14 Chapter 14 Maritime Cybersecurity [Nichols]
Student Objectives
Students will revisit the South China Sea and Chinese Threats to USN and Commercial vessels in the area.
Students will grasp the size and cybersecurity issues for the Maritime Transportation Sector (MTS)
Students will understand the nuances of Cyber-Physical systems, Operational technology, and the Internet of Things (IoT).
Introduction
I would like to dedicate this bonus chapter to Dr Gary C Kessler and Steven D. Shepard on their 2020 release of a fascinating book on Maritime Cybersecurity: A Guide for Leaders and Managers. (Kessler, 2020). I respect and agree with everything their many years of experience have witnessed and put into writing on the subject except strategies for maritime cyberdefense in which the authors mistake the priorities of Vulnerabilities over real Threats. The author has liberally cited this excellent work. We can do something about Threats – applying appropriate countermeasures to reduce risk. Vulnerabilities are a constant and represent an existing weakness in the information system that will always be present, will generally increase even after a computer security audit, or patch(es), and may or may not be a conduit for a real Threat to attack an information system. The security goal is to identify Vulnerabilities and to reduce Threats.
Our views are different. The author is a captain of a cruising yacht with 40 plus years as previous owner / master of five different medium – size sail and power boats. Every effort was made to maximize / duplicate the security of electronics, navigation systems, powertrain, fire suppression, pumping, SOLAS, anchoring, weather, piloting, RADAR, AIS, SONAR, seamanship, and passenger safety on my marine craft. My charges were USCGA approved / inspected every two years. It took nearly 20 years to become a decent captain. The author made every mistake that was on some novice list of “don’ts” on the water. But that is called experience. My career has been in cybersecurity and INFOSEC. Multiple systems on my craft were computer aided including AIS, RADAR plots, navigation, USCG soundings / charts, ATN, buoys, weight distribution / loading, emergency systems, power, bilge, satellite phone, EPIRB, entertainment, three VHS radios, previously LORAN-C, and remote communications. Threats to these coordinating computer – information systems were serious and might have denied me port entry if they were not adequately protected. [1]
The author’s point is that qualitative information system Risk is ~ f(Threats / Countermeasures). This is true because Vulnerabilities and Impact are essentially constants that drop out of the strategic consideration for planning for cyberdefense. Increase the Threat vector and we directly increase the risk. Increase applied Countermeasures and Risk is reduced. These can be calculated as qualitative levels of risk or translated into worst, best and normal case scenarios for comparison of incremental changes to either dependent variable.
This chapter will not debate the (Kessler, 2020) notions of Risk Vs Vulnerabilities Vs Threats. There are some valid points, charts, procedures presented in his final chapters. (Kessler, 2020) Instead, Chapter 14 will revisit the authors research on the spoofing of navigation systems on vessels in the South China Seas. This will be followed by a section on the MTS and potential cybersecurity vectors and end with a section focused on the holy grail of IoT as related to the maritime sector.
The Case for Cyber Weapon Spoofing of Legacy GPS Signals Affecting US Navy and Commercial Vessels in Pacific
In (Nichols R. K., et al., 2019), the author presented a detailed case for GPS spoofing by Chinese assets of US Navy and Commercial Vessels in South China Seas. It is summarized here as a starting point for a condensed discussion on maritime security.[2]
U.S Navy Vessel Collisions in the Pacific
In 2017 there was a chain of incidents/collisions involving four U.S. Navy warships and one U.S. Navy submarine. On 17 June, the destroyer USS Fitzgerald collided with the ACX, a 30,000-ton container ship resulting in seven dead. Records show that the ACX turned sharply starboard (right) at the time of collision. The captain of the Philippine-flagged container ship accused the Navy destroyer of failing to heed warning signs before the crash. Those warning signs came from the commercial vessels Automated Collision Systems (AIS) on the bridge. On 9 May, the guided-missile cruiser USS Lake Champlain collided with a South Korean fishing boat off the Korean Peninsula. There were no injuries (Department of the US Navy, Office of Chief of Naval Operations, 2017). On 31 January, the guided-missile cruiser USS Antietam ran aground dumping more than 1000 gallons of oil into Tokyo Bay. On 18 August, the ballistic-missile submarine USS Louisiana collided with the Navy Offshore Support Vessel in the Strait of Juan de Fuca. There were no injuries. “On 20 August, the guided-missile destroyer USS John S McCain collided with the 600-foot oil and chemical tanker Alnic MC at 0624 JST resulting in ten dead (Navy Information Office , 2017)”. (Weise, 2017)
Navy Response
In all five incidents, the U.S. Navy blames their field leadership for not responding in an appropriate manner. This response means that the Skipper / XO / COB and at least five (5) watch sailors on each Naval vessel (roughly 40 – 50 personnel including bridge staff plus 130 lookouts on the USS McCain because of ordered watch conditions) have been judged incompetent (Navy Information Office , 2017). Their careers are over, and some will face courts martial and possible brig time. This response also implies that all five Navy vessels’ radar, emergency positioning alert systems, AIS, sonar, and long-range collision avoidance equipment must have been functioning perfectly, without a catastrophic failure or interference of any kind. This conclusion assumes that none of the ships were in difficult maneuverable waters or serious traffic. The Navy blames funding, readiness, and training. However, their response may not fully account for the commercial vessel accident data, actions required, o GPS positional data received (Olson, August 30, 2017). (Nichols, et al., Unmanned Aircraft Systems (UAS) in Cyber Domain: Protecting USA’s Advanced Air Assets, 2nd Edition, 2019)
The Navy Official Reaction regarding the possibility of Cyber-Weapon or Cyber-Attack
The Navy has downplayed the possibility of a Cyber Weapon or Cyber Attack. Prior Chief of Naval Operations (CNO) Admiral John Richardson said in a tweet on Monday 23 August, referring to the USS McCain and USS Fitzgerald collisions, “there was no indication of the possibility of cyber intrusion or sabotage was involved or that the Navy ships were hacked, but the review will consider all possibilities.” (Weise, 2017) The Navy investigators after inspecting the physical damage to the USS McCain and USS Fitzgerald agree with the CNO’s conclusions (Olson, August 30,2017).
