7 The Remote Woo: Exploring Faux Transnational Interpersonal Romance in Social Imagery
Shalin Hai-Jew
AbstractOne aspect of globalization combined with information and communications technology (ICT) and social media is the advent of online data and resulting long-distance romances. The relationships that have come to the fore, though, are about transnational (and more local) romance scams perpetrated online that result in loss of funds, loss of time, loss of personal dignity, loss of personal reputation, and other harms. This work explores social imagery to better understand some of the messaging behind the “remote woo” and romance online and romance fraud and what insights these may provide on this issue, in this exploratory study.
|
Key Words
Remote Woo, Strategic Transnational Communications, Faux Interpersonal Romance, Cyber Romance, Romance Fraud
Introduction
“I want your ugly, I want your disease
I want your everything as long as it’s free
I want your love
Love, love, love, I want your love, hey
I want your drama, the touch of your hand (hey)
I want your leather-studded kiss in the sand
I want your love
Love, love, love, I want your love”
— Lady Gaga in “Bad Romance” (2009)
“It’s strange what desire will make foolish people do.
I’d never dreamed that I’d meet somebody like you.”
— Chris Isaak in “Wicked Game” (1989)
Human courtship has existed since the beginning of time and in various forms of wooing (trying to attain the love and favor of another). When two (or more) can find a match, align, and come to some agreement, they can create relationships that exist for many years, and more rarely, even a lifetime. The advent of cyber has enriched this space with more variety, according to Aaron Ben-Ze’ev (2015):
Cyberspace offers an alternative romantic (and sexual) environment that provides people with easy access to many tempting options. It is a kind of huge, dynamic, electronic bedroom loaded with imaginative interactions. This novel environment has a significant impact upon offline romantic activities. This impact is expressed in increased opportunities, greater self-disclosure, decreased vulnerability, greater satisfaction, lesser commitment, increase in violations of boundaries, and reduced exclusivity. Cyberspace provides technical tools that facilitate the opportunity to conduct several romantic (and sexual) relationships at the same time. Although cyberlove and cybersex are likely to become more popular, they will not replace offline relationships, but rather complement them. (p. 813)
In advertising and on social media, there are meta-messages of #soulmates, #theone, and #relationshipgoals. Advertisements for wedding rings talk about #forever and #eternity. Interpersonal relationships and love are to be celebrated. Dating sites of various types emerged with many of the same tropes.
Some of the early online ventures for “interpersonal connections” was thought (naively?) to shift focuses from physical attractiveness to more substantive aspects of a person (Cooper & Sportolari, 1997, pp. 7 – 9). Online dating has reached a “tipping point” and has wide acceptance globally (Cabrera-Frias, 2013, p. G:1). As a global industry, “e-love networks have proliferated since the mid-1990s and are expected to generate $1.9 billion by 2012” (Rege, July – Dec. 2009, p. 494), with 1,400 such sites by the late 2000s (Scott, 2009, as cited in Rege, July – Dec. 2009, p. 495) and hundreds of millions of dollars spent annually for dating services. As “business-to-consumer” electronic-business models, dating applications approaches proved highly lucrative (Singh & Jackson, 2015, p. 482). Various mobile online dating apps have peoples swiping left (no) and swiping right (yes) and agreeing to meet-ups and sexual assignations (and having an impact on the spread of sexually transmitted infections or “STIs”), according to the U.S. Centers for Disease Control and Prevention (Saleh, July 27, 2019). Research into these sites found many singletons looking for love as well as many marrieds (and dedicated dating sites for those married looking for “side action”). Online dating is “normative” in Western society (Whitty & Buchanan, 2012, p. 3), and it has popularized in many places around the world (although the expectations for the technologies seem to differ based on cultural contexts). One work describes a conservative society in which youth online dating and romance is typified by “approval of their parents for relationships, marriage and having children” and ”not idealised by sexual activities” (Rambaree, 2008, p. 34). Building relationships online requires regular contact over a continuous period of time, during which each learns about the other and they “negotiate a common relationship definition” (Döring, 2002, p. 3). A study of those who’ve experienced “romantic net relationships” suggests that these experiences are not “an exotic fringe phenomenon nor an epidemic mass phenomenon” but part of the everyday (Döring, 2002, p. 5). For some, the experiences sound euphoric and personally meaningful; for others, it was just an experience that did not result in desired ends. In the Global South, Facebook serves as “the one-stop-shop for social activity among the poor” and so is the socio-technical nexus for the pursuit of “sex, romance, and love” (Arora & Scheiber, 2017, p. 408), so such activities are not only occurring on dedicated sites. [“Netsex” (or “cybersex” or sex via online means) was found to have become a thing on an academic mailing list among members of an online group, with effects on offline life (Marshall, 2003, p. 229).]
More commonly, people are pursuing a less serious endeavor; they are socializing and pursuing pleasure; they are engaging in a seduction game, to draw or attract another to compromise themselves—in order to brag on social media. Many are pursuing “romance” [“a feeling of excitement and mystery associated with love” and “a quality of feeling of mystery, excitement, and remoteness from everyday life” (“romance,” 2019)], affection, feelings of self-worth, sex, or long-term relationships, or some combination of interests. If romance is popularly linked to rose-colored glasses, there may be something in that it may affect judgment and provide a positive filter or bias. In terms of risks, online dating risks include “the prospect of deceit, the possibility of encountering dangerous and suspect people online, as well as risks of a sexual, emotional, and / or physical nature” (Couch, Liamputtong, & Pitts, 2012, as cited in Luu, Land, & Chin, 2017, p. 2430).
Disconnected people look for a romantic connection, whether it is partial and temporary or longer term. (Figure 1) Misreading the state of the relationship entails risk, where a romantic come-on can turn into a con-on (confidence trick).
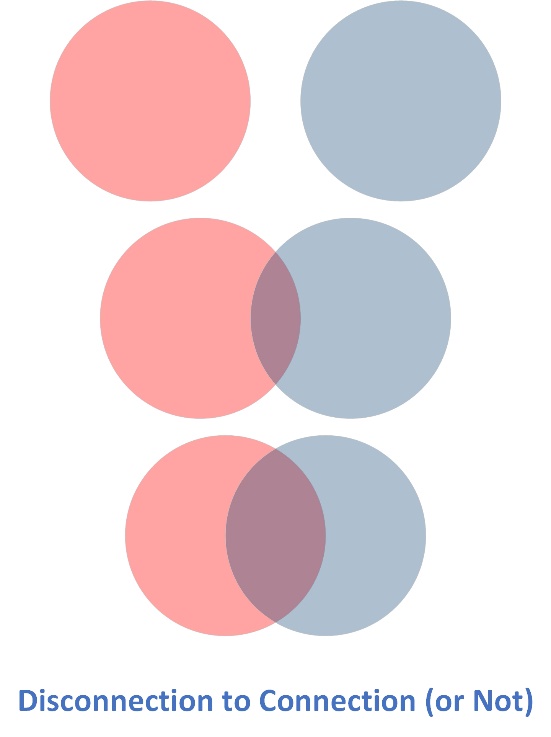
Figure 1: Disconnection to Connection (or Not)
Among the would-be daters, some types of suitors both abroad and domestic are after not love but money and other resources (like a “green card” or ability to migrate to another country as a foreign spouse), in a type of “social engineering” attack (in a cyber security sense), which is a modern-day version of an old-school confidence trick (or “con”), known as “dating fraud,” “relationship fraud,” and “sweetheart swindles” (Cross, Dragiewicz, & Richards, 2018, p. 1304). Romance scams are considered a sub-category of “imposter scams” (by the US Federal Trade Commission), with individuals pretending to be “government, business or tech support services” to trick people out of money (some $328 million in 2017, sent out through wire transfers and gift cards) (Doubek, Feb. 13, 2019, p. 3). In 2018, Americans lost $1.5 billion to fraud (Exley, Dec. 5, 2019). In other conceptualizations, romance scams are part of an “advance fee fraud” and “mass-marketing fraud” (the message of love and anticipated connection used to induce monetary giving) (Whitty, 2018, p. 105). Responding to faked identities, people have been lured to “click on malicious links, make fraudulent payments, or download malicious attachments” (Williams, Beardmore, & Joinson, 2017, p. 412). The “mark” (or “dupe”) believes he or she is in a genuine relationship because of efforts by the “offender” to create and maintain a sense of “trust and rapport” (Cross, Dragiewicz, & Richards, 2018, p. 1304). The romance scam originated many years prior as “paper mail fraud” and as an online threat in 2008, with losses ranging from £50 -£240,000 per victim, according to the UK Serious Organised Crime Agency (Whitty & Buchanan, 2012, p. 2).
The ”virtuality” of online, for a period of time, became a space for an expression of the pseudo-real. People could commit to so-called “cohabitation online” where people could create a sense of virtual domesticity (Lee & Chang, n.d., p. 1) and even create virtual marriages online. These practices do not seem like a practice with any seriousness currently. Fantasy cyber-affairs can have real effects on social “trust, self-esteem, and integrity in a relationship” (Maheu, 1999, p. 1). Married couples setting boundaries among themselves so as not to break bonds and trust with online activities, given the risks of “online infidelities” (Helsper & Whitty, 2010). The practices of sexual texting (sexting) and taking sexualized selfies (self-taken photos) are other in-world practices that overlap with cyber (Lee, 2018, p. 233). Various types of cyber-sex exists in the “twilight zone between virtual reality and virtual fantasy” (Dryer & Lijtmaer, Feb. 2007, p. 1). Online was seen as a space for the exploration of “virtual sexual fantasies” (Barnes, 1996, p. 34). More modern technologies bring together the virtual-physical sexual with virtually controlled sex toys and sex dolls (Ho, 2003, p. 2), adding different dimensions to “cybersex”. In general, there is more intimacy in face-to-face than computer-mediated or virtual romantic relationships (Scott, Mottarella, & Lavooy, 2006).
The “cyber-physical confluence” applies to romance, in both the virtual and the real. [Not everything that happens online stays online, and likewise in the physical real.] Certainly, there are externalities and spillovers from the real to cyber and back. People engage in “romance tourism” (and “sex tourism”), with various destination countries (often poor ones serving richer ones) offering recreational endeavors. International courtship via cyber (such as through “pen-pal agencies,” “mail-order bride sites,” “match-making” services (Agrawal, 2015) may include those seeking marriage. There are various “dot.cons” for those who are trying to procure not only brides but children for adoptions (Letherby & Marchbank, 2012).
