Chapter 3: Developing a C-UAS Strategy Goals, Options, Target Analyses, Process Selection, Operational Metrics Approaches to Countering UAS Activities (First Principles)
H.C. Mumm
Student Learning Objectives
The student will gain knowledge on the concepts and framework as it relates to the process of developing an end-to-end Counter-Unmanned Aerial System (C-UAS). The student will gain knowledge through real-world examples and a case study, allowing the student to use critical thinking skills to apply learning to multiple C-UAS situations.
History
When drones became dangerous, counter-drone responses had their start. One of the more famous counter-drone operations was waged against the German V-1 Buzz Bomb. Due to its speed and size, this was a difficult drone to destroy. The British air defense used anti-aircraft guns, static balloons where the cable was the kill mechanism, and fighter aircraft. (Military-history-now, 2015) Only the fastest fighters would do, such as the de Havilland Mosquito. British fighter aircraft would be alerted and guided to the V-1 by ground radar. Once the fighters intercepted the V-1, they would place their wingtip under the wingtip of the V-1. The disruption in the airflow would tip the V-1, which would cause the primitive gyro stabilization to tumble and send the V-1 crashing to the ground. The fighters would also shoot down the V-1, which was a risky decision as the V-1 could detonate and also destroy the attacking fighter. Post-World War II, counter-drone tactics have been mostly anti-aircraft guns.
C-UAS Analysis Framework
1. Analyzing the Threat
Careful study will allow for an in-depth analysis of the threat, and thus a critical first step in the process. By answering the questions in the C-UAS analysis phase, the requirements will be determined, and a solution can be devised to build an appropriate counter-drone system. Mistakes in this first step can result in developing an ineffective system or a system inappropriate for the job. There are several types of questions that need to be answered within the analysis steps: what is the nature of the threat; what are the aerodynamic abilities of the threat; what is the overall design of the threat; is it a singular or multiple entity threat? As well as what is the navigation method used by the threat?
Understanding the Purpose and Weaponization of the Threat
The analysis needs to include answers to the following questions: What is the nature of the drone threat? Is it just surveillance? Is it reconnaissance? Is it directing fire support? Is it a Kamikaze drone? A Kamikaze drone can be as small as a commercial quadcopter with explosives onboard to a significantly larger aircraft or even cruise missile. Does the drone have the ability to release weapons and return home? If the vehicle is equipped with a warhead, can it be detonated in flight? Is the drone delivering contraband items over a barrier? Small drones are commonly used to drop contraband drugs over prison walls (Biesecke, 2011). Once the nature of the threat is determined, the next step is to determine the aerodynamic capabilities of the threat.
Understanding the Aerodynamics of the Threat
These questions should include as much information as possible about the offending drone (s): How fast? How high? What is the range? What is its payload capacity? As the speed of the drones increases, the potential response methods decrease. As these questions are answered, the expense and level of effort to develop the defense can be determined. Additional questions that need to be asked include: How can it be tracked? Does the drone use stealth technology? Stealth technology may be applied to radar, infrared, visual, or auditory signatures. Most of the time, the drone is considered stealthy just because of its size and that it is made from material with little or no metal except for the avionics. Another component of a drone’s signature is speed. It is very common for modern radars to be dependent on the Doppler Effect for detection and tracking. Slow objects can fall into the notch designed to eliminate ground clutter (vehicles) and birds. Objects that are not moving towards or away from the radar (called the beam) can disappear altogether from the radar scope (Saabgroup, 2018).
Understanding the Air Vehicle Design of the Threat
Air vehicle design is an important factor in creating an effective defensive response. Questions need to be asked to determine what materials were used to construct the aircraft. Is it metal, plastic, or a composite? Non-metallic aircraft are more susceptible to a variety of counter technologies, including tactical lasers. For the main body and flight surfaces: what will it take to breach the body or disable the flight surface? Does the vehicle have exposed rotors or propeller that can be attacked? Rotors and propellers can be destroyed by lasers, broken by impact, or snagged by a net. Does the vehicle has exposed electronics or electronics that can be easily jammed, interfered with, or destroyed using lasers, jammers, radio waves, or by overpowering a frequency? Can the warhead (if equipped) be detonated in flight?
Is it One Drone or Multiple Drones?
Are there current intelligence reports that indicate the tactics that are or are expected to be employed by the enemy? Are they using one type of drone or multiple types? Are these drones operating independently, together, or using swarm tactics? As the numbers of drones increase, so does the complexity of the response. Drone tactics, techniques, and procedures are largely unwritten as the technology is adopted and adapted into the civilian and military arena at a rate of speed that has not allowed for in-depth, intelligent gathering, databasing or analysis to occur.
Understanding the Navigation
Threat control and navigation methodology can be fundamental to the potential solution. What frequencies is the drone using for control, information gathering, and distribution? What navigation platform does the drone use? A great variety of drones use either GPS (Global Positioning System) or GLONASS (Global Satellite Navigation System) or both. Some drones are extremely dependent on these navigational signals. Other drones have an IMU (inertial measurement unit) that provides both altitude and location references. The smaller the IMU, the higher the drift rate usually is and thus the dependence on GPS type signals for frequent corrections. (UNOOSA, 2019)
2. Solution Limitations
Before starting on a proposed response solution, limitations must be identified. Many limitations are governmental in origin, while others are weather or terrain-related, based on the location for the deployment of the counter-drone solution.
Frequency Limitations
Many world governments control the frequency spectrum for their country. In the U.S., that control comes under the Federal Communications Commission (FCC) (Commission-Licensing, 2019). UAV operators can passively listen to the frequency spectrum, but as soon as the solution involves transmitting on a particular frequency or frequencies, then permission and approval must be sought from the FCC (or similar agency) for that transmission. This is especially true when it comes to using jammers as part of the solution as “Federal law prohibits the operation, marketing, or sale of any type of jamming equipment, including devices that interfere with cellular and Personal Communication Services (PCS), police radar, Global Positioning Systems (GPS), and wireless networking services (Wi-Fi)” (FCC, Jammer Enforcement, 2019). When it comes to exemptions: “Only federal agencies are eligible to apply for and receive authorization” (Commission-Licensing, 2019). Smaller drones often fall into the Wi-Fi set of frequencies, while larger drones often use a variety of radio or satellite frequencies. There are other countries in the world where this limitation is not as restrictive. Combat operations also open up the solution to a variety of jammers. During combat operations, it is easier to coordinate the jamming of data linked frequencies than it is to coordinate GPS jamming, due to the dependence that U.S. military forces have on GPS. As more GPS jam-resistant equipment makes it into military services, this limitation of GPS jamming will decrease.
