5 Space Based Platforms and Critical Infrastructure Vulnerability (McCreight)
CHAPTER 5: SPACE BASED PLATFORMS AND CRITICAL INFRASTRUCTURE VULNERABILITY (MCCREIGHT)
Student Objectives
Students will discuss, analyze and study:
- the nature of critical infrastructure and its various subsystem elements today
- the impact of space-based platforms and technology on critical infrastructures
- the significance of selected space related technologies on the operational integrity of critical infrastructures and their relevant cyber vulnerabilities
- Potential threat indicators related to space-based platforms after 2023
- Security and risk management issues involving the protection and safeguarding of critical infrastructures from space-based threats as well as expected future challenges
Background
For well over 20 years, we have consistently recognized the existence of critical infrastructures which undergird our nation, its security, its economy, and overall operational integrity. The variety and number of Critical Infrastructures [CI] is significant and subject to modification and expansion based on an objective assessment by national governments of those essential systems which sustain the national security, societal stability, and economic wellbeing [such as clean water and reliable energy] of the nation safeguarding its cohesion and daily operation. Simply put, most modern societies in the 21st century would collapse and fail without reliable CI.
The original list of critical infrastructures outlined in 6 USC 671 in 2002 by language contained in the ‘Critical Infrastructure Protection Act’ includes a vague reference to “. any component or bureau of a covered Federal agency that has been designated by the President or any agency head to receive critical infrastructure information. (CISA, 2002) Today the broad term symbolizes distinct areas of activity, enterprise and industrial operations which support and guarantee everyday life in the nation. For example, critical infrastructures [CI] encompass energy systems, water and wastewater systems, agriculture and food supply systems and telecommunications to identify just a few. Moreover, it has been clearly established an emphasized that these critical infrastructures are essential to both national and homeland security despite ample evidence that the sheer reliability, performance, operational demands, and risks for each system is distinct in many case while uniformly vulnerable in others.
What is of paramount security interest is assessing the various space-based platforms [seen as distinct potential weapons systems with disruptive capabilities] and gauging their impact on critical infrastructures as they may retain the potential to nullify and adversely affect the normal operations of CI systems especially after 2023. We must recognize that space-based systems and platforms retain their own inherent vulnerabilities apart from the supporting role these orbital systems play in sustaining ground level CI systems. Exploiting space platforms as legitimate targets themselves, when combined with their pivotal role in sustaining certain CI systems, means the layers of security must envelop both aspects. Understanding this emerging security risk and enduring challenge will tax the national and homeland security enterprise in ways unexpected. The special risks arising from cyber intrusions on space systems merits a closer look. This offers an additional vulnerability for space systems apart from ASAT [anti-satellite weapons], directed energy systems, particle beam weapons and lasers to name a few.
Space systems are usually divided into several technological and operational segments, which are responsible for different functions and components all vulnerable to cyber intrusion to some degree. Together Ground Stations, Mission Control Centers, Ground Networks, Remote Infrastructure, and Launch Facilities work together to enable management of spacecraft, payload data, and telemetry. Most often exposed to different cyber threats are the ground segment, the space segment, and the link segment. Each segment presents its own unique vestiges of cyber risk and vulnerability. (Weigel, n.d.)
The ground segment consists of all the ground elements of space systems and allows command, control and management of the satellite itself and the data arriving from the payload and delivered to the users. Due to their role in collecting data, the ground stations and terminals are exposed to the threat of cyber espionage from states and non-state actors. Moreover, the military aspect of satellites and their importance to national security render them prime targets for hostile takeover, disruption, and shutdown. Most cyberattacks on the ground segment exploit web vulnerabilities and allow the attacker to lure ground station personnel to download malwares and Trojans to ground stations’ computers. Infiltrating the ground station’s network can allow the attackers to access the satellite itself. Hostile access could enable the attacker to execute a Denial of Service (DoS) attack and may involve taking over Industrial Control Systems (ICS) in order to control the satellite and damage it.
The space segment consists of the satellites themselves. Major security gaps within satellites’ architecture exist in both old and new satellites. Old satellites with life spans of decades were built with no awareness for cyber security; today, small satellites manufacturers tend to prioritize fast and cheap production, in which the investment in cyber security is perceived as a hurdle. Cyber threats to space segments usually derive from vulnerabilities in ground stations, in network components, and in the receivers which receive the data from the satellite, thus allowing the attacker to infiltrate to the network and remain undetected. Another threat may involve the introduction of a malware into the satellite’s hardware in the supply chain, in order to compromise ground units at a later stage. Consequences of cyberattacks on satellites could also be aggravated due to the rising connection and use of Internet of Things (IoT) devices. An attack on a communication satellite could cause wide disruptions to communication channels across countries, cause panic, and endanger national security.
The link segment consists of the signal transmission between the satellite and the ground station, as well as between satellites. The most common threat is GPS jamming. As GPS systems rely on radio signals sent from the satellite in order to determine the location of the users, GPS jammers send signals over the same frequency as the GPS device, in order to override or distort the GPS satellite signals. GPS jammers are widely accessible and cheap to purchase, rendering them available also to poorer state-actors. In November 2018, Russia was suspected of disrupting GPS signals in northern Norway and Finland as the two nations participated in NATO’s Trident Juncture exercise. Another type of attack is ‘spoofing’ – faking signals by broadcasting incorrect GPS signals, structured to resemble genuine ones. Spoofing is harder to carry out than jamming, but if executed effectively, can be much more dangerous, mainly because the victims do not necessarily know that they are being spoofed. According to a 2017 US Maritime Administration report, the GPS systems of at least 20 ships were spoofed, leading the ships 32 kilometers inland to the Gelendzhik Airport in the Black Sea, away from the original destination. The incident raised assumptions among experts that Russia had been experimenting new GPS spoofing techniques as part of its electronic warfare capabilities. While some experts define jamming and spoofing as physical threats as they involve disrupting or tampering with frequency signaling, an attacker could also intercept unencrypted satellite traffic. (Wechsler, 2020)
Critical Infrastructure, [Ci] A Foundational Achilles Heel, Today and Tomorrow
The Department of Homeland Security has defined, categorized, and described what critical infrastructure [CI] means and includes a list of essential systems as of 2022 in various official documents including the National Infrastructure Protection Plan [NIPP]. What is just as important is the list of current, as well as potentially relevant other critical infrastructures, which provide the secure operational backbone of our nation’s economy, societal wellbeing, and security. For the last two decades each of the enumerated CI systems have been studied and evaluated to discern their fundamental operational requirements, system strengths, vulnerabilities, maintenance issues and security aspects. Each distinct CI system is reviewed and administered via the Department of Homeland Security [DHS] and there have been some interesting studies since 2002 which drew attention to significant operational and security issues. For example, via the National Critical Infrastructure Prioritization Program, the DHS oversight agency known as the Cybersecurity and Infrastructure Security Agency (CISA) is required to identify a list of CI systems and assets that, if destroyed or disrupted, would cause national or regional catastrophic effects.
Back in 2007, for example, GAO found that certain CI control systems faced increasing risks due to cyber threats, system vulnerabilities, and the serious potential impact of attacks as demonstrated by reported incidents. Threats can be intentional or unintentional, targeted or nontargeted, and can come from a variety of sources. Control systems are more vulnerable to cyber-attacks than in the past for several reasons, including their increased connectivity to other systems and the Internet. Further, as demonstrated by past attacks and incidents involving control systems, the impact on a critical infrastructure could be substantial. Control systems—computer-based systems [such as SCADA-Supervisory Control and Data Acquisition] ] that monitor and control sensitive processes—perform vital safety and operational reliability functions can be found in many of our nation’s critical infrastructures such as electric power generation, transmission, and distribution; oil and gas refining; and water treatment and distribution. The disruption of control systems could have a significant impact on public health and safety, which makes securing them a national priority. Subsequent studies and objective evaluations have identified other similar issues. (GAO, 2007)
CI systems have been known to be sensitive to solar storms, targeted terror attacks, and EMP explosions in addition to their cyber weaknesses. In a recent 2022 GAO report CI stakeholders identified cyberattacks as among the most prevalent threats they faced but said that the program’s list was not reflective of this threat. Further, according to CISA data, since fiscal year 2017, no more than 14 states (of 56 states and territories) provided updates to the program in any given fiscal year. Ensuring that its process for determining priorities reflects current threats, such as cyberattacks, and incorporates input from additional states would give CISA greater assurance that it and stakeholders are focused on the highest priorities. Here, with high emphasis on protecting various CI systems against cyberattack, EMP or terrorist intrusion GAO found three major sectors had adopted cyber defense strategies while others were mired in various stages of adoption or implementation. The chart below illustrates one dimension of the cyber risk issue as GAO depicted it. [GAO Report-105102, Adopting Cybersecurity Frameworks in Critical Infrastructure, Feb 2022] (Sharon, 2022)
Figure 5-1 Status of Cyber Security Framework Adoption by Critical Infrastructure Sector
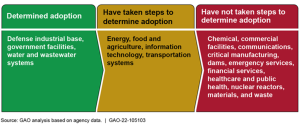
Source: (GAO-22-105103, 2022)
According to CISA officials, a National Critical Functions framework established in 2020 was intended to better assess how failures in key systems, assets, components, and technologies may cascade across the 16 critical infrastructure sectors. Examples of critical functions are shown below in CISA’s four broad categories of “connect” (nine of the 55 functions), “distribute” (nine), “manage” (24), and “supply” (13). Cascading systems failures and disruptions are especially significant from the standpoint of ensuring continued reliable and secure operations and the inherent risks that system collapse in one area triggers failure to other CI systems. Cascading collapse or failure in one CI system can adversely affect others. Traditionally, this cascading risk has most often been assigned to the energy grid. This chart illustrates the CISA scheme for arraying National Critical Functions (GAO-22-104279, 2022)
Figure 5-2 CISA Should Improve Priority Setting, Stakeholder Involvement, and Threat Information Sharing
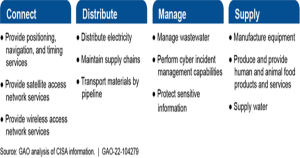
Source: (GAO-22-104279, 2022)
CISA is currently carrying out a process to break down each of the 55 national critical functions (such as “supply water”) into systems (such as “public water systems”) and assets (including infrastructure such as “water treatment plants”. In addition, the cascading shutdown dynamic which refers to energy loss triggering other dependent CI systems failing cannot be overlooked. This is a long, complex analytical process but includes consideration of selected factors deemed to place earth-based CI systems at greatest risk. These include
- Solar storms and geomagnetic waves [errant asteroids]
- Electromagnetic Pulse [EMP] weapons
- Terrorist attacks [physical or cyber]
- Insider threats/sabotage [criminal activity]
Today we must consider other potential threats to normal CI operations beyond that short list. That would include the emergence of sophisticated space-based weapons platforms which, depending on their inherent capabilities, could cripple or destroy selected CI systems. This would include space platform failures to protect friendly CI systems as well as hostile space-based attacks on CI. Before outlining these space-based threats, a routine inventory of CI systems is needed first. Here are the identified 16 CI systems which, as of 2021, CISA and DHS regard as bedrock value to homeland security.