Romance scams cost those in the U.S. some $143 million in 2018, according to the U.S. Federal Trade Commission, and with a median amount lost at $2,600 (Doubek, Feb. 13, 2019; Fletcher, Feb. 12, 2019). A single mother in Texas who got caught up in such a romance scam lost just under half a million dollars (Martin, Nov. 18, 2019), even though she was warned about this “relationship” by her bank and others. The illusory relationship was too alluring, and even though she was aware of how much she was spending, she kept thinking that she could earn back what she’d lost in something similar to a gambler’s compulsion (in her own explanation). Many who have been scammed are reluctant to admit that they were wrong and will continue in an erroneous belief even when that is contravened by facts (Barker, as cited in Bartlett, Nov. 24, 2019, p. 18). In 2016, the Australian Consumer and Competition Commission reported that there was $83,563,599 in scam losses that year with “dating and romance and investment scams (that) made up the bulk of the losses” (Lee, 2018, p. 226). In 2011, the costs of fraud in the United Kingdom was “over £38 billion a year” and some “6.5 per cent of the UK adult population” fall victim to scams annually (Whitty & Buchanan, 2012, p. 2). The nature of the crime suggests that victims may feel shame and therefore fail to report the fraud (Whitty & Buchanan, 2012, p. 8). Various estimates suggest that as few as 10 – 15% of such cases are reported (CBC News, 2017; Brenhoff, 2017, as cited in Cross, Dragiewicz, & Richards, 2018, p. 1303). Thousands of victims are affected by romance fraud globally (Cross, Dragiewicz, & Richards, 2018, p. 1303). A study by the American Association of Retired Persons (AARP suggests that four percent of U.S. adults were “victims of an online relationship scam” (Doubek, Feb. 13, 2019, p. 2).
Whatever the mental framing and pre-conceptions around particular social and cultural practices, like dating and the pursuit of romance, these practices do not occur in isolation from other phenomena in the world: individual and group health, finances, commercial endeavors and industries, work, lifestyle, and others. All choices have “opportunity costs” (doing one thing precludes doing some other things) but also potentials for actual relationships, even as they are a fast diminishing good in many cases. Demographic factors also come into play in different populations, with the relative availability of romantic partners changing based on a variety of factors.
Review of the Literature
Cyberspace is a common nexus for deceptions because of “the similarity between reality and digitally generated forms of communication (text, video, etc.)” (Thomas, 2008, p. 4). Humans have cognitive biases, which make them prone “to accept rewards, romance, charity, or other feelings of sensitivity and emotion” and to confuse “what is false is real, and vice versa” (Thomas, 2008, p. 4). A common deception includes “pretexting” (“the act of creating and using an invented scenario”…to “persuade a target to release information or perform an action” (Thomas, 2008, p. 4). When people are in a heightened emotional state, such as romance, they are more motivated to fall for various cyber scams (Thomas, 2008, p. 6). Messages that leave a person in a “hot state” can affect that person’s decision-making (as compared to decision making in a “cold state”). People may also enter the dating space with culturally-taught mental “scripts” of dating, with attendant manners and civilities, and tendencies towards trying to impress the other and “put the best foot forward,” and they may erroneously assume that those scripts are in play with others. Those who keep cultural frames top-of-mind may miss cues that others are acting in out-of-role behaviors and to other ends. They may read others’ profile-based assertions of careers and professions and assume that those might suggest particular traits of intelligence or class or moneys or personality features: “She is an engineer, so she probably…” “He is a construction worker, so he probably…” They may suspend (protective) disbeliefs and give others the benefit of the doubt. They may take a lifetime of learning about people and assume that the social rules of attraction may not apply or that they may be the exception and not the rule (even if that assumption is not statistically valid).
They may focus on hopes and not costs. Instead of paying attention to their own expenditures, they may focus on a future that will never come and fail to notice the one-directional giving of resources and the “red flags” (warnings) of faux “relationship.” Human mental shortcuts may also render cool judgment moot: for example, a person’s physical “hotness” (attractiveness) may be conflated with physical health, mental well-being, and regular employment. In some cases, what is being transactionally traded is human “attention” (and social performance and personal theatre) for “funds” (Schifferle, Feb. 12, 2019), and in the colloquial, “warm fuzzies” and schmaltz for “cold hard cash.” The duped can believe in his/her fundamental attractiveness and can brag about the relationship, and the con can walk off with funds. In some cases, actual human attention is not even in play; automated agents like chatbots are sometimes employed to do the wooing (Thomas, 2008, p. 6). [With the advance in AI, chatbots have become even more believable and able to converse around a variety of issues in improvisational ways. “Flirt” modules are not difficult to include in a natural language processing (NLP)-enabled ‘bot.]
Early research found that those who form new relationships online vs. those who didn’t did not differ in fundamental ways on measures of social skills or experienced loneliness (Bonebrake, 2002, p. 555). The Online Relationship Initiation Scale (ORIS), a validated instrument, suggests that particular variables may be found in those who initiate online relationships. This study found that “men were more likely than women to initiate online relationships” and that such initiation “was not strongly associated with perceived social support, but was positively related to financial distress, and willingness to engage in infidelity or unprotected sex” (Harris & Aboujaoude, 2016, p. 487). Such online relationship initiation “was negatively associated with age and satisfaction with life” (Harris & Aboujaoude, 2016, p. 487). The co-researchers suggest that those “struggling offline may find online technologies of some benefit to their personal lives” (Harris & Aboujaoude, 2016, p. 491).
People use online dating websites in different ways and for different gratifications depending in part on their “biological and personality traits.” One cross-sectional survey study found some patterns:
Specifically, women and homosexuals were found to be more neurotic, women were more agreeable, and homosexuals were more open to experiences. Homosexual users sought a wider range of gratifications (relationship, sex partner, distraction, and convenient companion) from online dating sites than their heterosexual counterparts. Women were less likely to use ODSs (online dating sites) to find sexual partners, but more likely to use ODSs to be social. Those who were neurotic use dating sites to build an identity, as a convenient companion, and as a distraction. People who are open to experiences were found to use dating sites to be social. Disagreeable people use dating sites because of peer pressure and as a status symbol, and conscientious people were found to use dating sites to find a relationship. (Clemens, Atkin, & Krishnan, 2015, p. 120)
Individuals “with high self-esteem were less motivated to use cyber dating to hook up” (Bryant & Sheldon, 2017, p. 1) or to meet to form a relationship or to engage in a sexual rendezvous (known colloquially as a “booty call”). “Older users and women were more likely” to use dating sites for “relationship reasons” (Bryant & Sheldon, 2017, p. 1). When the technologies were fairly new, many who used such sites may have been viewed in a somewhat derogatory way. However, the uses of such sites have become more common and more socially accepted over time, in the West.
The promise of marriage or a path towards marriage is an inducement in some cases. Researchers write: “In the case of a widow, divorcee, single lady or estranged wife, perceived to be rich or credit-worthy, a proposal of intention to marry will prevail” (Ojilere, Nnabue, & Oraegbunam, 2018, p. 6). In other social media postings, the promise of “marriage and romance” served as an inducement for women to join the fighters of the Islamic State (Liang, 2015, p. 3). [In this case, young women traveled to war zones only to be quickly widowed and married multiple times because of a repeat of the cycle.] In the sexual tourism space, researchers have observed the dangling of marriage to set up sexual assignations for when particular men visited a particular locale (Enteen, 2005), in brazen and cringe-worthy postings.
Interestingly, for others, escaping a relationship or a marriage in the real world…with fantasy…is an appeal to go online. Online anonymity has its own appeal:
Another element inherent in anonymity that heavily contributes to its allure is fantasy: one can project onto the screen one’s wildest imaginings. The conversation is limited only by the very limits of one’s imagination. The lack of identifying information, of visual input (in some cases), of a real body next to one’s own leads individuals to co-create an imaginative fantasy ambiance whose magnetism can be very strong. These are unlimited possibilities to fill in the blanks that computer-mediated communication creates by its very disembodied, virtual, machine-powered nature. The persona of the virtual partner usually evokes a very powerful response; however, this response may have more to do with the individual’s own projecting mind than with the virtual partner’s real personality or physical characteristics. In this respect, potent idealizations add up to produce an irresistible aura that captivates, engulfs, and soothes the chat room participant. (Mileham, 2007, p. 17)
People go online to form “romantic” relationships for any number of reasons, some seen as more wholesome than others.
Romance scammer profiles
Researchers have identified different types of “scam-cultures” informing romance scammers (Rege, July – Dec. 2009, p. 495). Pursuing moneys from the unwitting abroad are seen as part of sport, in a “hunter-and-antelope relationship,” and are celebrated in hip-hop music in the Nigerian context (Lazarus, 2018, p. 63). Here, the so-called “Yahoo boys” are lauded for their cyber-fraud abilities.
In general, most were “patient in grooming their victims” with some “six to eight month”(s) of invested time and “enduring, rational, planned, and coordinated” actions (Rege, July – Dec. 2009, p. 504). They treated this endeavor like a full-time job and with different units taking on specific tasks. Some hired “psychologists who assisted in further psychologically trapping victims” (CBC, 2008, as cited in Rege, July – Dec. 2009, p. 504). Another study found that the “earliest stages of the relationship were intentionally performed to build rapport and develop friendship and solidarity between strangers,” including the employment of “politeness strategies” (Brown & Levinson, 1987, as cited in Shaari, Kamaluddin, Paizi, & Mohd, 2019, p. 108). One researcher, in a multimodal study, described a basic “anatomy” of the scam, in five stages: “In the first stage the criminal creates an attractive profile to draw in the victim, in Stage 2 the criminal grooms the victim, priming them to send money, in Stage 3 the criminal begins to request funds from the victim (there a (sic) four potential trajectories at this stage), in Stage 5 (sic), which only a few went through, the victim is sexually abused via cybersex, and finally Stage 5 is the revelation. (Whitty, 2015). A seven-stage summary of this amended model includes the following:
(1) The victim being motivated to find an ideal partner, (2) the victim being presented with the ideal profile, (3) the grooming process, (4) the sting (crisis), (5) continuation of the scam, (6) sexual abuse and (7) revictimization (Whitty, 2013b, as cited in Cross, Dragiewicz, & Richards, 2018, p. 1306).
Another and more recent model involves three stages and a number of sub-steps (in a Malaysian context):
Stage 1: Setting up contact and establish(ing) relationship
Stage 2: Gaining trust (claim common ground) and developing personal relationship
- Step 1: Claim common Ground—Scammer shows similarities between him and target victim.
- Step 2: Scammer notices and attend(s) to victim’s interests and wants.
- Step 3: Scammer shows concern of victim’s needs and wants.
- Step 4: Scammer exaggerates interest/sympathy/approval/ towards victim.
- Step 5: Scammer strengthens his interest towards the victim (or at least makes victim feels as it is).
- Step 6: Scammer makes interesting offers.
- Step 7: Scammer shows the act of togetherness by including victim into his future plan.
- Step 8: Scammer urges for reasons or gives reasons for his action.
- Step 9: Scammer indicates that he wans victim to commit herself to do something (for) him.
- Step 10: Scammer offers interesting gifts.
- Step 11: Both scammer and victim show sympathy, understanding, cooperation towards each other.
- Step 12: Scammer assumes a different character (authority figure, lawyers, and police) to present a new excuse for the money.