Global Governance
In addition to particular frequencies, airspace is also controlled in many countries. In the U.S. that airspace control is governed by the Federal Aviation Administration (FAA). Drones in the U.S. are currently limited to 400ft AGL (above ground level) unless otherwise approved by the FAA. There are at least two drone-on-drone counter methodologies that would also fall under this limitation. Other countries have different limitations, and some countries have little or no limitations defined at this time. Any drone defense system will need to be coordinated with the host country or the combatant command within a war zone. Mutual coordination is especially true for any projectile or tactic that destroys the UAS, commonly referred to as a kinetic kill mechanism.
If the area to be defended is urban or suburban versus rural, the kill mechanism may be further limited; especially kinetic kill mechanisms. Bullets or missiles that are deployed and do not hit the intended target and can potentially injure or kill someone, and if the drone is large enough, the drone itself may crash into people or property. There are two caveats to consider when determining the risks of kinetic C-UAS against a lethal drone. One, the drone may cause much more damage if it is not destroyed, and two, even though an urban environment has a high population density, the odds of a drone crashing on an individual is surprising low. This is because people are physically a small portion of the area in an urban environment and often protected from this type of impact by buildings and other sturdy structures. This is especially true of all but the largest of drones; even they have limited mass per square foot of impact area. (C. Horowitz, 2016).
Legal Ramifications
Country, State, and local laws regarding drones and counter-drone operations are proliferating at a great rate around the world with no consistent theme. Some counter-drone technologies have been designated as illegal in some countries while not being recognized in other countries. Additionally, there are anti-hacking and technology laws that affect aircraft (in general) that can impact the use of certain counter-drone technologies. Hacking a drone to render it safe seems like a technically good idea; however, the legal ramifications can be significant, including being charged with grand larceny for drones ranging in price from $400 to $1,000. According to 18 U.S.C. § 32, it is a felony to willfully damage or destroy aircraft (§ 130i., 2019). Although many courts have chosen to sidestep these cases, a counter-drone engagement could subject the operator to civil, criminal, and tort liabilities. In the U.S., criminal and liability limits are disclosed, but these penalties (many severe) are not always disclosed in other countries. It is critical for the solution to adhere to the national and local laws including getting proper permissions or exemptions before any drone engagement. A major exemption falls under 6 U.S.C. § 130i Protection of certain facilities and assets from unmanned aircraft (§ 130i., 2019). Similar laws give the Coast Guard and Secretary of Energy Counter UAV authorization. Other countries are developing their own laws/rules for facility and asset protection.
Atmospheric Limitations
Weather is another limitation of a C-UAS solution. Atmospheric considerations are a key element in support of UAS flight testing. The local atmospheric environment (wind speed and direction, wind shear, temperature, precipitation, and turbulence) must be characterized and understood (Edward Teets, 1998). In regions where cloud cover and/or fog are prevalent for a significant portion of the year, most sensors used for the identification of UAS are significantly degraded.
3. Developing a Counter-drone Response:
Range
The range required for detection and interdiction of the drone or drones must be determined. If the drone can release weapons, that adds to the range required for detection and interdiction. The faster the incoming threat, the lower the approach, the larger the area needed to defend, the more lethal the weapon portion; the further out the drone needs to be detected and interdicted.
There is also the need to identify the number of response layers for the appropriate range. Will there be two or more response layers or just a one-point defense layer? Will there be a shoot-look-shoot requirement to produce the desired probability of kill on the drone? If there is a wave of attacking drones, more than one layer of defense is recommended.
Detection
There are several passive and active detection technologies available to include as part of the solution. Electronic Signal Monitoring (ESM) is a very desirable passive detection system. ESM systems detect the communication frequencies of the drone and its associated ground station. Depending upon the antenna sensitivity and the output power of the drone, these signals can be discovered at significant ranges. The key advantages of these systems are is that the ground station controlling the drone may be located and engaged and that the systems are numerous (İ, 2017).
When selecting a signal detection system, all of the potential frequency ranges must be considered to counter all of the potential threats. If only a sample of frequencies is known, then the solution might be lacking during execution. The systems that receive commercial drone frequency bands are proliferating and significantly increasing in capability. Additionally, these frequency detection systems can quickly identify the signals for the drone and ground station. Some frequency detection systems include the ability to produce a digital fingerprint that can be leveraged as evidence for later prosecution. However, these frequency detection systems that are available on the open market lack the frequency bands of the more sophisticated commercial drones as well as the military drone frequency bands.
There are acoustic sensors to detect drone sound signatures, but because of their short-range and limitations in noisy environments, they can be part of a solution; however, it is rare that a single sensor technique be a part of a complete in the overall C-UAS solution.
A key part of detection is identification. Other passive types of detectors such as long-range cameras, IR (infrared) sensors, and SWIR (short-wave infrared) can provide the necessary identification (Red-ID) that the object is a drone and a threat. There are software packages available that can provide a much quicker and longer-range identification than a human operator. Additionally, some detectors include powerful illuminators within a frequency band that provide a stronger return and fewer false alarms. Illuminators in the infrared bands are invisible to the eye.
Active detection is primarily centered on various radar types. Conventional military radars pick up large and fast-moving targets easily and reject slow or non-moving targets to reduce false alarms. There are some new tactical radars that are designed to pick up the smaller, slower set of drones in addition to the larger ones. One radar variety uses an active electronically scanned array (AESA), and another variation uses a continuous wave radar. The latter is currently range limited, but technology can be extended (İ et al., 2017).