“Navy experts in the technology and researchers at University of Texas at Austin say there are certainly scenarios they can imagine in which GPS hacks could have been used to foil ships’ navigations systems but emphasize there’s no evidence such attacks took place in the case of the Navy collisions.” (Weise, 2017) “The technology to jam or misdirect navigational software is readily available, though the Navy uses a much more robust encrypted version of GPS that would be very difficult to disrupt.” (Weise, 2017)
The only way to spoof such a system is a record and replay attack, “where a recording is made of the encrypted location data being sent from GPS satellites to the naval ship. Replaying the recording at a slightly later time could fool a ship into thinking it is someplace else. This is a very sophisticated and difficult hack that requires multiple recordings of the navigation data stream from multiple angles, and then sending the recorded signal from two or more locations.” (Weise, 2017) “To ensure that nearby ships do not also get the false data, it would have to be transmitted from close to the Navy ship being targeted, perhaps using multiple drones.” (Weise, 2017)
However, according to “ Professor David Lust, former president of the Royal Institute for Navigation in the United Kingdom, “it takes two to Tango…. I” think you just have to attack the weakest of the pair, which is the commercial vessel.” Commandeering the GPS of the cargo ship to get it to veer off course could cause collision, and it is a much easier hack.” (Humphreys, 2009)
The Case for a Cyber Weapon
There appears to be valid evidence to support the theory that at least two of the U.S. Navy Warships, USS John McCain, and the USS Fitzgerald AND/OR the commercial vessels involved were the on the wrong end of a Cyber-Weapon and were receiving incorrect GPS generated positional information. In agreement with Dr. Lust’s conclusions, the Cyber Weapon may have been deployed by an adversary’s [China PLAN] UAS off a small nearby vessel. The author believes that the subject Cyber-Weapon is an advanced modular entity that can spoof the GPS signals received by all vessels in its range. J.S. Warner & R.G. Johnson established in 2013 that the cyber-security of many common automated navigational systems today lacks basic cyber-attack protection; vessels using incorrect data will make wrong decisions in terms of navigation and emergency responses, leading to potential collisions and deaths (Warner & Johnson, 2013).
Surfacing Questions
Spoofing is generation of false transmissions masquerading as P(Y) [the encrypted] Precise Signal that makes up the military vessel positioning basis, or unencrypted C/A [Civilian Acquisition] code from GPS satellites. In a virtual world tracking invalid data streams or non-integrity-based data is difficult, especially on three dimensional vessels moving in time. However, there may be more than one method to spoof a signal no matter how well it is encrypted. The cargo ships involved could have received unencrypted GPS ranging; a much less complex method than is required for military vessels.
Both ships do not need to be disabled or spoofed. All ships (military, commercial, recreational, specialized service) in international waters require detailed positional information. GPS systems accurately supply a 3-D position, velocity, and time fix in all types of weather, 24 hours a day.
GPS satellite signals are ranging devices that deliver two signals made up of a civilian carrier, C/A code, NAV message, P-Code, and a military carrier. (Nichols, et al., Unmanned Aircraft Systems (UAS) in Cyber Domain: Protecting USA’s Advanced Air Assets, 2nd Edition, 2019)
Because of cost, most systems on commercial vessels have legacy GPS systems. In the author’s view, even if the GPS signals of the military vessels were not hacked the unencrypted C/A – L1 Civilian signal may have been. It is also provable that this spoof is technically feasible on the legacy systems. Experiments by Warner and Johnston out of Los Alamos, and surveys by Schmidt, et al out of Queensland University clearly support the GPS/GNSS Cyberattack threat vector. (Warner, 2013) In 2013, Humphreys and his students successfully spoofed an $80MM Yacht’s GPS system. (Humphreys, 2009)
What the physical damage indicates for the USS McCain and USS Fitzgerald is that both naval vessels appear to have collided on the starboard side. This leads to the theory that the Civilian vessels involved in crossing or approaching the US Naval vessels were relying on faulty information for their position. Further, the cyber weapon may have been delivered by small UAS from a nearby fishing or recreational vessel. It would be a perfect delivery vehicle: stealth, quiet, low radar signature, requiring only 1- 25 watts signal spoofing power. Since the true GPS signal strength reaching the surface of the Earth is about -160dBw (1x 10**-16 Watts), a 1-Watt GPS jamming spoof signal can override C/A code acquisition for more than 620 miles (Line of Sight (LOS) to horizon.) (Warner, 2013)
The starboard side collisions suggest that one of the vessels may have turned port or that the commercial ship tried to avoid a fake collision target received by turning starboard at the wrong time. The USS Fitzgerald report confirms this observation. These are huge vessels. Turning, stopping, or reversing course on a dime are not possible – especially by a large freighter. Decisions must be made well in advance of potential collision alerts. This is also why delivery of a cyber-weapon by UAS is so attractive. It would be a small bird in the glasses while attention was directed to the huge targets closing in on each other. In the chaos, the adversary wins.