Stage 3: Maintaining scam, the bait and execution.
-
Step 13: Orders and request: Scammer indicates that he wants victim to do or avoid from doing something.
-
Step 14: Suggestions and / or advice: Scammer convinces victim to do what he says.
-
Step 15: Sending reminders: Scammer reminds or indicates that victim should remember to do something.
-
Step 16: Threats, warnings, dares: Scammer indicates that he will take certain actions if victims refuse to do something. (Shaari, Kamaluddin, Paizi, & Mohd, 2019, p. 110)
Other studies suggest that certain psychological features, such as the Dark Tetrad, may identify those who might engage anti-socially on dating sites. An astute work suggests a tie between “romance fraud” and “domestic violence,” with psychological and financial abuses in both contexts (Cross, Dragiewicz, & Richards, 2018, p. 1304). Of special note, the researchers used the categories of psychological mistreatment identified by Tolman and his colleagues (1999), including: “economic abuse, creation of fear, isolation, monopolization, degradation, rigid sex role expectations/trivial requests, psychological destabilization, emotional or interpersonal withdrawal, (and) contingent expressions of love” (pp. 326 – 328, as cited in Cross, Dragiewicz, & Richards, 2018, p. 1308) to code insights by romantic fraud victims. Of these, they coded to every category except for “rigid sex role expectations / trivial requests” (Cross, Dragiewicz, & Richards, 2018, p. 1317).
Another research team, in studying people’s expressed romantic imaginations and “personal love stories,” suggests that the appeal to “strong emotions” at least partially explains the success of the Online Romance Scam (Kopp, Layton, Sillitoe, & Gondal, July – Dec. 2015, p. 205). The appeals to emotion create a false sense of a relationship, which can then be exploited for financial gains. Many of the faux profiles follow a basic formula: “The first part contained a personal description, and the second part describes what the character likes, and what their hobbies are. The third part covers the reason why the character is looking online for a partner, whilst the fourth part describes the character of the person they are looking for. We found that while the four parts can come in different order, most profiles start with a self-description, followed by hobbies, motivation and finally by the character they are looking for” (Kopp, Layton, Sillitoe, & Gondal, July – Dec. 2015, pp. 209 – 210). The describes are written to appeal to their target demographic. The male profiles emphasize their wealth and also their interest in traditionally female activities in some ways, as part of a ploy to appear as “a perfect male partner who might share exactly the same female-related interests or hobbies” (Kopp, Layton, Sillitoe, & Gondal, July – Dec. 2015, p. 210). The victim is being drawn into a narrative of an “ideal love story” through the various fictions (Kopp, Layton, Sillitoe, & Gondal, July – Dec. 2015, p. 213), in which there are shared interests (p. 214) [In some ways, those who post their own profiles on dating sites are expressing something of their own fantasy selves—their most attractive instantiations—their most idealized personas. The responses they can elicit can serve as affirmations.]
Romance scam victim profiles
There is not the same risk of victimization for everyone. People have varying susceptibility to “online influence” (Williams, Beardmore, & Joinson, 2017). One psychological analysis of a client who pursued “techno-intimacy” online, the researchers suggested that he was striving to meet needs for the actualization of his idealized self based on an ego-split and other childhood traumas (per Freudian analysis) (Dryer & Lijtmaer, Feb. 2007, pp. 52 – 53). Some go online to deal with ego deficiencies by idealizing potential lovers (Bollas, 1987) and may find “therapeutic benefit” in cyberspace (Whitty & Carr, 2003, pp. 886 – 887).
The application of protection methods for those engaged in online dating depends in part on knowing the profile of prior victims and a victimology profile. Those in the 55 – 64 age category “were over-represented in terms of financial loss, accounting for close to 40% of total money lost to fraud, in contrast to representing only 20% of reports made (Scamwatch, 2016, as cited in Luu, Land, & Chin, 2017, p. 2431). A 2015 report from the Internet Crime Complaint Center (a project of “the FBI and the National White Collar Crime Center”) “found 29% of people targeted in romance scams were women 50 or older, who accounted for more than 51% of all financial losses in romance scams” (Grant, 2015, as cited in Cornelius, Dec. 2016, p. 31). Both men and women are “targeted roughly equally, though women lost more money and were more emotionally affected than men by the scam” (Whitty & Buchanan, 2012b, as cited in Luu, Land, & Chin, 2017, p. 2432). Vulnerabilities include those females in prior “abusive relationships” and males with “mental health issues” like “social anxiety disorder and depression” (Whitty & Buchanan, 2012b), risk-taking and belief in “fate and destiny” (Dudley & Shadel, 2015), high ratings in “romantic beliefs” and a “high motivation to fall in love” (Whitty & Buchanan, 2012b), and being “sensitive and less emotionally intelligent” (Tatera, 2016, as cited in Luu, Land, & Chin, 2017, p. 2432). Many of the victims came from a range of professional backgrounds, with many highly educated and earning middle-to-high incomes (Luu, Land, & Chin, 2017, p. 2432). One intervention suggested by a research team suggests an intervention to show individuals their vulnerabilities and to empower them to use protective measures (Luu, Land, & Chin, 2017, pp. 2438 – 2439).
Another study found victims of “cyber-dependent crime” tended to be based on “individual and household factors, as well as online and prevention behavior” for those engaged in routine activities online (Bergmann, Dreißigacker, von Skarczinski, & Wollinger, 2018, p. 84).
Those who attain a state of flow (and pleasure) when engaging online are more susceptible to cyber-game addiction (Chou & Ting, 2003), and this dynamic may also play into engagements with dating websites and applications.
One research team proposes a mix of factors that culminate in a “holistic individual susceptibility” to workplace phishing involving features such as the following sub-elements as part of four variables: “high propensity to trust, low self-control, low self-awareness, high risk-taking, high self-deception, expertise, high need for affiliation” for one variable; “need for finance, goal conflict, desperation, negative mood, loneliness, cognitive overload, fatigue” for a second variable; “low power, hierarchical organization values, individualistic cultural values, relational cultural values” for a third variable, and “reciprocity, scarcity, commitment/consistency, conformity, authority, liking, loss” for a fourth variable. (Williams, Beardmore, & Joinson, 2017, p. 418) The various interaction effects among the variables and their sub-elements may come together to create vulnerability.
In the Malaysian cyber romance victimization profile, researchers found the following:
This study found that those between the ages of 25 and 45 years were likely to be the victims of cyber romance scams in Malaysia. The majority of the victims are educated and having a Diploma. In addition, this research shows that married people are more likely to be the victims of cyber romance scams. Study shows that non-income individuals are also vulnerable to being the victims because the study shows that 17 percent of respondents who are the victims are from this group. As expected, those who work and have monthly income between RM2001 (ringgit) and above are more likely to be targeted and become a victim of cyber romance scams. The study also shows that those who lack computer skills and (have) less levels of cyber-fraud awareness are more likely to be victims of cyber romance scams. (Saad, Abdullah, & Murah, 2018, p. 479)
Women tending to go online more than men for “relational maintenance” (Houser, Fleuriet, & Estrada, Jan. – Mar. 2012) and socialization. Beyond the scam risks, there are also risks of “cyber-stalking,” including “on-line verbal abuse (flaming), threatening e-mails, obscene e-mails, junk mails (spamming), electronic virus, improper messages on message boards” and other reported harassments” (Jerin & Dolinsky, 2001, p. 18).
Another profile of a romance scam victim is of “middle-aged, well-educated women” who tend to be “more impulsive (scoring high on urgency and sensation seeking), less kind, more trustworthy, and have an addictive disposition” (Whitty, 2018, p. 105).
Regardless of the romance scam victim profiles (which represent a cross-section of the gullible in a population), all who engage in the space are vulnerable to one degree or another. There are risks inherent in the social practices, the virtual spaces, the ease of deception, the moneys and peoples to be had.
Teen females were found to engaging in “many forms of risky behaviours while online” including “sharing personal information, posting personal, sometimes sexual photos on the internet, conducting searches to find individuals to talk about sex and arranging meetings with individuals they met online” with a majority “not scared by the experience” of being contacted by online predators (Kite & Gable, 2013, p. 243). One earlier study identified four profiles of adolescent risky behaviors online: “adapted adolescents,” “inquisitive online, and two high-risk ones: “risk-taking aggressive” and “sexually inquisitive online” (DeMarco, et al., 2017, p. 104). There are research and law enforcement endeavors to protect youth against cyber-sexual solicitations (Wurtele, 2017) and the risks of sexual exploitation for European youth (DeMarco, et al., 2017). Adolescents in romantic relationships experience concerning rates of face-to-face aggression, and the partner attachments are also affected by “partner-directed cyber aggression” due to “anxious partner attachment” and “insecure parental attachment” (Wright, 2015, p. 37). Youth cyber aggression arises out of “networks of friendship, dating, and aggression” based on dynamics of “competition, revenge, or attempts to fend off romantic rivals” (Felmlee & Faris, Sept. 2016, p. 243).
Cross-border appeal
Romance tourism is practiced by both men and women. One work, in the Jamaica context, describes how “many Euro-American women travelers” go to the islands to “pursue romantic affairs with local men”—who showcase their “gender repertoire” of “idealizations of local culture and masculinity” (Pruitt & LaFont, 1995, p. 422), as the exotic other. The “gender scripts” for romance include “ardent declarations of love, praises of beauty, and the like, which are a common part of a Jamaican man’s repertoire” (Pruitt & LaFont, 1995, p. 427).
One researcher studied Senegalese women who went online to find marriageable foreign men who could “be more generous than local men” (Venables, 2008, “Senegalese women…,” p. 113), with a special focus on their nationality and location. For others, online dating is part of a “migration strategy” (Venables, 2008, “Chapter 6: It’s all about making contacts…” p. 162).
Work place considerations for cyber romances
The advent of cyber for engaging human relationships has also meant that work places need to consider “the alchemy of sex, lust, love, and technology” (Mainiero & Jones, 2013, p. 198) and need to put the right policies and practices in place to address the challenges of workplace romances. With breakups, some will upload “revenge porn” online to shame and harass former partners (Arora & Scheiber, 2017). There can be spillover of intimate partner violence into cyber (Taylor & Xia, 2018). Victims of romance scams may end up risking company secrets. Those who
Are vulnerable to “emotional pressures” may be “manipulated by an outsider to extract or falsify internal information” (Rich, et al., July 2005, pp. 24 – 25), so there may be second-order and third-order effects beyond harm to the scammed individual.
The Remote Woo: Exploring Faux Transnational Interpersonal Romance in Social Imagery
For humanity, the various elements of “romance, love, coupledom, romantic partnership, live-in partner, marriage, altruism, romance fantasy” have long been with people, as may be seen in the mass digitized book text set in the Google Books Ngram Viewer (Figure 2). These concepts have hardened and been reified into concepts that have appeared in books for generations.