4. Interdiction
Small Drones
As small drones have proliferated, so too have the small drone counter systems. An initial favorite is the Radio Frequency (RF) jammer. These are designed to jam the control uplink for the drone. If a drone frequency is successfully jammed, there are multiple possible outcomes. One possible outcome could be the drone flying back to home base, which would be useful in capturing the operator. However, if the operator designated the target as the home base, this method would be ineffective. A second outcome might be that the drone makes a controlled landing. The least desirable outcome is that the drone exhibits uncontrolled behavior and crashes.
A GPS spoofer can gain a type of control over the drone by manipulating the GPS location. The drone can be directed to a safe location for capture and de-arming if necessary.
Figure 3-1: XBee Chip
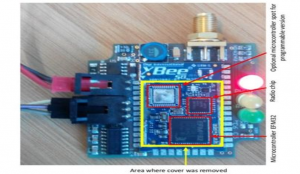
Source: (BBC, 2016)
Hacking a drone is facilitated by having multiple manufacturers using similar avionic designs and somewhat predictable drone behaviors. A relatively inexpensive set up like a telemetry module by Mr. Rodday using an XBee chip acquires the unique key and takes command of the drone, rendering it harmless. This action is significantly more difficult if the chip has been encrypted. (BBC, 2016). Nets are an effective tool against the typical small commercial drones as long as they are not too fast. See Figure 3-2. There are several varieties of employment: e.g., another small drone can carry a small net cannon and launch the net at another drone.
Figure 3-2: UAV Net

Source: (Openworksengineering, 2019)
This methodology usually comes with an attached line that allows the shooter to gently lower the offending drone to the ground. Nets can also be launched from the ground using equipment that looks like a bazooka. Less reliable unless used by an expert are the nets deployed by a shotgun shell.
A relatively inexpensive but effective system is a kamikaze type drone. See Figure 3-3. This can protect a fairly large area and can “shoot down” a variety of small drones. The key challenge is they must hit a vulnerable part of the target drone. As opposed to a missile, these types of systems can reattack if they miss.
Figure 3-3: Kamikaze Drone Example

Source: (Dormehl, 2019)
This capability is a function of the target drone speed. Another proven method is the use of a predatory bird to attack and potentially capture the drone. Though proven effective, this method requires a high level of maintenance.
Medium Drones
The medium drone classification is mostly made up of military drones designed for surveillance. The world market is seeing more and more kamikaze type drones entering the medium-sized classification. Iran has placed significant emphasis in this area and has a variety of direct attack drones.
Some of the same counter techniques used for small drones are also effective on medium drones. RF jamming, for example, can be effective, albeit with some limitations. Medium drones generally require more RF jamming power and across a variety of frequency bands. However, once in the target area, they may no longer need external control from a ground station. These drones can proceed to the target coordinates on their own. If the attack drone requires GPS/GLONASS, this can be jammed to limit precision, but the drone will land somewhere.
A more direct counteraction is required to be effective against this class of drones to include the use of missiles, bullets, and lasers. The type of missile to be used is dependent on the size of the offending drone and its signature. Generally, medium-sized drones have a very small infrared signature, which makes it difficult to deploy IR missiles as a countermeasure. This category of drones also has a limited radar signature. Radar guided missiles are most effective when they have their own terminal radar and can be guided by a more powerful ground radar data uplink. Surface-launched AMRAAM (SLAMRAAM) is an example of this type of weapon. The SLAMRAAM is no longer used by the U.S. military due to priority changes; however, there are indications that other countries will employ these weapons in a C-UAS scenario. An effective weapon is a laser-guided missile that does not have the signature limitation that the other missiles do, and it has a very limited countermeasure set to work against.
Bullets tend to be a last line of defense due to their limited range. There are two techniques that can be effective. First is the hail of bullets typically from a Gatling gun type system. The second is from a rapid-fire cannon that has bullets that fragment just before hitting the drone. There are 25mm bullets that fit into this desired capability. As a point of consideration, as the area to be defended increases, so does the required number of gun sites and ammunition needs.
High-Powered Microwave (HPM) systems directly attack the electronics onboard the drone. Depending on the power and range, the system disrupts the data links, and eventually, the actual circuitry as the power increases, and the range decreases. These systems can be indiscriminate, so a focused system and a clear background are important. See Figure 3-4.
Lasers, because of their price tag, are normally limited to military applications. These systems are getting more and more powerful and, therefore, more effective and capable of engaging at longer ranges. These systems target a vulnerable flight control on the drone. See Figure 3-5.
Large Drones
This classification includes both commercial and military drones; however, it is the military drones that represent the threat. [ Figures 3-6 and 3-7] These military drones range from slower, higher altitude, surveillance drones (some with weapon capabilities) to stealthy fighter-type drones. The latter of these two is more dangerous and more difficult to eliminate.
Figure 3-4 High Powered Microwave System

Source: (Trevithick, 2019)
Figure 3-5: Laser Sensor Ball

Source: (spazio-news.it, 2019)
The flight control is damaged, which then sends the drone out of control and to an eventual crash. There are now several versions of laser weapons available.
Manned attack aircraft are also included in this response category, especially for cruise missile type systems. For attack drones that fly under 200 knots, a propeller-driven light attack aircraft with an onboard gun system is sufficient. Once the speed rises about 200 knots, a jet-powered fighter-type aircraft is required. While missiles and guns are available, generally, the most effective choice is the gun for single drone engagements. In a situation where there are several attacking high-speed drones, the fighter aircraft will be required to use its missiles and follow up with guns or missiles on the ones that survive the initial response.
Some of the defenses for medium-sized drones carry over into the large drones. Defensive systems designed for attacking manned aircraft become prominent in this large drone category.
Figure 3-6: Iranian Drone

Source: (Singh, 2019)
Figure 3-7: Chinese Drones on Parade

Source: (George, 2019)
Jamming systems, though somewhat effective on some drones in this category, generally fall off as a primary defense system because the satellite uplink can be jammed. Jamming the uplink is a typical point defense solution unless it is space-based or has an included airborne relay. Bullets can no longer be used as a primary point defense system due to their short range and limited altitude coverage.
