks, identifies, and defeats hostile UAS. The technology comprises proven, radar and electronic warfare systems, a camera for visual identification of targets, and a 3-D user display to provide the warfighter with advanced situational awareness.
Small, slow, low-flying drones can easily slip through current security measures, posing an undetected threat to personnel and property. SRC’s Gryphon Skylight® drone security solution relies on radar and spectrum sensing to detect and identify UAS, commercial aircraft, and even birds to give you a clear picture of your secure airspace (Counter-UAS Systems, 2016).
Mission Planning Secrecy – Protecting the Data
The first question in protecting the data is, does it matter if the data is seen by others? This may seem counterintuitive to this conversation; however, encrypting data carries costs that may not be needed in most C-UAS scenarios. The art of surveillance and reconnaissance tends to be done in the shadows. In the C-UAS arena it might be more advantageous to allow the information to be known by all who have access, allowing for additional informational inputs and more “eyes” on the subject aircraft. Now, the response to the subject aircraft is another matter, as individual companies and governments may not want to disclose the exact methods being employed and the effect these methods will have on the subject aircraft. Information such as acoustics signatures is important to mask and not be disclosed as today’s sensor includes
a range of tracking and data collection capabilities and visualizations, including early warning alerts with target bearings, multiple simultaneous threat detection, and tracking, and 3D-track of targets. The system can be configured with multiple networked sensors to support a wide area of coverage, from remote field operations to congested urban environments. Captured data can be integrated into existing command and control software programs to support Intelligence, surveillance and reconnaissance, operations, and decision-support applications (General Atomics demonstrates acoustic drone-detector to US Army, 2019).
The nature of most UAS platforms are inexpensive and openly available components, yet these components are often:
built independently without cyber protection standards built-in leaving the systems vulnerable, and the very nature of “plug and play” tends to create incompatibility in cyber protection with very few if any true data standards.
Analysis of the configuration and flight controllers/microprocessors of several popular UAV models having multiple rotors revealed weaknesses associated with both the telemetry links streaming data to and from a drone via serial port connections (in which information could be captured, modified, or injected), and the UAVs’ connections to their ground station interface (whose data link could be spoofed, enabling hackers to assume complete control of the vehicle).” (Nichols & et.al, 2019)
Sensor data security and the threat of attacks within the cyber domain must be a part of all aspects of mission planning. Mission planning will require tradeoffs between target area access, sensor capability and availability, information time dominance, and cyber/data security requirements.
Mission Planning for C-UAS for Perimeter Protection
Now that the foundation of combined for C-UAS has been discussed, the placement and interconnection of these sensors systems are required for triangulation of the UAS. As seen in Figure 5-8, the interlocking nature and overlap of sensors will create a triangulation of the UAS target.
Figure 5-8: Overlapping Sensor Example
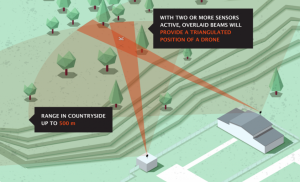
Source: (Perimeter Protection & Defense, 2019).
In protecting the perimeter of a given facility, an in-depth analysis must take place to understand the ability to obtain the security level required before surveillance and renaissance of the area can begin. Once the reconnaissance of the area is complete the surveillance of any unauthorized UAS can occur and will be digitally documented and the appropriate countermeasures taken against the offending UAS.
Combining the correct sensors (discussed earlier) will depend on many factors including:
- Topography (line of sight)
- Amount and height of buildings and human-made objects in the area
- Protection level- Provide for 24/7 operations, all-weather (or just during occupied times)
- Frequency noise level-electromagnetic interference
- Applicable laws for the area/country
- Threat level-is there known threats in the area-critical infrastructure or protecting the family business
- Most likely type of threat (quad-rotor with EO/IR sensor or fixed-wing suicide UAS)
- What are the likely responses to the threat? How does the combined sensors system verify the threat has been neutralized or has left the area and is no longer a threat?
- What is the budget for C-UAS? How much of this budget can be allocated to surveillance and reconnaissance?
- Can the sensors cover hidden areas or pockets without overlapping coverage?