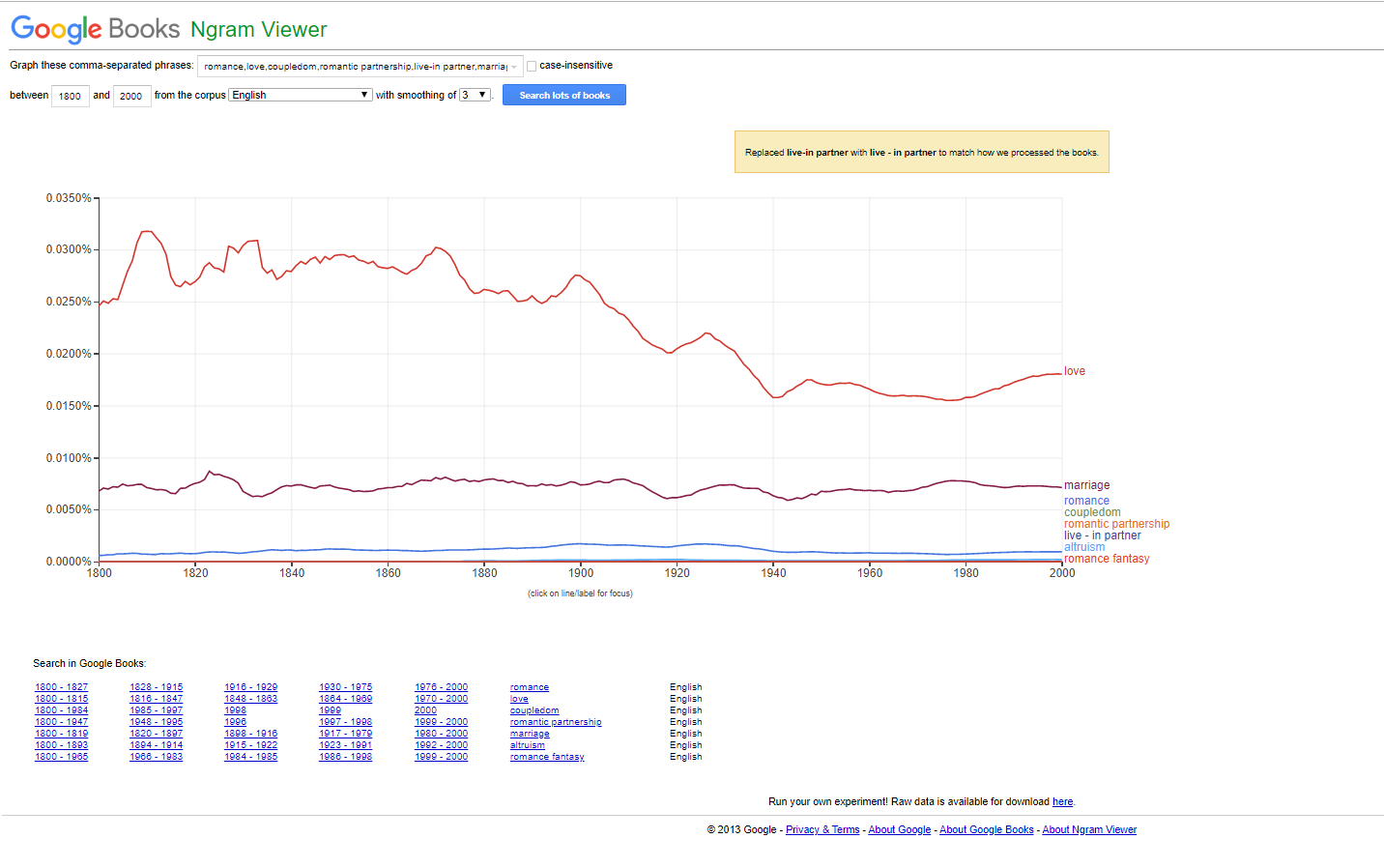
Figure 2: “romance, love, coupledom, romantic partnership, live-in partner, marriage, altruism, romance fantasy” on the Google Books Ngram Viewer
On social imagery, “romance” has been tagged as the expression of human passion, culminating in marriage and lovers. (Figure 3) The tags evoke some of Northrup Frye’s senses of romance (1957) as one of four mythic orientations (along with “comedy, tragedy, and irony”). Here, romance is seen as “adventure or quest,” “seeking peace, beauty, or something special,” and “retrospection to idealized past or nostalgia.”
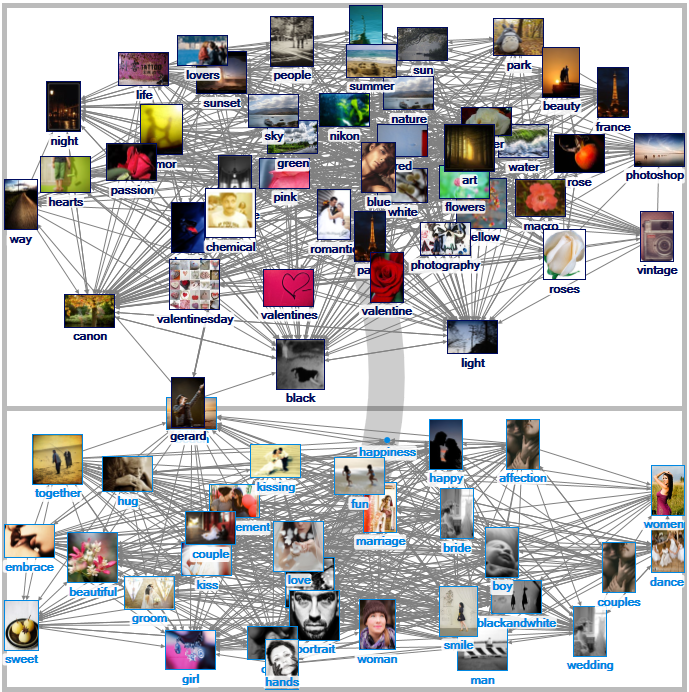
Figure 3: “Romance” Related Tags Network on Flickr (1.5 deg)
Time-correlated searches for “romance” on Google Correlate found many references to songs, films, and games, but nothing notable otherwise.
For the respective social imagery analyses, three sets of social imagery were collected:
- 89 images around “romance” were captured from the Flick social imagery sharing site
- 1,515 images around “romance” were captured from Google Images
- 1,131 images around “romance fraud” were captured from Google Images
On Flickr, the tags are by various hues and then with b/w, “shallow depth of field,” “minimalist,” and “patterns” for visual filtering. On Google Images, the related tags included the following: “relationship, hug, rain, movie, good morning, marriage, wallpaper, art, aesthetics, wedding, bad, heart, serial, drawing, shayari, english, new, quote, vampire, sad, hotel, holi, book, abhi pragya, valentine day, baby, neck, happy, back, (and) woman.” (Tags are represented in the lower case, so they are shown that way here.) There were no tags for the “romance fraud” imageset.
The respective “romance” images show people laughing, hugging, and kissing, many in highly stylized images (like slim silhouetted couples). Many express a language of commercialized romance: red roses, pink hearts, chocolate, jewelry, candles, stuffed teddy bears (and one stuffed panda bear), and others. There are depictions of cosmetics and lingerie. There are pictures of romantic sites: the tropics, beach scenes, and others. There are famous travel destinations: Paris, Venice, Honolulu, and others. There are images of artworks and sculptures. An older couple holds hands for the camera. Some images offer humor: some poetry, and then “Nice t-ts!” There are images of book covers related to the topic. The images show needlework. There are bouquets. There are images of weddings and marriages. There are bottles of alcohol. There are images of dancing, music. There are images of same-sex couples laughing together. Many of the images show an overlay of light-heartedness, such as a photo of two children kissing with their eyes closed. Some messages publicize how to bring romance back to relationships. There are several side-by-side images, showing a young couple to the left and the same couple to the right in old age. A photo shows a man kissing a woman’s pregnant belly. There are romance book covers, with the stylized couples in steamy poses and males with open shirts (showing off “six packs” and muscular abs). One blurred image shows a woman in lingerie from the back. While the people depicted in the imageset are from varied ethnic and racial backgrounds, the main language depicted is English. Some Hollywood couples are also featured. The animated gifs show a couple kissing, dancers performing, and a couple nuzzling. The focus is on positive sentiment and moods: flirty, fun, and maybe a little exciting. [The Graphics Interchange Format or “GIF” have become “a key communication tool in contemporary digital cultures” and are recognizable for their “snippet”-ized aspects and continuous looping (Miltner & Highfield, 2017, p. 1).] The florid messaging is about loving acceptance. There are messages of personal actualization. The images are expressively “loaded” ones with various implications to people’s lived lives. If one views them cynically, the messages are manipulative and saccharine; if one views them sentimentally, the messages celebrate love, which surpasses all, which overcomes hardships, which covers over the mundane.
By contrast to the buoyancy of the prior social imageset, the “romance fraud” imagery involves visuals of abstract broken hearts, handcuffed individuals, warning posters, FBI task force arrests during a press conference, hotline numbers, and crime report covers. One eye-catching message showed a stringy heart held by a clothespin on a branch with the question: “Will you be loved up? Or stitched up?” An information graphic warns again “Valentine’s Day fever.” A photo shows heart-shaped candies side-by-side: “love you” and “send me money.” The words are negative in terms of sentiment: prison sentence, bankruptcy, danger signals, romance fraudsters, and others. There are contact numbers for police in various jurisdictions. One image shows a fishhook running through a credit card. Another shows a mouse-trap with a red heart as bait. One photo shows a pair of male hands on a keyboard, with a shiny gold wedding ring on that finger. Some images show members of the U.S. military, who have had their identities stolen to scam others. Some posters warn against sharing too much information online (TMI), sharing financial details with strangers, and requests to move away from dating sites (which are apparently more attuned to scams than off-site social media accounts). There are warnings against being used for visas. These images show a communicating against the ideals of romance, the idea of idealized couple-dom. They are counterfactuals, alternate narratives, the downside to the earlier upside, the risk vs. the rewards. The narratives here are about actual value vs. face value for scams.
The social images show the presence of commerce, government, and less from the general public. If one were to categorize the sourcing of the images, most seemed to be from the Global North than the Global South, in terms of identifying image features. The messages were mostly about commercial “sell” and the reification of perfect love (shiny red hearts).