How could GPS chaos be achieved against US Vessels?
The author believes, that for the spoofing GPS signal theory [targeting a commercial vessel by cyber weapon to give it a false position and potentially cause collision to itself or another vessel], to be possible. It would require an enemy Unmanned Aircraft System (UAS) to be launched from either a sea-based vessel or land-based intelligence station in the Spratly Islands. The methodology contemplated consists of three cyber-attack activities:
1) Breaking the existing AIS GPS commercial vessel receiver signal locks,
2) Locking the AIS GPS tracking device onto the GPS Simulator counterfeit signal,
3) Maintaining access by continued broadcasting of the fake GPS signal.
The problem is interesting because there are two three-dimensional maritime targets moving in time based on inaccurate or false ranging (GPS position) signals. The clocks used in GPS satellite systems are extremely accurate and present synchronization difficulties with the target naval / commercial vessel receivers. If it is possible to simulate and spoof the GPS signals to the commercial vessel using AIS collision avoidance systems (Cyber-weapon CONOP), then it is also possible that the US Navy may not have given proper attention to the non – personnel issues in their accident investigations.
Further, the possible delivery of such a Cyber-Weapon by close range UAS means that adversaries may have increased their knowledge management and understanding of U.S. Navy defensive systems. Using asymmetric warfare tactics and attacking the commercial traffic, which deploys legacy and cheaper GPS receivers, forces dependence on faulty information. Unfortunately, it is an effective tactic that bypasses much of the military modernization of GPS signals and satellites. This same possibility could affect military and commercial aircraft also, especially at airports where traffic speeds are reduced, and aircraft are closer to each other. (Nichols, et al., Unmanned Aircraft Systems (UAS) in Cyber Domain: Protecting USA’s Advanced Air Assets, 2nd Edition, 2019)[3]
Chinese Nightmare
Think of Chinese use of swarming drones on the seas, in the air, floating nuclear power plants, underwater mining, robot freighters and anti-submarine UUVs. In the author’s view, they are leapfrogging US technology and antiquating defenses (Lehman, 2017).
It should be clear that the Chinese (PLAN) are heavily invested in military operations using unmanned aircraft and naval vessels in the Spratly Islands. This researcher has been tracking Chinese UAS and Intelligence assets /facilities / naval vessels since 2014. Figure 14.1 shows a glimpse of the deployment in the Spratly Area of Operations (AO). The black pin is the Spratly Islands group. Blue pins represent US Navy capital ships involved in either collisions or groundings in the AO. Red pins represent center of known Chinese UAS Intelligence elliptical paths. Green pins represent Chinese Intelligence facilities or seaborn assets. An exploded map view would show many more Chinese assets in the AO (Nichols R. &., 4 May 2018).
Given the capabilities that Chinese (and US) UAS systems can deploy in almost any conditions and any location, it seems reasonable to this researcher, that the Chinese military might test their cyber weapons from their UAS in the Spratly AO coverage to harass US vessels and potentially disrupt US Navy capital ships navigation systems. [This would be a natural priority for the Wanshan Marine Test Facility.] As a lesser alternative, the Chinese might take the 911 approach [ i.e. turning planes into missiles loaded full of fuel and ramming them straight into fixed buildings] by disrupting (signal spoofing) the GPS /AIS unencrypted signals of huge commercial vessels and forcing them to act as Greek trireme vessels, colliding into the US Naval vessels in restricted maneuverable waters. [4]
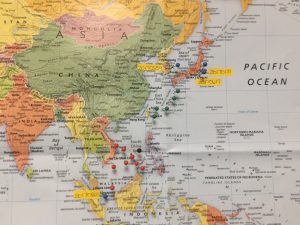
Figure 14.1 Chinese UAS Chinese Intelligence Assets Deployment in Spratlys
Source: (Nichols R. &., 4 May 2018)
Marine Transportation System / Sector (MTS) Scope
To their credit, Kessler and Shepard have a wonderful description of the MTS. (Kessler, 2020) Its size /scope and value to the economy as well as the enormity and complexity of its cyber structure cannot be overestimated. The MTS represents a very large cyberthreat surface, given every system with it represents a potential attack vector. (Kessler, 2020)
The MTS comprises ships, shipping lines, ports, passenger terminals, manufacturers, cargo facilities, intermodal partners, and all users of these facilities globally. Every element represents a potential vulnerability to cyber attack – a potential weak point to cyberthreats – and a vector for infection of other elements in the MTS. (Kessler, 2020) By 2023 there are expected to be more than 70,000 merchant vessels on the water operating in / out of approximately 4,800 ports in 200 countries. Merchant ships don’t make money if they sit idle, they are in constant motion. (Kessler, 2020) All modes of transportation interact with each other as cargo and passengers move be to disposal, tween ships, inland waterways, railroad cars, trucks, and airplanes. Intermodal connections are additional vectors for cybersecurity threats.
(Kessler, 2020) describe the MTS as a system of systems comprising of six interconnected systems: ships, ports, people, shipping lanes, inland waters, and intermodal transfers.
MTS Systems / Sector
The Ships subsystem includes all aspects of in the lifecycle of a vessel, from manufacturing, to maintenance, to operations, communications, networks, security, and navigation systems.
The Ports subsystem includes construction, maintenance, logistics, vessel traffic management, and daily port operations.