In 2022, the specific array of diversified CI systems which DHS officially recognizes, and which are central and pivotal to our national and homeland security include the following major areas:
-Chemical/Petrochemical and Natural Gas Processing Facilities
-Energy systems and Energy producing organizations
-Nuclear Reactors/Nuclear Waste management
-Commercial/Business organizations and corporate enterprises
-Public Telecommunications/Internet Management/Voice-Phone-Data
-Defense Industrial Base [equipment/finished weapons systems, research & development, etc.]
-Critical Manufacturing organizations
-Dams, levees, flood control and seawall barriers
-Emergency Services Sector
-Public Health systems
-Food Supply/Agriculture
-Transportation/Trade/Shipping/Maritime and Port Security
-Financial and Economic Transfer services
-Key Government agencies and facilities
-Information Technology/Cyber Systems
Each distinct system has its own functional characteristics, operational norms, requisite technological and resource requirements, and aspects which raise issues of security and assured stability of continued performance in normal situations. Too often we reckon with calculated irony that every conceivable crisis scenario and set of demands affecting each CI system cannot be effectively deterred or nullified in all scenarios or circumstances. Clearly, those systems which are reliant on dependable energy sources and uninterrupted cyber and information/telecommunications technologies are most likely to require more robust and redundant security safeguards than other CI elements because they undergird and support the others. For example, the safety, security, and operational control systems which support and manage the daily activities of chemical plants rely heavily on reliable electric power and related energy sources to maintain the integrity of their various programs and functions. The photo below demonstrates just one small aspect of this CI system where safe and secure storage of finished and unblended chemicals enables the chemical industry to perform its ordinary work. (Nichols & Mumm, 2020)
Figure 5-3 Chemical Facility Storage Tanks [DHS-2018]

Source: (Primary) (GAO-20-453, 2020)
So, one paramount security issue to ensure the smooth and reliable functioning of CI systems is their ultimate reliance on energy regardless of threat, disruption, or extended crisis. External threats to that energy source where sporadic or reduced energy loads, or indefinitely cancelled energy supplies, jeopardize continued operations indicates a prime area where special protective measures, security system safeguards and threat nullification measures are needed. In many cases these adaptive security safeguards must be devised, engineered, and developed to fit the unique operational requirements of the specific CI system needing an upgrade.
CI systems reliant on consistently reliable cyber connectivity must also be considered. Earlier in 2022 Congress passed the Cyber Incident Reporting for Critical Infrastructures Act [CIRCIA] which marks an important milestone in improving America’s cybersecurity. While law does not eliminate all cyber risks and concerns it recognizes in our modern complex society is the ever-present risk of cyber warfare designed to disable and weaken an adversary prior to an all-out attack. The primary worry in a surprise cyber-attack is that there will be collateral damage to the critical infrastructure of allied and friendly countries not directly involved in the current conflict.
Today, services such as healthcare systems, power grids, transportation and other critical industries are increasingly integrating their operational technology with traditional IT systems in order to modernize their infrastructure. As such, these CI systems are open to a new wave of covert cyberattacks many of which are largely undetectable or preventable . The continuing conundrum of designing effective cyber deterrent measures and technologies against future cyber threats further complicates this risk terrain and makes estimations of evolving jeopardy to our own vulnerable cyber systems where AI and quantum may be involved is very serious.
While many businesses have ramped up their security initiatives and investments to defend and protect their own commercial interests, their efforts involving security upgrades and protective measures have been piecemeal, reactive, limited and lack uniform business context across all enterprises large and small. Further the digitalization of critical infrastructure, coupled with increased dependence on third parties, has made it vulnerable to ongoing cyberattacks across multiple vectors in a global network of shared communications. Supply chain attacks are becoming increasingly commonplace with several critical infrastructure businesses being compromised as collateral damage is inflicted or they become crippled by targeted ransomware attacks. These companies in various sizes now must monitor and manage employee workforce risk, third, fourth, criminal dark web intruders and other parties (not just their vendors, but their partners and suppliers’ networks, too), where the native technology stack, compliance, and regulatory frameworks, including internal policies and processes may be flawed or porous.
Vulnerabilities to cyber intrusion are several and experts agree those CI systems most at risk include energy, water, food supply, transportation, finance, and healthcare systems that are needed every day for national survival. Safeguarding these interconnected systems is crucial to assure national and homeland security against a daily onslaught of cyber probes and threats. The ability to disable and deny access to any of these resources is a massive threat to any country’s economy and its continued security and stability. Worse, cyber intrusions open the door to an attacker gaining control over space systems and networks, which could have devastating consequences. That attack could come from foreign enemies as well as determined terror groups.
Again, the energy grid in particular has often exhibited a frailty owing to risks of external cyber intrusion and influence. Fundamentally the energy grid, and all the other related CI systems which it supports, is the prime CI concern to achieve the highest reliability assurance possible against disruption, breakdown, and system loss. The energy grid is complex and diversified reflecting variety of designated zones for daily service. Extra high voltage (EHV) transformers are critical components of our nation’s backbone transmission grid. Approximately 90 percent of consumed power flows through the transmission grid and through such a transformer. These EHV transformers are very large, challenging to transport, and often have lengthy procurement times of one year or greater. There integral subcomponents include circuit breakers; isolators;– instrument transformers; surge arresters; neutral-earthing reactors; current-limiting reactors;
shunt reactors and capacitor banks all of them vital to secure continuous operations involving many EHV substations which may have several configurations (topologies), depending on continuity requirements, as well as the reliability and the quality of power supply. (electricaltechnology, 2018)
In addition to federally sponsored efforts many State and local entities have taken the initiative towards proactively assessing, prioritizing, and managing threats. Resources and options for investing incremental budget increases among all CI sectors is always constrained by shifting priorities. Both public and private sector organizations can share information and cyber defense best practices in critical infrastructure communities of interest, such as CISA’s Information Sharing and Analysis Centers. There are also many popular commercially backed exchanges where information can be shared specific to critical infrastructure threats. Cyber risk quantification, backed by sound data science principles, has a unique opportunity to help mitigate and solve this challenge. Two key steps involve information and technology management best practices, to include network segmentation, multi factor authentication, network access control, etc. Organizations also need to implement quantitative risk management, ensuring they are able to properly assess, prioritize, and manage their relative cybersecurity risks. (CISA, 2022)
(CISA) conducts specialized but voluntary security and resilience assessments on the CI systems to assist CISA and its federal, state, local partners—and private industry—to better understand and manage disruptive CI risks. The assessments examine infrastructure vulnerabilities, interdependencies, capability gaps, and the consequences of their disruption. Vulnerability assessments, combined with infrastructure planning resources developed through the CISA sponsored Infrastructure Development and Recovery program forms an integrated planning and assessment capability. This suite of capabilities, methods, and tools support the efficient and effective use of resources to enhance critical infrastructure resilience to all hazards
Because most U.S. critical infrastructure is privately owned, the effectiveness of CISA assessments depends upon the voluntary collaboration of private sector owners and operators. CISA’s Protective Security Advisors (PSAs) work collaboratively to foster and facilitate technical assistance to buttress of the security and resilience of the Nation’s critical infrastructure. Assessments are offered through the PSAs at the request of critical infrastructure owners and operators and other state, local, tribal, and territorial officials. The question is—what else about CI systems interacting with space-based platforms signals a security concern?