The messaging is designed for fomenting aspirational hunger and discontent, a hankering for something that is rare and difficult to achieve. If you are already in a relationship, there is better out there. Is yours true love or something not quite? If you are not in a relationship, two is better than one. If you are starting a relationship, think of the possibilities! The suggestion is that if people keep trying (and spending), they will eventually find true love, when in fact, true love is something co-built and co-created and co-maintained. Everything is at risk at every moment. True love is not for the faint-of-heart, and it is not for the dreamers who cannot engage the reality of another human being. A sense of American marriages is that many of these tend to be “transactional,” with consideration for how well the spouse may provide in terms of financing, and those experiencing unemployment being much less competitive on the marriage market (Chen, Aug. 20, 2017)
Behind the commercial layer are meta-narratives from literature and poetry and song; dance; opera, plays; movies; paintings, and other desiderata of cultures. (Some sources are even constructed biographies of actual people.) These meta-narratives are stories of grand passions, great loves, in which the locus of control is outside of the swept-away individual. The various depicted characters live in a sense of heightened drama. When relationships fail, the heartbreaks are irrecoverable, one-of-a-kind, and lamentable in the long term. When love exists, the self-sacrifice is extreme and emphatic. With such soundtracks and storylines running in people’s heads, they go out into the world with their imaginations forefronted and their good sense somewhere else.
Discussion
Humans experience various needs and appetites. They need to connect to others to meet various needs. People meet their perceived needs in various ways. Sometimes, they pin their hopes to illusions. Humans are vulnerable to fantasies and outsized hopes. They are vulnerable to messaging in all modalities, whether in-person or online, whether text or audio or visual or some combination. They can be misled by messages from within (self-deception) and without (other-deception). People are poor at discerning false notes. They are pretty poor at anticipating the future, except by using averages and data patterns and extrapolating roughly from there. And yet, relationships begin with hope. That is a core fundamental because connecting is effortful and often costly in time and sometimes, funds. That hope can eclipse good sense or critical thinking or rationality. Relationships continue with negotiation and compromises because that is what is required for relationships to maintain, with work and life demands, other relationships, and so on. People shift in their thinking from “I” to “we,” and many times, shift back to the “I.”
In this work, social imagery around “romance” and “romance fraud” (as seeding terms for the downloading of social imagery) showed a focus on commercial descriptions of romance, with bright red hearts, red roses, sweet candies, lace, and a contrastive failure of real life to live up to those ideals. (This is 64% of the images in the Flickr “romance” set were commercial vs. non-commercial, 99.6% of the Google Images “romance” set, and 92% of the Google Images “romance fraud” set commercial.] [Side Note: “Commercial” images are those with clear products in view, recognizable personages in poses, and a professional sheen—in terms of composition, lighting, color jumping, context, and other features. Many of these images are from films, music, soap operas, and others. During the visual coding, it was important to pay close attention since professional photo shoots try to look somewhat realistic, and many photos by amateurs strive to look professional. There were shared visual tropes, such couples kissing against a sunset background on a beach, and others. After the manual coding, the images started to look saccharin and artificial, quite unrealistic and almost silly. “Romance” is about civilities and palate-able indirections, so that people can address personal issues in polite company. Euphemisms, symbolisms, and make-believe narratives can better mask people’s lifestyles and choices that may be highly personal. There seems to be a conscious avoidance of lewdness or offensive imagery, although some skirt and even cross the line.] Law enforcement experts suggest that people should be protective of their online identities and be highly wary when asked to share funds with a stranger who has stories to tell—of surprise costs, of problems crossing borders, and others. [For all the risks of online dating, some con people are caught by the concerted efforts of people who collaborate online and share information online and work with law enforcement. (Monroe, Mar. 16, 2018)]
A “remote woo” sequence
A typical sequence of the “remote woo” con may be seen in Figure 4. At the start, it really does not matter how potential “cons” and “marks” meet because there are many ways such connections can occur. The instigator may be either the “cons” or the “marks”. [Research does suggest that “in almost all situations, the scammer will initiate contact with their target victim” (Tracy, 2008, as cited in Luu, Land, & Chin, 2017, p. 2431). Prior reconnaissance enables a sense of organic and unforced relationship (when in the real, there are very natural awkwardnesses, in many cases). A different study suggests that social media may be another initial point of contact and not dating websites (Kopp, Layton, Sillitoe, & Gondal, July – Dec. 2015, p. 207).] For many, the distances between respective locations (or countries_ may be a boon or a weakness to the relationship. After all, some people prefer something low-maintenance than something much more present. One researcher suggested that the interactions to build trust may take “six to eight months” for the bonding (Rege, 2009, as cited in Whitty & Buchanan, 2012, pp. 2-3). Given that amount of time, it would seem wholly possible to create a backstopped online identity and to misdirect a target mark to various information (look here, not there). Some romance scammers use existing relationships (affinities) to access individuals, who may have lowered guard because of the pre-existing senses of trust (Cross, Dragiewicz, & Richards, 2018, p. 1305). For many, the friending of strangers is not a common way of meeting others to date; what is more typical is reaching out to an extended social network (Arora & Scheiber, 2017).
By definition, the core interests of the “cons” and the “marks” are different, and at some point, the differences lead to a divergence—when the “cons” have better opportunities elsewhere, when the “marks” wise up and stop being “milked” for resources (moneys, information, and other compromises). The end may involve law enforcement or some other paths, like “ghosting” (one or the other withdrawing from all communications from the other and disappearing).
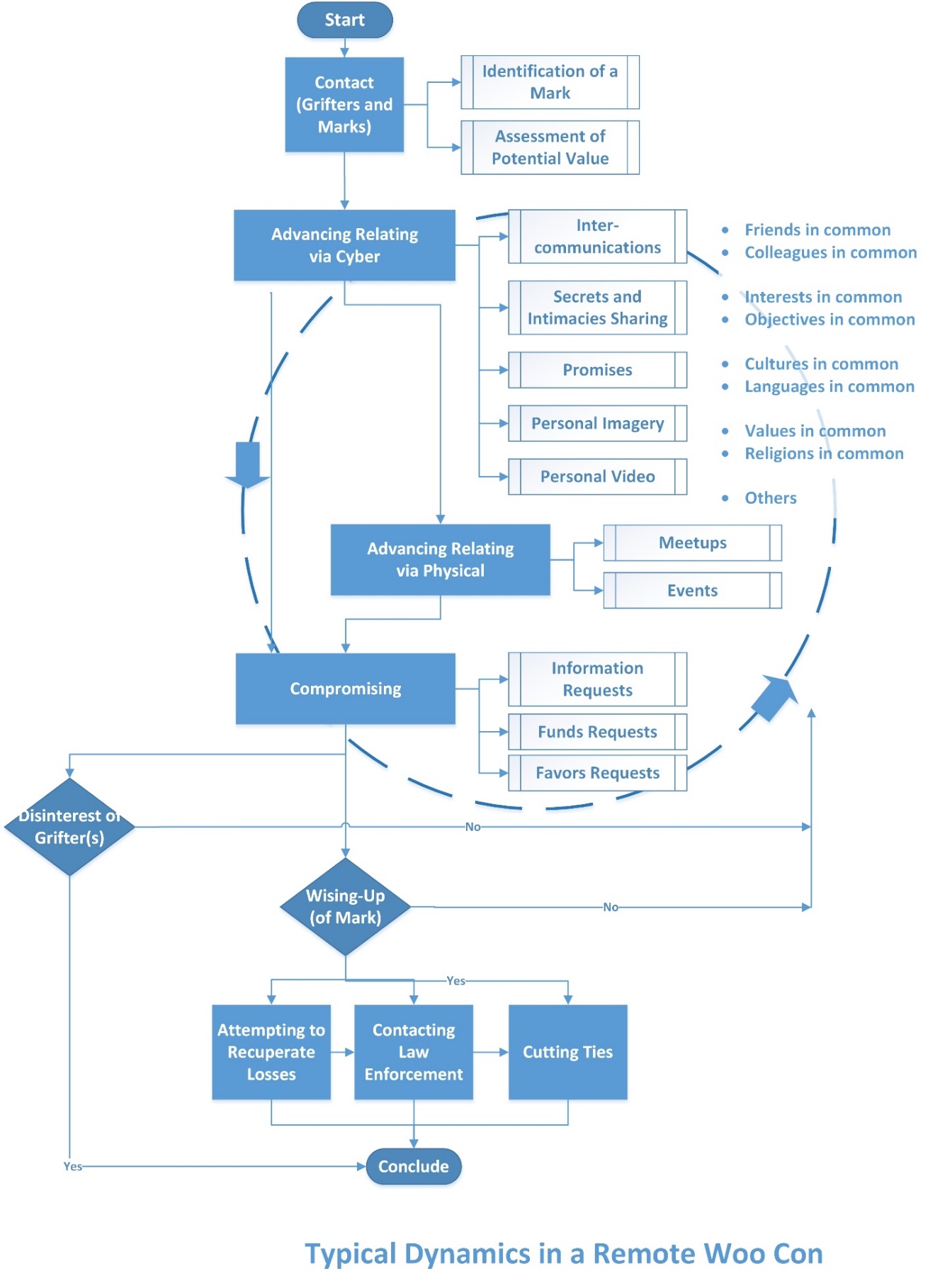
Figure 4: Typical Dynamics in a Remote Woo Con
Per the Review of the Literature, researchers have noted that those who are victimized by romance scammers online tend to be unaware of the actual risks. One intervention may be to share the information about the levels of risk, so that those who go online in pursuit of love can avoid the “high risk, low reward” quadrant, at minimum (Figure 5). Informational asymmetries can be highly de-stabilizing and risky because they enable vulnerabilities in human interactions and relationships to be exploited, even severely.