Each of these factors will affect the type and number of sensors placed and how these sensors report back, store information, and are utilized during the normal course of time, or during a C-UAS threat event and the threat de-escalation and neutralization phase. Additionally, technology refresh schedules should be considered as the UAS market continues to evolve, and the tactics and techniques from threat actors get more sophisticated. The planning for C-UAS perimeter protection must be updated to match the new threats.
Conclusions
Reviewing the difference between surveillance and reconnaissance in the context of C-UAS offers distinctions between the typical thought process of sensors looking down on a target and the reality of the difficulty in attempting to find UAS targets in the vastness of the sky. The sensors that track manned aircraft are often not good at finding and tracking UAS as the size, materials, heat signatures, and overall UAS radar profiles are vastly different than of manned aircraft. The ability to discern this difference, catalog it and maintain the accuracy of the database information is imperative to avoid loss of life from an accidental mischaracterization of manned aircraft versus from a hostile UAS. The introduction of ADS-B will assist in identifying manned aircraft in controlled airspace. The transponder will also make the task of determining a threatening UAS in this airspace easier to detect and mitigate. The use of multiple sensor suites and continued innovation in this space is required to have the best chance of allowing surveillance and reconnaissance to occur in this ever-changing and growing field of UAS. The overall identification mechanisms, be it administrative or technical for UAS are issues that are still being developed through the creation or adaptation of policies, laws, and governances by aviation authorities across the globe. The ability for all aviation authorities to agree upon identification mechanisms, ontologies and taxonomies of the UAS arena along with national and international cooperation agreements offers an opportunity to positively impact the safety of the aviation community.
Questions
- What is the difference between reconnaissance and surveillance in the context of C-UAS?
- What airspace can UAS operate in? (Hint below 400AGL)
- For C-UAS surveillance and reconnaissance, does the UAS size and composition matter? Why or why not?
- How would you position multiple sensors to surveil a given area for C-UAS?
- What is the correct sensor placement for triangulating UAS?
References
9 Counter-Drone Technologies To Detect And Stop Drones Today. (2019). Retrieved from www.robinradar.com: https://www.robinradar.com/9-counter-drone-technologies-to-detect-and-stop-drones-today
Amos, J. (2019). Satellite plane-tracking goes global. . Retrieved from www.bbc.com/news/: https://www.bbc.com/news/science-environment-47793983
Aviation-Design of UAV Systems. (2014). Retrieved from aviation.stackexchange.com: https://aviation.stackexchange.com/questions/43780/why-arent-there-any-single-turbofan-airliner
Big Sky Theory. (2019). Retrieved from www.apstraining.com: https://www.apstraining.com/resource/the-big-sky-theory-luck-and-loss-of-control-in-flight/
CACI. (2019). SkyTracker® Technology Suite. Retrieved from www.caci.com/skytracker/: http://www.caci.com/skytracker/
Caris, M. (2019). Detection of Small Drones With Millimeter Wave Radar . Retrieved from www.fhr.fraunhofer.de/en/businessunits/security/: https://www.fhr.fraunhofer.de/en/businessunits/security/Detection-of-small-drones-with-millimeter-wave-radar.html
Counter-UAS Systems. (2016). Retrieved from www.srcinc.com: https://www.srcinc.com/about/index.html
Dictionary, M.-W. (2019). Definition of Reconnaissance. Springfield, MA: Merriam-Webster, Inc.
Drone Detection . (2019). Retrieved from www.crfs.com/drone-detection/: https://www.crfs.com/drone-detection/
Eggers, J. (n.d.). MQ-1 Predator/MQ-9 Reaper Unmanned Aircraft Systems. Retrieved from slideplayer.com/: https://slideplayer.com/slide/5070244/
Encyclopedia Britannica. (2019). Factors Affecting Radar Performance. Chicago IL: Britannica Group.