A Brief Excursion into Cyber/Satellite Attacks on CI
Several CI systems exhibit a degree of vulnerability to cyber/space systems intrusion and disruption. For example, nuclear plants are composed of an impressive number of components such as SCADA/ICS, sensors and legacy systems that could be hit by a hacker. The most popular case of a cyber-attack was against a nuclear plant launched in 2010 . Known as Stuxnet the attack involved malware developed by experts from the US and Israel with the intent of destroying or disabling the Iranian nuclear program. Hackers hit the plant of Natanz in Iran in 2010 interfering with the nuclear program of the Government of Teheran. The Stuxnet targeted a grid of 984 converters, the same industrial equipment that international inspectors found out of order when visited the Natanz enrichment facility in late 2009. IAEA inspectors noted, “The cyber-attack against the Cascade Protection System infects Siemens S7-417 controllers with a matching configuration. The S7-417 is a top-of-the-line industrial controller for big automation tasks. In Natanz, it is used to control the valves and pressure sensors of up to six cascades (or 984 centrifuges) that share common feed, product, and tails stations’. Stuxnet was designed with a number of features that allowed to evade detection; its source code was digitally signed, and the malware uses a man-in-the-middle attack to fool the operators into thinking everything is normal. Stuxnet proves it is possible to use a malicious code to destroy operations at a nuclear plant. Experts and authorities confirm a continued risk of future cyber-attacks exists, also involving satellite systems which can enable such attacks, against Nuclear plants. (Langner, 2013)
In 2021, two Russian COSMOS satellites in orbit were stalking a US spy satellite high above the earth. It wasn’t clear if they could attack U.S.-245, an American surveillance spacecraft, already in orbit. The incident passed, but it marked a new stage in the mounting arms race in space, where potentially bomb-armed satellites, laser-shooting spacecraft and other ‘satellite kamikaze’ technologies have moved from science fiction to reality. The stakes were made clear recently when Russia launched a missile from Earth and blasted to pieces one of its satellites in a show of force. (phys.org, 2021)
China has tested a maneuverable satellite that has demonstrated potential anti-satellite (ASAT) capabilities joining similar Russian efforts aimed at attacking US satellites, says a new study by CSIS. Recently the US used its X-37B spaceplane to covertly launch several CubeSats that could demonstrate its ASAT capabilities and practiced extensive GPS jamming during several naval exercises. And India joined the ASAT club as the fourth country to test a kinetic-kill ASAT, while France and Japan intensified exploration of new ASAT capabilities, according to the Center for Strategic and International Studies (CSIS). The three CSIS studies [2019,2020,2021] offer an analytical series which finds a major overall increase in the ability of nation-state space antagonists to threaten each other’s satellites, as well as an expanded number of countries pursuing ground- and space-based capabilities to damage or destroy satellite systems. For example, the 2021 CSIS report says the U.S. Space Force notes that, “military space forces should make every effort to promote responsible norms of behavior that perpetuate space as a safe and open environment in accordance with the Laws of Armed Conflict, the Outer Space Treaty, and international law, as well as U.S. government and DoD policy.” Counterspace weapons, particularly those that produce orbital debris, pose a serious risk to the space environment and the ability of all nations to use the space domain for prosperity and security. (Harrison, 2021)
These reports note that China, Russia, Iran, North Korea, India, France, Israel, UK, Japan, South Korea, all display diverse investments and enthusiasm for increased space platform launches and activity while major differences exist between them about adopting, let alone enforcing, norms applicable to satellite systems. Other CI systems are also clearly at risk as long as cyber avenues to their disruption are real and ever present. In contrast to nuclear plants, the idea that reliable access to water, especially the clean, drinkable kind, has become yet another CI battlefield. Security experts have noted that many national and local water and wastewater systems are extremely vulnerable to attacks by cyber criminals. In 2020, an unknown hacker or group of hackers was able to gain access to the operations technology (OT) system of a water treatment plant in Oldsmar, Florida attempting to poison the water supply by increasing the amount of sodium hydroxide, also known as lye, in the water from 100 parts per million to 11,100 parts per million. The attempt was thwarted by an operator who was able to reverse the change to the settings before the toxic levels of the chemical reached the water. In June 2021 NBC News claimed that a hacker attempted to poison a water treatment plant that served parts of the San Francisco Bay Area a few months earlier. (MaGill, 2021)
Finally, another example arising in Germany dealt with wind turbine operators reporting a fault in the satellite connection of their systems saying the remote monitoring and control of thousands of wind turbines had failed. The failure coincided with the Russian invasion of Ukraine making German officials suspect a Moscow-led cyber-attack. Instead, a spokesperson for the German Wind Energy Association said the disruption was due to the failure of the KA-Sat communication satellite belonging to ViaSat where turbine shutdowns appeared to be based. German wind turbine operators first reported the remote monitoring and control of thousands of wind turbines had failed due to suspected collateral damage from a Russian cyber-attack on a primarily military target. The KA-Sat network is also used by satellite communication service provider Euroskypark. Wind turbines in areas without mobile network coverage use satellite-supported communication for control and remote monitoring. Euroskypark could not be reached for comment. (Willuhn, 2022)
Grasping Space Systems and Platforms as New Critical Infrastructure
Today we must also confront another relevant CI system not officially listed with those which CISA/DHS have recognized as of 2022 but which reflect the shifting security environment of tomorrow—is space platforms and systems. During the recent 2022 Satellite conference, guest speaker Peter Hoene president and CEO of SES Government Solutions, a telecommunications services provider from Luxembourg said ‘…we are facing incredible threats from space-based systems,”. We must also recognize the Russia-Ukraine conflict illustrates how crucial the commercial space sector, multinational satellite communications companies, and those businesses that sell remote sensing data and images are part of tomorrow’s armed battles. . This would also include small businesses that supply space subsystems, launch companies, ground-station servicers, and cybersecurity support providers. With the successful launch of Space X many others followed suit.
The National Geo-Spatial Intelligence Agency declared years ago that it would buy space imagery from private sector companies. This changed the game board significantly. Remote sensing was once the purview of the military and spy agencies and less secretive NASA and NOAA for Earth observation causing the commercial space-data-as-a-service industry to explode in significance. With it, however, is an awareness of new threats. There is even the threat of “killer satellites,” maneuverable spacecraft that could potentially cripple spacecraft using robotic arms or destroy them with kinetic force. One challenge remains inside the private sector is the dicey question of protecting intellectual property and patented technologies which often prevents commercial space companies from sharing data on their respective vulnerabilities.
War and interstate conflict must include a cyber and space offensive dimension after 2020 knowing that states with the ability to execute attacks in both spheres will likely do so with impunity. The ViaSat company suffered an attack at the outset of the Ukraine war, which according to press reports, knocked out users’ modems throughout Europe. With the Ukraine war its government leaders warned of possible cyberattacks on domestic and international satellite systems with increased geopolitical uncertainty. Satellite systems are prone to a variety of threats and Russia amply demonstrated that in late 2021 by launching an anti-satellite test destroying a defunct spacecraft using an anti-ballistic interceptor missile. Space systems are also vulnerable to signal jamming, laser dazzling — which blinds remote sensing satellites — and cyberattacks, both in space and directed toward ground systems. (Magnuson, 2022)
Speaker Sam Costak, the national counterintelligence officer for space at the Office of the Director of National Intelligence said at the conference “While space is not designated technically as critical infrastructure, I think we can all agree that all of the critical infrastructure sectors rely on space…and the commercial space industry is just continuing to grow beyond what anybody ever thought would happen,” Commercial space system providers must be factored into the conversations because despite military systems used for surveillance, reconnaissance and communication the Pentagon uses less than 15% of the space assets orbiting our planet. Private sector space companies are looking to invest in more space systems if the Pentagon can provide leasing and security assurances. Costak also said, “.the government is currently taking steps to add space to its critical infrastructure list.” Back in May 2021, CISA formed the space systems critical infrastructure working group, designed to function as “a mix of government and industry members that will identify and develop strategies to minimize risks to space systems that support the nation’s critical infrastructure. (Magnuson, 2022)
In addition, a white paper released in 2021 by the Intelligence and National Security Alliance (INSA) calls for the formal designation of U.S. space systems as a new sector of U.S. critical infrastructure. Developed by INSA’s Cyber Council, the paper, Designating the U.S. Space Sector as Critical Infrastructure, notes that space systems have become vital to U.S. national and economic security even though space-related assets were not considered as one of 16 critical infrastructure sectors designated by the 2013 Presidential Policy Directive on Critical Infrastructure Security and Resilience (PPD-21). Space assets are now integrated into almost all essential sectors and functions, including defense, agriculture, transportation, energy, and telecommunications. Designating the space sector as critical infrastructure, the paper asserts, would enhance the resiliency of space-related assets and thereby make these other critical infrastructure sectors more secure. “Space-related capabilities have become essential to both national security and economic security, yet countries like Russia and China – which have advanced offensive cyber capabilities and anti-satellite weapons – have the potential to take them offline,” said Larry Hanauer, INSA’s Vice President for Policy. “Designating the space sector as part of the nation’s critical infrastructure would make it easier for government organizations, the military, and commercial space companies to share information on threats and vulnerabilities and thereby enhance the space sector’s resilience.” (INSA, 2021)
The space sector includes mission control, launch facilities, more than 6,500 satellites currently in orbit, [some active and some not] deployed by a wide range of companies and universities engaged in advanced research & development and technology deployment. Some experts predict the space industry will reach almost $1.5 trillion in value by end of 2030. Designating the space sector as the United States’ newest critical infrastructure sector would clarify government agencies’ roles and responsibilities in protecting it and make clear to U.S. adversaries that the United States is committed to defending its space infrastructure, contribute to the establishment of global norms regarding the safety and security of space systems, and accelerate development of best practices and technologies for ensuring cybersecurity and resilience of space. (INSA, 2021)
When CISA established the Space Systems Critical Infrastructure Working Group [SSCIWG] in 2021 CISA’s acting director Brandon Wales remarked, “The critical infrastructure on which the United States depends relies heavily on space systems. Increasing the security and resilience of space systems is essential to supporting the American people, economy, and homeland security. Secure and resilient space-based assets are critical to our economy, prosperity, and our national security,” He also said, “This cross sector working group will lay the foundation for our collective defense against the threats we face today and in the future.” noting, “this working group will serve as an important mechanism to improve the security and resilience of commercial space systems. It will identify and offer solutions to areas that need improvement in both the government and private sectors and will develop recommendations to effectively manage risk to space based assets and critical functions.” (CISA, 2021)
Further at a conference in October 2021, an experts panel discussed the need to consider space systems as part of our nation’s critical infrastructure due to its unique technologies and capabilities combined with its interdependence with other critical infrastructure sectors. Dawn Beyer, senior fellow at Lockheed Martin, was quoted saying “We’re still debating whether space is critical infrastructure, meanwhile of all the domains, space is the furthest behind when it comes to cybersecurity.” Samuel Visner, technical fellow at MITRE and member of the ISAC board of directors, noted that “Our adversaries see space as critical to their national interest, they see space as critical to our national interest, and frankly I think they see it as a vulnerability to our national interest that they can exploit.” (Bahr, 2021)
Recognizing the value of supporting and reinforcing space-based systems which undergird CI systems is important however, beyond that fact is the issue of increasing dependency of CI systems on space platforms and the extent to which those platforms can be arrayed to target and disable CI systems as a prelude to war or other armed conflict This is much less well known and examined and will be the subject of discussion later in this chapter.
Greater Dependency of CI on Space Systems Creates New Security Concerns
Space assets require protection from extremely hostile environments where ground-based attacks, attacks from other space platforms, and cyber enabled attacks originating anywhere can happen frequently and without warning. . Attacks from cyber-space can be shown to be as harmful to spacecraft, and to their ground-based data and support systems, as radiation belts and temperature extremes have always been. To the extent that certain space systems and platforms are the targets of disruptive cyber-attacks reinforces the notion that CI systems are also in some indirect jeopardy from those cyber probes. Some examples years ago of adversarial cyber activity against space assets found in the open literature include:
–“On July 23, 2008, Landsat-7 experienced 12 or more minutes of interference. The responsible party did not fulfill all steps required to command the satellite.”
— “On October 22, 2008, Terra EOS AM-1 experienced nine minutes of interference. The responsible party fulfilled all steps required to command the satellite but did not do so.”