High-end missile systems, such as the US Patriot system, can be brought to bear for these type threats. Typically, missile systems are an early choice because they are already in the military inventory. For wealthy countries, the poor cost exchange of using expensive missiles against often less expensive UAS is not much of a factor. The potential cost of damage from an enemy UAS often outweighs the cost of the missile. Interdiction success is the primary metric. Stealthy drones are the most challenging, but acquisition ranges, though shorter, are typically sufficient for a successful engagement. The most significant limitation of this drone response is the amount of area that is being protected is relatively small.
Directed energy weapons, though of limited use against manned aircraft, are becoming a weapon of choice for larger drones. Directed energy weapons include high powered microwaves and lasers, which are considered point defense systems. If the attack corridors are known and limited, then these types of systems can be set up like a picket fence formation to protect a much larger area and engage threats much earlier. Of the two, the high-powered microwave systems tend to be more effective due to the short engagement time required. Lasers often must dwell on the target for several seconds to be effective. Against the slower end of the large drone category, lasers can be extremely effective. Faster aircraft are more problematic for current lasers, but as the lasers become more powerful, the dwell time required will go down, and this type of weapon system will be effective against the fast-moving UAS in this category.
Manned aircraft become a primary part of the defense to protect larger areas and engage the threat much earlier. Large drones, including the stealthy ones, can be easily terminated by a fighter jet as these drones have no self-awareness and have limited maneuverability. Since these drones usually have no weapons to fight back, they can be attacked and re-attacked with impunity. Fighter pilots quickly become drone aces. The most challenging scenario is a swarm of stealthy attack drones. Fighter squadrons must determine if there are enough missiles and gun rounds to take out all of the attacking drones before the drones reach their intended targets (U.S. Air Force Major Jay Snyder, 2019).
Case Study
The case study below reviews the swarm drone attack in Saudi Arabia on the morning of September 14, 2019. Although the event is real and well documented, the analysis, limitations, and solutions are fictional and designed to demonstrate the C-UAS analysis framework.
Background:
On the morning of September 14, 2019, two state-owned Saudi Arabian oil production sites were attacked. The Abqaiq and Khuraid oil fields are the largest oil production facilities in the world. These two plants account for almost 8% of the world’s oil supply (bbc, 2019). The attacks were conducted using drones and cruise missiles from an unknown origin. “According to the Saudi Defense Ministry, eighteen drones and seven cruise missiles were fired at the kingdom” (Frantzman, 2019). Defense News stated, “If ever the world needed a reality check for the threat posed by drone swarms and low-altitude cruise missiles, this was it” (Frantzman, 2019).
The news reports differ as to the specific number and types of drones and missiles used in the attack. Four missiles did hit their intended oil field targets; however, it is unclear how many did not complete the mission. (Frantzman, 2019). This was a major escalation in UAS attacks given the type and number of utilized drones. There also continues to be speculation as to the geographical origins of the attack. Previous drone attacks had come from Yemen and were limited in size, scope, and range. It is widely believed by Saudi Arabia and the United States that Iran was the source; however, Iran has not claimed credit for this attack.
What is remarkable is that despite the heavy defenses of the Abqaiq oil field, none of the systems or technologies thwarted the attack. The facility is believed to have air defenses that include an American Patriot system, a Swiss-made 35 mm anti-aircraft Oerlikon cannon in conjunction with a Skyguard radar, and a French-designed Shahine, which is a surface to air missile system. (Frantzman, 2019). The Patriot missile defense system is the only component specifically designed to defend against UAVs. It is highly possible that the drones were guided using on-board sensors and not GPS programmed, which, given the infrastructure of an oil processing facility, was quite advantageous.
If US-supplied air defenses were not oriented to defend against an attack from Iran, that’s incomprehensible. If they were, but they were not engaged, that’s incompetent. If they simply weren’t up to the task of preventing such precision attacks, that’s concerning, said Daniel Shapiro, a former U.S. Ambassador to Israel. (DM, 2019).
Brig. Gen. Pini Yungman believes that the “primary challenge in stopping an attack like that in Saudi Arabia is not the ability to shoot down the threats, but rather to detect things that can sneak in near the ground” (DM, 2019).
Creating a Solution
Analyzing the Threat:
In this case study, the threat determination is more speculative than defined. Iran denied launching the attack, but the weapon systems were most definitely Iranian in design and possibly in manufacturing. The origin of the drones was determined by these same drones being previously used against Saudi Arabia and the recovered wreckage. There is some speculation that one type of drone was used against the Patriot defense system, while the second type of UAS was used against the oil facility, based on the wreckage from numerous sites. The recovered delta-winged drone was determined to be most likely from a Toofan Iranian drone or a similar design class with a greater range.
Toofan Drone
The Toofan drones are a series of drones developed and used by Iran specifically for suicide missions. Iran does not publish information about the drones it builds and designs. The Toofan drone is considered small and is known to be very fast – up to 250km/hr. One of the advantages is its’ undetectable launch. All of these features make it difficult for an effective C-UAS response. See Figure 3-8.
Figure 3-8: Toofan Drone

Source: (“Iran Suicide Drones,” 2019)
Industry analysts who have seen the Toofan describe it having a small radar cross-section and appearing to be made with lightweight radar-absorbing materials and guided by cutting edge avionics. It can fly for over one hour. There is also a front-facing camera in the nosecone which transmits live images until the moment of impact. All of these characteristics make the Toofan a very effective suicide drone (memri, 2019).
Although the Toofan has a small radar signature, the estimated speed of approximately 135 knots places it in the detectable range. The other possible drone used in the attack was most likely a Yemeni Houthi militia Quds-1 cruise missile (memri, 2019).
Possible Cruise Missiles
Cruise missiles are slower than traditional missiles, fly at lower altitudes, and are small – all radar-evading advantages. Another advantage is that cruise missiles are typically lower in price than other types of missiles. (armscontrolcenter, 2017) Cruise missiles can be launched from almost any location: by land, from the air, or an ocean vessel (armscontrolcenter, 2017). These types of missiles can have multiple guidance systems depending upon the design. The missiles can be completely pre-programmed for GPS flight or can be guided by an operator using a forward-positioned camera.