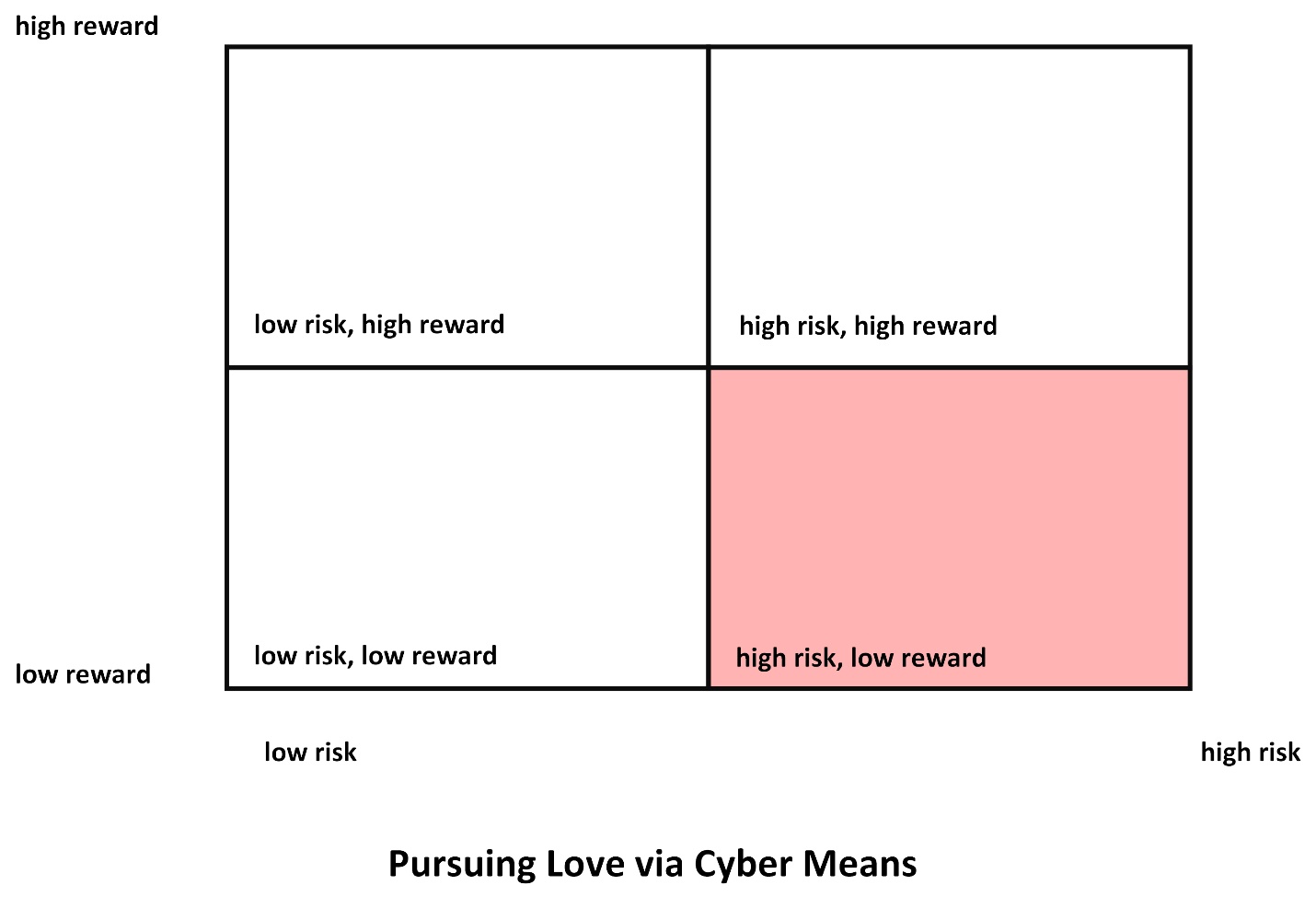
Figure 5: Pursuing Love via Cyber Means
The work of “catfishers” (those who create fake profiles to target specific victims to make them more vulnerable) can be quite sophisticated and impactful (“catfishing,” Nov. 28, 2019). Many know how to set so-called “honey traps,” with “irresistible bait” in digital format. The stratagem are not unlimited, and the tactics are fairly known. Other research suggests that gangs of romance scammers share information and tools; they share tips on what verbiage and methods work. There is research on how romance is seen through particular cultural lenses, to better understand expectations and how to communicate towards those expectations to advantage-take. It turns out that many people can be lured by an attractive story. Confidence tricks “exploit typical human characteristics such as greed, dishonesty, vanity, opportunism, lust, compassion, credulity, irresponsibility, desperation, and naivety” (“Confidence trick,” Feb. 24, 2020).
Experientially, the stages of the confidence trick may be understood in Table 1.
|
Stages of the Con |
Remote Woo |
|
Foundation Work |
Creations of online profiles, setups of confederate accounts, planning for the “social engineering” deceptions, identification of targets |
|
Approach |
The “mark” is approached |
|
Build-up |
“The victim is given an opportunity to profit from participating in a scheme. The victim’s greed is encouraged, such that their rational judgment of the situation might be impaired.” (“Confidence trick,” Feb. 24, 2020) In this case, the romantic interest is roused, to raise both interest and lower rational judgment. |
|
Payoff or Convincer |
The mark is given attention, flattery, and promises (true love everlasting, a spouse, a life of wealth and adventure, an affair). Perhaps presents exchange hands. |
|
Hurrah |
There may be “a sudden manufactured crisis or change of events (which) forces the victim to act or make a decision immediately.” (“Confidence trick,” Feb. 24, 2020) |
|
The In-and-In |
This last step may be a false confirmation bolstering the claims of the remote wooer…by a confederate of the wooer…to reaffirm the false assertions of the false suitor. |
Table 1: Stages of the Remote Woo Con [based on Smith’s “Six Definite Steps or Stages of Growth” in a Confidence Game in 1923, as cited in “Confidence trick,” Feb. 24, 2020]
The growing numbers of people who are compromised suggests that there will always be a percentage of a population that will be vulnerable and gullible to such romantic illusions. Said more harshly: “The booming online dating industry with its ever increasing membership continues to offer scammers with a ready pool of suckers that are ideal for exploitation” (Rege, July – Dec. 2009, p. 508). If the stock market is about “fear and greed” and veering between the two, the online dating scene is about “fear and lust”. The victim’s desires are harnessed in order to create individual and personal vulnerability, albeit on a mass scale. Perhaps the need for love and romance is inelastic for many and creates a constant thrumming need which enables misuse.
People orientate to the world differently, with different expectations of both realspace and cyberspace and their fellow humans. From their different subjectivities, they express differently in the world. They rationalize their own and others’ actions differently. Early research into deception detection from others’ demeanor suggest that even law enforcement often did not perform better than chance (O’Sullivan & Ekman, 2004, p. 269). In an online space, with just a few indicators (all easily faked), it can be more difficult to tell. Social conventions, cultural habits, politeness, and social norms make it difficult to ask others for evidentiary proofs. And even “evidence” can be faked, and if people want to believe hard enough, they will often convince themselves even in the face of overwhelming evidence to the contrary, given people’s confirmation bias (Kahneman, 2011). People’s vulnerabilities are hard to mitigate, based on the prevalence of cognitive biases, self-deception, vanity, emotional desires, and even fantasy needs. Still, potentially, some of the more egregious harms may be somewhat mitigated and headed off in some cases.
The research suggests advancements in computational methods, psychological methods, and others to identify scammers. The ability to conduct reverse image searches may help identify swiped images and actual identities of “heart throbs” whose images are stolen for grifting. Research in this space suggests that faux cyber-romances are not 100% identifiable, and some will slip through. Companies that offer dating services do not have any interest in refereeing people’s respective relationships or personal behaviors. However, they do have an interest in ensuring that their respective platforms are not used for systematic and continuous misrepresentations and frauds. From the outside, with limited communications, it would be difficult for social platforms to level charges of malfeasance without solid evidence, or they will be creating legal liabilities for themselves.
Some researchers refer to “false self-representation” as a form of “micro-fraud” that is pervasive and common (Arora & Scheiber, 2017, p. 418), on social media and in the real. Basic common sense might suggest that people approach online spaces with basic cautions. They may remember pithy advice: If it’s too good to be true, it probably is. Indeed, if those in such relationships cannot discern what they are engaged with, how much harder would it be for someone from the outside (unless they have additional information about the scammer’s prior actions and interrelationships.
Law enforcement, banks, and others are doing what they can to disrupt the criminal groups and individuals engaged in romance scams. There are advances to coalescing scattered online information to understand the pieces as a “SuperIdentity” to validate or invalidate digital personhood (Black, et al., 2012, p. 1). [This is not to say that people can recoup their financial losses from romance scams through litigation, given the challenges of lawsuits across borders and between countries.]
Even if people are “real” and “good-intentioned,” relationships are difficult, and many do not last beyond a few months, much less a year. Not all achieved relationships are necessarily idyllic nor static. A study of Facebook relationships showed that few made it past three years. [The researcher writes: “With every month that passes, more and more shaky relationships end, leaving an ever-larger proportion of solid relationships around” (State, Feb. 12, 2014, p. 1).] The study shows that the longer a couple has already been together, the longer that relationship is likely to last. However, the linegraph shows fast-dropping lines that cumulatively dwindle by half in 48 months or thereabouts. There were also seasonal trends in when breakups occurred, with yearly peaks “during summer months” (May to July) and “a small dip in breakups during February…perhaps a result of Valentine’s Day!” (State, Feb. 12, 2014, p. 1). On average in the U.S., with the promise of “forever” until death parts one or the other or both, approximately half of all marital unions end in divorce. Those marriages that end in divorce last about eight years (or 8.2 years to be more exact). (Fraudulent online romances on average last about 8 months.) The prior is suggestive of probabilities of romances making in time. This assumes clean motives and goodwill and efforts towards connecting, in a world with changing interests and maturing in and out of different connections and relationships. If relationships are to be anticipated and “gamed out” in the “shadow of the future,” the probabilities look stark. A different calculation may provide an actuarial sense of risk in engaging in each. A person can decide what he or she is trading away to be in a relationship and the odds of that relationship turning out to be something healthy and long-term and potentially permanent.
So how can people differentiate a fraud-based romance versus just a bad romance? How can they exercise a healthy dubiousness without shutting themselves down from healthy possibilities?
Romance fraud can be differentiated from a ‘bad’ relationship by its modus operandi, with the offender explicitly seeking to form a relationship with a person for the sole purpose of deceiving and manipulating them into sending money. (Cross, Dragiewicz, & Richards, 2018, p. 1304)
Given the long odds, those who would pursue romantic fairytales and stories of being actualized by love (finding a prince, finding a princess) are at a disadvantage, liable to compromise their personal finances, physical health, psychological well-being, and social reputation, by blithely engaging others on face value, by confusing promises for reality, and mixing “cheap talk” for “costly signaling.” Still, if the odds seem worth it, people do better to engage cyber-skepticism as the “mind’s firewall” (Thomas, 2008, p. 8). Trust is never a once-and-done but something that has to be tested and reinforced continuously. It would seem that those who engage in swift trust, without some due diligence, without some testing of others’ claims, would put themselves at risk. [Some popular impressions suggest that fast intensifications of online relationships may lead to “compulsive overindulgence in, this speeded up, heightened, eroticized pseudointimacy” even as researchers suggest that that may be a negative stereotype only (Cooper & Sportolari, 1997, p. 13).] Those who set redlines for their own well-being and safety but are unable to enforce those lines are also at risk. People who care too much about social approval and enable strangers to speak into their lives are also putting excessive power in others’ hands. People who tend to spill a lot of personal information on social media offer a much larger “attack surface” for others’ to exploit. Internal monologues and other shares can be excessive and can be deeply revelatory (even unintentionally so). It seems wise to apply common sense to decision-making and apply analytical thinking to all aspects of a life, especially in moments of emotional vulnerability (after a breakup, on the rebound). It seems wise not to be clouded by dreams and ambitions. People should not be apologetic about being self-advocating and self-protecting because people have to be responsible for themselves. They should not compromise themselves based on vulnerabilities from personal feelings of insecurity, loneliness, or the turmoil from undergoing life changes.