–“On June 2012, a Romanian national known as ‘Tinkode’ pleaded guilty in Romanian court to charges of illegally accessing numerous NASA systems as it seems the Pentagon, the Romanian government, and U.S. commercial entities were also involved in the case
In 2014 the Director of National Intelligence wrote in particular about space: “Threats to US space services will increase during 2014 and the decade beyond as potential adversaries pursue disruptive and destructive counterspace capabilities’ Chinese and Russian military leaders understand the unique information advantages afforded by space systems and are developing capabilities to disrupt US use of space in a conflict. For example, Chinese military writings highlight the need to interfere with, damage, and destroy reconnaissance, navigation, and communication satellites. China has satellite jamming capabilities and is pursuing antisatellite systems. In 2007, China conducted a destructive antisatellite test against its own satellite. Russia’s 2010 military doctrine emphasizes space defense as a vital component of its national defense. Russian leaders openly maintain that the Russian armed forces have antisatellite weapons and conduct antisatellite research. Russia has satellite jammers and is also pursuing antisatellite systems.” (Byrne, 2014)
The key issue of satellite controls raises three risks that must be mitigated: (1) the potential for an adversary to remotely introduce a false satellite command; and (2) the potential for an adversary to prevent the satellite operator from transmitting daily commands or receive telemetry from the satellite; and (3) an adversary could wrest hostile extended control of satellite systems from their owner/operators using cyber or related interventions. ” Unfortunately, specific, detailed, information about particular incidents are hard to find in the open literature including- details describing the exact commands issued by the adversary, or the various avenues of cyber access to the space system environment at the time of the attack. Worse, limited post incident forensics often make it extremely difficult for defenders to construct a viable defense for their own space systems. Regrettably, asserting that existing controls will protect against current and future risks, or that all vulnerabilities have been remedied is sometimes accepted without reasonable supporting data. Worse, it is accepted where the lack of data is used as proof. It is important to note that as the cyber-threat environment changes, cyber defenses need to be implemented or adapted to keep pace. This can only get more complicated with the onset of quantum computers and their unhackable attributes. Cyber-attackers of today and tomorrow are malicious, persistent, and evolve their attacks over time. By contrast, radiation doesn’t change the way it attacks materials after you’ve chosen your shielding. Continual study of changing adversarial actions with respect to the operational needs of a mission is an important process that must supplement the more static failure model approaches currently prevalent in mission design. (Byrne, 2014)
Cyber Defense architectures, designs, and mitigation strategies must be evaluated against a range of conditions that reflect the existing and expected threat environment and cannot be static or adopt the ‘one size fits all’ philosophy. Whatever verification activity is adopted it must cover at least these attributes: [1] Range of conditions (not just single or “best case” points); [2] Observable behaviors; [3] Comparable observations; [4] Repeatable tests; and [5] worst case scenarios. Test demonstrations must raise awareness that existing fault containment zones were inadequate in providing protections, contained gaps, or did not operate as originally intended, to provide. Considering a normal systems assurance lifecycle featuring development, integration & test, and conventional operations. Tests must be robust enough to reveal a potential security breach or an exploitable weakness in a given system. Hopefully, these tests will help identify where in the systems testing and demonstration phases that existing security controls had gaps in their coverage. This is technically tough but not impossible and consideration of using red team penetration exercises to identify and root out weaknesses ought to be considered.
There is also the ever-present threat to space platforms and systems from EW [electronic warfare] technologies. This would include identification, interception, and characterization [friend or foe analysis] of deliberate or unintended electronic warfare signals and pulses. These EW considerations would also include aspects of false targeting, uplink or downlink interference, phantom or duplicate target generation, faux surveillance, degrading radiation and signal jamming. EW spoofing attacks launched via cyber mechanisms can cause GPS receivers to provide the wrong information about satellite position, time, and signal coordinates. Mitigation and defense measures can include masking, hardening and engineered deterrence subsystems.
Space and Satellite Systems and Platforms can Monitor CI
Satellite technology plays an important role in the monitoring of and response to infrastructure problems. For example, heavy machinery at ground level that’s in the wrong place where disasters or hazards occur can be identified before major damage is done. Some examples which illustrate the infrastructure monitoring value of satellites include:
Communications. Satellites are integral to support global communications systems especially in a remote area or if the client needs a redundant communications plan to avoid loss of connection and its wide coverage radius allows connectivity with otherwise inaccessible locations.
Optical images. Optical sensors perform like a camera sensor capturing high resolution images for photography–or low-resolution options–where the distance between pixels equals more than 100 feet, while others can capture a distance of less than three feet between pixels. However optical sensors can’t penetrate cloud cover or capture images in darkness since they rely on reflected light. This makes them unreliable during changing weather conditions and at night.
SAR images Synthetic aperture radar sensors operate on a higher frequency in the electromagnetic spectrum versus optical sensors. They transmit microwaves and measure backscattered radiation that is received analyzed and pictured as a two-dimensional image. The main advantages of SAR are its abilities to see through cloud cover and capture images in the dark.
Thermal images. Thermal image sensors capture infrared radiation from the Earth using a spectrum of colors based on temperature differences. Thermals have proven value in monitoring power lines, but often space based spatial resolution is much less precise than small aircraft (plane, helicopter, or UAV), which deliver much higher resolutions. They are also useful also in tracking changes in the composition of the land or pinpointing sudden changes observed around the infrastructure’s general location to predict threats or risks which can be natural or man-made. Some specific applications of these space systems include
Pipeline monitoring. When oil and gas pipelines are buried 5 feet underground often, they are. vulnerable to construction accidents which can trigger a majority of gas pipeline failures. With well over 2 million miles of pipeline in the world, using ground-based solutions or small-craft aerial images is without real value and infeasible. Imaging satellites provide wide coverage and high-resolution alerts to companies tracking macro changes in physical pipelines – i.e., explosions, damaged segments, or ground movements – so that fixes can be made quickly.
Power line monitoring Utility companies which routinely monitor the health of power lines in their service area or to offset risks of major downtime can use aerial images used by companies to make decisions regarding maintenance of power line conductors with a reported rate of 90% accuracy. When paired with new, powerful AI image analysis software, future decisions could become more efficient and incorporate a high degree of automation, lowering response times.
Railway monitoring. Finding significant weaknesses or deformation along railway tracks is crucial to reduce the potential for disastrous consequences. SAR satellites can track extremely precise changes over enormous distances enabling random scanning of construction accidents quickly. SAR satellites can identify rail gaps and deformations which merit immediate attention. (Morgan, 2020)
Reckoning with the vulnerability of satellite communications to cyber manipulation is critical to grasping their contributing role in assuring CI stability of everyday operations. GPS and related geo-location services rooted in satellites illustrate one prime security concern. Increased deployment of satellites have left space-based assets a target for hackers looking to compromise sensitive information, for terrorist, criminal or hostile nation aims with potentially devastating consequences. With the stakes so high when it comes to protecting the data that satellites carry, security cannot be an afterthought and it must play an integral part of the design process itself.
Satellite ground technology is also advancing with more innovation and scalability, as it looks to leverage virtualization, orchestration, and network splicing to support 5G connectivity. Software-defined satellites that can be reprogrammed to move capacity based on market demands create additional problems. With many new 5G and IoT applications these connections open up potential doors for hackers making satellites the new gateway. This jacks up the requirement for smarter satellite security and protection from hackers. There was a time when satellites seemed almost untouchable, but today’s hackers can purchase and operate the right equipment such as an antenna at a satellite and send communication to it and influence its normal operations.
Security is the most significant area of technical concern for most organizations deploying IoT systems and now 5G networks, with multiple devices connected across networks, platforms, and devices. This is also true for satellite, given the size and scope, as well as the number of earth station access points. The rise in IoT means if one single device isn’t encrypted or the communication isn’t protected, a bad actor can manipulate it and potentially a whole network of connected devices. It isn’t just the devices themselves that need to be protected, but it is also every stage of data transmission too.
A key first step is for organizations to understand the vulnerabilities they have and how they can be exploited such as legacy satellite communications that are not easily updated. Significant testing must be completed to ensure upgrades for communication with next-generation platforms will not interfere or impact other key system functions. Weak encryption and old IT equipment are key vulnerabilities for satellite networks, which are a prime target for hackers to exploit. So, for over 1,500 satellites in orbit today encryption and other network security measures are essential and enable communications to be authenticated at every stage of data transmission between earth-bound devices and satellites. For authentication to work as designed enabling devices must meet compliance requirements at the networking level to safeguard data when traveling across the satellite ecosystem.
Real-time security solutions are essential because any that do not operate in real-time offer hackers an infiltration route allowing them to be in and out in seconds. Satellites play foundational roles in GPS, time validation , geolocation, weather, traffic, ATMs, video conferencing, TV and radio, inventory control, pay at pump gas stations, phone and broadband, air traffic control systems, sea navigation systems, and the vehicle navigation features used in our cars. Many countries routinely use satellites in these primary areas: Intelligence, Surveillance, Reconnaissance and Remote Sensing; Communications; Navigation and Science and Technology. As of 2020 the array of nearly 900 US owned and operated satellites include: 353 for Intelligence, Surveillance, Reconnaissance and Remote Sensing; 391 for communications; 7 for Navigation and 94 for Science and Technology.
Figure 5-4 Competing in Space, National Air and Space Intelligence Center. Jan 2019
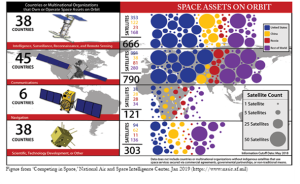
Source: (NASIC, 2022)
Taking a Look at UUV/Underwater Threats to CI
It is important to recognize the additional unseen threat which UUV [Unmanned Underwater Vehicles] systems pose to CI whether or not their eventual connectivity to space systems can be verified and tested. Overall capabilities linking UUVs with other UAV, satellite and related space-based platforms is not beyond the scope or pursuit of finding engineering technologies which permit operational linkages. Here are just two examples where subtle threats to port CI and related CI systems is within the realm of realistic risk.