Quds-1 Missile
Initially thought to be designed in Yemen by the Houthi, the Quds-1 cruise missile is powered by a Czech built turbojet engine. See Figure 3-9. However, based on an Iranian industry analyst, the Qud-1 might have been developed and designed in Iraq (armscontrolcenter, 2017). The Iranians have been developing several different types of missiles for the past few decades. The Quds-1 is smaller than the Soumar and Hoveyzeh missiles and has less thrust than the Ya Ali missile. (armscontrolcenter, 2017). The Quds-1 appears to be primarily made out of metal, based on the wreckage. The signature is likely small but in line with other cruise missile signatures (Hinz, 2019).
Figure 3-9: Quds-1 Cruise Missile

Source: (Hinz, 2019)
Potential DIANA Missile Usage
Since little is known about the Quds-1 cruise missile besides the suspected range of 425 miles, the DIANA target cruise missile can be used as a surrogate for analysis since it has the same engine and is approximately the same size (Hinz, 2019). This gives the Quds-1 a suspected speed of 330-350 knots. Manufactured by Equipaer Industria Aeronautica, the DIANA has a flight altitude variance of 10m – 8,000m and is designed for high speed / high maneuverability. It is advertised to have a maximum speed of 380 mph (equipaer, 2011).
Tactical Analysis:
The oil facility attack demonstrated a precise and sophisticated attack utilizing multiple drones with different attack profiles to multiple locations within a small amount of time. It is suspected that multiple Toofan drones first attacked the Patriot radar, followed by additional Toofan drones and Quds-1 cruise missiles attacking the oil facilities. The Toofan’s optical final guidance could have been employed. That would mean the human controller(s) would have to be part of the attack. The Quds-1 most likely uses an IMU and GPS for guidance (Hinz, 2019). This is consistent with what is known about their anti-ship cruise missiles. The attackers used low-cost attack vehicles specifically designed to evade radar. The attackers knew the specific locations for the radar defenses and the overall defenses of both facilities. Additionally, the attackers used a combination of manned and unmanned systems – but no human support was physically located at either oil field.
Solution Limitations:
In this scenario, the use of the Patriot radar and patriot missile response, coupled with little intelligence against an unknown number of targets, limited the effectiveness of the system. It has been reported that the guards at the facility attempted to use their rifles and handguns to defend the installation (DM, 2019).
Preservation of Existing Infrastructure
Saudi Arabia’s oil fields have high value and are in a protected area, which is relatively remote; there are fewer limitations on the potential solution. As this is an industrial site, the solution needs to consider minimal damage to the physical facilities as well as the electronic and communication systems of the facility infrastructure. Returning to the concept of not incurring damage to the physical facilities, mitigation plans need to be developed if friendly or threatening drones are destroyed over the oil fields. There should be special care taken to consider any combustible materials.
Governance
Additionally, military and commercial air traffic need to be accounted for in the plan. If GPS/GLONASS jamming is to be part of the solution, it needs to be coordinated and approved by the Saudi government. The oil fields are owned by the Saudi government; this fact should assist in any governance being written, altered or waivered to protect this critical infrastructure.
Atmospheric Limitations
Several atmospheric limitations exist in the Middle East Region. The weather in Saudi Arabia is normally sunny with mixed or no cloud cover, and the week of September 8 – 14, 2019, the weather in this region averages from 80 – 107 degrees Fahrenheit. The days are coolest just before midnight until approximately 7 am. During September, the dew point average is 6 %. Abqaiq skies experience cloud cover between 7-29 % of the time for this month (weatherspark.com, 2019). In this region, there are sand storms, heatwaves and even fog in the air near the ground. These conditions don’t preclude laser solutions, but it does have an impact on them. Consideration should be made to elevating the laser above the ground if it is part of the system, possibly in a guard tower or in an airborne platform. The topography is considered to have modest variations with a 1,270 ft variation for a 50-mile radius.
A Multi-Layered Counter Drone Response Plan
The multiple drones used in the Saudi oil field attacks are considered medium drones; therefore, the solution should consider all appropriately sized and quantity countermeasures. The countermeasure response should account for multiple drones attacking at once; more than one type of drone; with one drone being relatively high speed; and a sprawling soft infrastructure to be protected; all lead to more than one layer of defense and that the first engagement should far enough away to allow for an assessment and engagement of leakers before they can reach the facility. As the first layer of defense is extended out, the larger the engagement arc distance grows.
For this case study, the first layer should be about 25 miles out from the protected area. This perimeter allows for advancing targets and receding targets, as well as enough time to coordinate the second layer response. The proximity of the coastline is a factor in the system placement. The expanse of the perimeter precludes the use of shorter-range systems because of the number of sites required. Bullets, lasers, and high-powered microwaves concede to missile-based solutions at this range. Ground-based missile systems are a more practical choice for protection than aircraft-based missile systems. The cost of the aircraft and pilot patrolling the airspace becomes astronomical for an irregular threat.
The range for the point defense second layer needs to be far enough out to interdict the drone and not have it come down within the facility boundaries; while at the same time not creating an arc distance that is too big not to be cost-effective. In this case that range would be approximately 5 miles to account for the cruise missile type attack drone. With the shorter coverage zone, the variety of shorter-range systems can be considered.
Detection
Detection is one of the more challenging portions of the solution. At least one of the threat drones is a low altitude ingress type drone, and therefore the detection system needs to be elevated. The Quds-1 is unlikely to be transmitting any signal for an ESM type system. The Toofan may or may not be transmitting. The interdiction system selected needs a precise location for weapon guidance, and since sensors in the light spectrum have too short of a range for this protection ring, the best choice is a radar type system.
The next decision is the type of elevation method. Is the radar system on a tethered balloon or an extendable arm or a fixed tower? Due to the risk of sand storms, a tethered balloon is not the best solution. For maintenance reasons and sand storm considerations, the extendable arm is preferable over the fixed tower. Although stationed on the outer perimeter, the radar needs to be effective across the entire facility.