When people invest hopes in another, some respond by being their best selves (in a virtuous cycle), and others respond by advantage-taking (in a vicious cycle). Sometimes, it may take decades before the malicious or destructive behaviors manifest in full. Categorizing victims as “innocents” does not seem appropriate, given the wide availability of warnings about such frauds and all sorts of evidence about core human nature. It seems more accurate to assume that everyone out there who is a volitional adult has to be responsible for their own well-being and not assume that they will have an effortless “happily ever after.” Those who would set standards very low will end up having to engage unnecessary risks. Finally, if idealized “true love” is lauded so often, it is because it is also rare. Their mentions create a misguided sense of reality, based on “survival bias.” (People do not tend to laud breakups, so the stories that “survive” in the public mind are those of mythicized love as possible.) The dazzle and the promise of such a future may inspire some people to rely on the thinnest of claims about others’ personality, others’ character, others’ trustworthiness, and this can result in all sorts of vulnerabilities and abuses. Practically, dyadic romantic matches require hard work, plenty of communications, mutual respect, risk-taking, trust-building, and compromise, and they do not just appear on digital horizons as common fact patterns. There is no point at which a couple has finally “arrived” for good, and then it’s wine and roses. Plenty of long-term couples and spouses are found to have difficult relationships. If time were a measure, a majority of serious relationships also fail—whether formally on paper and / or in the real, in terms of breakdowns of relationships and negative emotions and apathy. At a minimum, though, simple scams (and other get-rich-quick schemes based on alluring storytelling and emotional manipulations) such as the ones online should be able to be spotted and addressed. Social imagery may provide visibility into some massmind concepts of romance and love and heartbreak but shows little about the complexities of the voracious human heart and devious mind.
Future Research Directions
Beyond social media and dating apps, there are immersive virtual worlds that are venues for romance. Researchers point to the sexualization of digital avatars (Behm-Morawitz & Schipper, 2016), sex work on Second Life (Lynch, 2010), and the ability to build a 3D sense of a person through avatars and enabling the “immersive parasocial” (Hai-Jew, Sept. 2009), the pursuit of one-way “relationships” with a public figure, with the socio-technological ability to directly address human-embodied avatars with a sense of online presence. How romance scams manifest in immersive virtual worlds and online games would be of interest.
Follow-on research may involve other systematized ways to understand the “remote woo”—from different cultural contexts and criminal groups and criminal individuals. More research may capture how the respective teams function, how they conduct research and reconnaissance, who they target and how, how they make decisions, and so on.
Perhaps imagery from private holdings may be analyzed for their messaging, to better understand the online ploys and what is efficacious.
Finally, it would be helpful to explore more powerful defenses against romance scams, at the individual, group, platform, and societal levels, as well as transnational and global ones. To these ends, at every level, it would help if people (and machines) could be employed to either substantiate or falsify senses of each other, even though the haze of wanting to believe in the rarity and the dream of “love at first sight” and of “love” in the social imaginary and individual attractiveness and self-value. In the absence of avenues of recourse, oftentimes, given the limits of the reaches of legal systems and policing abroad, perhaps there can be pre-online-dating counseling, to address some of the gullibility of both “noobs” (newbies) and the more experienced. It would also help to mitigate senses of pressure and competition—that might discourage individuals from being skeptical. Also, in terms of social engineering, sometimes, people are manipulated when they follow cultural scripts such as in relating to apparent high-status individuals or authoritative ones; people need to train against such scripts and think more critically. It may help to have clearer senses of statistical probabilities, given the outsized impressions of romantic connections made through advertising, marketing, and “survival bias” in terms of news coverage (what is described as successes vs. the many failures that do not attain media attention). Celebrities gush and share about what makes and the weddings, but focus less on the breakups and divorces. In this competitive landscape, the gullible or the naïve or even the ordinary person who gets “sold” = “compromised,” in the hands of skillful con artists.
As former confidence man and later FBI Frank Abagnale observes, the uses of social technology is a force multiplier, and the ability for de-humanized interactions enables confidence individuals to take an individual for every cent. He suggests that there are two red flags or warnings in every scam: an “urgent need for money” and “asking for personal information” (Exley, Dec. 5, 2019). The pressure for speedy action shortens the time for a person to respond with reasoned thinking, and the personal information is harvested for mis-use. (A colleague of mine who was propositioned on the street and asked for personal information responded, “What’s it to you?” That sense of street smarts—would you accept an intimate proposition from a stranger?—would hold people in better stead than assuming that people are as they self-portray online. Those acculturated to online dating and swiping left with strangers may be amenable to stranger propositions on the street, though, and rely on others’ civilization, others’ non-violence, and prophylactics to try to stay “safe”. They put their own wellbeing into the hands of others based on a good faith understanding.)
A core premise of this chapter is that people (at heart) do not want to be “bamboozled by a fake” (Pyne, 2019, p. 9), particularly if it is costly to the wallet and to self-identity / ego. However, if this premise is wrong, then faux romances may be a form of adult play, with incursions into the imaginary. Those who engage in that may appreciate “knock-off affection,” outsized digital displays of attraction and faux loyalty, and fantastical stories of love that stretch credulity. Perhaps some people enjoy playing at reality with so-called “genuine fakes,” known fakes. Perhaps the allure of “idolatry” (Pyne, 2019, p. 36) has an appeal to some consumers of fakes. Faux romance can like projecting oneself into a glowy movie or another fantasy space. The surfeit of hope is important for some in their constructed senses of the world. Here, perhaps an individual wants to believe in their own great beauty and charm and wit; they want to believe in the accolades of the enchanted lovers from abroad. This penchant for the red and pink hazes of illusions means that flattering words are swapped for finances and goods, and the fraudsters crowd-fund by deceptions to the tune of hundreds of millions a year globally. Some research may explore the social-psychological aspects of such self-deceptions.
This work used a basic binary: a “real” romance vs. a “faux” one. If there are objects in the world “that defy a neat, superficial categorization—it’s full of in-between objects that are real and not-real at the same time” (Pyne, 2019 p. 10), perhaps this in-between concept may be helpful in terms of a real-try sort of romance. Perhaps a “real” romance may be too challenging that some fakery or some escapism or some fantasy is beneficial and even necessary to try for love. After all, people may have a taste for the artificial, the staged, the white lies, and the performative. If people cannot defend themselves with some rigor against manipulations, then the cost is on them and to those close to them.
Conclusion
Finally, new romance scams are emerging all the time, as variations on an old and trite scam. In recent times, with the global novel coronavirus pandemic, there have been outreaches to people via their personal accounts and phones by people who want to connect, who want to chat, who want to be social. Romance scammers are reaching out to those in social isolation and self-quarantining because so many are used to socializing in workplaces and with friends in local hotspots. The new quiet makes some anxious and uncomfortable, and the remote woo merchants are trying to find a way in, to exploit. They have romance to peddle, and there are always buyers.
References
Agrawal, A. (2015). Cyber-matchmaking among Indians: Re-arranging marriage and doing ‘kin work’. South Asian Popular Culture, 13(1), 15-30.
Arora, P., & Scheiber, L. (2017). Slumdog romance: Facebook love and digital privacy at the margins. Media, Culture & Society, 39(3), 408-422.
Barnes, S. B. (1996). Internet relationships: the bright and dark sides of cyber-friendship. Telektronikk, 92, 26-39.
Bartlett, J. (2019, Nov. 24). Cryptoqueen: How this woman scammed the world, then vanished. BBC News. Retrieved Nov. 29, 2019, from https://www.bbc.com/news/stories-50435014.
Behm-Morawitz, E., & Schipper, S. (2016). Sexting the avatar: Gender, sexualization, and cyber-harassment in a virtual world. Journal of Media Psychology, 28(4), 161 – 174.
Ben-Ze’ev, A. (2015). Sexuality and the Internet. International Encyclopedia of the Social & Behavioral Sciences, 21, 813 – 818.
Bergmann, M. C., Dreißigacker, A., von Skarczinski, B., & Wollinger, G. R. (2018). Cyber-dependent crime victimization: the same risk for everyone?. Cyberpsychology, Behavior, and Social Networking, 21(2), 84-90.
Black, S. M., Creese, S., Guest, R. M., Pike, B., Saxby, S. J., Stanton Fraser, D., Stevenage, S.V., & Whittty, M. T. (2012). SuperIdentity: Fusion of identity across real and cyber domains. 1 – 10.
Bonebrake, K. (2002). College students’ Internet use, relationship formation, and personality correlates. CyberPsychology & Behavior, 5(6), 551-557.
Bryant, K., & Sheldon, P. (2017). Cyber dating in the age of mobile apps: understanding motives, attitudes, and characteristics of users. American Communication Journal, 19(2), 1 – 15.
Cabrera-Frias, L. (2010). Cyber Courtship: Computer Matchmaking and Trends in Online Romance. Synesis: A Journal of Science, Technology, Ethics, and Policy, G:1 – G:4.
Catfishing. (2019, Nov. 28). Wikipedia. Retrieved Nov. 30, 2019, from https://en.wikipedia.org/wiki/Catfishing.
Chen, V.T. (2017, Aug. 20). America, home of the transactional marriage. The Atlantic. Retrieved Jan. 19, 2020, from https://getpocket.com/explore/item/america-home-of-the-transactional-marriage?utm_source=pocket-newtab.
Chou, T. J., & Ting, C. C. (2003). The role of flow experience in cyber-game addiction. CyberPsychology & Behavior, 6(6), 663-675.
Clemens, C., Atkin, D., & Krishnan, A. (2015). The influence of biological and personality traits on gratifications obtained through online dating websites. Computers in Human Behavior, 49, 120 – 129.
Confidence trick. (2020, Feb. 24). Wikipedia. Retrieved from https://en.wikipedia.org/wiki/Confidence_trick.
Cooper, A., & Sportolari, L. (1997). Romance in cyberspace: Understanding online attraction. Journal of Sex Education and therapy, 22(1), 7-14.
Cornelius, D. R. (2016). Online identity theft victimization: An assessment of victims and non-victims level of cyber security knowledge (Doctoral dissertation, Colorado Technical University).
Cross, C., Dragiewicz, M., & Richards, K. (2018). Understanding romance fraud: Insights from domestic violence research. The British Journal of Criminology, 58, 1303 – 1322.
DeMarco, J., Cheevers, C., Davidson, J., Bogaerts, S., Pace, U., Aiken, M., Caretti, V., Schimmenti, A., & Bifulco, A. (2017). Digital dangers and cyber-victimisation: a study of European adolescent online risky behaviour for sexual exploitation. Clinical Neuropsychiatry, 14(1), 104-112.
Döring, N. (2002). Studying online-love and cyber-romance. In B. Batinic, U.-D., Reips, & M. Bosnjak (Eds.), Online Social Sciences (pp. 333 – 356). Seattle: Hogrefe & Huber Publishers. Retrieved Nov. 27, 2019, from
Doubek, J. (2019, Feb. 13). Americans lost $143 million in online relationship scams last year. Your Money. National Public Radio.
Dryer, J. A., & Lijtmae, R. M. (2007). Cyber-sex as twilight zone between virtual reality and virtual fantasy: Creative play space or destructive addiction? The Psychoanalytic Review, 94(1), 39-61.