FAA. (2019). Airspace 101 – Rules of the Sky. Retrieved from www.faa.gov/uas/: https://www.faa.gov/uas/recreational_fliers/where_can_i_fly/airspace_101/
Friedberg, S. (2019). CUAS Technology Series: Detection Hardware. . Retrieved from www.dedrone.com/blog/: https://www.dedrone.com/blog/cuas-technology-series-detection-hardware
General Atomics demonstrates acoustic drone-detector to US Army. (2019). Retrieved from www.unmannedairspace.info/: https://www.unmannedairspace.info/counter-uas-systems-and-policies/general-atomics-demonstrates-acoustic-drone-detector-us-army/
Goyal, S. (2019). airport-surveillance-radar. Retrieved from www.jagranjosh.com/: https://www.jagranjosh.com/general-knowledge/airport-surveillance-radar-1551178752-1
-Handbooks, F. (2019). Airspace. Retrieved from www.faa.gov/regulations_policies/handbooks_manuals/aviation: https://www.faa.gov/regulations_policies/handbooks_manuals/aviation/phak/media/17_phak_ch15.pdf
How Radar Works. (2019). Retrieved from www.weather.gov/jetstream/how: https://www.weather.gov/jetstream/how
Lambeth, B. S. (2006). Air Power Against Terror: America’s Conduct of Operation Enduring Freedom. Santa Monica, CA: RAND Corporation.
Lavars, N. (2019). Boeing’s aircraft refueling drone flies for the first time. Retrieved from newatlas.com/military/: https://newatlas.com/military/boeings-aircraft-refueling-drone-first-flight/
Marsh, G. (2010, Volume 54, Issue 6, November–December). Going Stealthy with Composities. Reinforced Plastics, pp. Pages 30-33.
McNabb, M. (2019, July 10). U.S. Lawmakers Express Frustration With Drone Remote ID Delay, “This Summer” Says Standards Committee Chair. Retrieved from dronelife.com: https://dronelife.com/2019/07/10/u-s-lawmakers-express-frustration-with-drone-remote-id-delay-this-summer-says-s
Michel, A. (2018, February). CSD-Counter-Drone-Systems-Report. Retrieved from dronecenter.bard.edu/: https://dronecenter.bard.edu/files/2018/02/CSD-Counter-Drone-Systems-Report.pdf
Nichols, R. K., & Mumm, H. C. (2018). Unmanned Aircraft Systems (UAS) in the Cyber Domain: Protecting USA’s Advanced Air Assets. Manhattan, KS: New Prairie Press /21/.
Nichols, R., & et.al. (2019). Unmanned Aircraft Systems in Cyber Domain: Protecting USA’s Advanced Air Assets, 2nd Edition. Manhattan, KS: NPP Press /27.
Perimeter Protection & Defense. (2019). Retrieved from www.sqhead.com/drone-detection/: https://www.sqhead.com/drone-detection/#1533491859389-4d070f8f-97fb
Snow, C. (2014, February 6). Making Sense of Drones. Retrieved from droneanalyst.com: http://droneanalyst.com/2014/02/06/making-sense-of-drones
Surveillance, D. o. (2019). Definition of Electronic Surveillance. Detroit, MI: Rock Holdings, Inc.
Szabolcsi, R. (2016). Beyond Training Minimums – A New Concept of the UAV Operator Training Program. International conference KNOWLEDGE-BASED ORGANIZATION, 22. doi:doi:10.1515/kbo-2016-0096
The “No-BS” PDQ ABC’s of ADS-B. (2019). Retrieved from murfreesboroaviation.com/: https://murfreesboroaviation.com/no-bs-pdq-abcs-ads-b/
The new world of counter-drone technology. (n.d.). Retrieved from www.militaryaerospace.com/unmanned/: https://www.militaryaerospace.com/unmanned/article/16707131/the-new-world-of-counterdrone-technology
Thermography Fundamentals. (2016). Retrieved from www.fluke.com/en-us/: https://www.fluke.com/en-us/learn/best-practices/measurement-basics/thermography
U.S. Army Unmanned Aircraft Systems Roadmap 2010-2035. (2010). Fort Rucker, AL: US : U.S. Army.
Wilson, J. (2018, November 1). the-new-world-of-counterdrone-technology. Retrieved from www.militaryaerospace.com: https://www.militaryaerospace.com/unmanned/article/16707131/the-new-world-of-counterdrone-technology
[1] ** Starting January 1, 2020, aircraft must be equipped with ADS-B Out to fly in most controlled airspace. (“Airspace,” 2019) See http://www.asy.faa.gov/safety_products/airspaceclass.htm for additional information.