The People subsystem includes the entire supply chain, trading partners, vendors, and customers.
The Shipping Lanes subsystem comprises the operation and management of companies that own ships, passengers and cargo, reservation and scheduling, finances, operations, and communications.
The Inland Waters subsystem includes the inland waterway systems, Aids to navigation (ATN), Notice to Mariners (NTM) and dredging and maintenance.
The intermodal Transfer subsystem describes the MTS interfaces with other transportation modalities, including barge, railroads, trucking and to lesser extent aviation. (Kessler, 2020)
MTS Scope
The MTS is a significant economic driver for the nation. It contributes about $5 trillion annually to the GDP, supports 30 MM jobs, representing 20% of the workforce. It includes 25,000 miles of navigable channels, 95,000 miles of shoreline, 361 commercial ports, 50,000 federal and millions of private aids to navigation (ATNs) / (ATONs), 20,000 bridges over water, greater than 3700 marine terminals, 200 ferry operations, 238 locks at 192 locations. The MTS user community includes hundreds of thousands of small fishing , sightseeing, liveaboard, dive boats, and 12 million recreational boats. MTS waterways are shared by military, public safety, LEO vessels; work boats, dredge boats, buoy tenders; commercial fishing vessels; personal power boats and sailing vessels; and drilling platforms , wind turbines, moorings, and fixed location offshore facilities. (Kessler, 2020)
It should be clear that the MTS environment comprises countless moving parts, each playing a critical role in maritime transportation safety and operations. Each represents a potential attack vector through their associated computer networks.
MTS Cyber Attack Vectors / Targets
Most maritime cyber-attacks are via operational computer networks. In general, they are not designed for robust security nor are they modern.[5] (Kessler, 2020) identifies eight critical cyberattack vectors in the MTS: vessel operation, shipping line operations, port operations, cargo and transit, manufacturing, vessel traffic control (VTC), remote control and autonomous operations and partners.
Vessel operations: Ships are floating networks. They include operational networks controlling ships systems, security and cargo management, bridge controls for navigation, weapons control, and lad / ship to ship / satellite communications.
Shipping line operations: cargo and passenger shipping lines have complex outward facing networks and internal networks. They use the public internet for public relations, e-commerce, reservations, partner portals, reservations, cargo tracking and sales / marketing information. Internal networks handle all the vessel operations above plus payroll, taxes, logistics, legal compliance, route management and partner relations.
Port operations: networks handle all the shipping line functions, vessel tracking, USCG operations, vessel traffic management (VTM),immigration, drug enforcement, cargo security, and links to intermodal carriers.
Cargo and shipping: cargo-related operations include SCADA systems to move cargo, onloading / offloading, port cranes, security at several stages, inspections, and autonomous systems.
Manufacturing: All the functions of the port are seen through the eyes of its supporting manufacturers and vendors. Critical to the security is supply chain management, intellectual property protection, and ID theft resolution.
VTC: Managing the flow of vessels, especially in a busy port or narrow body of water requires reliable communications; positioning, navigation, and timing (PNT) systems. Automatic Identification Systems (AIS), NTM, are critical to safe operations. Each of these systems provides a fertile line of cyber-attack in geographic areas than can tolerate a low margin of error. VTC does not control the recreational or commercial fishing vessels. (Kessler, 2020)
Remote control and autonomy: Unmanned and autonomous vehicles and vessels, are emerging as
shortage of qualified personnel becomes more acute. Remote control ships, tugs, docking facilities, drones, trucks, and cranes are sprouting up like weeds. Each can be manipulated independent of the owner /operator. The author did a simulation of taking over an oil company’s storage facilities and SCADA systems to pour 12 MM gallons of oil into the Chesapeake Bay. The environmental damage was in the billions and loss of services, crab industry, effects on the recreational boating industry took a decade to recover. (Nichols R. K., Nov 28-30 2006)
Partners: Vulnerable computer network systems can be exploited as a jumping point on to a more fertile target. Attackers do not want your computers or your networks; they want your information. That is the very definition of partner in the context of cybersecurity. A partner is any entity that affects, the chain of custody of your data. Last point, the IT structure in many organizations are shared ownership. In terms of security, this is akin to sharing a hypo needle for cocaine. Organizations use the cloud as a host. Reservations, ticketing, are managed by an e-commerce host. It is linked to a financial system. This is nuts of course. So many ID frauds and compromised credit cards in huge numbers ought to tell us this. Corporate networks general use VPNs to provide access to their internal network via a public internet.
Civilian ships have multiple onboard networks to handle ballast, propulsion, power, status monitoring and provides a pathway to communicate with their land-based counterparts. GPS, AIS, VHF, and VTS communicate over public radio channels. (Kessler, 2020)
The MTS represents a huge cyber threat surface, given that every system within it represents a potential attack vector. (Kessler, 2020)
Cyber-Physical Systems, Operational Technology, and the Internet of Things (IoT)
Cyber-physical systems(CPS) is the global term encompasses people, computers, and physical devices into an operational system. CPS takes advantage of sophisticated sensors, instruments, networks, embedded computers, SCADA brains, and combines them into smart infrastructures and industrial applications. CPS applications run the whole gamut from the smart grid; medical monitoring; autonomous vehicles, vessels, aircraft; process control systems; robotics systems; and automatic aviation and maritime navigation systems. (Kessler, 2020).