Interdiction
Interdiction is best done when layering defense technologies, methodologies, and systems. Numerous scenarios need to be considered when designing an effective counter-drone defense solution. Combination systems can be more effective, especially when defending against different types of drones. As an example, the Toofan type drone is more susceptible to a directed energy weapon, whereas the Quds-1 cruise missile is more susceptible to a hard kill. Each layer should have overlapping interdiction systems to preclude multiple attack drones attempting to overwhelm a single sector. Additionally, if ground missiles are part of the overall solution, then, the number of ground stations, missiles and support personnel need to be considered as part of cost and maintenance.
Graphical representation of the anticipated engagement envelope can be particularly useful when determining point positioning. Most engagement envelopes are not a circle; effective engagement zones look much more egg-shaped. The narrow end is drawn for the receding targets and the wide end for the advancing targets. The faster the incoming target, the more the egg shifts such that the receding target zone gets smaller. The faster the intercepting missile, the larger the egg gets, and the greater the receding target capability (Snyder, 2019).
Integration
When dealing with a variety of interdiction methods, the system needs to be evaluated so that no one part of the system conflicts with any other part of the system. It would be counterproductive to have a communications system that is susceptible to the jamming solution. If an HPM is being integrated, it should be analyzed to make sure it will not damage other system components. Additionally, shots fired at receding targets should not cause collateral damage to the property being protected. All components should be tested with every other component to validate that all components work harmoniously together and do not harm the home facility (U.S. Air Force Major Jay Snyder, 2019)
The Chosen Solution:
Figure 3-10 shows a SAAB Giraffe AMB Radar. The Giraffe is a 3D detection system that can detect small, low, and slow targets as well as aircraft, cruise missiles, rockets, artillery, etc. The radar is on an extendable arm to increase the detection range of low-level targets.
Outer Layer
Figure 3-10: SAAB Giraffe AMB Radar

Source: (Saabgroup, 2018)
The radar system operates out to approximately 65 nautical miles. The small signature of the Toofan drone reduces the maximum detection and tracking range of the system. SAAB demonstrated detection and tracking of a small drone with a signature of .001 square meters at a range of 4 km. (SAAB, 2019)
Extrapolating this information to the Toofan (using the Harpy drone as a surrogate) delivers an approximate detection and tracking range of 25 km. By placing the radars approximately 40 km apart, there is good detection range throughout the arc with small notches. See Figure 3-11. (US Army, 2019)
Figure 3-11: Toofan Detection System

Source: (US Army, 2019)
Interdiction is provided by a ground-launched version of the AMRAAM-ER missile. It comes in a six-box configuration that can be ground or vehicle-mounted. This is called NASAMS II (National Advanced Surface to Air Missile System). The AMRAAM-ER is a Mach 4 missile with an approximate range of 27 nautical miles (50 km). (globalsecurity.org, 2019) The missile launch systems will also be 24 miles (40 km) apart to provide dual coverage to the arc. Twelve missiles per site deliver the capability to shoot down up to 24 drones in any given sector before requiring a reload (US Army, 2019) Based on the potential threat approach directions, an initial arc of 270 degrees will be used for the outer layer. The arc can be reduced or increased depending on enemy tactics.
The StarStreak II is a Mach 4 class missile system is designed for a kinetic kill with a range of approximately four nautical miles. It employs three tungsten darts that are laser-guided and immune to all known countermeasures (Sparks, 2017). See Figure 3-12.
Inner Layer
Figure 3-12: Stark-Streak II Missile System

Source: (Sparks, 2017)
This permits the engagement of targets with extremely small signatures. (Minister, 2008) To complement this system for the inner layer is a High-Powered Microwave (HPM) system designed to fry the internal electronics of the attacking drone.
The system will be deployed on a fixed turret with an 8-missile configuration. The turrets will be remote-controlled from the Command Center. They will be deployed at six nautical mile increments around the inner 5-mile ring. This provides continuous and overlapping coverage. The typical concept of operations would use a shoot-look-shoot methodology. The concept of operations is facilitated by the speed of the missile. The StarStreak II is a very versatile weapon system and is capable of handling inner layer defense against a large variety of medium and large drones.
To complement the StarStreak system for the inner layer is a High-Powered Microwave (HPM) system designed to destroy the internal electronics of the attacking drone. There are two viable systems for this particular solution: Boeing’s Thor and BAE Systems’ HPM. See Figure 3-13.
Figure 3-13 Example of a High Powered Microwave System
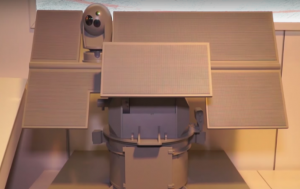
Source: (Vavasseur, 2019)
Since this will be a component of the inner layer of defense, the BAE Systems’ HPM is a logical
choice. The Boeing system is overkill for the inner layer due to its size and power output (Vavasseur, 2019)
BAE Systems HPM is “Scalable and designed for use on all sizes of surface combatants[.] HPM instantaneously defeats a wide range of air and surface threats at tactically significant ranges (such as UAV, Aircraft, Helicopters, USV, Fast Attack Craft…)” (Systems, 2018) A High-Powered Microwave System was chosen to prevent the overall system and especially the inner layer from being overwhelmed with the number of simultaneous attacking drones. The HPM type of defense system also permits the overall system to defend against swarming small drones if or when those also become part of the threat matrix. The HPM system will be deployed on a six-mile arc, halfway between the StarStreak systems. This slightly more forward deployment is to prevent possible interference with the StarStreak systems (Vavasseur, 2019).
Command and Control
The more complex the system and the more layers involved, the more integrated the command and control system must be. Sensors, weapons, and communications need to be integrated and robust. Threat or no threat determinations need to be made in a quick and efficient manner to include an appropriate method of engagement. The number of personnel to accomplish this can be reduced by an expert or an AI system (U.S. Air Force Major Jay Snyder, 2019).