[1]-China’s once-secret unmanned underwater vehicle (UUV) may have been tested already in the strategically vital Taiwan Strait, back in 2010. These revelations come from a military-funded research program that was partly declassified recently, according to the South China Morning Post. The UUVs in question have the ability to recognize, follow, and attack enemy submarines without human instruction and conduct harbor surveillance. It was developed by the Harbin Engineering University, Beijing’s top submarine research institute. The same article also raises the possibility of a variant of the sub that could be planted on sea floors and activated in the event of a clash or war. The concept seems to be based on using artificial intelligence (AI) technologies to identify and track submerged targets, promising results better than human sonar operators. Sonar operators still need to use their eyes and ears to make judgments on important issues such as identifying friendly vessels, with final decisions taken by the captain, the article asserts. (Kongsberg Gruppen Maritime, 2021)
[2]Threats to our critical infrastructure and vessels are on the increase. Combat divers and now a new generation of underwater drones, are known risk factors. These threats are evolving and in parallel the technology required to detect, track, and identify the threats is also evolving technology uses active sonar elements to insanity an area and then analyses the return signals. Typically deployed in shallow waters and with a requirement to detect threats as far as possible, the design of the instrument must consider carefully the challenges imposed by confined areas, such as complex sound velocity profiles, multipath effects, and shadow zones. The most successful sonars use a circular transducer configuration to ensure even coverage. The sonars track and analyze targets’ behavior to discard false alarms. They are widely deployed today to protect harbors, critical infrastructure, and private property. Navies are equipping corvettes and patrol vessels to help protect their ships, for instance while docked overseas, or to provide a deployable detection capability. (Tena, 2019)
Spaced Based Systems as Actual Space Weapons Threats to CI
Space is a recognized domain of future warfare and conflict. Back in 2007, China demonstrated how space can become a combat zone by conducting an anti-satellite mission test. The country shot down its own weather satellite with a kinetic kill vehicle. It was just a weather satellite – their own satellite. Here was the unmistakable and clear message to the rest of the world: –satellites can be destroyed from Earth, and at least one nation can do it. Space technology and services represent a major component of advanced societies and their inherent infrastructure. At the same time, space technologies and services lay in the vastly unsettled area of legislative and institutional measures, leading to a growing ambiguity among professional community, reunited under the concept of ”space traffic management” (STM). STM seeks to address the tension between governmental and private initiatives related to the management and the coordination for space traffic, in short, reconciling the problem of space weather phenomena, space debris and near-Earth objects along with projected future launches. At the same time, STM analysis also considers the development of anti-satellite weapons and other forms of space warfare. (Janosek, 2020) (Botezatu, 2020)
The Joint Chiefs of Staff, according to the NIPP [National Infrastructure Protection Plan] report, has warned that space conflict “will be intense, highlighted by satellites maneuvering to hinder the operation of other satellites, co-orbital jamming, and the use of ground-based lasers to dazzle or destroy imaging sensors.” Space attacks will include the use of anti-satellite (ASAT) weapons launched from the ground and orbiting weaponized satellites that could create large debris fields and possibly produce a chain reaction that would destroy other orbiting systems. Electronic jammers and dazzlers will be used to disrupt or impede the functioning of key satellites, such as GPS navigation and communications systems. Electronic jamming, uplink and downlink attacks, spoofing, directed energy, and lasers. (Lambakis, 2018)
Consideration of various space systems and platforms includes reckoning with orbiting systems which have been in their respective paths for some years as well as likely newcomers to the crowded zones and operational areas where emerging space weapons threats must be evaluated comparatively as many system capabilities are covert and classified. Space based platforms and systems which pose a security dilemma for most CI subsystems include a variety of well-known and sometimes vague orbiting mechanisms which merit a closer look. We must consider a variety of space-based systems which symbolize a range of potential threats to CI
Particle Beam systems accelerate particles without an electric charge—particularly neutrons—to speeds nearly at the speed of light directing them against a target. The neutrons knock protons out of the nuclei of other particles they encounter, generating heat on the target object. This technology offers a “heat ray” or “death ray” option unlike lasers, which burn the surface of a target. Instead, particle beams penetrate hover in orbit against satellites or enemy missile attack burning beyond the satellite’s surface to disrupt, melt and adversely affect its interior. Such beams are immune to measures that can deflect lasers generating enough heat to burn a target, ignite its fuel supply, render it aerodynamically unstable, or fry an oncoming missile’s onboard electronics. Particle beam weapons include both charged particle beam (CPB) weapons and neutral particle beam (NPB) weapons. Charged particle beams do not propagate in straight lines in outer space because of the Earth’s magnetic field. Because of this, their utility in the ASAT role appears limited. However, neutral particles can propagate long, linear distances in outer space. In late 2019 however U.S. Undersecretary of Defense for Research and Engineering Mike Griffin recently told a gathering of defense reporters, “We are deferring work on neutral particle beams, indefinitely. It’s just not near-term enough.” Griffin emphasized however that the Pentagon was still forging ahead with research into lasers and microwave weapons, for use by ground forces, air forces, and in space. With regard to that development there are no guarantees that despite what the US does, or declines to do, many hostile military forces have rejected the idea of jettisoning this technology or delaying its development. (Tucker, 2019) (Nichols & Carter, 2022)
High Energy Lasers high-energy laser systems use photons, or particles of light, to carry out military missions and civil defense. Directed energy [DE] technology enables detection of threats, tracking during maneuvers, and positive visual identification to defeat a wide range of threats, including unmanned aerial systems, rockets, artillery, and mortars. High energy laser weapon systems work on land, in the air and at sea, providing 360-degree coverage that protects bases, airports, stadiums and other high-value military or civilian targets against missiles, and even drone swarms. Laser systems, including coherent radiation, aligned waveform, and other devices operating at or near the optical wavelengths, operate by delivering energy onto the surface of the target. The gradual or rapid absorption of this energy leads to several forms of thermal damage. Its ruggedized packaging means it can be used as a standalone system or rapidly installed on a variety of military platforms. Full installation and testing on select combat vehicles as well as helicopters has shown its operational value.
Kinetic-Energy Weapons Kinetic-impact weapons include a wide variety of systems which can cause structural damage by impacting a target with one or more high-speed densely packed masses. Small pieces of kinetic debris can inflict substantial damage or destroy a satellite. In January 2007, China successfully tested a direct-ascent, kinetic-kill ASAT vehicle, destroying an inactive Chinese Feng Yun 1C (FY-1C) weather satellite (launched in 1999). The satellite was in a polar orbit at an altitude of 865 km (537 miles) and was attacked when it passed over the Xichang Space Centre in Sichuan Province. The satellite broke into more than 900 pieces, generating more debris. The launch vehicle was probably a mobile, solid-fuel KT-1 missile, a version of the DF-21 medium-range ballistic missile (MRBM), with a range of 1,700 km to 2,500 km, although according to some accounts it was a KT-2, also mobile and solid fuel, based on DF-31 intermediate-range ballistic missile (IRBM)/intercontinental ballistic missile (ICBM) technology, with a range of more than 6,000 km. The launch vehicle and warhead were guided to the target by ground-based radars. (SPACE, 2016) (Nichols & Carter, 2022)
EMP weapons Recently Chinese engineers brought down a large, unmanned aircraft using a new electromagnetic pulse-type weapon in what could be China’s first test of its nascent venture into advanced EMP weaponry. New reports say the test reportedly concentrated a powerful beam of electromagnetic energy on the unmanned aircraft during its flight at 1,500 meters, or nearly 5,000 feet in altitude. The aircraft “did not drop immediately but veered abruptly from one side to another for a period. Flight data and analysis of debris recovered from the crash site suggested that sensitive electronic devices, including its satellite navigation system, cryoscope, accelerometer, barometric altimeter, and communication device, had not been damaged. The battery and motors also functioned properly until collision.” In all likelihood, the aircraft’s “flight control system malfunctioned, issuing an error control command,” an engineer involved with the live-fire event explained. Unlike kinetic or explosive weapons, electromagnetic pulse-type weapons rely on ‘frying’ electrical systems, rendering them useless. Thus, airplanes, drones, trucks—anything that relies on onboard electronics are vulnerable unless specifically hardened against EMP threats. (Chen, 2021)
KA Band Weapons Chinese researchers have developed a microwave machine named Relativistic Klystron Amplifier (RKA) which can jam and destroy satellites in space. A Taiwan News agency recently reported. The RKA can generate a wave burst measuring 5-megawatts in the Ka-band. The Ka-band is a portion of the electromagnetic spectrum which is used for civilian as well as military purposes. It may not be able to shoot targets out of the sky from the ground, but it can be mounted onto satellites and used to attack enemy positions in space by frying their electrical components. Experts at US based think tank Centre for Strategic and International Studies (CSIS) told the Taiwan Times that these developments should force the United States to deploy space-based sensors to counter the Chinese military’s new missiles. China denies that the RKA is a directed energy weapons (DEW) system. A DEW system used concentrated electromagnetic energy rather than kinetic energy to destroy enemy equipment and personnel, news agency ANI explained. The Taiwan News report expressed concern that if RKA turns out to be a DEW it can rip apart metallic materials moving at speed. (TAIWAN News, 2022)
Microsatellites and Nanosatellites We already know that microsatellites (microsats) can target US commercial space systems because they offer the opportunity for a broad range of newer countries to enter space using off-the-shelf hardware to build inexpensive satellites and very affordable launch options to place them into orbit. Currently at least 40 countries have demonstrated some ability to design, build, launch, and operate microsats. Used offensively, maneuvering microsats can inspect and interfere with operations of orbiting assets. India, Russia, China, and Japan all have the ability to launch microsats as secondary payloads to low Earth orbit (LEO) and geosynchronous Earth orbit (GEO). “Parasitic” microsats/nanosatellites could also be launched inside the structure of primary payloads without the knowledge of the launch provider and deployed without detection. There is a significant risk that criminals, terrorists, or nation-state hackers can covertly enter a company’s network to disable satellites or steal intellectual property such as satellite designs or software. For decades, government agencies or multinational corporations controlled the vast majority of satellites, and many of those satellites were as large as school buses. Data was received and commands were sent through private networks backed by sophisticated security apparatuses. Now, small, and obscure startup companies can hook up simple microsatellites (weighing 10 to 100 kilograms) to the internet for affordability and the convenience of customers. Today some imagery, weather data and communications bandwidth are delivered this way. “Microsatellites are completely driven by software and completely networked. That’s where the vulnerability comes in,” For example, as some experts have warned a private firm’s vulnerabilities are embedded on its internet reliance. They warned that an employee on an overseas trip could unwittingly create a conduit to the company’s satellite constellation and blueprints by firing up a laptop on public Wi-Fi. So, employees are no longer allowed to bring their work laptops on many such trips. Instead, they travel with blank laptops containing no information about the company or its satellite.