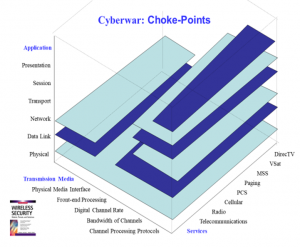
Figure 14.2 Cyberwar: Chokepoints
Source: (Nichols R.K, 2002)
There are lots of views / models of CPS systems. Figure 14.2 shows a differentiation of computer “choke points” (vulnerable to cyberattacks in cyberwar scenario) based on network parameters, transmission media, applications, and services. Figure 14.3 shows the interaction between physical and cyber systems and how they leverage each other.
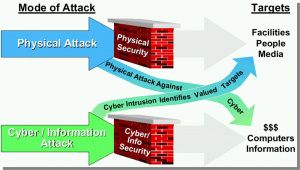
Figure 14.3 Shared Cyber Threats in CPS System
Source: (Nichols R. K., Nov 28-30 2006)
Figure 14.4 shows the complex interdependencies between Infrastructure and the SCADA controls that dictate the inter-flows in a CPS system.
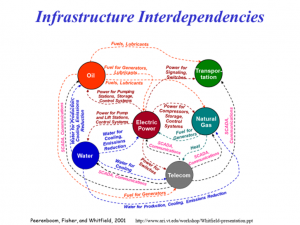
Figure 14.4 shows SCADA and Infrastructure interdependencies in a CPS System
Source: (Peerenboom, 2001)
Operational Technology (OT) comprises the technologies and methods that enable the cyber and physical worlds to interact. In OT systems, computers directly provide real-time monitoring, and control of physical devices such as valves, pumps, dams, power grids, robots and transportation systems. Industrial Control Systems (ICS) make up the largest OT devices. SCADA is the control brains of these systems and represents the preferential vector for cyberattacks. (Randall K. Nichols, 2000) (Nichols R. K., Nov 28-30 2006) (Kessler, 2020)
Internet of Things (IoT)
The Holy Grail of CPS is the Internet of Things (IoT)! IoT combines data analytics, artificial intelligence (AI), wide available broadband networks (WABN), advanced sensor technology, miniaturized processors, embedded ASICS,[6] and advanced software to allow independent devices to share all kinds of information and engage in network-wide decision making. This transforms traditional physically limited devices into smart equivalents. (Kessler, 2020) IoT devices number in the multi-billions. IoT applications are found in every business and infrastructure and home. They are single reason that privacy is a thing of the past. {I have taught my students the theory behind hacking the house smart electrical meter (installed in about 80% of homes without their permission or realization how much privacy and control of their lives was lost ). The meter-hack can tell the Bad Actor how many times you flush your toilet, use the microwave, the frequencies behind your security systems, or turn lights off /on or even charge your phone. All without the user knowledge or permission. IoT!}
Computers within CPS and IoT networks are prone to the same threats and vulnerabilities with any other architecture BUT the span of control has a much larger purview. Unsecured IoT devices are a very real threat to the global internet and attached devices. They are the favorite target for criminals. Websites like censys.io and shodan.io allow people to search the internet for IoT devices where one can find passwords to hacked IoT devices. Many of them crack security monitoring / credit monitoring services.
Maritime CPS Applications and Cybersecurity
The trend is to increase automation systems on vessels. The trends is also miniaturization and to some extent replace people. The USN is doing this at David Taylor Research Center in Annapolis , MD. There goal is to automate vessels and reduce the crew size. The author has been on some of these experimental ships.
There is no doubt that automation has safety and economic benefits and achieve precise solutions to navigation scenarios. But more systems also means increasing interdependencies and more risky cyber vulnerabilities. New ICS and IoT technologies have enabled innovations inside the ship envelope and outside. From bridge to the engine room, system designers have endeavored to build more integrated shipboard control systems (ISCS) and make the supply chain operations and fuel systems more efficient.
New IoT technologies have enabled innovative systems outside of the ship:
- ü Intelligent mooring systems with embedded sensors in mooring lines. From the bridge, these monitor tension, time, temperature, and predict early failure or wear. (Kessler, 2020)
- ü Supplement Interactive Electronic Maintenance Manuals ( IETM) and optimize outcomes.
- ü Act as building blocks for a Cooperative Cognitive Maritime Cyber Physical System (CCMCPS) to provide high-speed, low-cost communications between ships, ports, buoys,offshore platforms, and shore stations. This includes automation of the cranes and transport vehicles. Ports are the bottleneck for movement of cargo. CCMCPS optimizes communication between vessels, ports, maritime terminals and cargo handling systems. (Kessler, 2020)
Autonomous maritime systems are starting to incorporate drones, UAVs to provide surveillance, situational awareness in a port area, for both manned and unmanned ships. UAVs supplement ship inspections by their ability to safely enter locations too dangerous for people. They are used for a detailed analysis of hull or cargo bay in real-time. They supplement autonomous tugs and mooring systems by transporting heaving lines from the dock or tug or ship. (Kessler, 2020)
Conclusions
IoT, ICS and autonomous maritime systems are technologies bringing the maritime industry into the future. While the individual devices are small the systems they interact with are large, complex, and complete with cybersecurity issues because fundamentally, they are merely computer hardware, software, SCADA, and communications technologies.
Student Questions
- Make a taxonomy of the top cybersecurity attacks on the MTS and needed cyber defenses to reduce risk in the chosen targets.
- Where do you see the IoT landscape in terms of cyber attack payloads on MTS.
- There is no silver bullet to protect the MTS “elephant.” So develop an initial plan to protect the “part of the elephant” subsystem in the MTS that offers the biggest return on investment ( lowers risk of cyber attacks).