For this case study solution, all of the detection and interdiction components will be commercial off the shelf components to create the final comprehensive, integrated command and control center. Although many of these components have been integrated in the past, they have not been integrated with the inner layer systems. To minimize labor hours required and to maximize effectiveness, Artificial Intelligence (AI) will be leveraged as much as possible into the solution. When integrating a system of systems, it is always best to involve a major system vendor in that integration. There are several defense contractors who excel at complex integration, testing, and receiving government authorization for the final solution. Creating a new command and control system will most likely involve multiple vendors including one like the ARES Corporation to work with the lead integrator (Snyder, 2019). The ARES’ mantra is “Protecting the world’s most critical assets” (ARES Security, 2019).
ARES AVERT C2 product, as seen in Figure 3-15, creates a singular scalable interface that integrates partners’ command and control portal. The company touts the configurability of the system to adapt to multiple situational awareness and incident response needs utilizing role-based security. The proprietary system can link unique network systems, sensors, with unique customizable client requirements collaborative response. (ARES Security, 2019) See Figure 3-14.
Figure 3-14: Sample Image of an AVERT C2 System

Source: (Vavasseur, 2019)
As this is a static design, the primary communications solution should be fiber optic cabling. The hard-wired cable provides a stable, consistent communication platform and avoids possible interference problems with the radars and HPM systems and can be secured. Wi-Fi or satellite links could be jammed, cause interference, receive interference, or have intermittent to poor performance (Snyder, 2019). Figure 3-15 is a composite of the overall solution coverage.
Figure 3-15: Case Study C-UAS Solution Diagram
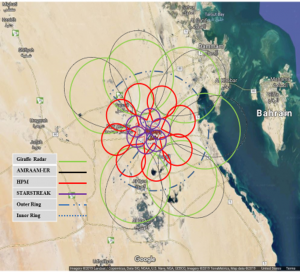
Source: (U.S. Air Force Major Jay Snyder, 2019)
Conclusions
This chapter has examined some of the challenges and thought processes required to build a C-UAS framework for a given area. Developing a solution requires a multi-step process to avoid potential pitfalls and achieve a very high degree of success. Analyzing the threat or threats is the first step in the process. This process could involve something as easy as a quadcopter delivering contraband into a prison yard or as hard as cruise missiles and attack drones with the added challenge of having limited intelligence data available. The drone’s mission and potential level of weaponization will determine the appropriate C-UAS response. The number of attacking drones will also govern the complexity of the overall solution.
Before contemplating a counter-drone solution, careful consideration needs to take place regarding the limitations to the possible solution set. Some limitations are physical, such as the weather, but some limitations could create legal issues, including jail time. Those limitations are set by the government of the respective country. Working with a government agency or requesting a waiver may be the only path to a successful counter-drone system.
As a counter-drone system is developed: range, detection, and interdiction will be the supporting foundation. At what distance does the drone need to be detected, and at what distance does the drone need to be engaged or interdicted? As these distances and perimeters increase, so does the need for a line-of-sight limitation solution. More than one layer or ring may be needed. Passive detection systems are fantastic if the drone and possibly the ground station are emitting RF signals. However, if the attacking drones are radio silent, then a radar type system will likely be necessary. Interdiction choices are often driven by the size of the drone and whether it is carrying weapons that can be released. As the size increases, the interdiction methods move from a soft interdiction using jammers, nets, etc. to more traditional weapons for aircraft that include bullets and missiles. As the number of attacking drones increase, the interdiction method moves from kinetic attacks to the non-kinetic realm of directed energy such as lasers and high-powered microwaves.
Do not forget the limitations and requirements for command and control in the overall solution. The command and control solution may be extremely simple and potentially designed for a variety of commercial drones. As the threat grows and the number of defense layers grows, so too does the complexity of the command and control system. The necessary level of complexity may require an expert software solution embedded with artificial intelligence to help guide the attack and response phases. C-UAS will continue to change and adapt as the technology improves, and the drone/counter-drone issues are more constrained by human innovation than the science that empowers the machines.
Questions
- Name three factors that must be taken into consideration when building the framework for C-
UAS? - What are the limitations of a C-UAS solution?
- Can C-UAS be countered? If yes, how?
- Why would a non-kinetic kill be chosen over a kinetic kill in C-UAS around populated areas?
References
130i., U. C. (2019). U.S. Code § 130i.Protection of Certain Facilities and Assets From Unmanned Aircraft. Retrieved from www.law.cornell.edu/uscode: https://www.law.cornell.edu/uscode/text/10/130i
ARES Security. (2019). ARES Security. Retrieved from aressecuritycorp.com: https://aressecuritycorp.com/#home1
armscontrolcenter. (2017). Fact Sheet: Ballistic vs. Cruise Missiles. Retrieved from armscontrolcenter.org: https://armscontrolcenter.org/fact-sheet-ballistic-vs-cruise-missiles/
BBC. (2016). Police drone can be hacked with $40 kit says researcher using XBEE. Retrieved from BBC.com: www.bbc.com/news/technology-35709676
bbc. (2019). Saudi Arabia oil facilities ablaze after drone strikes. Retrieved from www.bbc.com/news: https://www.bbc.com/news/world-middle-east-49699429
Biesecke, C. (2011). CBP Continues To Explore Small UAS Options. Defense Daily, 249(16), 2-2. Retrieved from Biesecker, C. (2011). CBP Continues To Explore Small UAS Options. Defense Daily, 249(16), 2-2. : Biesecker, C. (2011). CBP Continues To Explore Small UAS Options. Defense Daily, 249(16), 2-2.
- Horowitz, K. S. (2016). Separating Fact from Fiction in the Debate over Drone Proliferation. International Security, 41(2), 7-42. doi:10.1162/ISEC_a_00257.