Likewise demand for microsatellites and nanosatellites is increasing significantly in the recent years. According to nanosats.eu, as of January 2021, more than 2,900 nanosatellites were launched in the earth’s orbit. Companies across the globe are launching constellations of nanosatellites or microsatellites in the earth’s orbit for earth observation and telecommunication applications such as high-speed space-based internet services. For instance, in January 2020, Sateliot, a Spain-based nanosatellite and telecommunications operator, signed a Memorandum of Understanding (MoU) with the European Space Agency (ESA) to analyze, develop, and implement innovative technologies, products, and services with space capability using 5G. The company is planning to invest around 100 million Euros to launch constellation of 20 nanosatellites for hybrid terrestrial space networks, 5G network architecture, spectrum management, and spectrum exchange. constellation. Microsatellites and nanosatellites are more cost-effective than traditional satellites and usually developed for communication, commercial, and space research purposes. The demand for these satellites has increased significantly since 2015 owing to their lightweight attribute, shorter development cycle, high capability of performing complex computational tasks, and lower cost for development and launch. Major and upcoming companies, such as Planet Labs, GomSpace, Sierra Nevada Corporation, among others, are launching constellations of micro and nanosatellites to offer near real-time remote sensing data for government and commercial clients. (Werner, 2019)
Directed-Energy Weapons Include laser, RF, and particle-beam weapons often seen collectively as “standoff” weapons because they are primarily either ground- or air-based systems many miles from their target. Most of these concepts are technically sophisticated and attack the target from longer ranges than most kinetic interceptors. In addition, these technologies are capable of engaging multiple targets, whereas interceptors tend to be single-shot systems. Additionally, if the geometric conditions are right, directed-energy weapons can acquire and attack their targets in seconds, whereas kinetic-interceptor engagement times tend to be much longer. Finally, standoff directed-energy weapons provide the enemy with a degree of deniability. This is because the attack is relatively quick—probably no intelligence indicators associated with it—and because the degradation of the target spacecraft may not be immediately apparent, making it difficult to figure out when and where the attack actually occurred. (Nichols & Carter, 2022)
Radio Frequency Weapons. RF weapons concepts include ground- and space-based RF emitters that fire an intense burst of radio energy at a satellite, disabling electronic components. RF weapons are usually divided into two categories: high-power microwave (HPM) weapons and ultrawideband (UWB), or video pulse, weapons.16 UWB weapons generate RF radiation covering a wide frequency spectrum—nominally from about 100 MHz to more than 1 GHz—with limited directivity. Because of the UWB weapon’s low-energy spectral density and directivity, permanent damage to electronic components would be very difficult to achieve, except at very short ranges. The UWB enters through the satellite’s antenna at its receive frequency, as well as through openings in the system’s shielding. If enough power is applied, the received radiation may cause major damage to the satellite’s internal communications hardware. However, in many cases, UWB weapons will simply cause system upset, which may persist only while the target is being irradiated or may require operator intervention to return the satellite to its normal state. Most frequently an RF weapon uses radio waves at power levels high enough to cause electrical disruption. Microwaves (high-frequency radio waves) are usually preferred, so this type of device is sometimes called a High-Powered Microwave, or HPM weapon. RF weapons also overlap generally with Electromagnetic Pulse, or EMP weapons, which emit a powerful burst of radio waves in all directions. Unlike jammers, which just interfere with the signal received by radios or radar, radio frequency weapons do actual damage. They do this by two methods: ‘front door coupling’, where radio waves are picked by the antennas and aerials normally used for receiving, and in ‘back door coupling’, where wires inside the electronics act as receivers resulting in an extremely powerful pulse is to put far more current through a component than it can handle. (Nichols & Carter, 2022) (Hambling, 2019)
Orbital interceptors. These weapons are typically ground- or air-launched into intercept trajectories or orbits that are nearly the same as the intended target satellite. Radar or optical systems on board the satellite guide it to close proximity of the target satellite The variety available include : [1] Low-Altitude, Direct-Ascent Interceptors launched on a booster from the ground or from an aircraft into a suborbital trajectory that is designed to intersect that of an LEO satellite. Because these interceptor systems are on a direct suborbital trajectory, the on-orbit lifespan of these systems is measured in minutes, making them the simplest type of interceptor weapons to design, build, and test; [2] high-altitude, short-duration weapon is an interceptor that is launched from the ground into a temporary parking orbit from which it maneuvers to attack a high-altitude satellite. Because these interceptor systems enter a temporary parking orbit, the on-orbit lifespan of these systems is measured in hours, which makes them slightly more complex than direct-ascent; and [3] Long-Duration Orbital Interceptors are launched into a storage orbit for an extended period of time, possibly months to years, before it maneuvers to engage and attack the target satellite. The weapon may be stand-alone or covertly placed on or in a “mothership” satellite. Orbital choices include farsat, nearsat, space mine, fragmentation or pellet ring, and space-to-space missile. Farsats are parked in a storage orbit away from their targets and maneuver to engage them on command. Nearsats are deployed and stay near their targets to inspect and attack on command. Space mines are parked in orbits that intersect the target’s orbit and are detonated during a periodic close encounter. Fragmentation or pellet rings are vast quantities of small, non-maneuvering objects that are dispersed from one or more satellites in such a way that an artificial Earth-orbiting ring is created. Satellites flying through the ring are damaged or destroyed. Space-to-space missiles are rocket-propelled interceptors launched from an orbiting carrier platform into an orbit that intercepts the intended target. Presently, there is no existing treaties or other specific international law that bans states from deploying conventional weapons in space, including the use of interceptor missiles. (Harper, 2017)
ASATs [Anti Satellite Weapons] Diverse nations are aware of and intend to deploy sophisticated ASAT systems in anticipation of the space frontier as explicit future battlefield. Many nations plan to use microsatellite technology to develop and deploy long-duration orbital ASAT interceptors. Beijing’s decision to develop and deploy the ASAT system has both long-term and short-term strategic objectives. The long-term objectives are to establish a strategic balance among the larger nations, and to break up the monopoly on utilization of space that large space systems of the superpowers are holding; thus, weakening their capabilities in information warfare. In the short-term China would strengthen its capabilities in controlling the usage of space globally and change drastically the Chinese-American military balance so that the U.S. would not intervene easily in the event of a conflict in the Taiwan Strait and at the Chinese perimeter. One can expect a continual growth and development of ever increasingly sophisticated ASAT systems. On Nov. 15, 2021, Russia tested and demonstrated an anti-satellite weapon (ASAT) system by destroying one of its inactive satellites at an altitude of about 300 miles above the earth’s surface. At this altitude, the satellite’s debris will orbit the Earth for a long time. The United States has identified more than 1,500 pieces. Russia may have calculated that in the context of rising great-power rivalry, especially between the United States and China, the growing trend of space weaponization is the future of warfare. At the same time, this trend of weaponization opens the door to stringent space regulations that will limit the development and use of these capabilities. Displaying technological capability before new international regulations are created can be valuable for both national security and political reasons. By destroying its satellite in space, Russia achieved two objectives. It enhanced its defense and deterrence capabilities, and also projected its power before testing, demonstrating, and using ASAT capabilities could be prohibited or significantly restricted by international mechanisms. Additionally, Russia has ensured that it will be a significant party in any major international regulatory process by publicly possessing such a capability. (Paikowsky, 2021)
The overall threat these various space-based weapons systems and platforms pose to the energy grid, reliable and potable water, farm to market food supplies, public health, transportation, emergency services and the industrial/commercial base of a nation’s daily operations cannot be underestimated. It will require serious and sustained research efforts after 2022 to devise defensive, protective, and deterrent countermeasures and security practices to safeguard what major CI systems are deemed essential to normal and routine daily life in those advanced nations which demand their reliable and uninterrupted operation.
Counter Space Operations, Countermeasures and Protection of Space Systems
Because commercial and military satellites, and related space systems, are equally crucial for national defense, reliable industrial and commercial operations, as well as being part of a nation’s critical infrastructure their secure and stable operations must be protected against a variety of threats. Threatening or attacking a nation’s space capabilities would have domestic, economic, and political consequences and could provoke international disputes about the origin and intent of an attack and likely bring nations to the brink of open warfare. Such ambiguity and uncertainty among nations experiencing degraded satellite performance and security would trigger a crisis of national safety and survival. Risks of misinterpretation arising from lengthy lapses in secure satellite operations could accelerate national security crises rapidly and permit victimized nations to consider the advent of a surprise attack if absolute confidence in control of friendly platforms was deemed ambiguous, unreliable, or unconfirmed.
There are a number of possible crises or conflicts in which the potential vulnerability of national security space systems would be especially worrisome. During these situations, national leadership and its senior military commanders and civilian advisors would be dependent on information from satellite systems to help manage the crisis, conduct military operations, or bring about a resolution to the conflict. A real time damage assessment which depicted the status of friendly platforms and satellites would be essential along with a discerning capability to determine which systems were inoperable or compromised. If the performance of any of these. systems were reduced, the geostrategic influence and leverage of the jeopardized nations could decline rapidly. In addition, the geostrategic position of an opportunistic and determined adversary could be vastly improved, and the risks of strategic blindness or dissolving confidence in friendly space systems would be enormous tilting in favor of the attacker or party exerting operational influence over home nation satellites and systems.
Strategic miscalculation and error would be part of the ongoing crisis climate until or unless nations could restore positive control over their own orbiting space systems. The sheer opacity and technical uncertainty of verified satellite systems control in such a crisis could create conditions which would diverge among some leaders who would require further confirmation of trouble and await an update versus those presuming the worst case and launching their own pre-emptive attack on suspected enemies based on a feeling of diminished security.
Countermeasures such as hardening, mobile ground control stations, autonomous operations better threat analysis, targeting hostile space systems, creating orbital redundant nodes, randomized platform maneuverability, deploying decoys which simulate the radar and optical signatures of the satellite are all effective to some degree. In the age of quantum and deceptive cyber controls no guarantee of foolproof self-defense systems exist. Shrewd enemies with technical skills can covertly capture or control satellites unless measures are devised to nullify or neutralize satellite operations based on periodic security code transmission updates. Nevertheless, demands for upgraded defensive measures, including methods for neutralizing platforms at will, or detecting immediate operational threats are more engineering issues than reality. Here the priority and national security burden is placed equally on military and commercial satellite owners and operators.
It is important to reckon with some of the things that could go wrong and understand the security implications attached to each. For example, the potential impact of deception, disruption, denial, degradation, or destruction of specific space systems by foreign offensive counterspace operations designed to erode, weaken, or nullify friendly platforms include:
- Impairment or elimination of reconnaissance satellites that would reduce situational awareness and could lead to military surprise, underestimation of enemy strength and capabilities, less effective planning, and less accurate targeting and battle damage assessments.
- Impairment or elimination of missile launch detection satellites that would degrade the US’s ability to perform missile launch warning, GPS targeting, missile defense, and would increase the psychological impact of the adversary’s ballistic missiles.
- Impairment or elimination of satellite communications systems that would disrupt troop command and control problems at all force levels.
- Impairment or elimination of navigation satellites that would make troop movements more difficult, aircraft and ship piloting problematic, and could render many precision-guided weapon systems ineffective or useless.
- Impairment or elimination of Earth resource and weather satellites that would make it more difficult to plan effective military operations.
IT Vulnerability in Space Systems and the Importance Of Penetration Testing for CI
Penetration testing plays a key role in preemptive cybersecurity. Leadership at water districts, power plants and other critical infrastructure can no longer think “it will happen to others, but not us.” They’re seeing the impacts of successful attacks in the news and a correlated rise in their cyber insurance premiums. Penetration testing will continue its growth because the people in charge are humbler about their current safeguards and the scope of attacks. They’ve accepted that if they do a good job at running a plant or other facility, then someone out there is interested in compromising their hard work, whether it’s for ransom, intelligence gathering or simply promoting chaos. Penetration testing is a vital part of a critical infrastructure assessment that allows all parties to assess risks and implement cybersecurity mitigations and standards. Looking for a broad range of problems, such as software vulnerabilities, network issues and even things like phishing schemes and other human-based attacks are part of it. Penetration testing is not a new practice, but it’s heightened now due to the increase in nation-state attacks and people seeing successful attacks like Colonial Pipeline.