References
Adamy, D. -0. (2015). EW 104 EW against a New Generation of Threats. Boston: Artech House.
Adamy, D. (2001). EW 101 A First Course in Electronic Warfare. Boston, MA: Artech House.
Adamy, D. (2009). EW 103 Tactical Battlefield Communications Electronic Warfare. Boston, MA: Artech House.
Adamy, D. (2015). EW Against a New Generation of Threats. Boston: Artech House.
Adamy, D. L. (2004). EW 102 A Second Course in Electronic Warfare. Boston: Artech House.
Adamy, D.-9. (1998, Jan). Lesson 4: the basic link for all EW functions. (electronic warfare)(EW Reference & Source Guide). Journal of Electronic Defense, Jan 1998 Issue.
Alford, L. (2000). Cyber Warfare: Protecting Military Systems. Acquisition Review Quarterly.
Angelov, P. (2012). Sense and avoid in UAS research and applications. Hoboken: NJ.
Army, U. (1992, November 23). US Army Field Manual FM 34-40-7. Communications Jamming Handbook.
Austin, R. (2010). “Design for Stealth”, Unmanned Aircraft Systems UAVS Design Development and Deployment. New York: John Wiley and Sons.
Balduzzi, M. W. (2014). A Security Evaluation of AIS. Retrieved from Trend Micro: https://www.acsac.org/2014/program-final/oc_multifile/3/62.pdf
Barnhart, R. K. (2012). Introduction to Unmanned Aircraft Systems. New York: CRC Press.
Beaudoin, L. e. (2011). Potential Threats of UAS Swarms and the Countermeasures Need. ECIW.
Dalamagkidis, K. V. (2012). On Integrating Unmanned Aircraft into the National Airspace System, 2nd edition. Denver, CO: Springer.
Department of the US Navy, Office of Chief of Naval Operations. (2017, November 29). Report on the USS Lake Champlain Collision. Retrieved from www.documentcloud.org/documents/: https://www.documentcloud.org/documents/4316708-171129-USS-Lake-Champlain-Collision-Report.html
DoD-01. (2018). JP 1-02. Retrieved from Department of Defense Dictionary of Military and Associated Terms: www.dtic.mil/doctrine/new_pubs/jp1_02.pdf
DoD-02. (2018). Information Operations (IO) in the United States. Retrieved from JP 3-13 : http://www.dtic.mil/doctrine/new_pubs/jp3_13.pdf
DoD-03. (2015). Unmanned Systems Roadmap 2013 to 2038. Retrieved from DTIC: http://www.dtic.mil/dtic/tr/fulltext/u2/a592015.pdf
DTRA. (2019, October 18). Private Communication re Aviation Vulnerabilities. (Nichols, Interviewer) Retrieved from https://www.dtra.mil/
Durham, W. (2013). Aircraft Flight Dynamics and Control. The Atrium, Chesterton, UK: Wiley.
EIA. (2019, June 20). The Strait of Hormuz is the world’s most important oil transit chokepoint. Retrieved from EIA – US Energy Information Administration: https://www.eia.gov/todayinenergy/detail.php?id=39932
Eshel, T. (2019, September 14). AFRL to Test a Drone-Swarm Killer HPM. Retrieved from Defense Update: https://defense-update.com/20190923_hpm.html
FAA. (2018, February 1). Part 107 Rule for sUAS. Retrieved from Fly under the Special Rule for Model Aircraft: https://www.faa.gov/uas/getting_started/model_aircraft/
Filbert, F. &. (2014, (July – August). Joint Counter Low, Slow, Small Unmanned Aircraft Systems Test. Fires PB644-14, no 4. Washington: DoD.
Fitts, R. (1980). The Strategy of Electromagnetic Conflict. Los Altos, CA: Peninsula Publishing.
Gallagher, S. (2019, September 16). Missiles and drones that hit Saudi oil fields: Made in Iran, but fired by whom? Retrieved from Arstechnica.com: https://arstechnica.com/tech-policy/2019/09/missiles-and-drones-that-hit-saudi-oil-fields-made-in-iran-but-fired-by-whom/
Hartman, K. a. (2013). The Vulnerability of UAVs to Cyber Attacks – An Approach to the Risk Assessment. 2013 5th International Conference on Cyber Conflict . Tallin: NATO CCD COE Publications.
Horowitz, E. (1978). Fundamentals of Computer Algorithms. Potomac, MD: Computer Science Press.
Howard, C. (2019, June 21). What is the Strait of Hormuz, where Iran shot down US Navy drone? Retrieved from Fox News: https://www.foxnews.com/world/whats-the-strait-of-hormuz-iran-shot-us-navy-drone
Humphreys, T. e. (2009, January 1). Assessing the Spoofing Threat: Development of a Portable Civilian GPS Spoofer. Retrieved from Cornell University: https://gps.mae.cornell.edu/humphreys_etal_iongnss2008.pdf, Cornell University
Kania, E. (2017, July 6). Swarms at War: Chinese Advances in Swarm Intelligence. China Brief Volume: 17 Issue 9. China Brief Volume: 17 Issue 9.
Kaye, T. a. (2001, September 30). ACHIEVING INFORMATION DOMINANCE:. Retrieved from DODCCRP-Space and Naval Warfare Systems Center San Diego: http://www.dodccrp.org/events/2002_CCRTS/Tracks/pdf/026.PDF
Kessler, G. &. (2020). Maritime Cybersecurity: A Guide for Leaders and Managers. Daytona Beach, FL: Kessler & Shepard (Self-published) ISBN: 979-867-6215354.