Enteen, J.B. (2005). Siam remapped: Cyber-interventions by Thai women. New Media & Society, 7(4), 457 – 482.
Exley, R. (2019, Dec. 5). The real ‘Catch Me if You Can’ con artist says every scam involves these red flags. CNBC. Retrieved Dec. 5, 2019, from https://www.cnbc.com/2019/12/05/catch-me-if-you-cans-frank-abagnale-says-every-scam-has-2-red-flags.html.
Felmlee, D., & Faris, R. (2016, Sept.) Toxic ties: Networks of friendship, dating, and cyber victimization. Social Psychology Quarterly, 79(3), 243- 262.
Fletcher, E. (2019, Feb. 12). Romance scams rank number one on total reported losses. Consumer Protection. Federal Trade Commission. Retrieved Feb. 10, 2020, from https://www.ftc.gov/news-events/blogs/data-spotlight/2019/02/romance-scams-rank-number-one-total-reported-losses.
Hai-Jew, S. (2009, Sept.) Exploring the immersive parasocial: Is it you or the thought of you? Journal of Online Learning and Teaching, 5(3), 1 – 10. Retrieved Nov. 24, 2019, from https://jolt.merlot.org/vol5no3/hai-jew_0909.htm.
Harris, K.M., & Aboujaoude, E. (2016). Online friendship, romance, and sex: Properties and associations of the Online Relationship Initiative Scale. CyberPsychology, Behavior, and Social Networking, 19(8), 487 – 493.
Helsper, E.J., & Whitty, M.T. (2010). Netiquette within married couples: Agreement about acceptable online behavior and surveillance between partners. Computers in Human Behavior, 26, 916 – 926.
Ho, J. (2003). Cyber Sex: Sexuality, youth, and cyber space. Cyber Sex: Sexuality, Youth, and Cyber Space.
Houser, M.L., Fleuriet, C., & Estrada, D. (2012, Jan. – Mar.). The cyber factor: An analysis of relational maintenance through the use of computer-mediated communication. Communication Research Reports, 29(1), 34 – 43.
Jerin, R., & Dolinsky, B. (2001). You’ve got mail! You don’t want it: Cyber-victimization and on-line dating. Journal of Criminal Justice and Popular Culture, 9(1), 15-21.
Kahneman, D. (2011). Thinking, Fast and Slow. New York: Farrar, Straus and Giroux.
Kite, S.L., & Gable, R.K. (2013). Cyber threats: A study of what middle and high school student (sic) know about threatening behaviours and internet safety. Int. J., Social Media and Interactive Learning Environments, 1(3), 240 – 254.
Kopp, C., Layton, R., Sillitoe, J., & Gondal, I. (2015). The Role of Love stories in Romance Scams: A Qualitative Analysis of Fraudulent Profiles. International Journal of Cyber Criminology, 9(2).
Lazarus, S. (2018). Birds of a feather flock together: the Nigerian cyber fraudsters (Yahoo boys) and hip hop artists. Criminology, Crim. Just. L & Soc’y, 19, 63- 81.
Lee, M. (2018). Crime and the Cyber Periphery: Criminological Theory Beyond Time and Space. In The Palgrave Handbook of Criminology and the Global South (pp. 223-244). Palgrave Macmillan, Cham.
Lee, C. W., & Chang, R. K. (n.d.) Faithfulness and Unfaithfulness of Cyber Cohabitation–An Example of iPartment. 1 – 4.
Letherby, G., & Marchbank, J. (2012). Cyber-chattels: buying brides and babies on the Net. In Dot. cons (pp. 76-93). Willan.
Liang, C.S. (2015). Cyber jihad: Understanding and countering Islamic State propaganda. Geneva Centre for Security Policy, 1 – 12.
Luu, V., Land, L., & Chin, W. (2017). Safeguarding Against Romance Scams–Using Protection Motivation Theory. In the proceedings of 25th European Conference on Information Systems (ECIS) 2017. 2429 – 2444.
Lynch, M. J. (2010). Sex Work in Second Life: Scripts, Presence, and Bounded Authenticity in a Virtual Environment. Social Thought & Research, 31, 37 – 57.
Maheu, M. M. (1999). Women’s Internet Behavior: Providing Psychotherapy Offline and Online for Cyber-Infidelity. TeleHealth.net.
Mainiero, L.A., & Jones, K.J. (2013). Sexual harassment versus workplace romance: Social media spillover and textual harassment in the workplace. The Academy of Management Perspectives, 27(3), 187 – 203.
Marshall, J. (2003). The Sexual Life of Cyber‐Savants. The Australian Journal of Anthropology, 14(2), 229-248.
Martin, R. (2019, Nov. 18). The language of cybercrime. National Public Radio.
Mileham, B. L. A. (2007). Online infidelity in Internet chat rooms: An ethnographic exploration. Computers in Human Behavior, 23, 11 – 31.
Miltner, K.M., & Highfield, T. (2017). Never gonna GIF you up: Analyzing the cultural significance of the animated GIF. Social Media + Society, 1 – 11.
Monroe, R. (2018, Mar. 6.) The perfect man who wasn’t. Atlantic. Retrieved Jan. 16, 2020, from https://getpocket.com/explore/item/the-perfect-man-who-wasn-t?utm_source=pocket-newtab.
Ojilere, A., Nnabue, U., & Oraegbunam, I. K. (2018). Conceptualizing cyber scam in Nigeria. African Journal of Criminal Law and Jurisprudence, 2, 1 – 13.
O’Sullivan, M., & Ekman, P. (2004). 12 The wizards of deception detection. The detection of deception in forensic contexts, 269 – 286.
Pruitt, D., & LaFont, S. (1995). For love and money: romance tourism in Jamaica. Annals of tourism research, 22(2), 422-440.
Pyne, L. (2019). Genuine Fakes: How Phony Things Teach Us about Real Stuff. London: Bloomsbury Sigma.
Rambaree, K. (2008). Internet-mediated dating/romance of Mauritian early adolescents: A grounded theory analysis. International Journal of Emerging Technologies and Society, 6(1), 34 – 59.
Rege, A. (2009). What’s Love Got to Do with It? Exploring Online Dating Scams and Identity Fraud. International Journal of Cyber Criminology, 3(2).
Rich, E., Martinez-Moyano, I. J., Conrad, S., Cappelli, D. M., Moore, A. P., Shimeall, T. J., Andersen, D.F., Gonzalez, J.J., Ellison, R.J., Lipson, H.F., Mundie, D., Sarriegui, J.M., Sawicka, A., Stewart,T.R., Torres, J.M., Weaver, E.A., & Wiik, J. (2005, July). Simulating insider cyber-threat risks: A model-based case and a case-based model. In Proceedings of the 23rd International Conference of the System dynamics Society (pp. 17-21). The System Dynamics Society.
“romance.” (2019). Oxford English Dictionary (online).
Saad, M.E., Abdullah, S.N.H.S., & Murah, M.Z. (2018). Cyber romance scam victimization analysis using Routine Activity Theory versus Apriori algorithm. International Journal of Advanced Computer Science and Applications, 9(12), 479 – 485.
Saleh, N. (2019, July 27). Are Internet dating sites endangering public health. Very Well Health. Retrieved Dec. 1, 2019, from https://www.verywellhealth.com/are-internet-dating-sites-endangering-public-health-4118176.
Schifferle, L.W. (2019, Feb. 12). Romance scams will cost you. Federal Trade Commission blog. Retrieved Nov. 25, 2019, from https://www.consumer.ftc.gov/blog/2019/02/romance-scams-will-cost-you.
Scott, V. M., Mottarella, K. E., & Lavooy, M. J. (2006). Does virtual intimacy exist? A brief exploration into reported levels of intimacy in online relationships. CyberPsychology & Behavior, 9(6), 759-761.
Shaari, A. H., Kamaluddin, M. R., Paizi, W. F., & Mohd, M. (2019). Online-Dating Romance Scam in Malaysia: An Analysis of Online Conversations between Scammers and Victims. GEMA Online® Journal of Language Studies, 19(1).
Singh, M., & Jackson, M. (2015). Online dating sites: A tool for romance scams or a lucrative e-business model? In The Proceedings Of The 28th Bled Econference. June 7 – 10. Bled, Slovenia. 482 – 488.
State, B. (2014, Feb. 12). Flings or lifetimes? The duration of Facebook relationships. Retrieved Nov. 27, 2019, from https://www.facebook.com/notes/facebook-data-science/flings-or-lifetimes-the-duration-of-facebook-relationships/10152060513428859/.
Taylor, S., & Xia, Y. (2018). Cyber partner abuse: A systematic review. Violence and Victims, 33(6), 984 – 1011.
Thomas, T. L. (2008). Cyberskepticism: The Mind’s Firewall. Foreign Military Studies Office (Army), Fort Leavenworth, Kansas. 4 – 9.
Venables, E.C. (2009). Chapter 6: It’s all about making contacts”: Côtéman and Migration. In Imagining Migration: Cyber-cafes, sex and clandestine departures in the Casamance, Senegal. Unpublished Ph.D. Thesis. Centre of African Studies, University of Edinburgh. 146 – 171.
Venables, E. (2008). Senegalese women and the cyber café: Online dating and aspirations of transnational migration in Ziguinchor. African and Asian Studies, 7(4), 471-490.
Whitty, M. T. (2015). Anatomy of the online dating romance scam. Security Journal, 28(4), 443-455.
Whitty, M.T. (2018). Do you love me? Psychological characteristics of romance scam victims. Cyberpsychology, Behavior, and Social Networking, 21(2), 105 – 109.
Whitty, M.T., & Carr, A.N. (2003). Cyberspace as potential space: Considering the web as a playground to cyber-flirt. Human Relations, 56(7), 869 – 891.
Whitty, M. T., & Buchanan, T. (2012). The online romance scam: A serious cybercrime. CyberPsychology, Behavior, and Social Networking, 15(3), 181-183.
Williams, E. J., Beardmore, A., & Joinson, A. N. (2017). Individual differences in susceptibility to online influence: A theoretical review. Computers in Human Behavior, 72, 412-421.
Wright, M. F. (2015). Cyber aggression within adolescents’ romantic relationships: Linkages to parental and partner attachment. Journal of youth and adolescence, 44(1), 37-47.
Wurtele, S.K. (2017). Preventing cyber sexual solicitation of adolescents. In R. Alexander (Ed.), Research and practices in child maltreatment prevention. Vol. 1 of 2 (pp. 361 – 393). St. Louis, MO: STM Learning, Inc.
Key Terms
Catfishing: The creation of fake personal profile online to be particular attractive to a target individual
Cyber Dating: Using Internet apps and information and communications technology (ICT) to create a social or romantic connection
Remote Woo: The uses of information and communications technology (ICT) to try to win over a person from a physical distance
Romance: A sense of mystery and novelty from daily life
Transnational Interpersonal Romance: A distance “love” relationship