Commission-Licensing, F. C. (2019). Federal Communications Commission-Licensing. Retrieved from www.fcc.gov/licensing-databases/licensing: https://www.fcc.gov/licensing-databases/licensing
Congress Bills. (2018, May 14). Retrieved from Protection of certain facilities and assets from unmanned aircraft: https://www.congress.gov/115/bills/s2836/BILLS-115s2836is.xml
DM, C. (2019, October). Can anything stop attack drones? . Retrieved from www.asiatimes.com: https://www.asiatimes.com/2019/10/article/the-rise-of-stealth-combat-drones/
Dormehl, L. (2019). DroneBullet is a kamikaze drone missile that knocks enemy UAVs out of the sky. . Retrieved from www.digitaltrends.com: Dormehl, L. (2019). DroneBullet is a kamikaze drone mihttps://www.digitaltrends.com/cool-tech/dronebullet-anti-drone-tech/
Edward Teets, J. D. (1998). Atmospheric considerations for uninhabited aerial vehicle (UAV) flight test planning. In 36th AIAA Aerospace Sciences Meeting and Exhibit. Washington: AIAA.
equipaer. (2011). DIANA: Aerial Target Drone. Retrieved from www.equipaer.com: http://www.equipaer.com/diana.php
FCC. (2014, December 8). Enforcement Advisory No. 2014-05. Retrieved from https://transition.fcc.gov/eb/Public_Notices/DA-14-1785A1.html
FCC. (2019, November 19). Jammer Enforcement. Retrieved from Jammer Enforcement FCC: https://www.fcc.gov/general/jammer-enforcement
Frantzman, S. J. (2019, September 26). Are air defense systems ready to confront drone swarms? Retrieved from www.defensenews.com/global/mideast-africa: https://www.defensenews.com/global/mideast-africa/2019/09/26/are-air-defense-systems-ready-to-confront-drone-swarms/
George, S. G. (2019). China shows off new stealth drones. Retrieved from https://www.cnn.com/asia/live-news: https://www.cnn.com/asia/live-news/china-hong-kong-oct-1-live-intl-hnk/h_1ba984e1cf9a99769648fe35eb06cec5
globalsecurity.org. (2019). AMRAAM-Extended Range – AMRAAM-ER. Retrieved from www.globalsecurity.org: https://www.globalsecurity.org/military/systems/munitions/aim-120-er.htm
Hinz, F. (2019). Meet The QUDS 1. Retrieved from www.armscontrolwonk.com: https://www.armscontrolwonk.com/archive/1208062/meet-the-quds-1/
İ, G. O. (2017). Detection, localization, and tracking of unauthorized UAS and Jammers. 2017 IEEE/AIAA 36th Digital Avionics Systems Conference (DASC). Washington: DASC.
memri. (2019). Iran Presents its Suicide Drones. Retrieved from /www.memri.org: https://www.memri.org/reports/iran-presents-its-suicide-drones
Military-history-now. (2015, February 6). Buzz Kill – 13 Remarkable Facts about the V-1 Flying Bomb. Retrieved from Militaryhistorynow.com: https://militaryhistorynow.com/2015/02/06/buzz-kill-15-amazing-facts-about-the-v-1-flying-bomb/
Minister, M. (2008). MoD Minister Announces Missile Support Contract Win to Thales in Belfast. Retrieved from www.copybook.com: https://www.copybook.com/companies/thales-uk/articles/missile-support-contract
Openworksengineering. (2019). Sky Wall Patrol. Retrieved from openworksengineering.com: https://openworksengineering.com/skywall-patrol/
SAAB. (2019). Giraffe Elss Uav Detection and Tracking. Stockholm, Sweden: SAAB.
Saabgroup. (2018, June 1). United Kingdom Becomes Largest Operator of Saab Land-based Giraffe AMB Radars. Retrieved from saabgroup.com: https://saabgroup.com/media/news-press/news/2018-06/united-kingdom-becomes-largest-operator-of-saab-land-based-giraffe-amb-radars/
Singh, S. (2019). How military drones are becoming deadly weapons across the globe . Retrieved from economictimes.indiatimes.com/news/defence: https://economictimes.indiatimes.com/news/defence/how-military-drones-are-becoming-deadly-weapons-across-the-globe/articleshow/71236124.cms
Snyder, J. (2019). Engineering Solutions for Countering Autonomous Systems. Arlington, VA: Mongo 1, LLC.
Sparks, M. (2017). Starstreak Multi-role Missile- not just a SAM. Retrieved from www.angelfire.com: http://www.angelfire.com/art/enchanter/starstreak.html
spazio-news.it. (2019). Raytheon Delivers First Laser Counter-UAS to US Air Force. Retrieved from spazio-news.it: Retrieved from http://spazio-news.it/raytheon-delivers-first-laser-counter-uas-to-us-air-force
Systems, B. (2018). SNA 2018: BAE Systems Unveils High Powered Microwave. Retrieved from www.navyrecognition.com: www.navyrecognition.com/index.php/news/naval-exhibitions/2018/sna-2018/5854-sna-2018-bae-systems-unveils-high-powered-microwave.html
Trevithick, J. (2019). Air Force Set To Deploy Its Counter-Drone “Phaser” Microwave Weapon Overseas. Retrieved from www.thedrive.com: https://www.thedrive.com/the-war-zone/29992/air-force-set-to-field-test-its-counter-drone-phaser-microwave-weapon-overseas-in-2020
U.S. Air Force Major Jay Snyder, R. (2019, October 30). Counter Drone Tactics, Techniques and Procedures. (L. L. H. C. Mumm. Victory Systems, Interviewer)
UNOOSA. (2019). Global Navigation Satellite Systems (GNSS). Retrieved from www.unoosa.org: https://www.unoosa.org/oosa/en/ourwork/psa/gnss/gnss.html
US Army. (2019). NASAMS Norwegian Advanced Surface to Air Missile System. Retrieved from www.armyrecognition.com: https://www.armyrecognition.com/norway_norwegian_army_missile_systems_vehicles_uk/nasams_norwegian_advanced_surface_to_air_missile_system_technical_data_sheet_pictures_video_1
Vavasseur, X. (2019, January 1). Video: BAE Systems High Powered Microwave at SNA 2019. Retrieved from www.navalnews.com: https://www.navalnews.com/event-news/sna-2019/2019/01/video-bae-systems-high-powered-microwave-at-sna-2019/
weatherspark.com. (2019). Average Weather in September in Abqaiq Saudi Arabia. Retrieved from weatherspark.com: https://weatherspark.com/m/104790/9/Average-Weather-in-September-in-Abqaiq-Saudi-Arabia#Sections-Precipitation