Today critical infrastructure managers are searching for someone they can trust to conduct penetration testing. It’s an important part of mitigation strategies to expose what they might have missed (for potentially years) and need to address before it’s too late. Overall penetration testing has become a necessity. It’s a marker of the cyber hygiene of an organization, under the overall vulnerability management umbrella. While penetration testing brings forth anxiety, it also prompts change. When an experienced firm conducts the testing, they’ll not only simulate attacks but also train the security team on best practices to react and survive an attack from a threat. Just two examples illustrate the value of this approach—[1] validating existing security controls to ensure they work as designed; and [2] reducing the risk of zero-day threats where attackers routinely probing IT systems find gaps and vulnerabilities before the owner can close or fix them allowing zero days to repair what’s important. (Morris, 2022)
Humans and Their Essential Role in CI Systems and Space Systems
If after all the concerns about space systems, IT, cyber security, and daily IC operations rooted in technology weren’t enough it is always the overlooked and discounted resource which skilled and trained people behind these various systems are which make them work as intended. The damaging lapse in human performance and productivity arising from nearly three years reeling from the global COVID crisis with staffing shortfalls and periodic skills gaps drives home the point. The workforce which underwrites, supports, and sustains CI and space systems can be easily forgotten unless attention is drawn to their vital role in making the connections between CI and space systems obvious and apparent. This DHS chart underscores the basic message. One source claims more than 104 million U.S. workers, or 71 % of the total U.S. workforce, are employed in the “Essential Critical Infrastructure Workforce”. (NCSL, 2020)
Figure 5-5 Essential Critical Infrastructure Workers
Source: (NCSL, 2020)
By contrast about 170,000 workers can be identified as part of the US space systems workforce according to the US Department of Labor in 2017. (BLS, 2017) By comparison a more recent data point which includes all workers in the commercial and government space sector combined reckons the total closer to 2 million workers. This aggregate number of US based space workers when combined with CI workforce data suggests that nearly 106 million workers can be found in both camps. (Aerospace Industries Association, 2020)
Consider the Extra Achilles Heel: Devising Resilience Standards for Space and CI
Here, the engineered and periodically tested measures of resilience applicable for each distinct CI system must be weighed against space system resilience criteria which are not equivalent or similarly ranked. Most often because so much of CI and about 50% of space systems are in private commercial hands, we can find no uniform resilience criteria except to consider how these complex systems tolerate or resist natural disasters, terrorism, cyber hacking, sabotage or natural stress and age-related decline. However, it begs the question of when, how and under what rigorous standards verifiable criteria to gauge resilience in each CI and space system could be derived or developed. It also raises the perplexing dilemma of what organization or objectively skilled enterprise has the requisite talent and expertise to do so.
Inside DHS (CISA) conducts specialized but voluntary security and resilience assessments on the Nation’s CI and its partners—federal, state, tribal, territorial governments, and private industry—in better understanding and managing CI risks. The assessments examine infrastructure vulnerabilities, interdependencies, capability gaps, and the consequences of their disruption. Vulnerability assessments, combined with infrastructure planning resources developed through the DHS sponsored Infrastructure Development and Recovery program. This approach forms an integrated planning and assessment capability featuring an integrated suite of capabilities, methods, and tools support the efficient and effective use of resources to enhance critical infrastructure resilience to all hazards. These voluntary, nonregulatory assessments are a foundational element of the National Infrastructure Protection Plan’s risk-based implementation of protective programs designed to prevent, deter, and mitigate the risk of a terrorist attack while enabling timely, efficient response and restoration in an all-hazards, post-event situation.
Because most U.S. critical infrastructure is privately owned, the effectiveness of CISA assessments depends upon the voluntary collaboration of private sector owners and operators. CISA’s Protective Security Advisors (PSAs) work locally to foster this collaboration and facilitate technical assistance to support enhancement of the security and resilience of the Nation’s critical infrastructure. Assessments are offered through the PSAs at the request of critical infrastructure owners and operators and other state, local, tribal, and territorial officials.
However, the voluntary nature of uniform resilience testing and verification does raise questions about best ways to validate, confirm and test the resilience claims by CI owners and operators. (Hardcastle, 2022)
Fifty-six vulnerabilities – some deemed critical – have been found in industrial operational technology (OT) systems from ten global manufacturers including Honeywell, Ericsson, Motorola, and Siemens, putting more than 30,000 devices worldwide at risk, according to private security researchers. Some of these vulnerabilities received resilience severity scores as high as 9.8 out of 10. That is particularly bad, considering these devices are used in critical infrastructure across the oil and gas, chemical, nuclear, power generation and distribution, manufacturing, water treatment and distribution, mining and building and automation industries. The most serious security flaws include remote code execution (RCE) and firmware vulnerabilities. If exploited, these holes could potentially allow miscreants to shut down electrical and water systems, disrupt the food supply, change the ratio of ingredients to result in toxic mixtures, and do all manner of cyber based havoc including – denial-of-service condition, change control logic, or disable communication links and found frequent flaws in such as programmable logic controllers (PLCs) and remote terminal units (RTUs) – control physical processes, while level 2 devices include supervisory control and data acquisition (SCADA) and human-machine interface systems. (Hardcastle, 2022)
Outlining Threat Dynamics and Vulnerabilities for CI from Cyber and Space
It appears that cyber probes hunting for key hubs or nodes, or classes of items could they impact to deliver a shutdown many CI systems or render these systems hostage Our adversaries have been conducting infrastructure reconnaissance using cyber for many years, they likely already understand our infrastructure choke points. What is missing is a standard inventory of CI weaknesses and vulnerabilities shielded from public view and shared in classified or proprietary confidence between DHS/CISA and the managers of national CI systems. A far more serious question that has NATO ramifications is whether any CI probes and attacks which undermine or neutralize CI systems within the alliance would be seen as ‘acts of war’ sufficient to trigger an Article V military response? One key challenge is devising foolproof forensics to identify what party is engaged in the probe or attack with enough solid confidence to hold a hostile regime accountable. It appears that devising a standby strategy to anticipate and respond to such a scenario would be essential as part of US and NATO combined arms security.
A catalogue of verified CI system vulnerabilities is a starting point but with so much of CI in the operational control of the private sector, and with DHS urging voluntary resilience actions, it is hard to ascertain how CI is protected and sustained against threats in a global comparative manner. Another crude way of putting the issue is to consider whether some advanced societies reliant on CI and space systems have explored all the obvious [and less obvious] pathways to undermine, destroy or disrupt CI as a prelude to armed conflict or as a strategic ‘checkmate’ maneuver to obviate the need for a kinetic attack. In that sense the EU, US, and other advanced nations with CI at risk must tackle the sobering question of preparedness and resilience against the widest possible spectrum of threats and contingencies. If all nations, including Russia, China, Iran, and all others were equally vulnerable in CI terms one could argue the playing field is mostly level. However, what degree of confidence do we have in that perspective?
So, we are left to contemplate the spectrum of immediate and downstream threats against CI considering the ever-present risks arising from a variety of space systems. While the nexus between space systems adding increased jeopardy to CI systems is fundamental, we cannot lose sight of all the other avenues of potential CI mayhem and destruction. More specifically, the array of threat dynamics which entail robust CI protection, and which consider the reciprocal effect of space system influence on CI systems, is large and complex. It certainly includes at least the following threat factors:
- Space based weapons systems
- Catastrophic natural disasters
- Covert cyber hacking and external manipulation [quantum probes]
- Targeted terrorism
- Solar storms
- EMP attacks
- Natural age/stress related system failures
- Insider threats/sabotage
- Interstate war and armed conflict
FBI—NGB Role//Homeland Defense and Estimating CI Protection Priorities
Under existing regulations and normal interagency practices DHS has arranged for the FBI and the National Guard [NGB] to play a major role in restoring damaged or impaired CI systems in conjunction with the private sector enterprises which own and operate them. While not every CI system is rigorously tested and exercised against all possible hazard and threat scenarios the FBI role is integral most often in cases where CI damage or disruption is claimed to be linked to a terrorist act. The overall Homeland Defense posture of Pentagon resources versus defined roles in DHS contingency plans for selected natural disasters which are part of the National Planning Frameworks which depict federal interagency roles in differential disasters and hazard situations. This is also reinforced in the Comprehensive Preparedness Guide 101 which provides guidelines on developing emergency operations plans and promotes a common understanding of the fundamentals of community-based, risk-informed planning and decision making to help planners examine threats or hazards and produce integrated, coordinated, and synchronized plans.
It is fair to ask whether the NGB has developed and tested its operational plans for handling a range of CI system scenarios involving disruption or loss of functionality caused by space system interventions of attacks. In this case a comprehensive exploration of scenarios and readiness plans which are geared to a variety of scenarios for exercise purposes would make sense. In the case of other developed nations with substantial CI assets to protect and safeguard from a presumptive range of space-based threats the same challenge exists to determine if and in what ways the various agencies and organizations charged with protection and restoration of damaged CI are ready to do so. This also reinforces the point that the time and energy required to restore a damaged or impaired CI system from its victimized state to a point of interim versus full restoration presumes that in many cases the difference between interim and full CI restoration will be measured in days or weeks versus minutes or hours. This also assumes that in cases of complex cascading CI failures that resurrecting the one pivotal and keystone CI element which supports many others can be done in a manner that ensures the restoration of other dependent CI systems in an effective and timely manner, From the standpoint of realistic exercise design and conceptual testing this will be a complex and difficult undertaking. This also implies that designated teams involving both government and private sector leaders should be marshaled to assess the current standby capabilities of CI subsystems to withstand space-based damage scenarios and devise strategies for building in greater resilience for these systems.
It begs the question in advanced societies with substantial CI interests and systems to protect and support whether plans and strategies exist to be exercised and thereby affirm the concept.
Reinforcing CI Systems Against Space Based Threats
One clear signal from this brief review of CI systems and their connection to space-based systems is that advanced technologies to harden CI systems to ensure a level of resilience against presumptive space-based threats entails consideration of
- Cyber hardening
- Protective shielding
- Redundant CI systems
- Counter-space deterrent technologies
Conclusions
Once it becomes clear that CI systems are largely vulnerable to space platforms and systems those nations seeking to buttress their CI systems and dependent networks will need to devise strategies and technologies appropriate to the estimated threat. Failure to calibrate and analyze the threat, or do nothing to mitigate its worst effects, seems to leave open the issue of catastrophic CI systems breakdown and loss. How many advanced nations will accept that risk?