Kim, A. G. (2012, June). Cyber Attack Vulnerabilities Analysis for Unmanned Aerial Vehicles. Retrieved from Infotech@Aerospace.com: https://www.researchgate.net/publication/268571174_Cyber_Attack_Vulnerabilities_Analysis_for_Unmanned_Aerial_Vehicles
Lehman, C. (2017, August 29). China Increasing Drone Operations in Disputed Seas, Freebeacon. Retrieved from Freebeacon: http://freebeacon.com/author/charles-lehman
Lipschutz, M. (1969). Schaum’s Outline for Differential Geometry. NYC: McGraw-Hill .
Lister, T. (2019, September 16). Attack is a game-changer in Gulf confrontation. Retrieved from CNN: https://www.cnn.com/middleeast/live-news/saudi-oil-attack-dle-intl/h_3e647100fa720927c962d7643472b12d
Marshall, D. M. (2016). Introduction to Unmanned Aircraft Systems, 2nd Edition. New York: CRC Press.
Moir, I. a. (2006). Military Avionics Systems. New York: Wiley Aerospace Series.
Monahan, K. (2004). The Radar Book: Effective Navigation and Collision Avoidance. Anacortes, WA: Fineedge Publications.
Myer, G. (2013, May-June). Danger Close Definition. Retrieved from US Army Magazine: www.benning.army.mil/infantry/magazine/issues/2013/May-June/Myer.html
N/A. (2020, July 25). Cambridge Dictionary online. Retrieved from dictionary.cambridge.org/us/: https://dictionary.cambridge.org/us/
NASA. (2018). Unmanned Aircraft Systems (UAS) Integration in the National Airspace System (NAS) Project. Retrieved from NASA: https://www.nasa.gov/feature/autonomous-systems
Navy Information Office . (2017, November 1). Navy Releases Collision Report for USS Fitzgerald and USS John S McCain Collisions. Retrieved from Story Number: NNS171101-07: Story Number: NNS171101-07Release Date: 11/1/2017 9:01:00 AM
Nichols, R. &. (4 May 2018). RSCAD Presentation of Research to KSUP Faculty on Deployment of Chinese Cyber-weapons and GPS spoofing of Naval Vessels. Salina, KS: KSU.
Nichols, R. K. (2008, September 05). Counterintelligence & Sensitive Compartmented Information Facility . (SCIF) Needs – Talking Points.
Nichols, R. K. (2019, March 14). Hardening US Unmanned Systems Against Enemy Counter Measures. 7th Annual Unmanned Systems Summit. Alexandria, VA, USA: PPTX presentation , self.
Nichols, R. K. (Nov 28-30 2006). Presentation on Cyber Terrorism, Critical Infrastructure and SCADA . Shirlington, VA: Defense Threat Reduction Agency Conference.
Nichols, R. K., Mumm, H. C., Lonstein, W. D., Ryan, J. J., Carter, C. M., & & Hood, J. P. (2020). Counter Unmanned Aircraft Systems Technologies & Operations. Manhattan, KS: New Prairie Press #31.
Nichols, R. K., Mumm, H. C., Lonstein, W. D., Ryan, J. J., Carter, C., & and Hood, J.-P. (2019). Unmanned Aircraft Systems in the Cyber Domain, 2nd Edition. Manhattan, KS: NPP eBooks. 27. Retrieved from www.newprairiepress.org/ebooks/27
Nichols, R. L. (2002). Wireless Security : Threats, Models, Solutions. Washington, DC: McGraw Hill.
Nichols, R. (Nov 28-30, 2006). Cyber Terrorism, Critical Infrastructure, & SCADA Presentation. In R. Nichols (Ed.), Defense Threat Reduction Agency Conference. Shirlington VA: Utica College, Utica NY.
Nichols, R., Ryan, J., Mumm, H., Carter, C., Lonstein, W., & Hood, &. J. (2020). Counter Unmanned Aircraft Systems Technologies and Operations. Manhattan, KS: New Prairie Press #31.
Nichols, R., Ryan, J., Mumm, H., Lonstein, W., Carter, C., & & Hood, J. (2019). Unmanned Aircraft Systems (UAS) in Cyber Domain: Protecting USA’s Advanced Air Assets, 2nd Edition. Manhattan, KS: New Prairie Press #27 .
Nichols, R.-0. (2016, March 29). NCIE UAS SAA Final Rev 4. 2016 INFOWARCON conference presentation April 4-7, Nichols, R.K. et. al. (3-29-2016) Presentation to INFOWARCON April 4-7 on NCIE UAS SAA Final Rev 4, presented to 2016 INFOWARCON conference, Memphis TN. Available as PPTx presentation download from author or in CANVAS. Memphis, TN, USA: INFOWARCON16.
Nielsen, P. E. (2012). Effects of Directed Energy Weapons. Middletown, DE: CreateSpace Independent Publishing Platform.
Olson, W. (August 30,2017). Adm No Evidence of Hacking in McCain Fitzgerald Collisions pdf. Washington: Stars and Stripes.
Osborn, K. (2019, October 15). Swarm Hell: Can the U.S. Army Stop Hundreds of Drones Armed with Explosives? Retrieved from National Interest: https://nationalinterest.org/blog/buzz/swarm-hell-can-us-army-stop-hundreds-drones-armed-explosives-88206
Peerenboom, F. &. (2001). Whitfield Presentation ppt re Infrastructure Interdependencies. Retrieved from ari.vt.edu/workshop: http://www.ari.vt.edu/workshop/whitfield-presentatrion.ppt
Randall K. Nichols, D. J. (2000). Defending Your Digital Assets against Hackers, Crackers, Spies and Thieves. New York: RSA Press.
Rani, C. M. (2015). Security of unmanned aerial vehicle systems against cyber-physical attacks. The Journal of Defense Modeling and Simulation: Applications, Methodology, Technology.
Reklaitis, G. R. (1983). Engineering Optimization: Methods and Practices. Boston: Wiley.
Sheena McKenzie, M. W. (2019, September 17). Saudi attacks send oil prices soaring. Retrieved from CNN: https://www.cnn.com/middleeast/live-news/saudi-oil-attack-dle-intl/h_1ab7e8469e98525f887c3a4e588dde8a
Singer, P. W. (2010, February 25). Will Foreign Drones One Day attack the US? . Newsweek.
Skolnik, M. (2008). Radar Handbook, 3rd Edition. Boston: McGraw Hill.
Sood A.K. & Enbody, R. (2014, December 19). https://www.georgetownjournalofinternau-s-military-defense-systems-the-anatomy-of-cyber-espionage-by-chinese-hackers. Retrieved from georgetownjournalofinternationalaffairs.org/online-edition: https://www.georgetownjournalofinternationalaffairs.org/online-edition/u-s-military-defense-systems-the-anatomy-of-cyber-espionage-by-chinese-hackers
Spratly. (1955). Spratly Islands Fact Page. Retrieved from Library of Congress: http://hdl.loc.gov/loc.gmd/g9237s.ct002223
Stratfor. (2019, October 20). strait-of-hormuz-chokepoints. Retrieved from https://www.stratfor.com: https://www.stratfor.com/sites/default/files/styles/wv_small/public/strait-of-hormuz-chokepoints.jpg?itok=xSgx6Hhi
Tewari, A. (2011). Advanced Control of Aircraft, Spacecraft and Rockets. Chichester, UK: Wiley.
Tsourdos, A. &. (2011). Cooperative Path Planning of Unmanned Aerial Vehicles . Reston, VA: American Institute of Aeronautics and Astronautics, Vol #235.
Warner, J. &. (2013). A Simple Demonstration That the Global Positioning System (GPS) is Vulnerable to Spoofing. Retrieved from Journal of Security Administration: https://pdfs.semanticscholar.org/8ddb/89f56dd3e2ae265047822bc47cfb06815d9a.pdf, LAUR-03-6163
Weise, E. (2017, August 23). could-hackers-behind-u-s-navy-collisions. Retrieved from USATODAY: https://www.ruidosonews.com/story/tech/news/2017/08/23/could-hackers-behind-u-s-navy-collisions/594107001/
Wikipedia. (2020, July 26). A* Algorithm. Retrieved from Wikipedia: https://en.wikipedia.org/wiki/A*_search_algorithm
Wiley, R. G. (1993). Electronic Intelligence: The Analysis of Radar Signals, 2nd ed. Norwood, MA: Artech House.
Wilson, M. (2012). The Use of Low-Cost Mobile Radar Systems for Small UAS Sense and Avoid. Sense and Avoid in UAS Research and Applications.
WWF. (2019, July 25). South China Sea, between the Philippines, Borneo, Vietnam, and China. Retrieved from worldwildlife.org/ecoregions/: https://www.worldwildlife.org/ecoregions/im0148
Yu, X. &. (2015). Sense and avoid technologies with applications to unmanned aircraft systems: Review and prospects. Progress in Aerospace Sciences, 74, 152-166.
Yunmonk Son, H. S. (2015, August 12-14). Rocking Drones with Intentional Sound Noise on Gyroscopic Sensors. Proc. 24th Usenix Security Symposium. Washington, DC: USENIX. Retrieved from https://www.usenix.org/conference/usenixsecurity15/technical-sessions/presentation/son
Zhang, Z. W. (2020). Rapid Penetration Path Planning Method for Stealth UAV in Complex Environment with POP-UP Threats. International Journal of Aerospace Engineering, TBA.
[1] (Kessler, 2020) discuss exactly this kind of scenario in their Preface. This excellent book is highly recommended for purchase. https://www.amazon.com/Maritime-Cybersecurity-Guide-Leaders-Managers/dp/B08HBDDSQD/ref=sr_1_1?dchild=1&keywords=kessler+Maritime+Cybersecurity&qid=1600025530&sr=8-1
[2] The full case with equations of closest point of approach (CPA) are given in www.newprairiepress.org/ebooks/27/
[3] The South China Seas GPS scenario is the sole speculation of the author based on his research and proposals during 2017-2018. It is not the opinion of KSU, NPP, CADS or any official in the line of publication. The USN has admitted that cybersecurity of its systems and commercial vessels has vulnerabilities. They have devoted significant resources to the cybersecurity threats / subject under command of an Admiral. There is significant work to mitigate these navigational threats.
[4] Triremes were used in the Peloponnesian Wars to ram at about 4 knots at a 60-degree angle of attack. The greater the angle of attack the lesser the speed requirement for ramming. What is interesting is that the Athenians used a multi-trireme attack, an early predecessor to Swarm tactics. They also used grappling hooks to engage the enemy ships directly up close. This was the predecessor to piracy tactics in the 1500’s – 1830’s. Wikipedia.
[5] Authors evaluation based on his research at KSU.
[6] ASICs= Application specific integrated Circuits & circuit boards