References
Aerospace Industries Association. (2020, Mar 11). Workforce Statistics Aerospace Industries Association. Retrieved from www.aia-aerospace.org: https://www.aia-aerospace.org/research-center/statistics
Bahr, L. (2021, Oct 20). space-as-critical-infrastructure-to-enhance-cybersecurity. Retrieved from https://spacesecurity.wse.jhu.edu: https://spacesecurity.wse.jhu.edu/2021/10/20/space-as-critical-infrastructure-to-enhance-cybersecurity/
BLS. (2017). Space careers: A universe of options – Bureau of Labor . Retrieved from www.bls.gov: https://www.bls.gov/careeroutlook/2017/article/careers
Botezatu, A. G. (2020, April 11). CRITICAL_INFRASTRUCTURE_DEPENDENCY_ON_SPACE_SYSTEMS. Retrieved from www.researchgate.net: https://www.researchgate.net/publication/304454658_CRITICAL_INFRASTRUCTURE_DEPENDENCY_ON_SPACE_SYSTEMS
Byrne, D. (2014). 2014 Conference on Systems Engineering Research. procedia-computer-science/vol/28, https://www.sciencedirect.com/journal/procedia-computer-science/vol/28. Retrieved from https://www.sciencedirect.com/journal/procedia-computer-science/vol/28
Chen, S. (2021, Aug 26). did-chinese-scientists-just-bring-down-an-unmanned-plane-with-an-electromagnetic-pulse-weapon. Retrieved from www.thestar.com.my/tech/: https://www.thestar.com.my/tech/tech-news/2021/08/26/did-chinese-scientists-just-bring-down-an-unmanned-plane-with-an-electromagnetic-pulse-weapon
CISA. (2002). CRITICAL INFRASTRUCTURE INFORMATION ACT OF 2002. Retrieved from www.cisa.gov: https://www.cisa.gov/publication/cii-act-2002
CISA. (2021, May 13). cisa-launches-space-systems-critical-infrastructure-working-group. Retrieved from www.cisa.gov/: https://www.cisa.gov/news/2021/05/13/cisa-launches-space-systems-critical-infrastructure-working-group
CISA. (2022). Cyber Incident Reporting for Critical Infrastructure Act of 2022. Retrieved from www.cisa.gov/circia: https://www.cisa.gov/circia
electricaltechnology. (2018, March 18). ehv-hv-substations-design-installation-types-configuration. Retrieved from www.electricaltechnology.org: https://www.electricaltechnology.org/2018/03/ehv-hv-substations-design-installation-types-configuration.html
GAO. (2007, Oct 17). Critical Infrastructure Protection: Multiple Efforts to Secure Control Systems Are Under Way, but Challenges Remain. Retrieved from https://www.gao.gov/products/gao-08-119t: https://www.gao.gov/products/gao-08-119t
GAO-20-453. (2020, March 14). Critical Infrastructure Protection: Actions Needed to Enhance DHS Oversight of Cybersecurity at High-Risk Chemical Facilities. Retrieved from https://www.gao.gov/products/gao-20-453: https://www.gao.gov/products/gao-20-453
GAO-22-104279. (2022, Mar 1). Critical Infrastructure Protection: CISA Should Improve Priority Setting, Stakeholder Involvement, and Threat Information Sharing. Retrieved from www.gao.gov/: https://www.gao.gov/products/gao-22-104279
GAO-22-105103. (2022). Critical Infrastructure Protection: Agencies Need to Assess Adoption of Cybersecurity Guidance. Retrieved from www.gao.gov/: https://www.gao.gov/products/gao-22-105103
Hambling, D. (2019, Aug 27). frontline-tech-how-are-radio-frequency-weapons-shaping-future-battlefields. Retrieved from www.forces.net: https://www.forces.net/news/technology/frontline-tech-how-are-radio-frequency-weapons-shaping-future-battlefields
Hardcastle, e. L. (2022, June 21). cisa-and-friends-raise-alarm-on-critical-flaws-in-industrial-equipment-infrastructure. Retrieved from www.msn.com: https://www.msn.com/en-us/news/technology/cisa-and-friends-raise-alarm-on-critical-flaws-in-industrial-equipment-infrastructure/ar-AAYGbOn
Harper, J. (2017, July). Pentagon Examining Options for Space-Based Missile Interceptors. Retrieved from www.jstor.org/: https://www.jstor.org/stable/pdf/27021837.pdf
Harrison, J. M. (2021). space-threat-assessment-2021. Retrieved from www.csis.org: https://www.csis.org/analysis/space-threat-assessment-2021
INSA. (2021, Nov 2). designating-space-systems-as-new-u-s-critical-infrastructure-sector. Retrieved from www.insaonline.org: https://www.insaonline.org/designating-space-systems-as-new-u-s-critical-infrastructure-sector/
Janosek, D. M. (2020, May 8). part-1-critical-infrastructure-space-security-and-cybersecurity-intersect. Retrieved from www.captechu.edu/: https://www.captechu.edu/blog/part-1-critical-infrastructure-space-security-and-cybersecurity-intersect
Kongsberg Gruppen Maritime. (2021, March 2). UUV -unmanned-persistent-surveillance-longendurance. www.militaryaerospace.com, pp. https://www.militaryaerospace.com/unmanned/article/14198451/unmanned-persistent-surveillance-longendurance.
Lambakis, S. (2018). Foreign space capabilities: Implications for U.S. national security. Retrieved from cogentoa.tandfonline.com: https://cogentoa.tandfonline.com/doi/abs/10.1080/01495933.2018.1459144?journalCode=ucst20
Langner, R. (2013, Nov). to-kill-a-centrifuge. Retrieved from www.langner.com: https://www.langner.com/wp-content/uploads/2017/03/to-kill-a-centrifuge.pdf
MaGill, J. (2021, July 25). us-water-supply-system-being-targeted-by-cybercriminals. Retrieved from www.forbes.com: https://www.forbes.com/sites/jimmagill/2021/07/25/us-water-supply-system-being-targeted-by-cybercriminals/?sh=77421de428e7
Magnuson, S. (2022, May 10). acknowledging-space-systems-as-critical-infrastructure. Retrieved from www.nationaldefensemagazine.org: https://www.nationaldefensemagazine.org/articles/2022/5/10/acknowledging-space-systems-as-critical-infrastructure
Morgan, C. (2020, April 2). satellites-role-in-monitoring-critical-infrastructure. x2n.com/, pp. https://x2n.com/blog/satellites-role-in-monitoring-critical-infrastructure/.
Morris, M. (2022, Jul 21). the-rising-importance-of-penetration-testing-in-critical-infrastructure-environments. Retrieved from www.forbes.com: https://www.forbes.com/sites/forbestechcouncil/2022/07/21/the-rising-importance-of-penetration-testing-in-critical-infrastructure-environments/?sh=31aa7fd85220
NASIC. (2022). About-Us/Fact-Sheets/Article/1738710/competing-in-space/. Retrieved from www.nasic.af.mil/: https://www.nasic.af.mil/About-Us/Fact-Sheets/Article/1738710/competing-in-space/
NCSL. (2020, Mar 29). covid-19-essential-workers-in-the-states. Retrieved from www.ncsl.org: https://www.ncsl.org/research/labor-and-employment/covid-19-essential-workers-in-the-states.aspx
Nichols, & Carter, H. J. (2022). Drone Delivery of CBNRECy – DEW Weapons: Emerging Threats of Mini-Weapons of Mass Destruction and Disruption (WMDD). Manhattan, KS: New Prarie Press #46.
Nichols, R. K., & Mumm, H. C. (2020). Counter Unmanned Aircraft Systems Technologies & Operations. Manhattan, KS: www.newprairiepress.org/ebooks/31.
Nichols, R. K., Sincavage, S., Mumm, H., Lonstein, W., Carter, C., Hood, J., . . . & Shields, B. (2021). Disruptive Technologies With Applications In Airline, Marine, Defense Industries. Manhattan, KS: New Prairie Press, #38.
Paikowsky, D. (2021, Dec 28). why-russia-tested-its-anti-satellite-weapon-349678. Retrieved from publisher.tbsnews.net: https://publisher.tbsnews.net/features/panorama/why-russia-tested-its-anti-satellite-weapon-349678
Sharon, R. (2022, Oct 10). GAO -105102 GAO assesses progress in adopting cybersecurity framework. Retrieved from www.ronsharon.com: https://www.ronsharon.com/2022/02/10/gao-assesses-progress-in-adopting-cybersecurity-framework/
SPACE. (2016, Dec 21). The Most Dangerous Space Weapons Ever. Retrieved from www.space.com: https://www.space.com/19-top-10-space-weapons.html
TAIWAN News. (2022, Mar 19). china-develops-laser-weapon-that-can-shoot-down-satellites. Retrieved from taiwannew.net: https://taiwannew.net/china-develops-laser-weapon-that-can-shoot-down-satellites
Tena, I. (2019). Standing up to new underwater threats – counter UUV intruder. Retrieved from cdn.asp.events: https://cdn.asp.events/CLIENT_Clarion__96F66098_5056_B733_492B7F3A0E159DC7/sites/UDT-2020/media/libraries/draft-abstracts–slides/33-Ioseba-Tena.pdf
Tucker, P. (2019, Sept 5). pentagon-shelves-neutral-particle-beam-research/159660/. Retrieved from www.govexec.com: https://www.govexec.com/technology/2019/09/pentagon-shelves-neutral-particle-beam-research/159660/
Wechsler, G. B. (2020). Cyber Threats to Space Systems Current Risks and the Role of NATO Gil Baram and Omree Wechsler —NATO 2020. Retrieved from www.researchgate.net: https://www.researchgate.net/publication/342666394_Cyber_Threats_to_Space_Systems_-_Current_Risks_and_the_Role_of_NATO
Weigel, A. (n.d.). Space System Architecture Lecture 1: Space Systems and Definitions Framing Document. Retrieved from s3vi.ndc.nasa.gov/: https://s3vi.ndc.nasa.gov/ssri-kb/static/resources/01010wk1_framing.pdf
Werner, D. (2019, Sept). small-satellites-big-weakness. Retrieved from aerospaceamerica.aiaa.org: https://aerospaceamerica.aiaa.org/features/small-satellites-big-weakness/
Willuhn, M. (2022, March 1). Satellite_cyber_attack_paralyzes_11GW_of_German_wind_turbine. Retrieved from article.wn.com/: https://article.wn.com/view/2022/03/01/Satellite_cyber_attack_paralyzes_11GW_of_German_wind_turbine/

